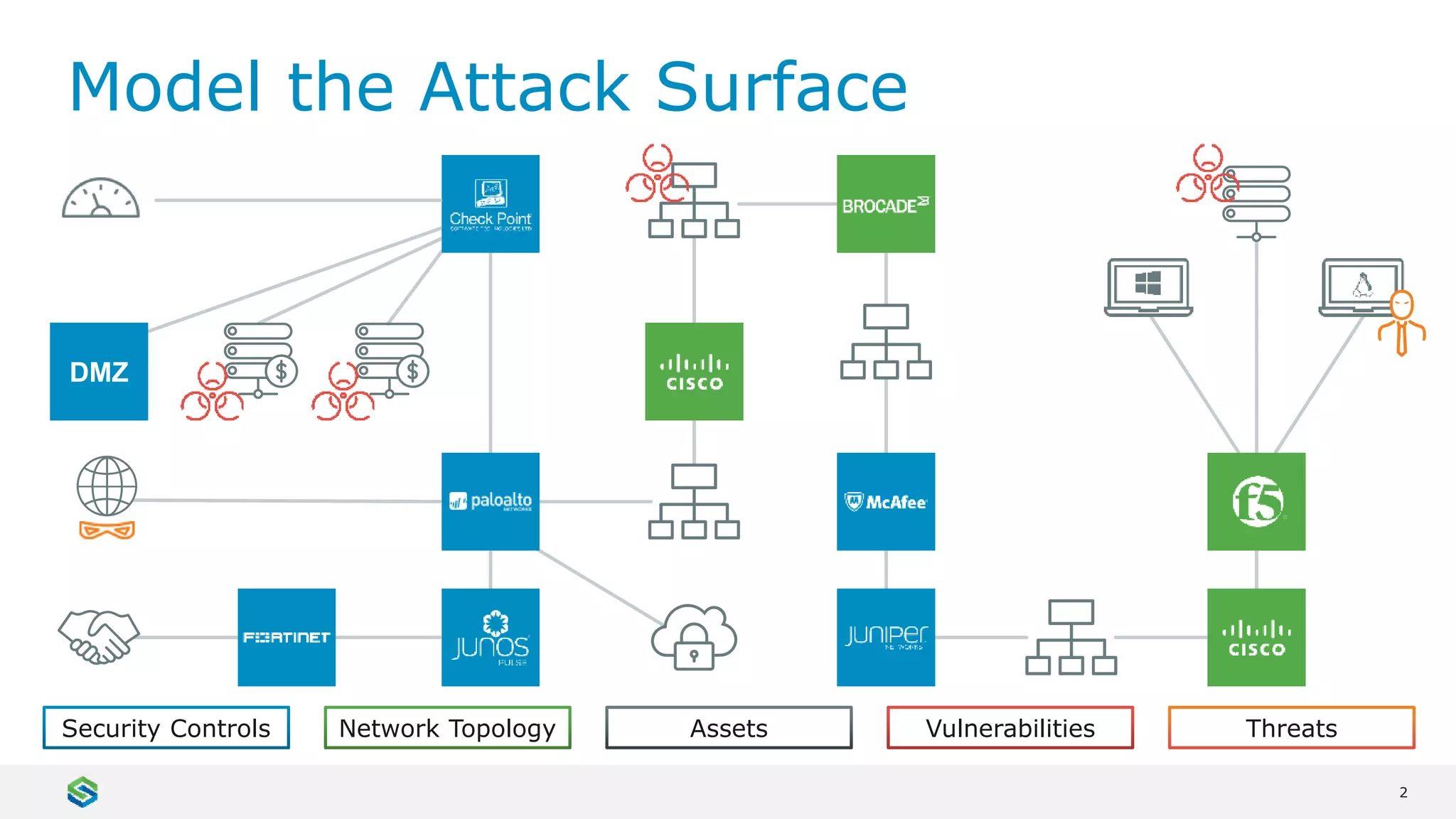
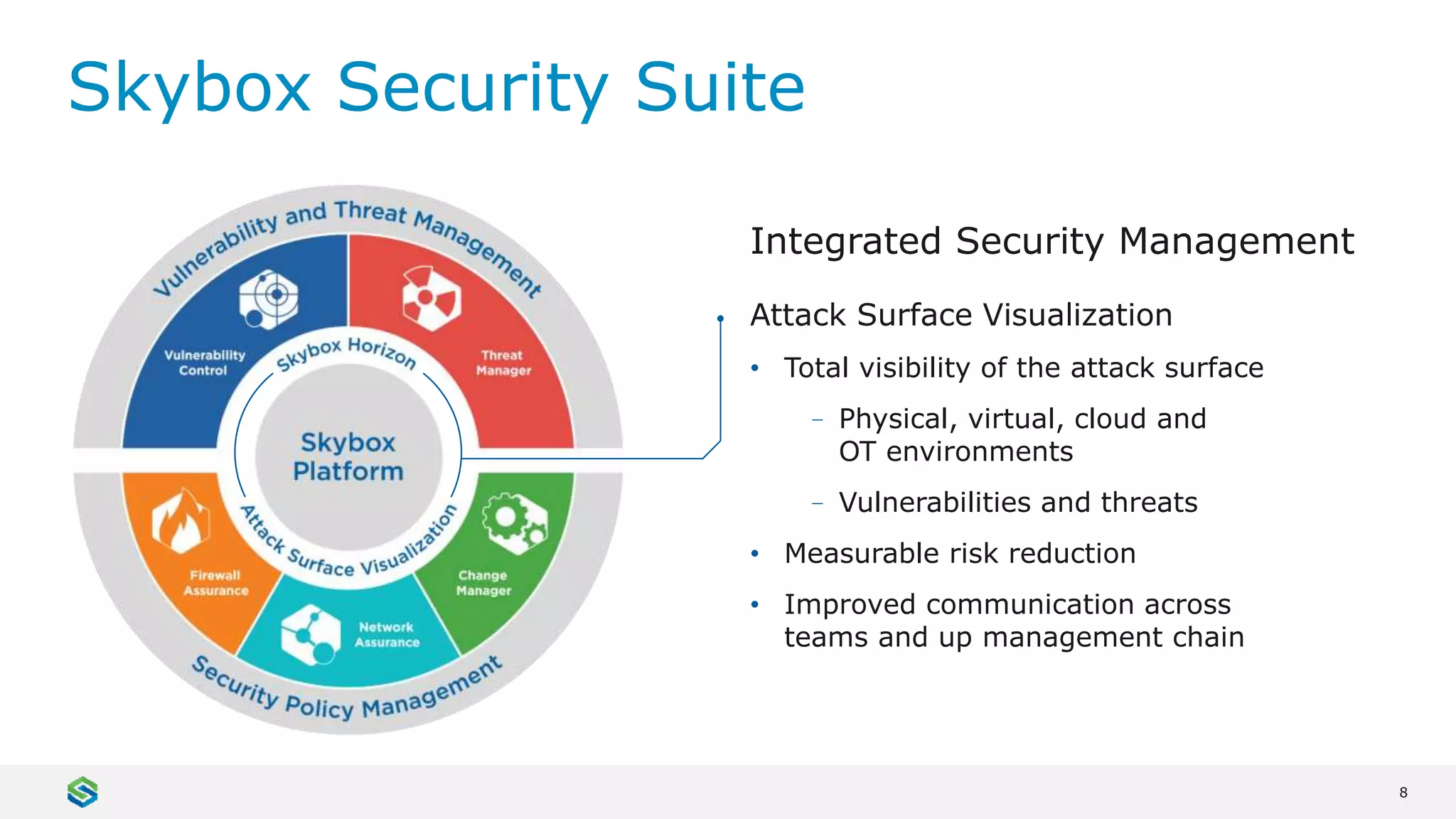
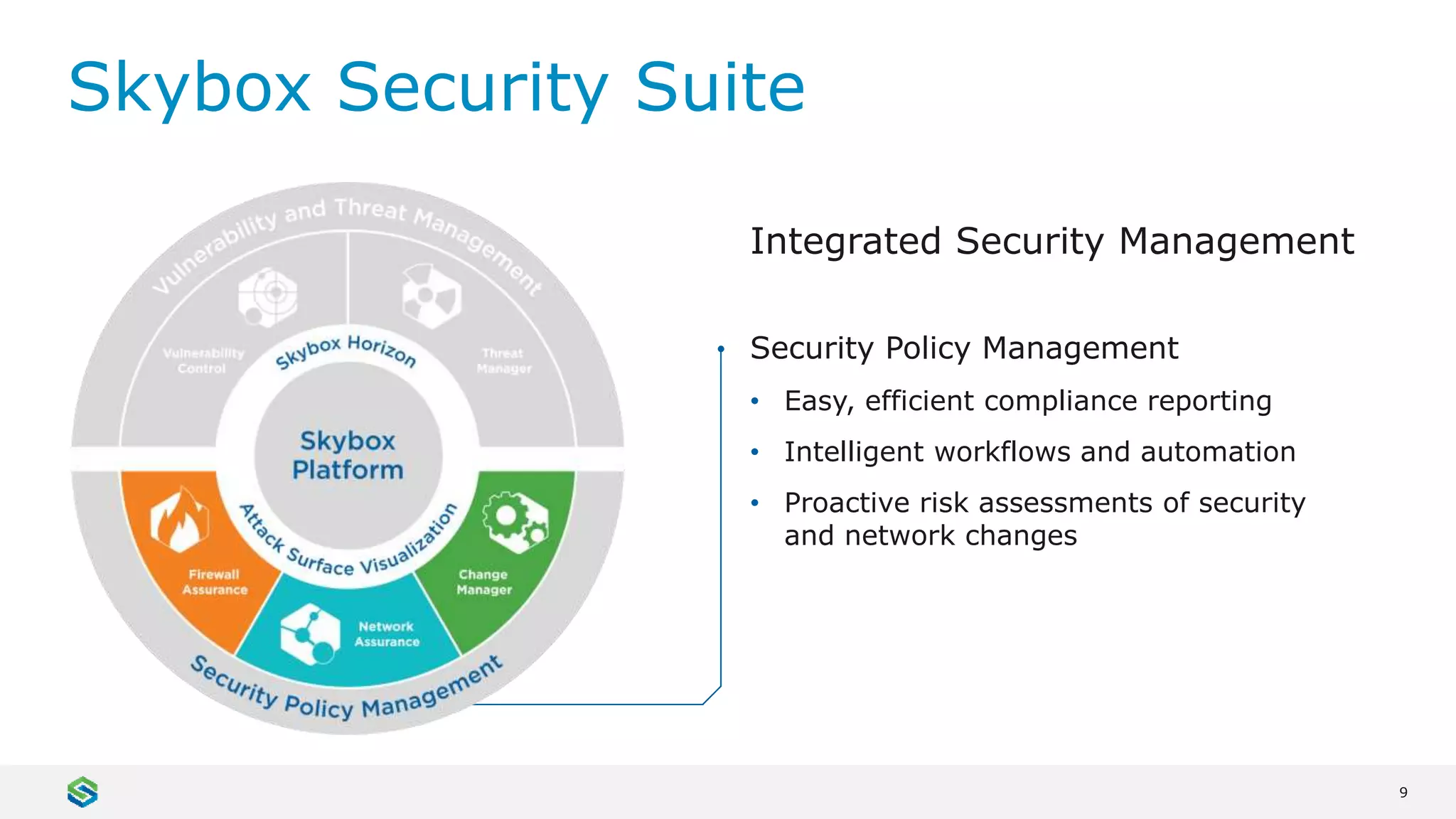
