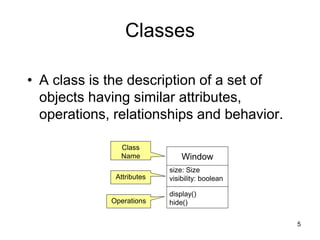
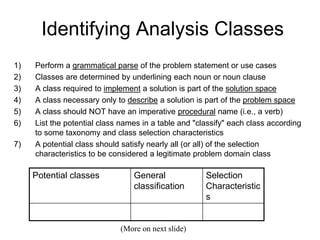
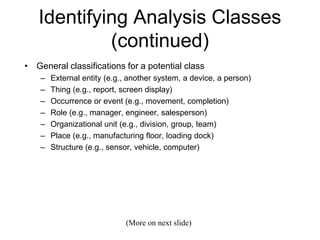
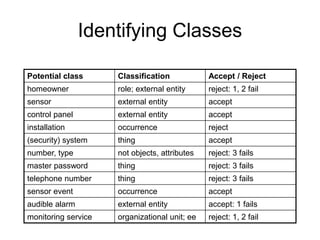
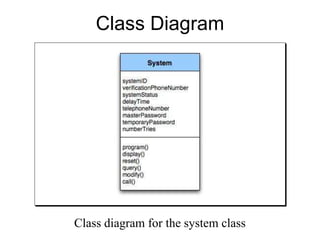
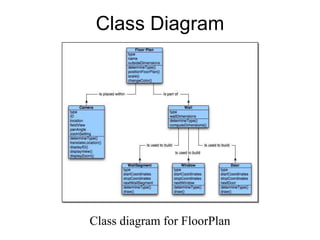
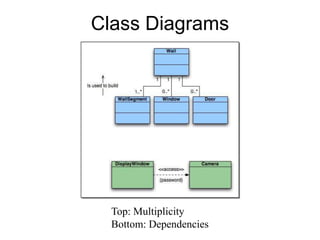
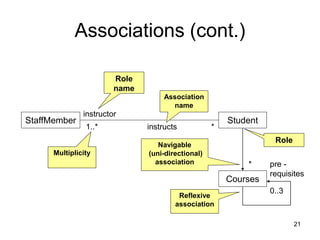
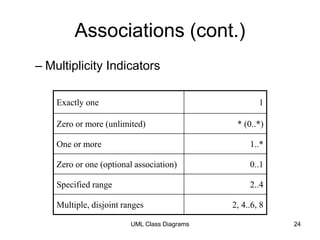
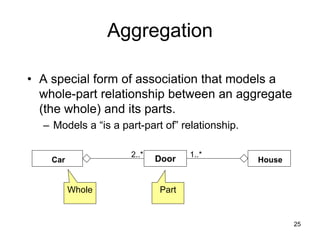
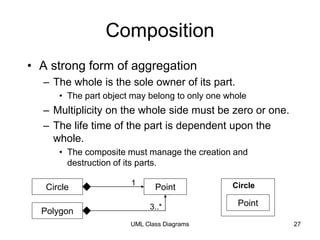
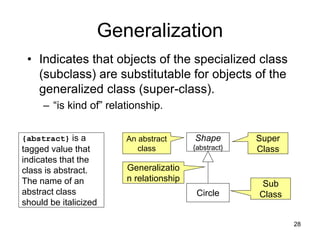
The document discusses class-based modeling and UML class diagrams. It defines what a class diagram is and its purpose of describing object types and relationships. Key elements of class diagrams are then explained, including classes, attributes, operations, and relationships like associations, generalization, and dependencies. The document provides guidance on identifying classes from problem statements and defining their attributes and operations. Examples of partial class diagrams are also included.