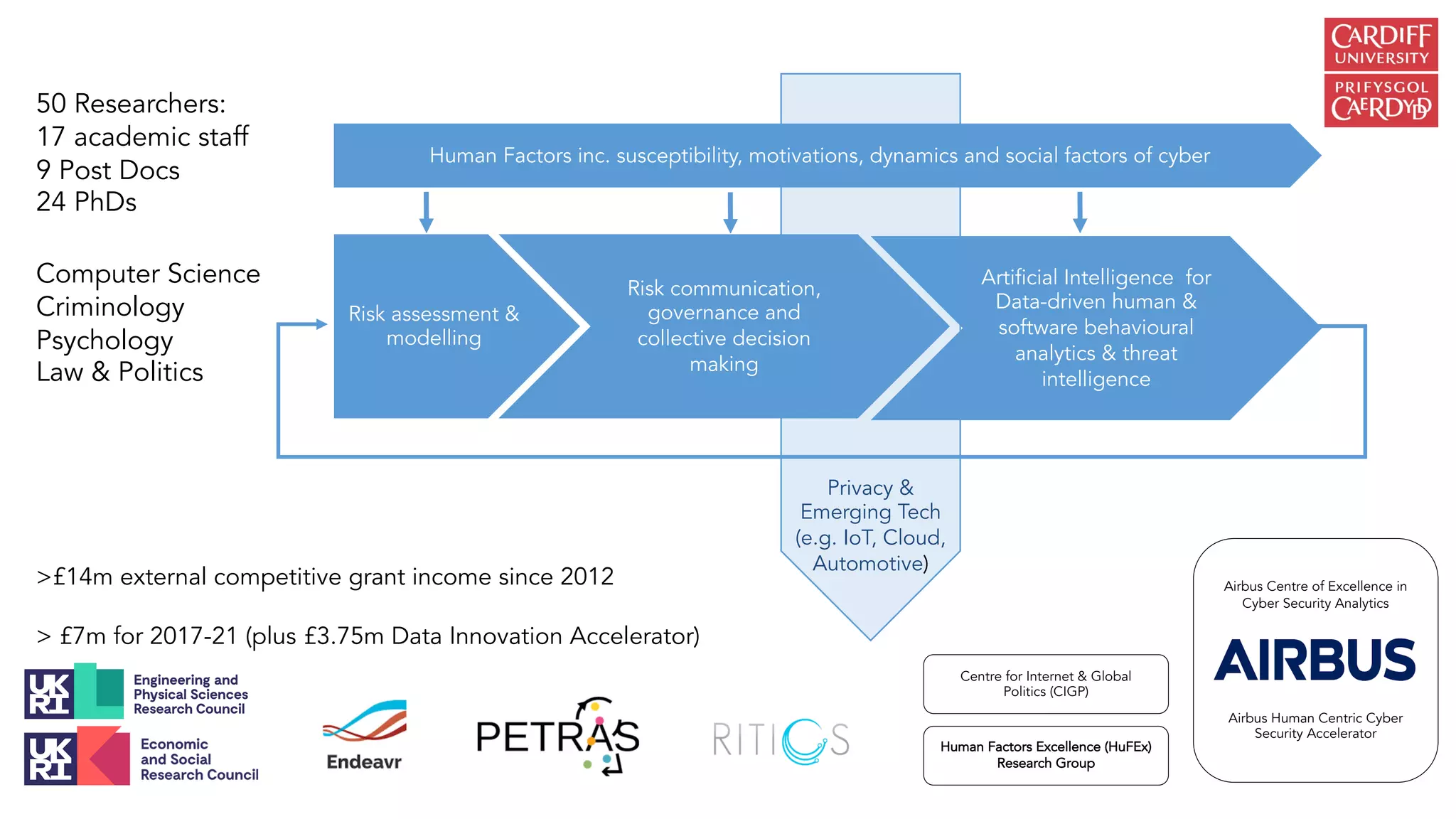
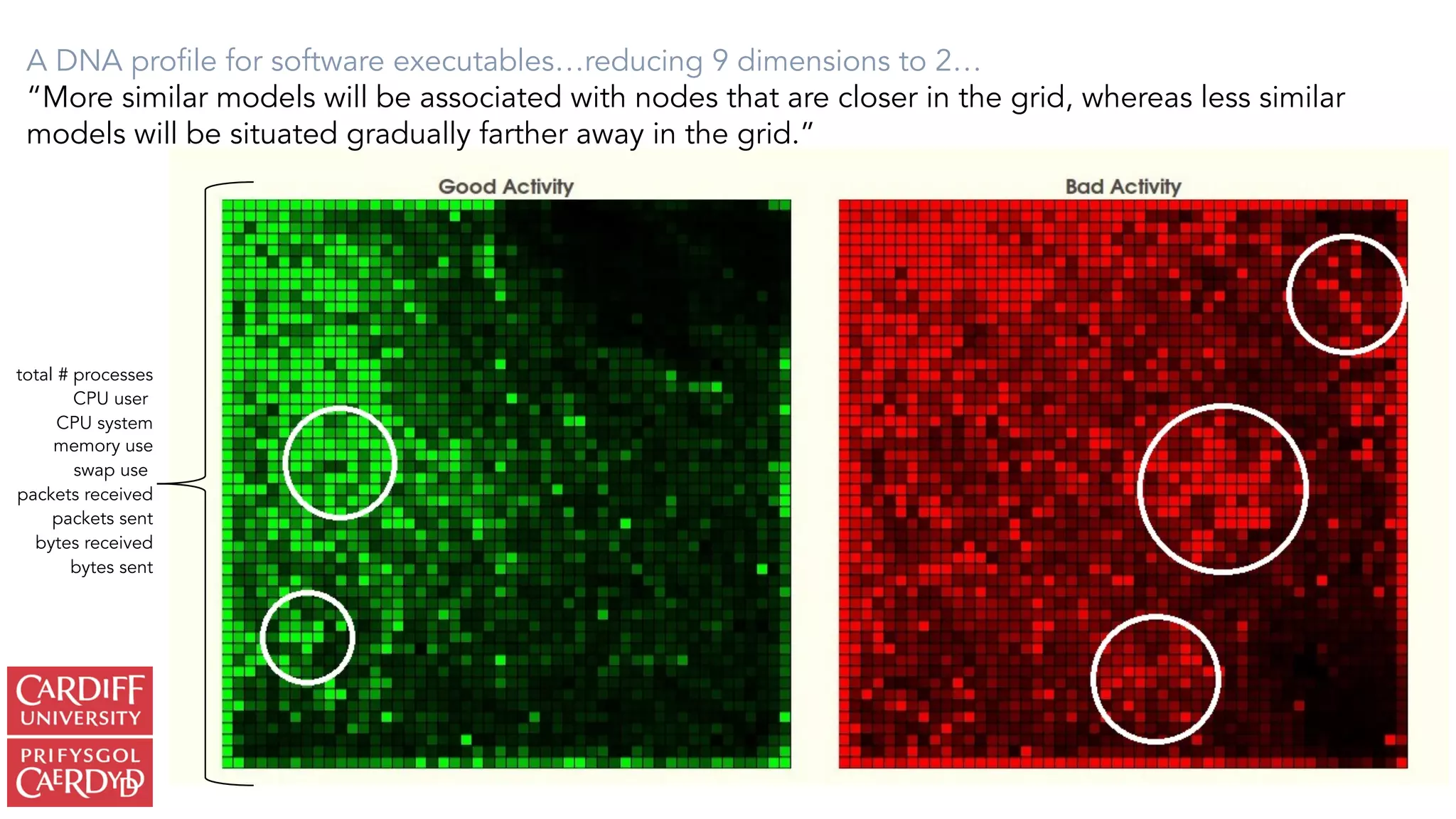
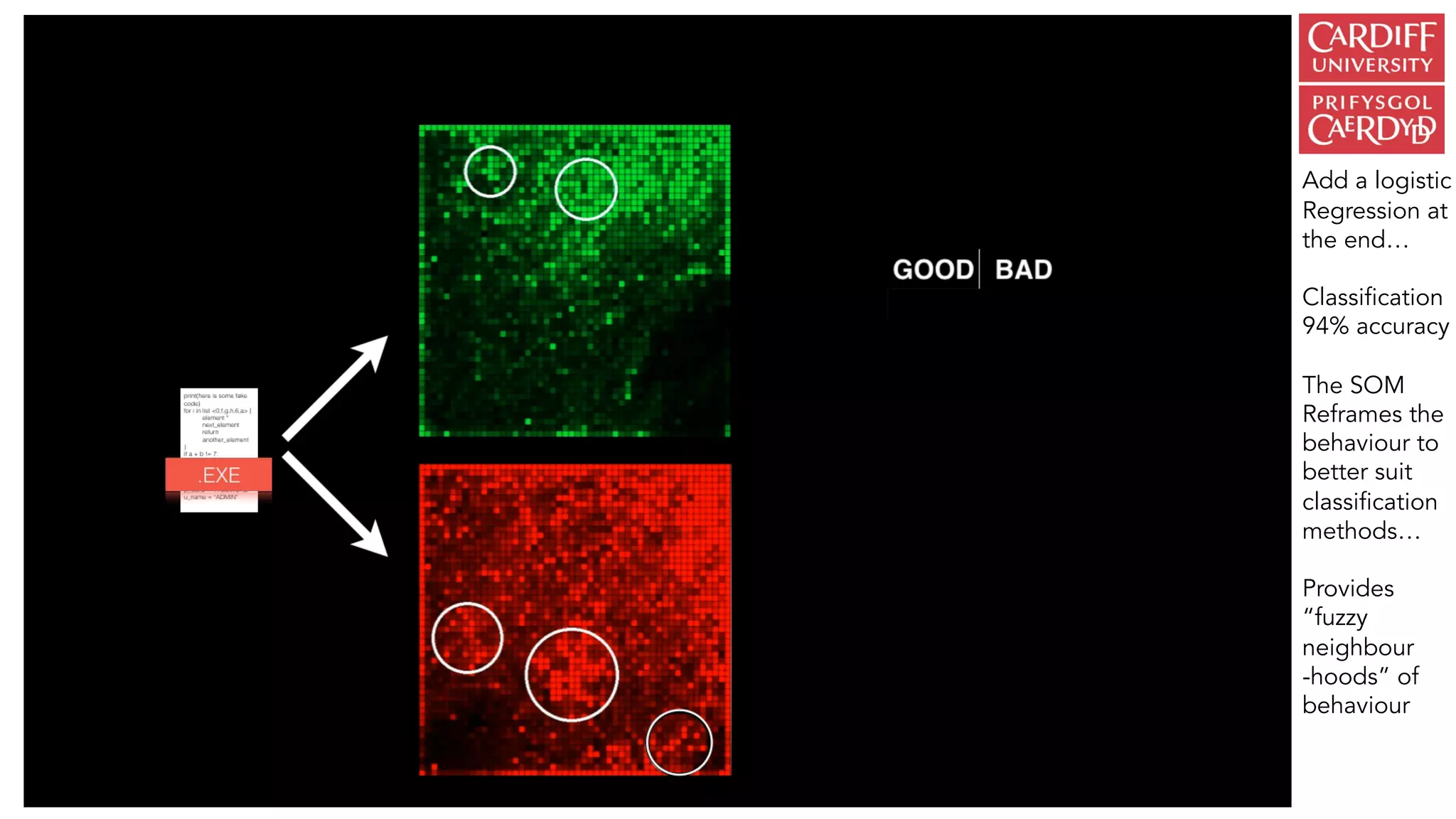
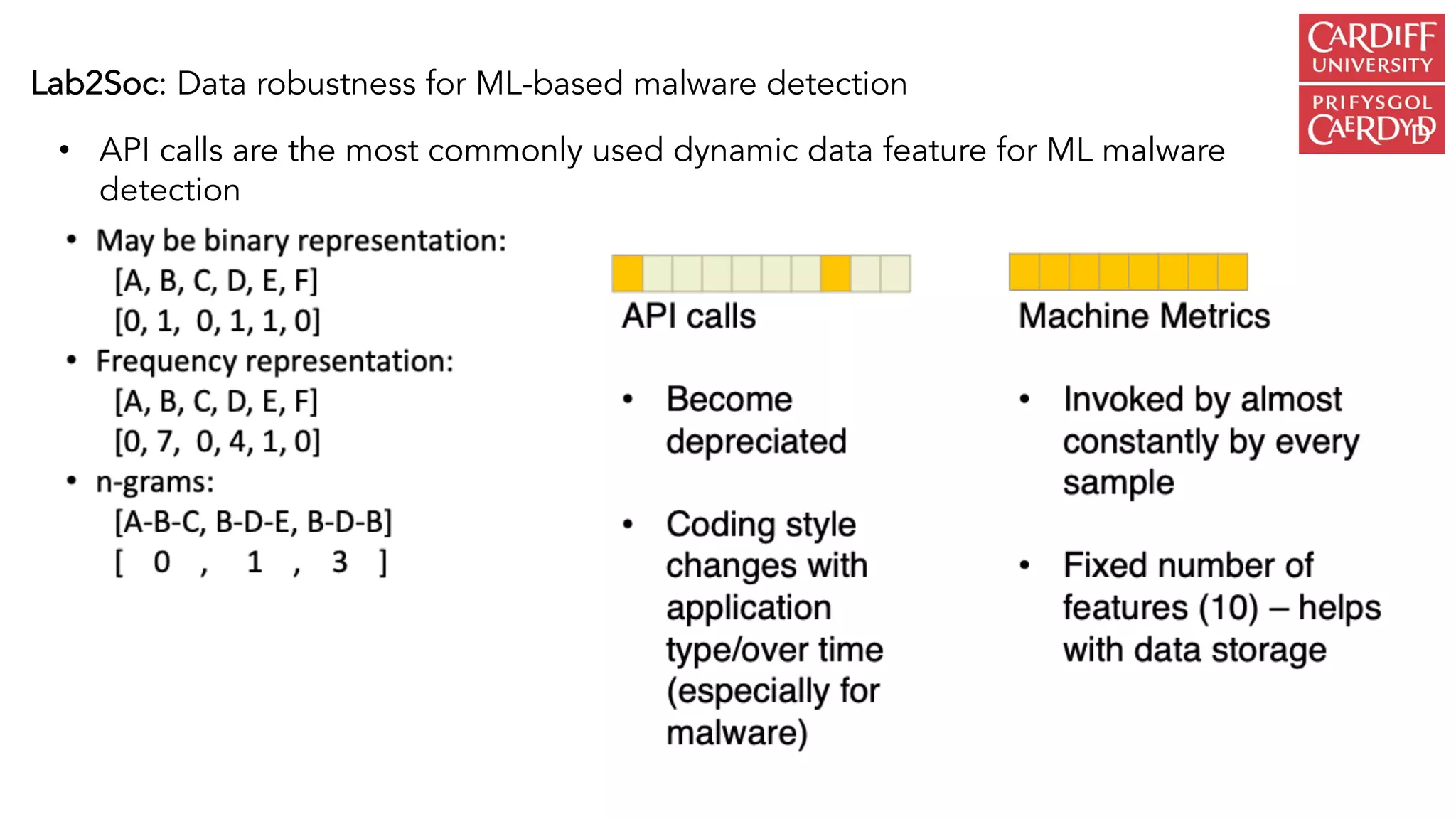