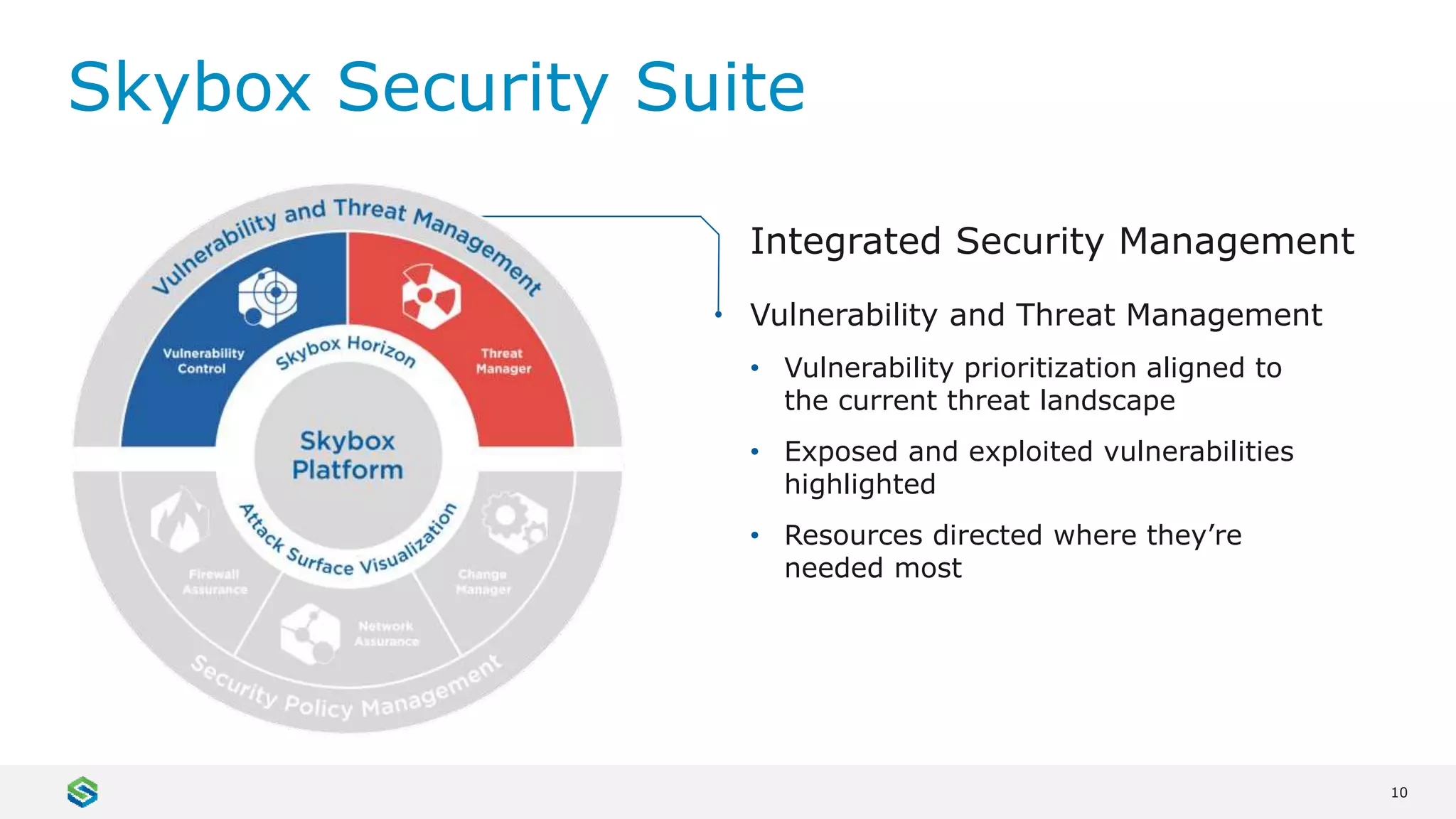
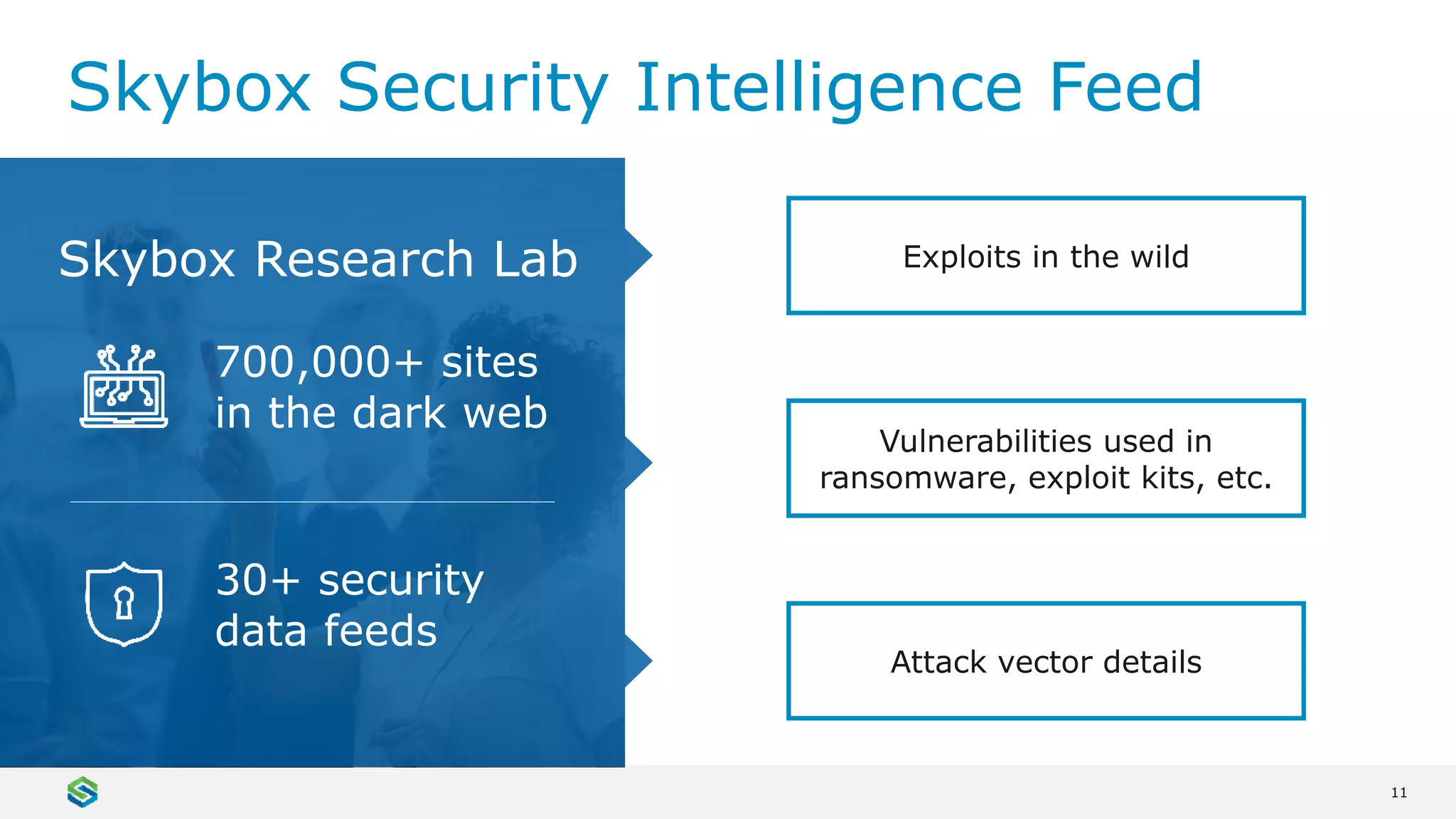
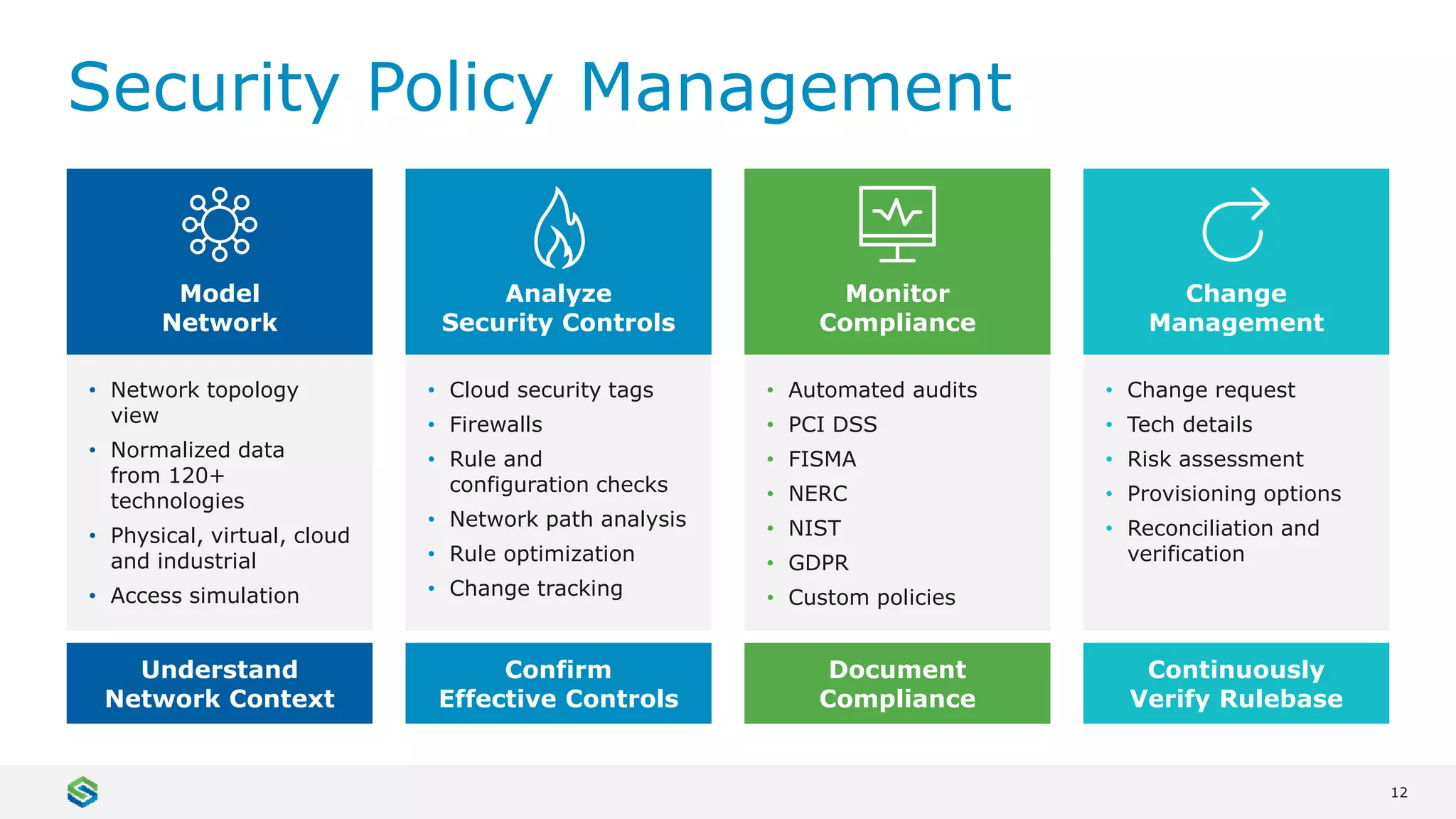
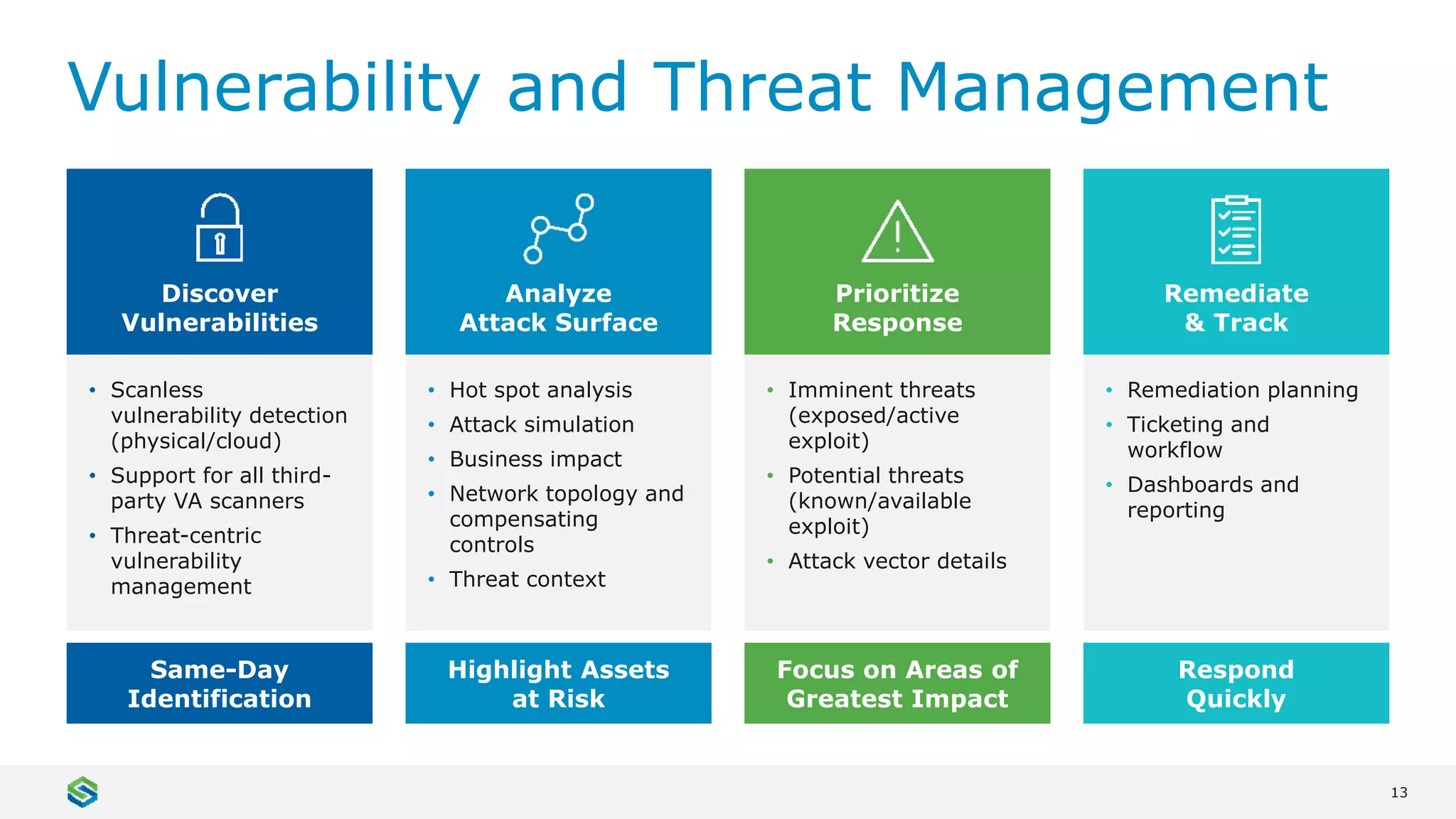
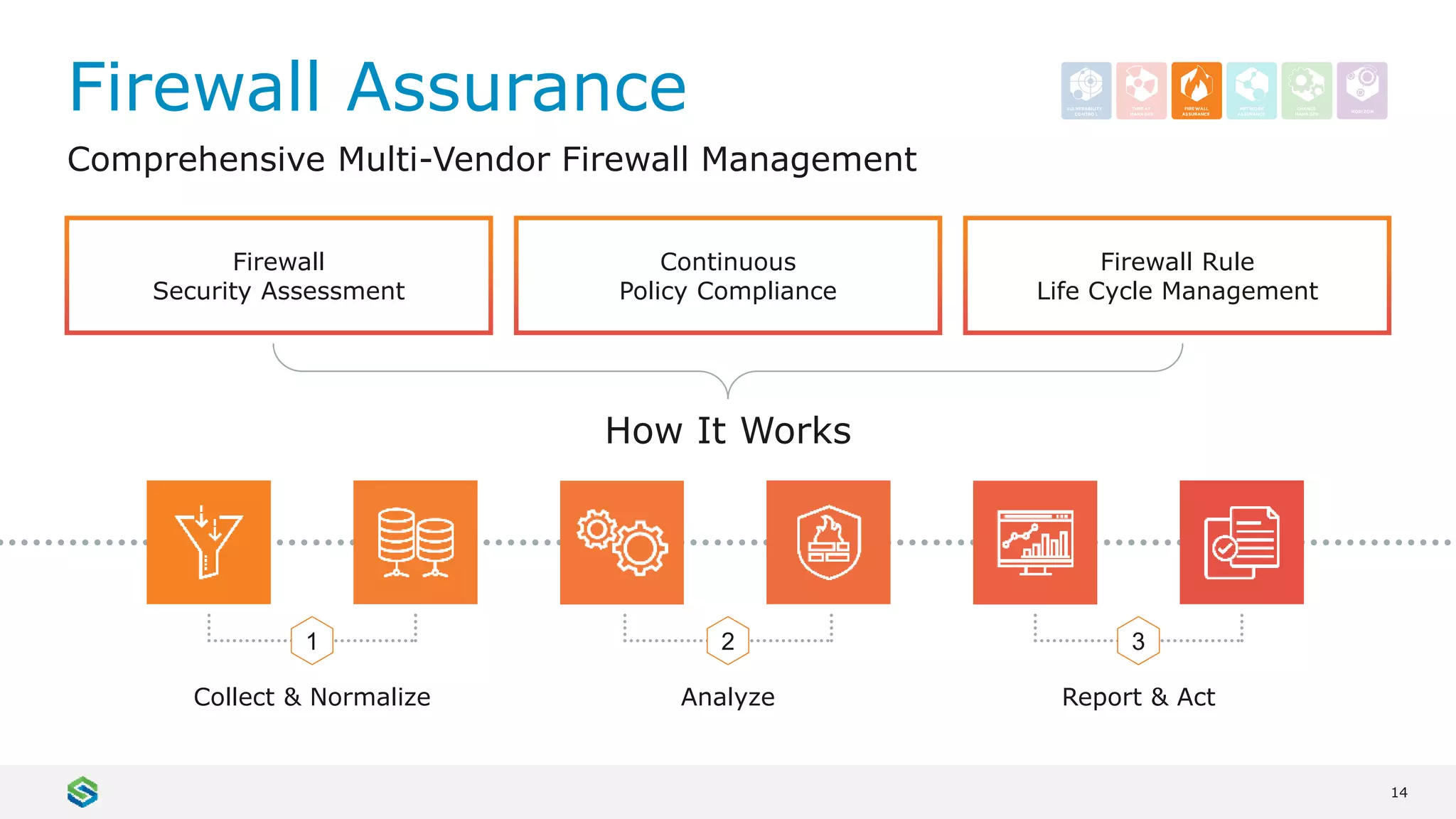
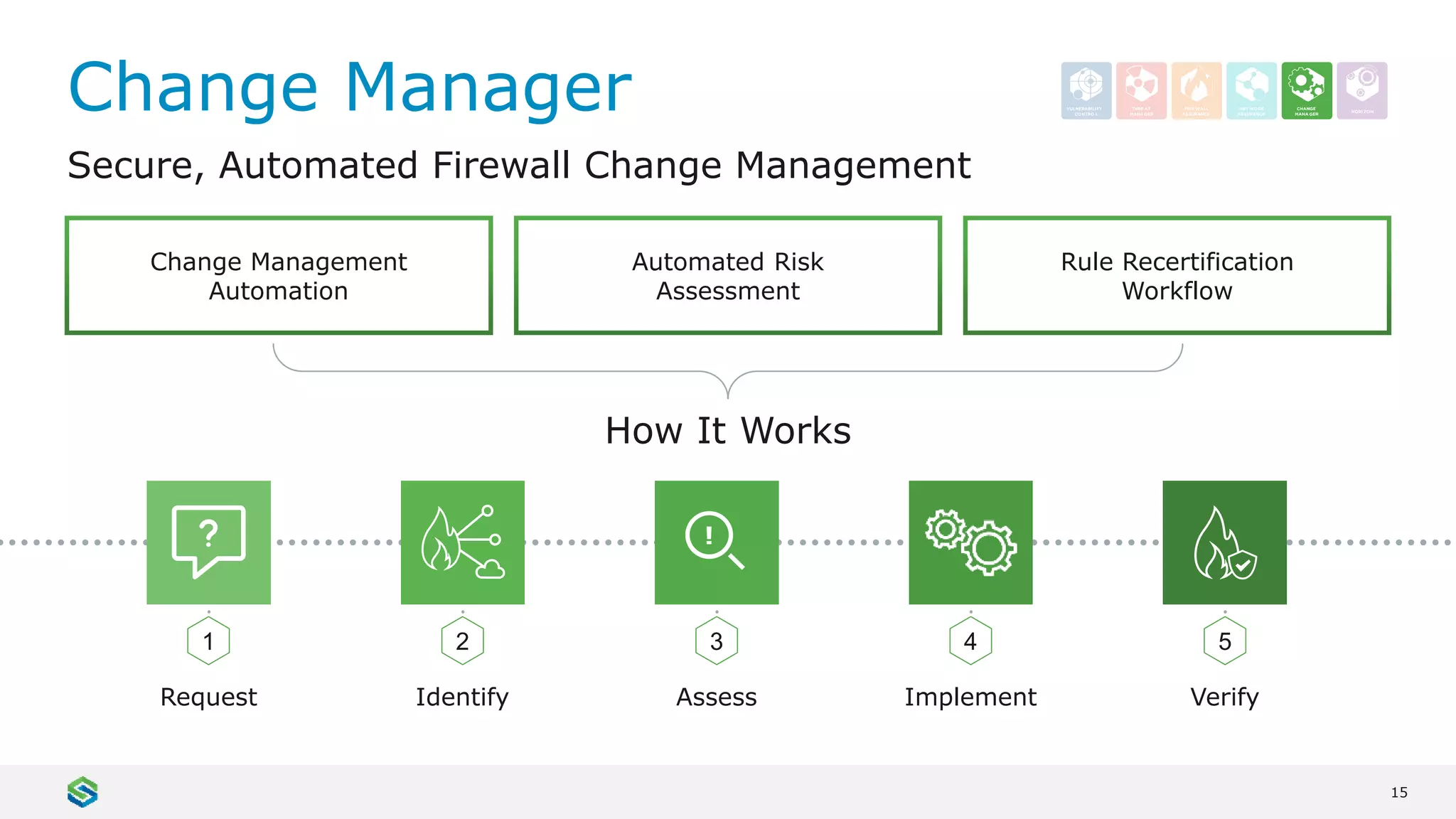
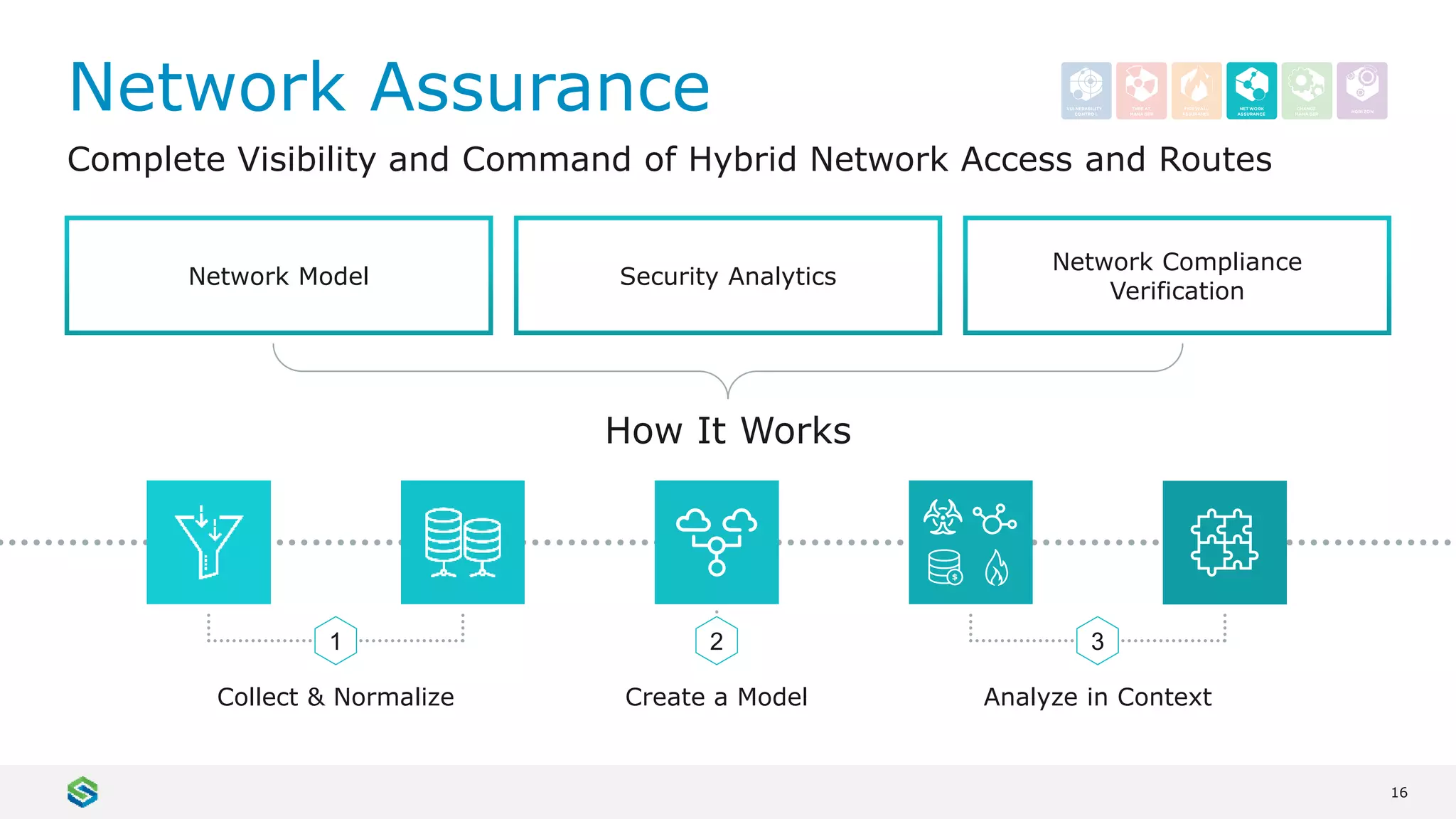