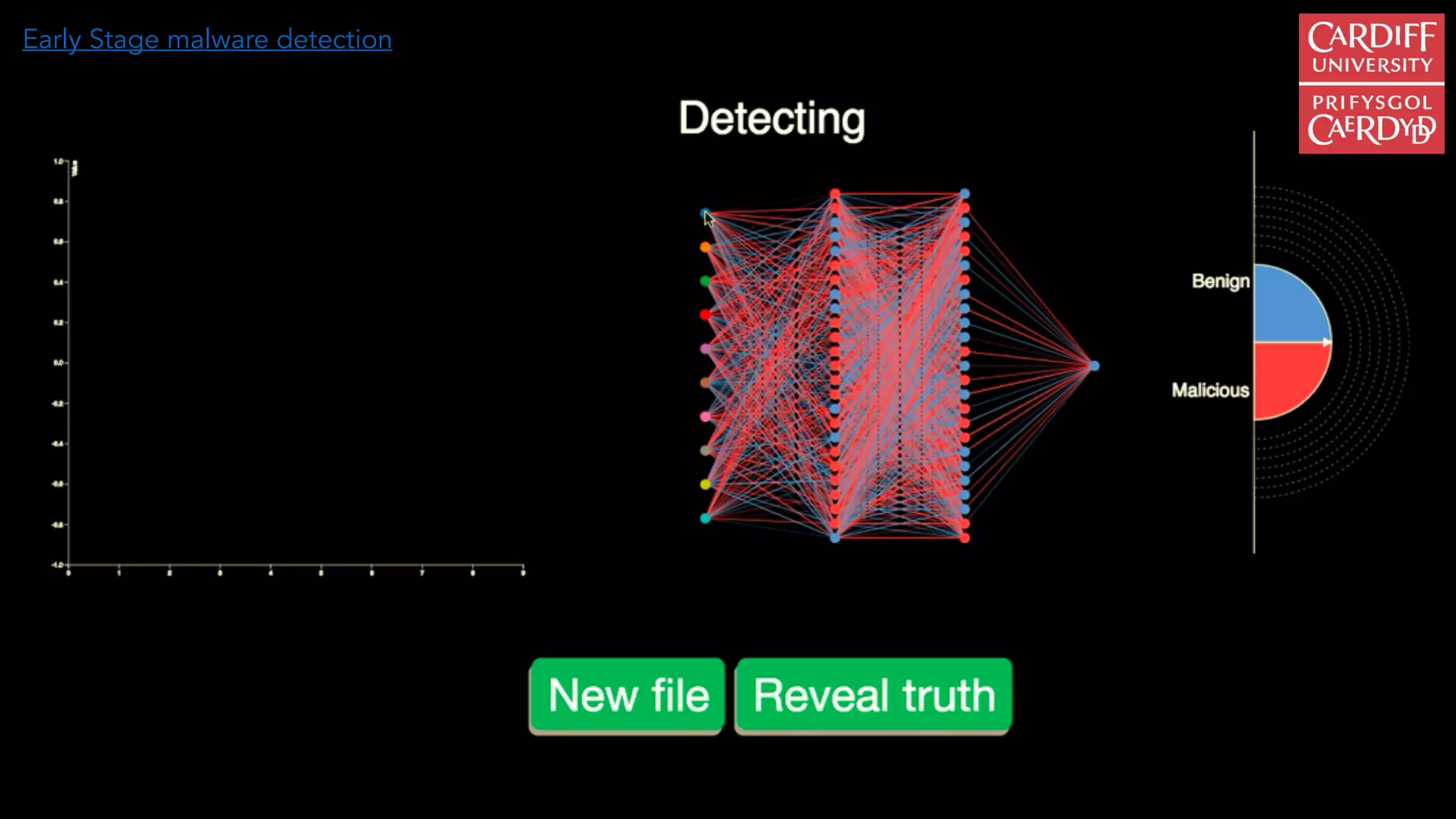
The document outlines the vision and initiatives of an academic center focusing on cybersecurity innovation, emphasizing the integration of artificial intelligence and cutting-edge research to build resilience against cyber threats in the UK. It highlights the development of advanced security operations centers (SOCs) and machine learning techniques for real-time malware detection and prediction, achieving significant accuracy rates. The research combines expertise from various fields, including computer science, criminology, and psychology, to address emerging challenges in cybersecurity analytics.