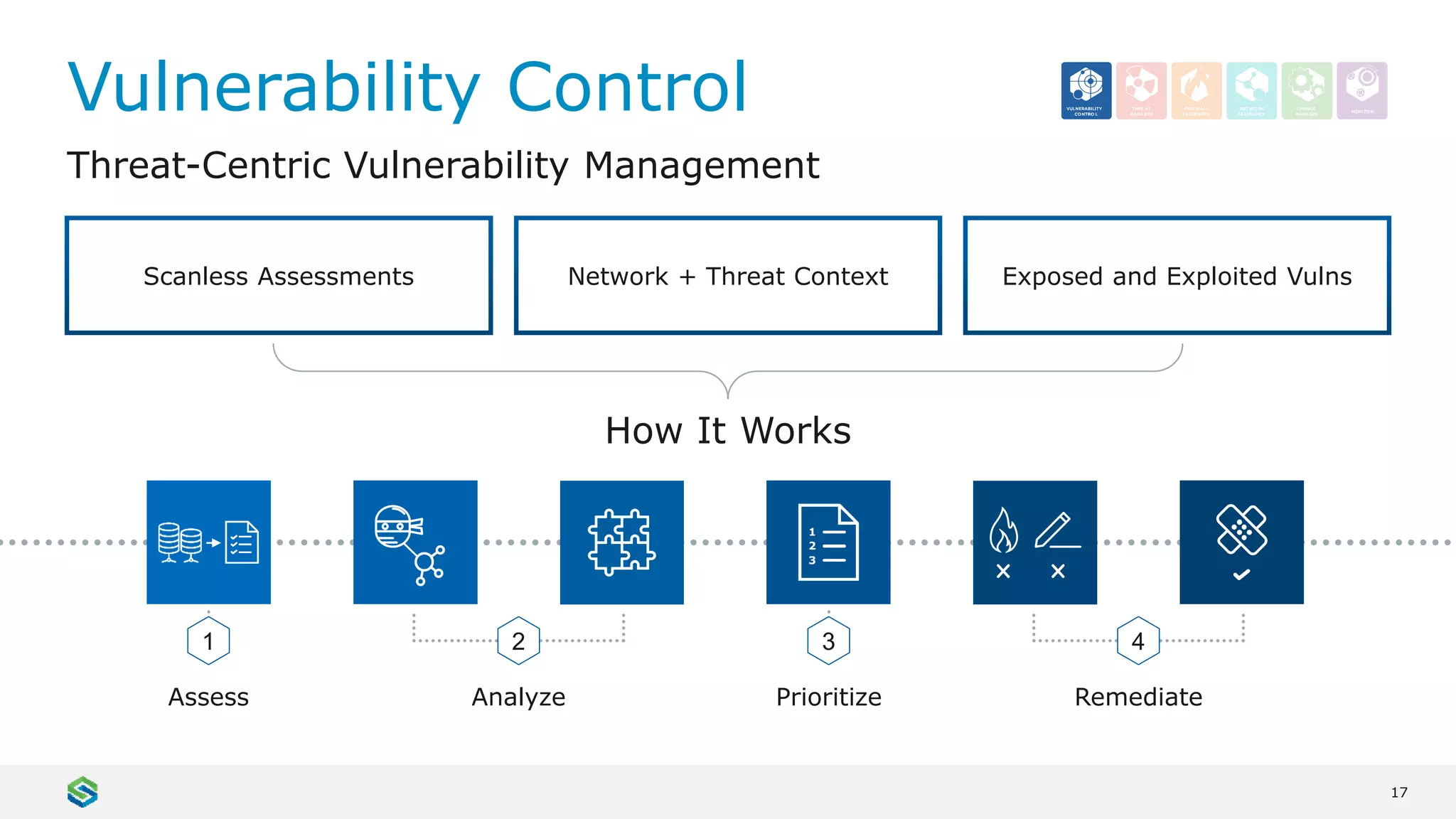
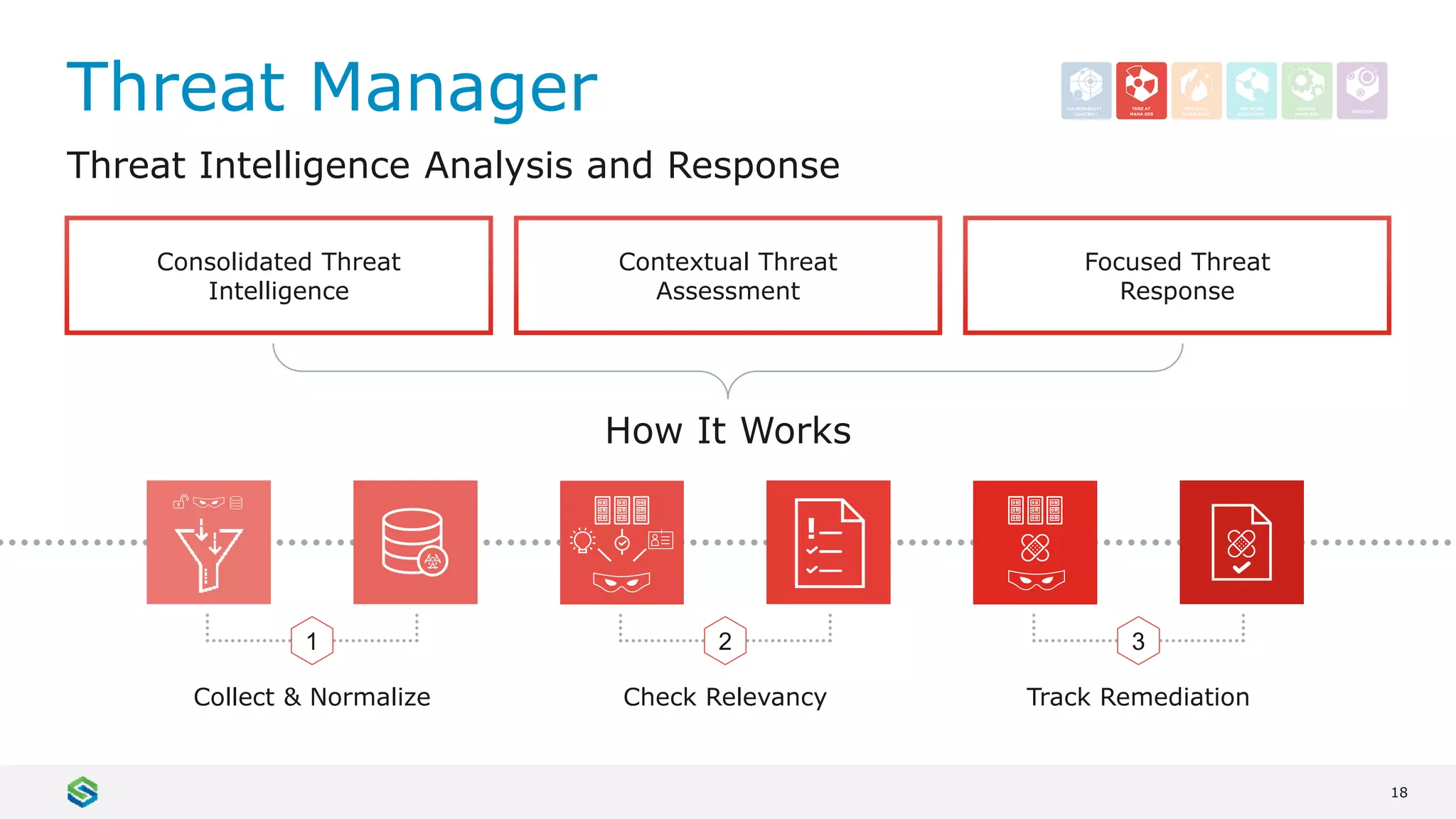
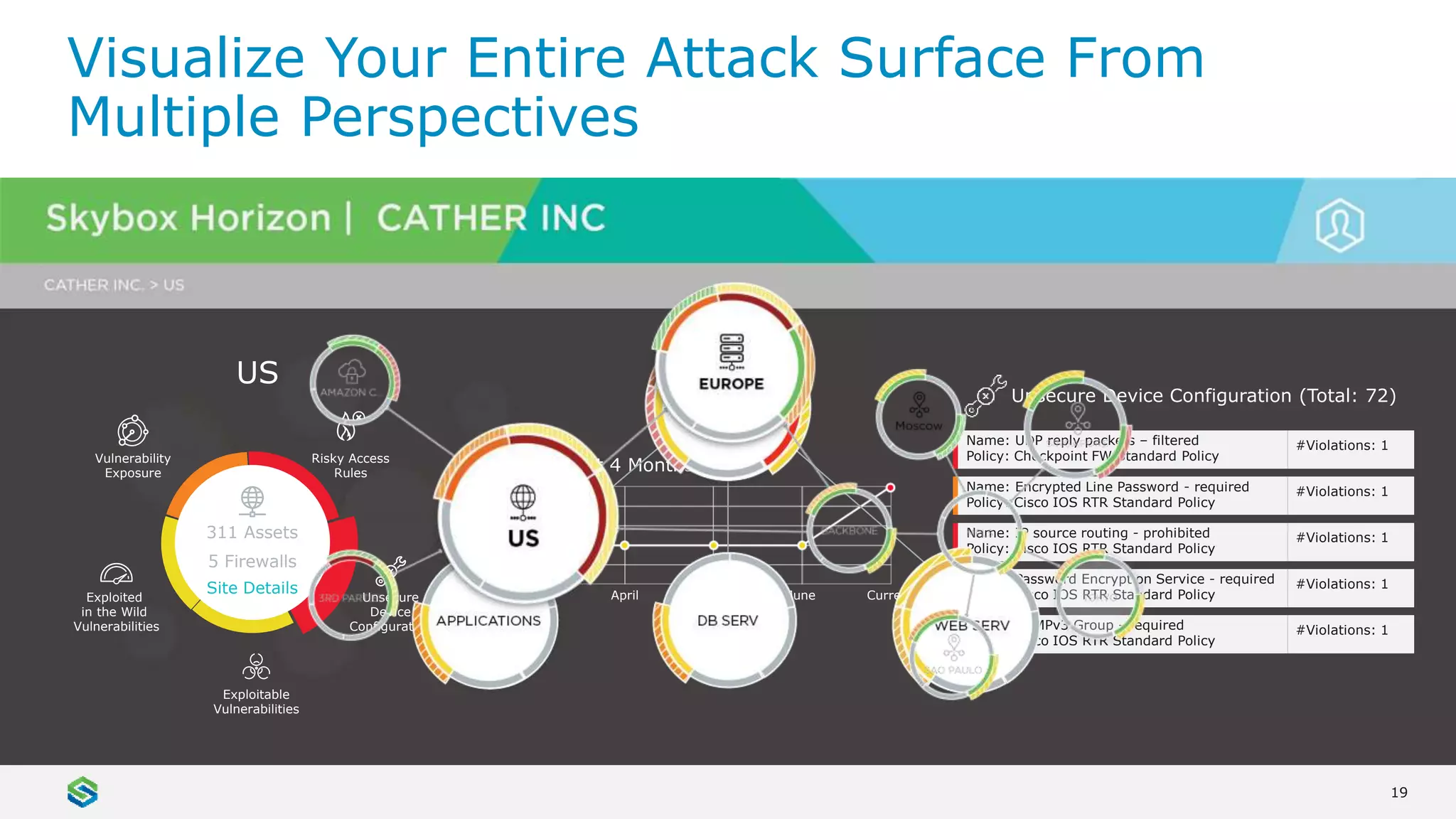
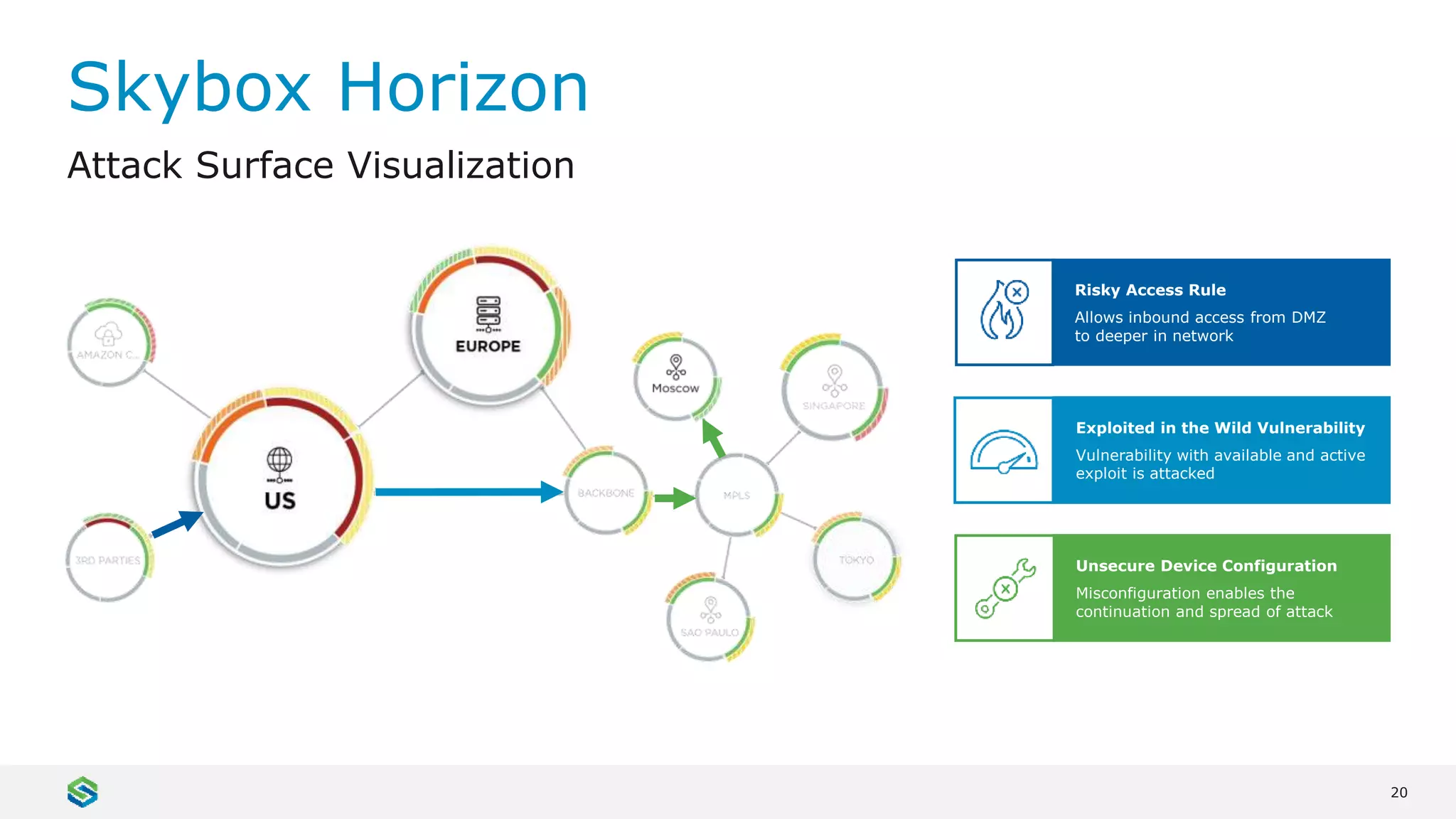
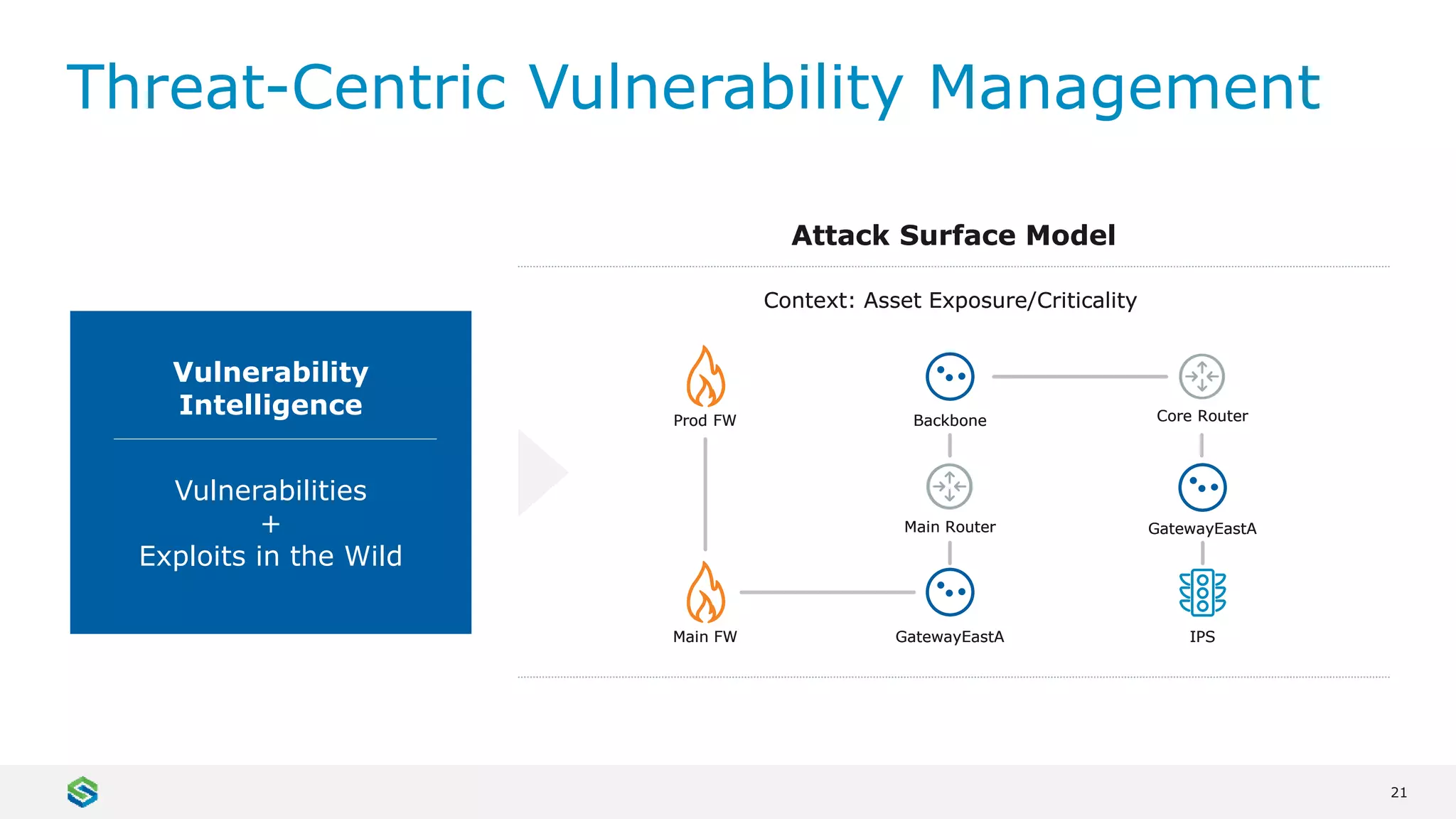
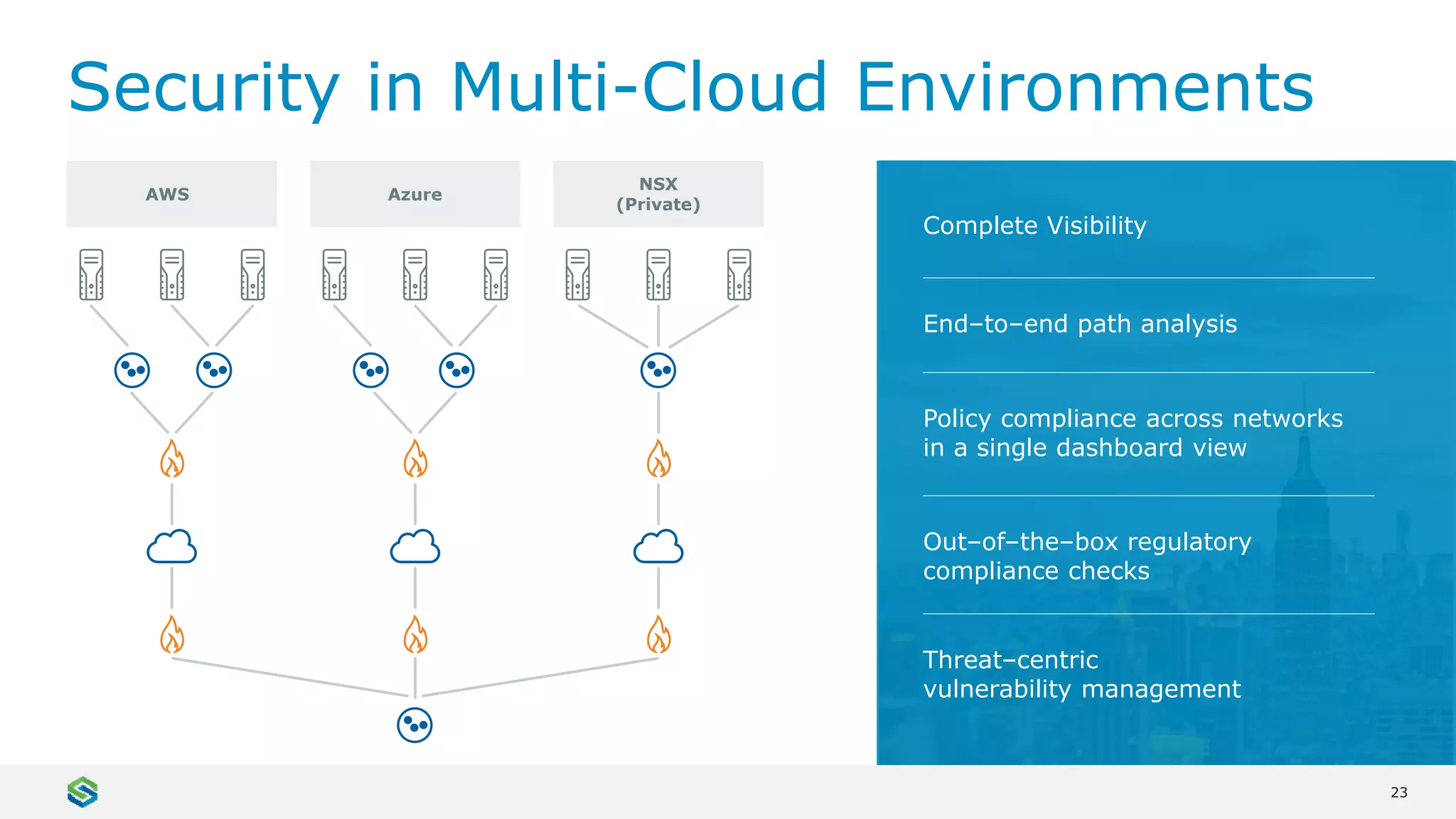
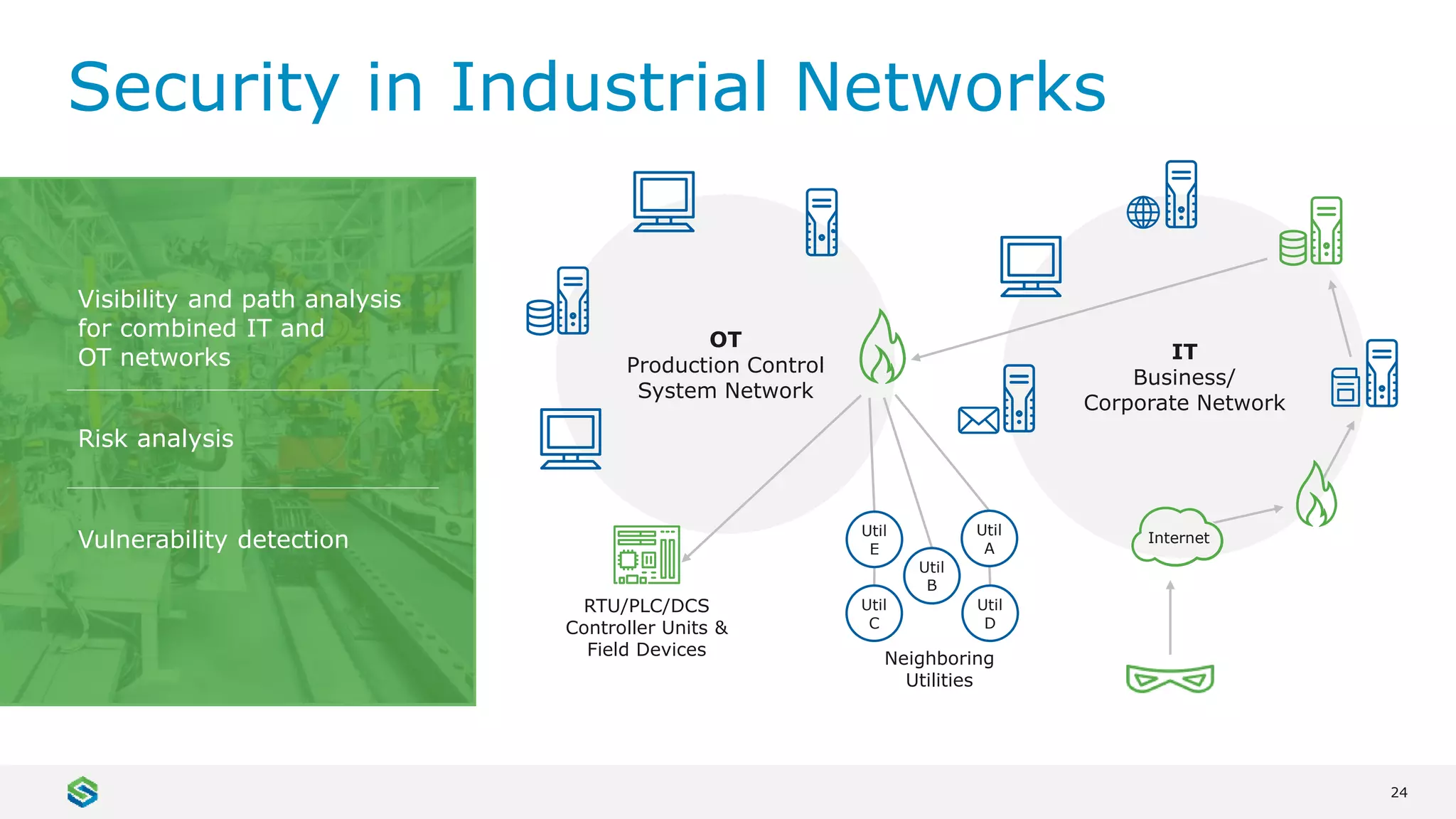
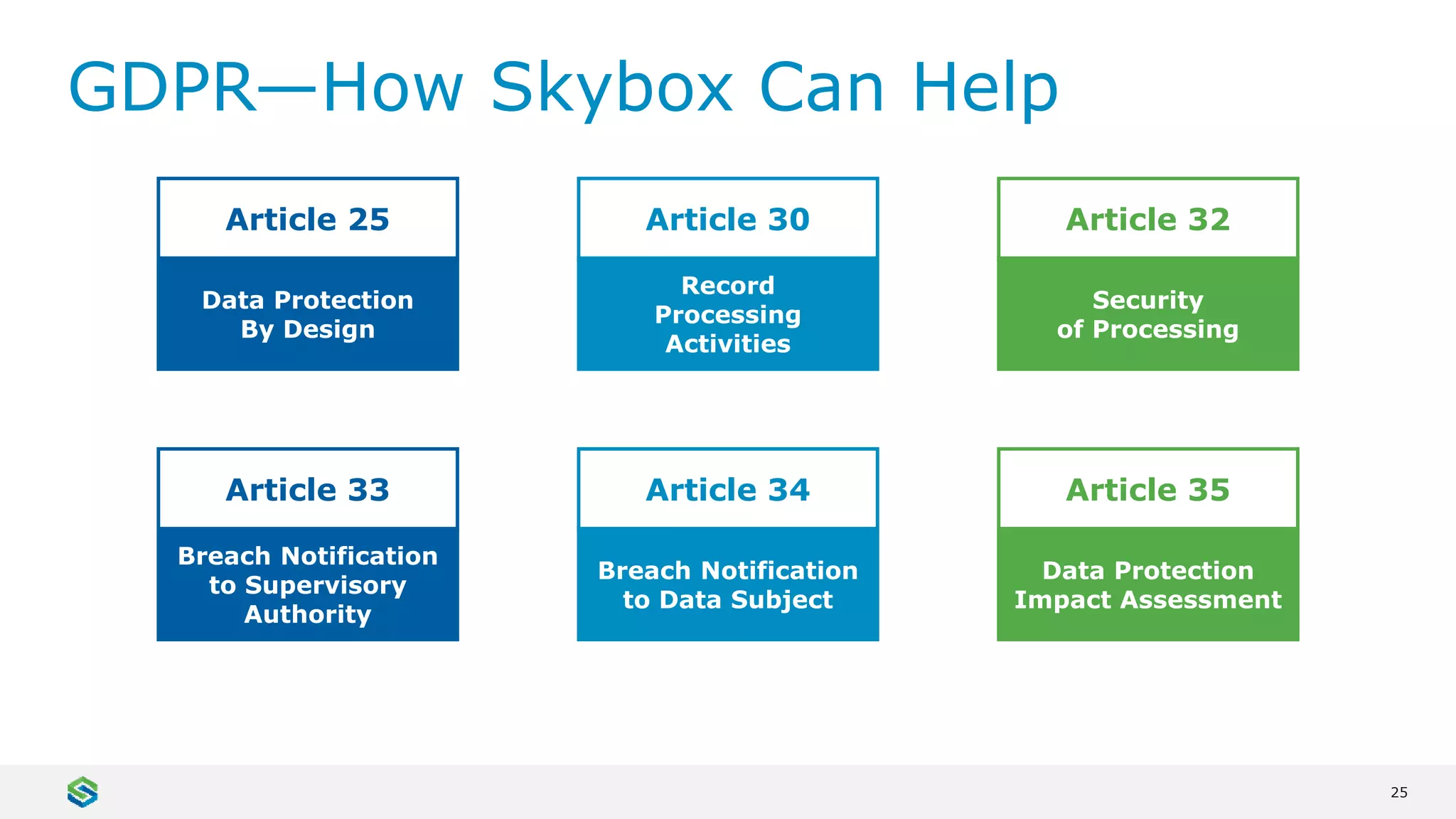
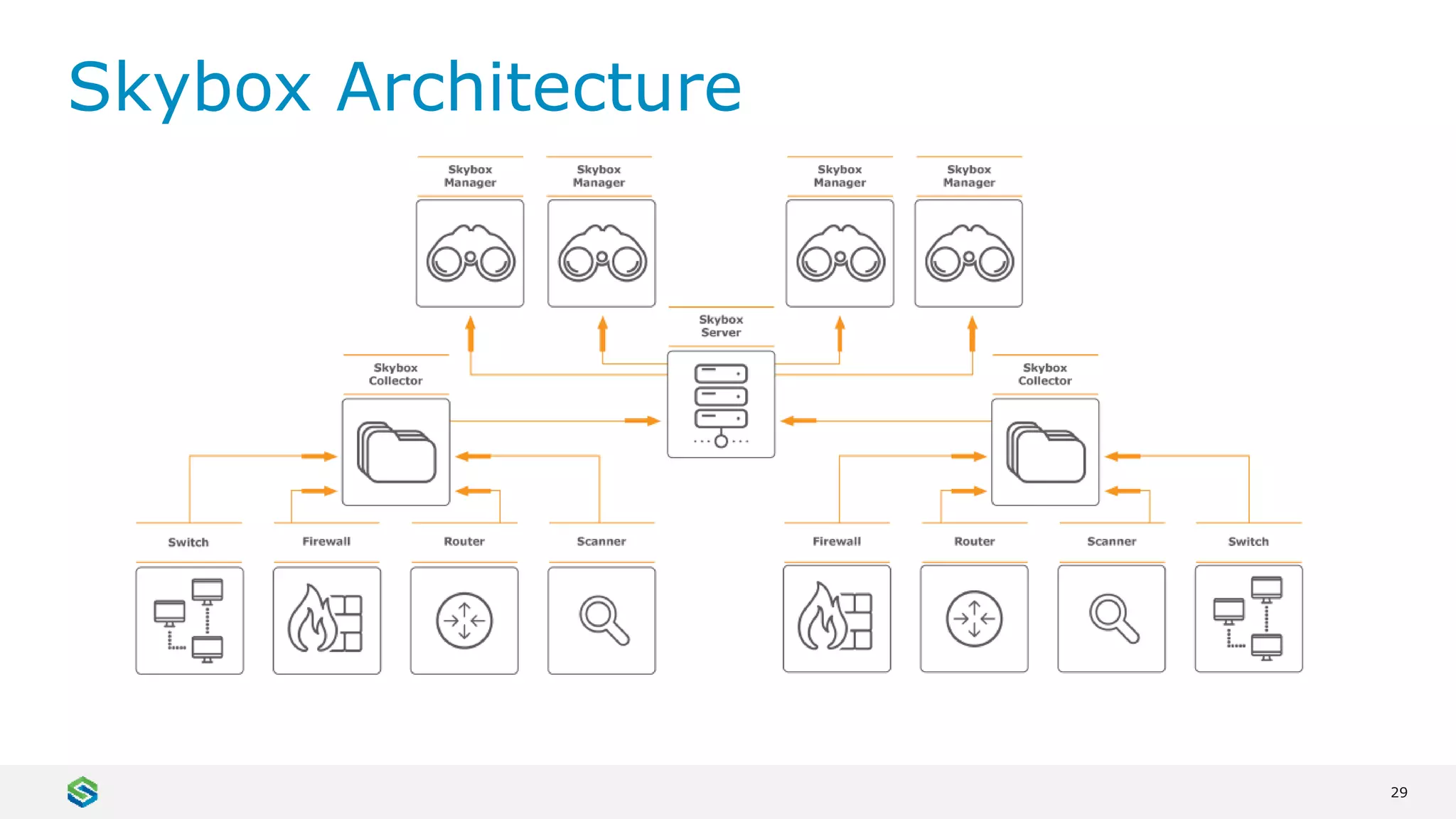
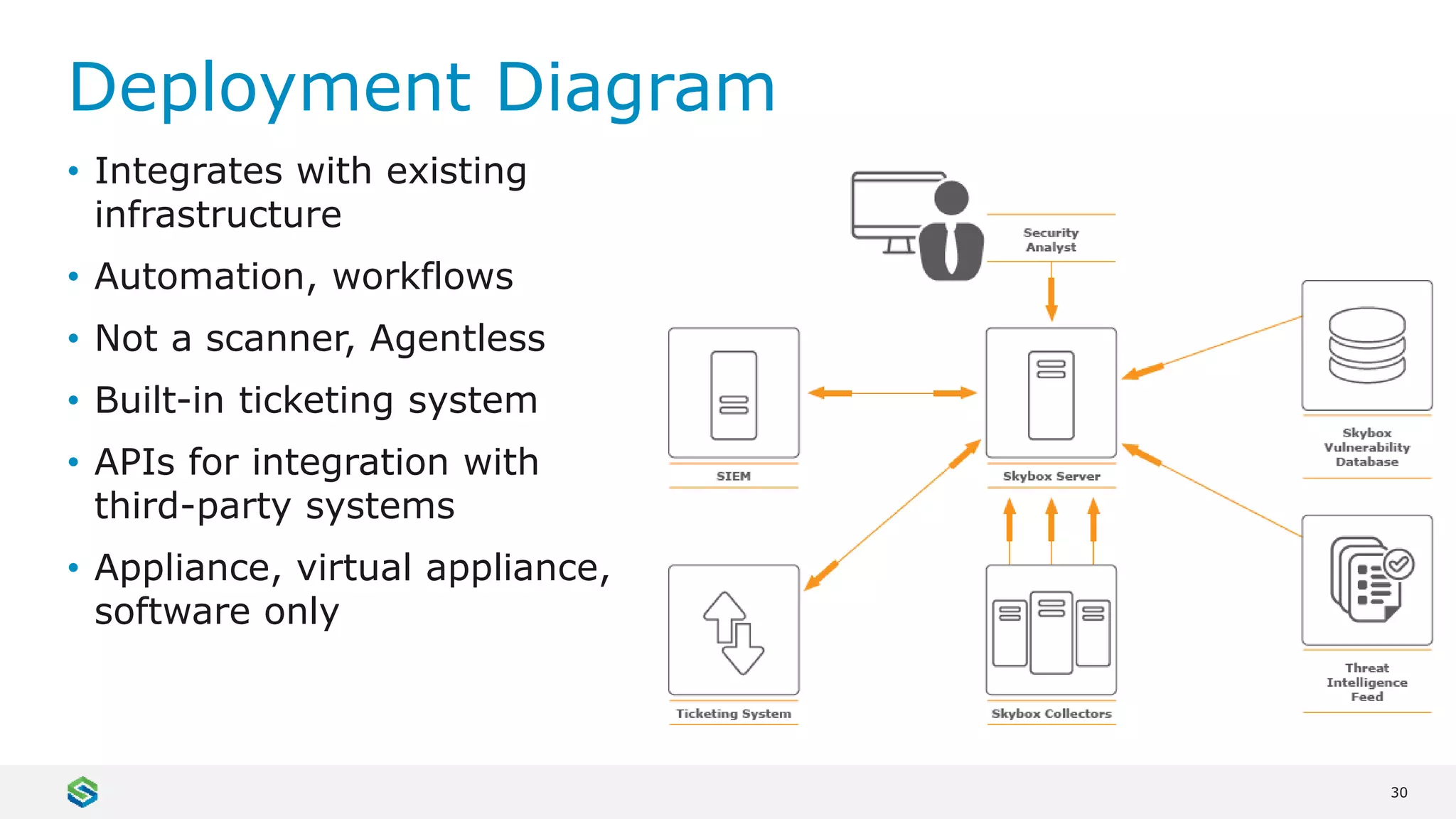
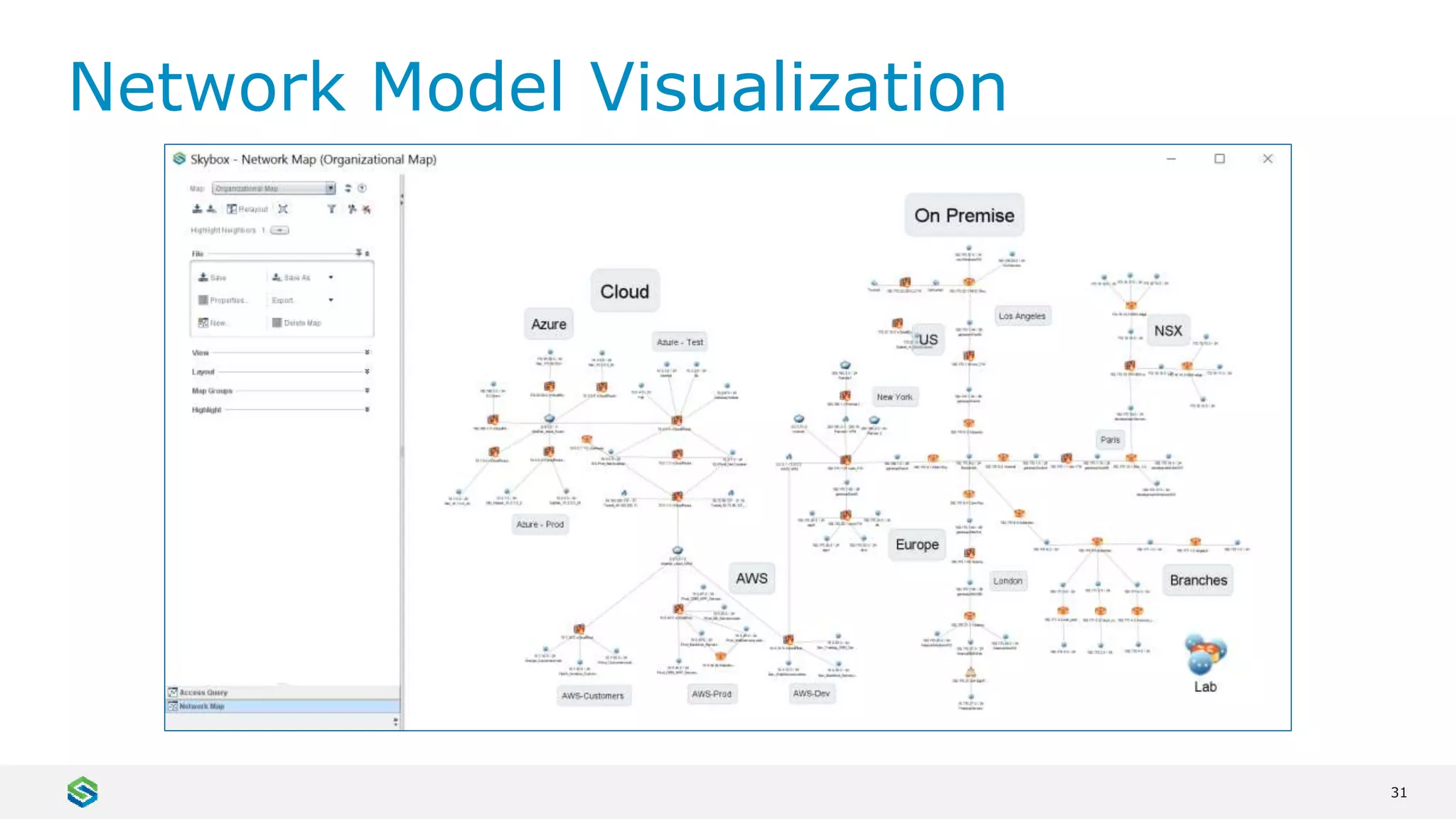
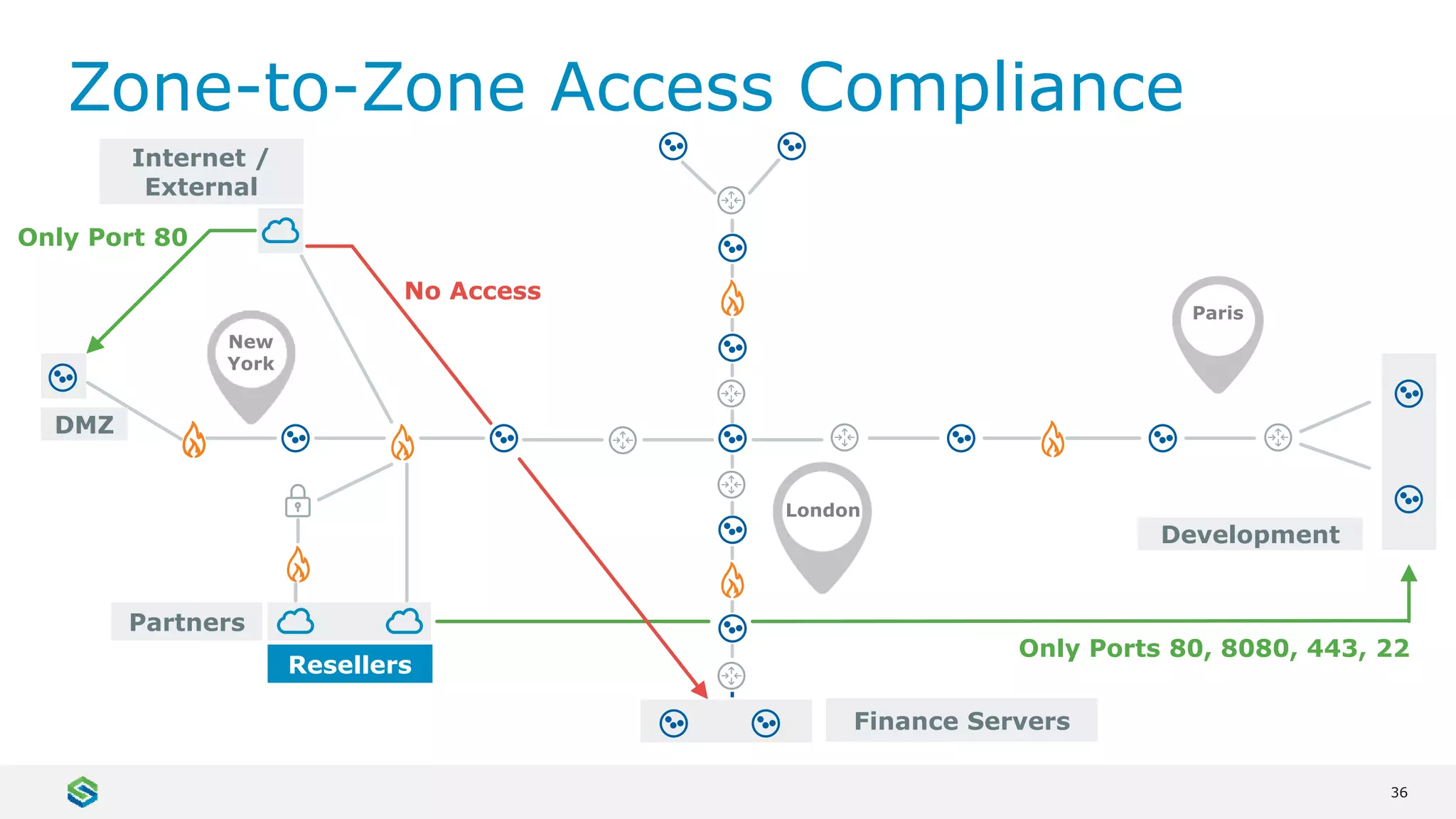
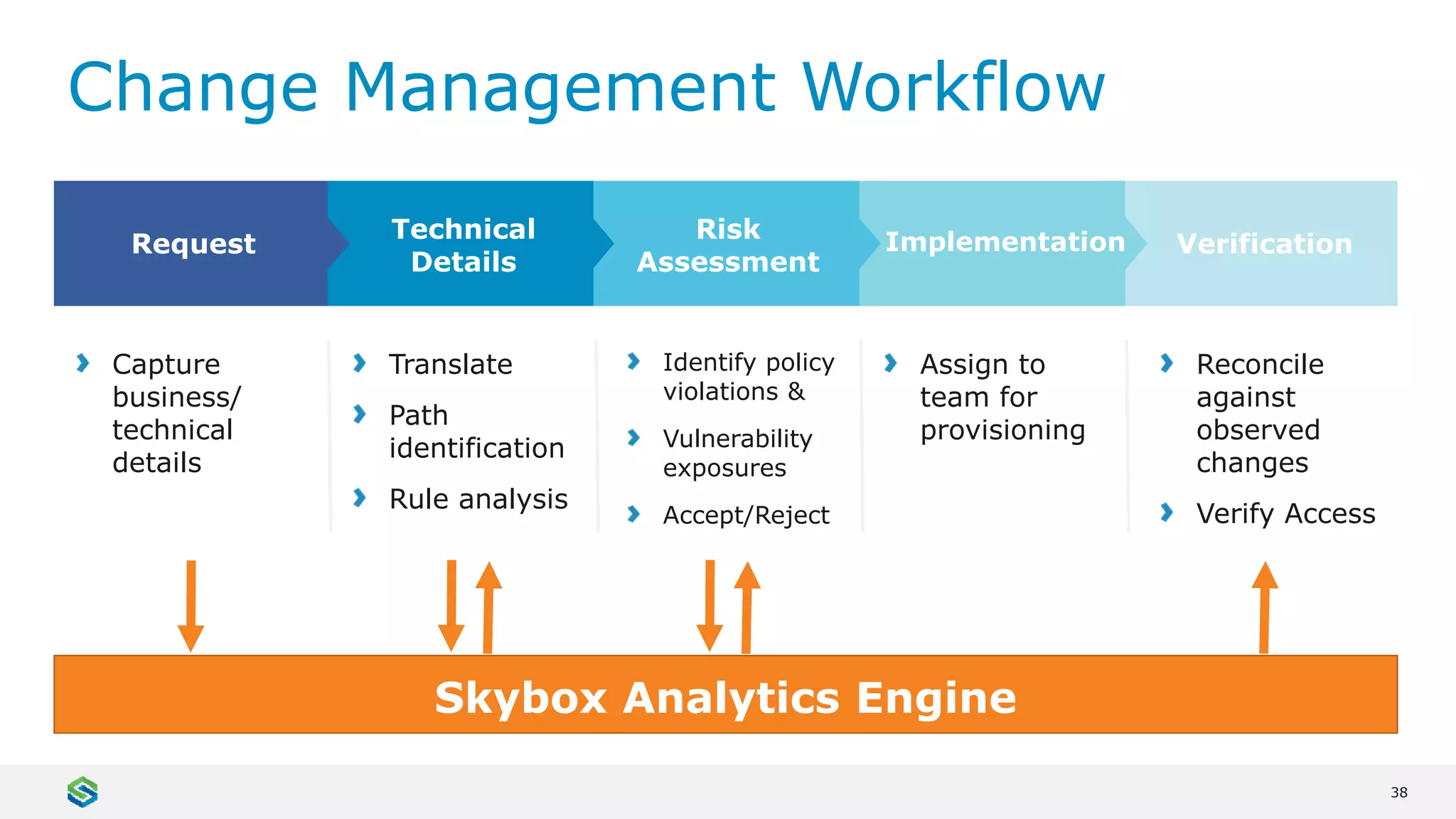
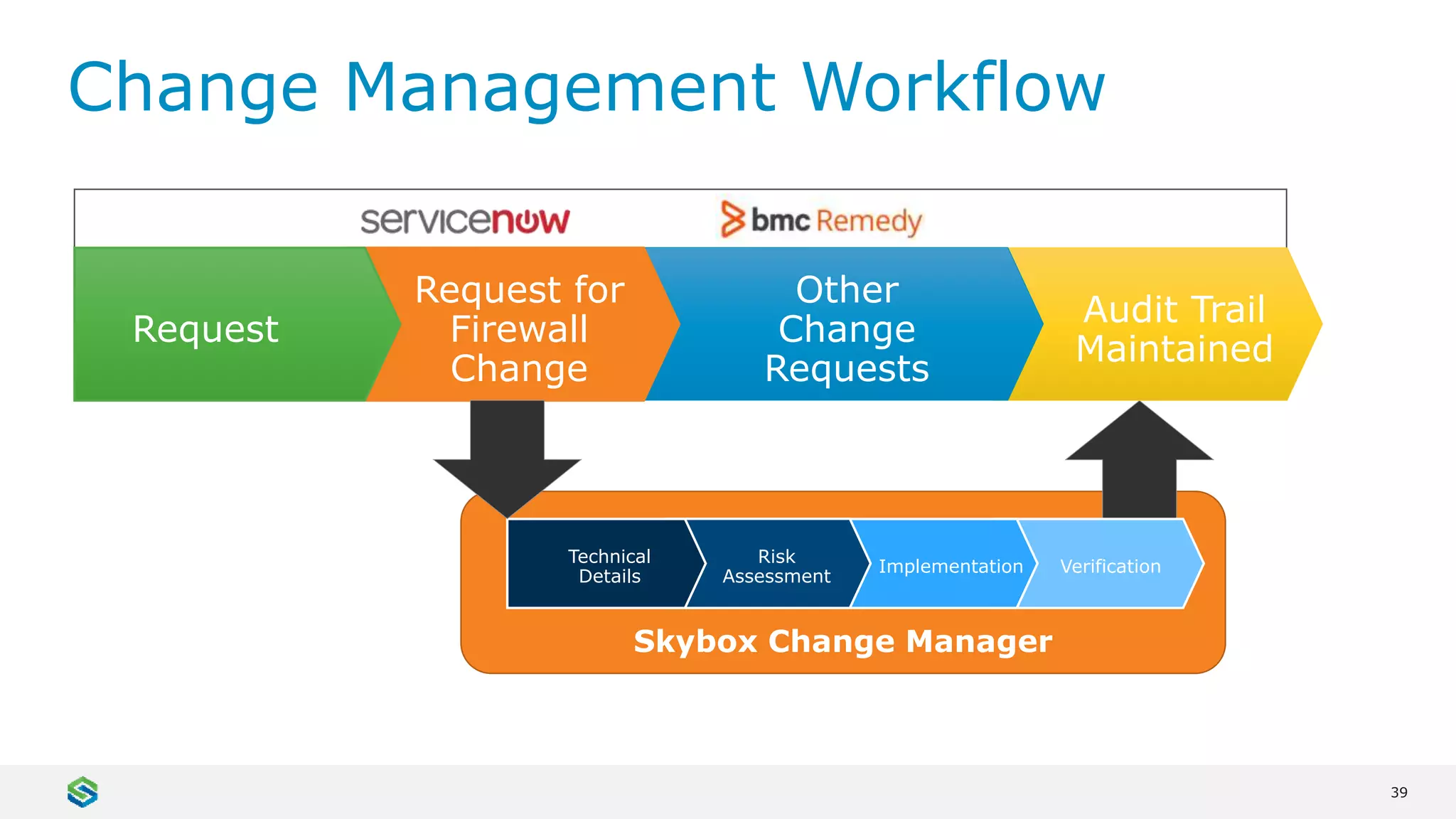
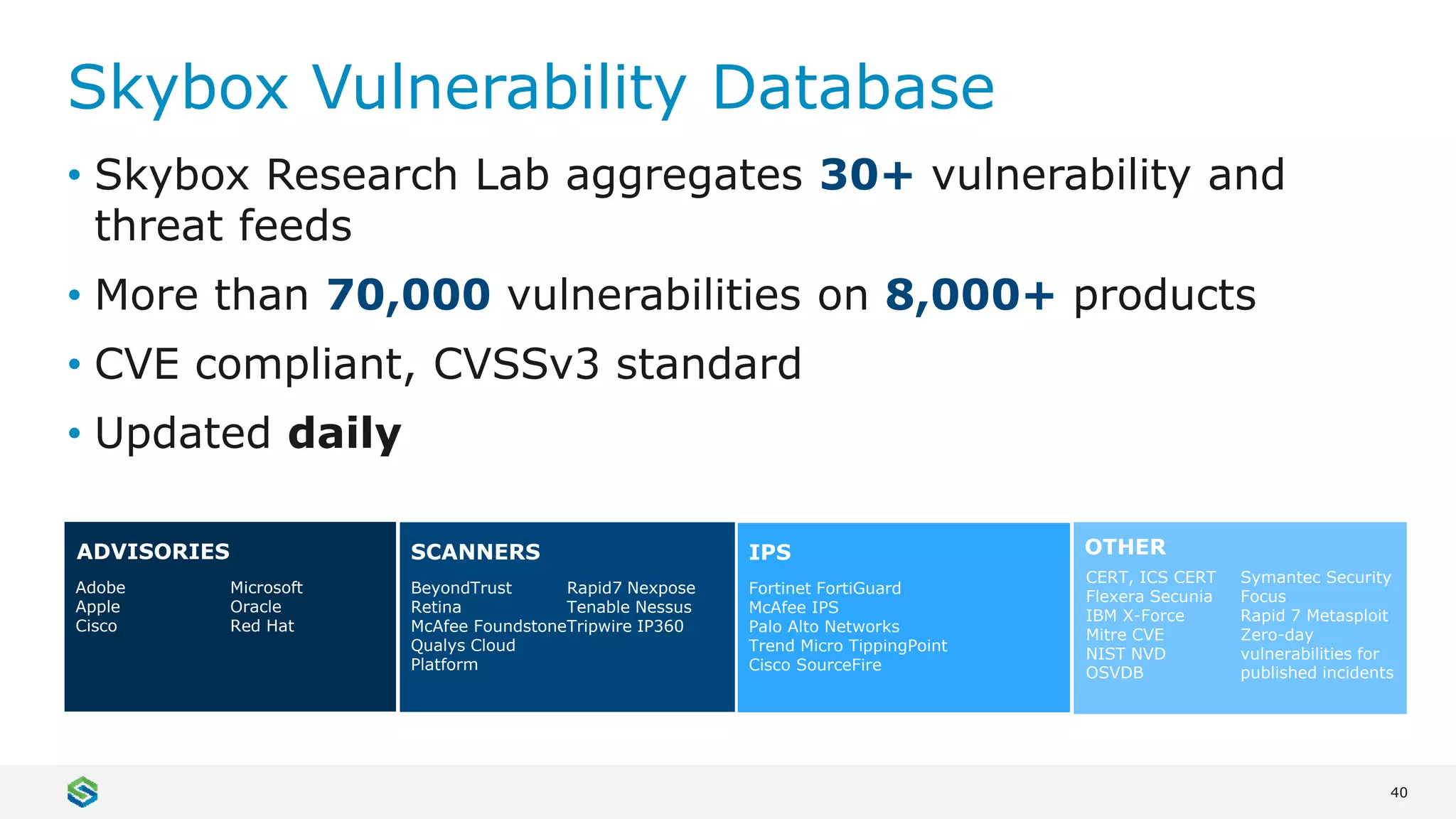
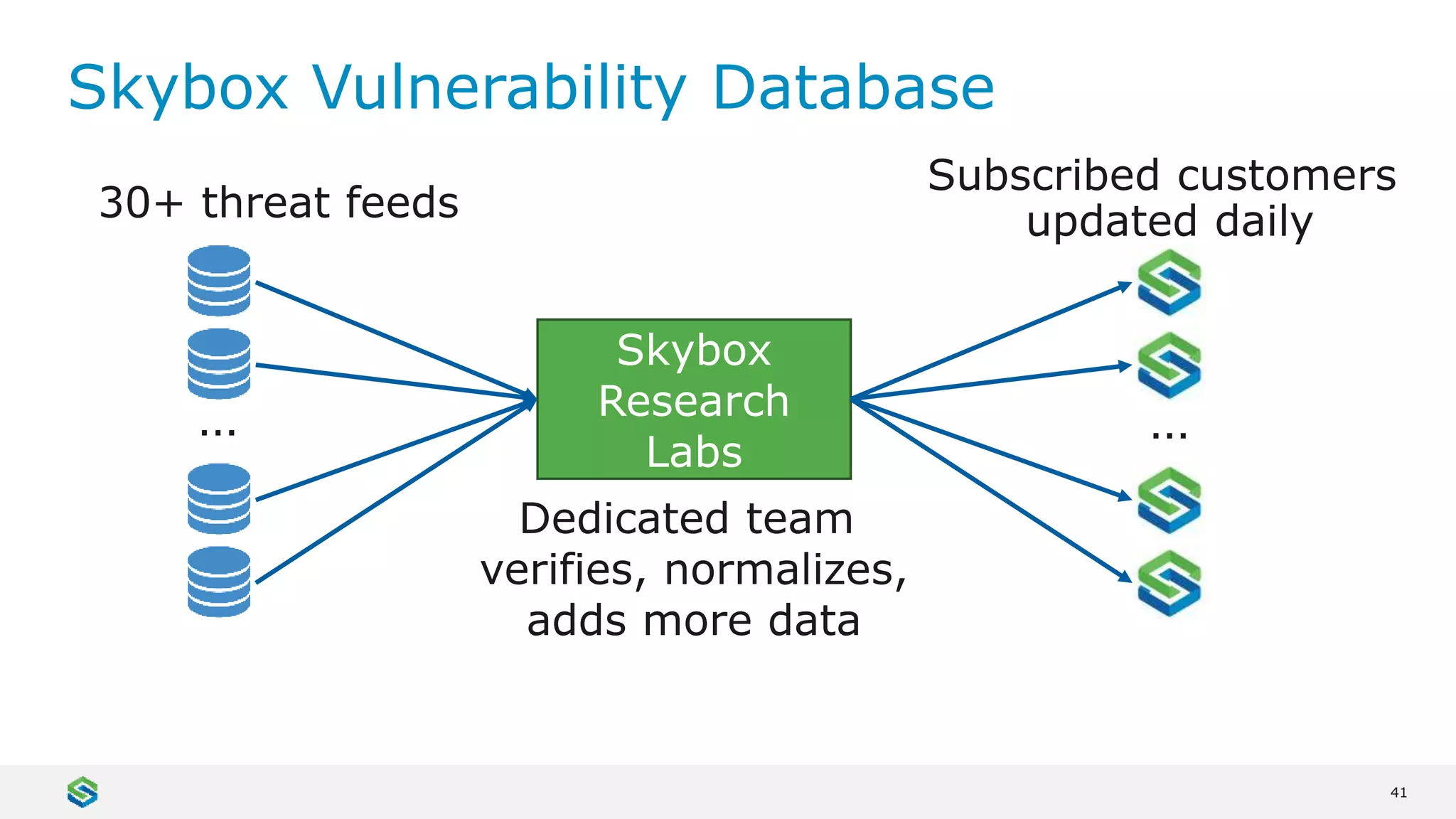
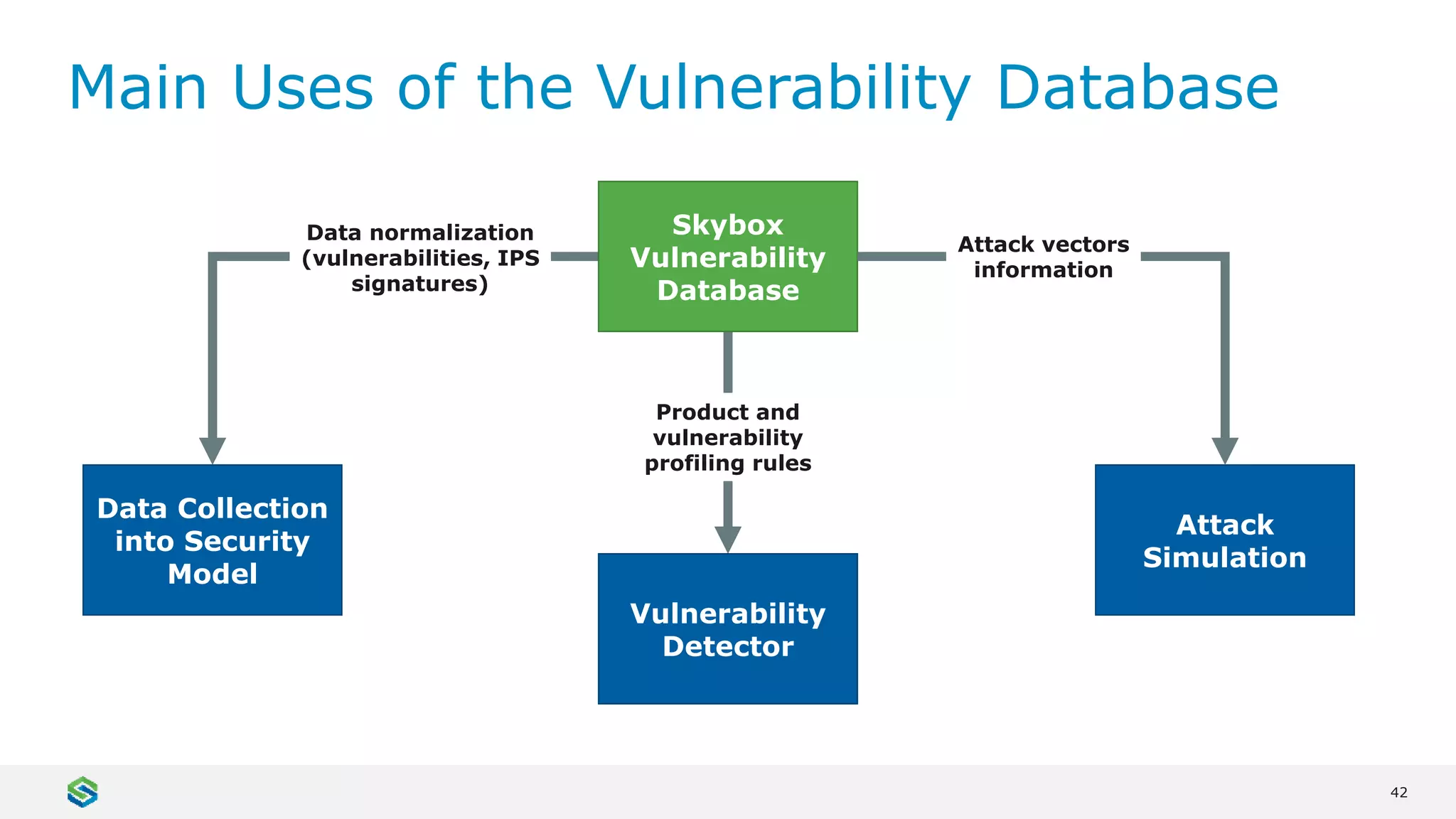
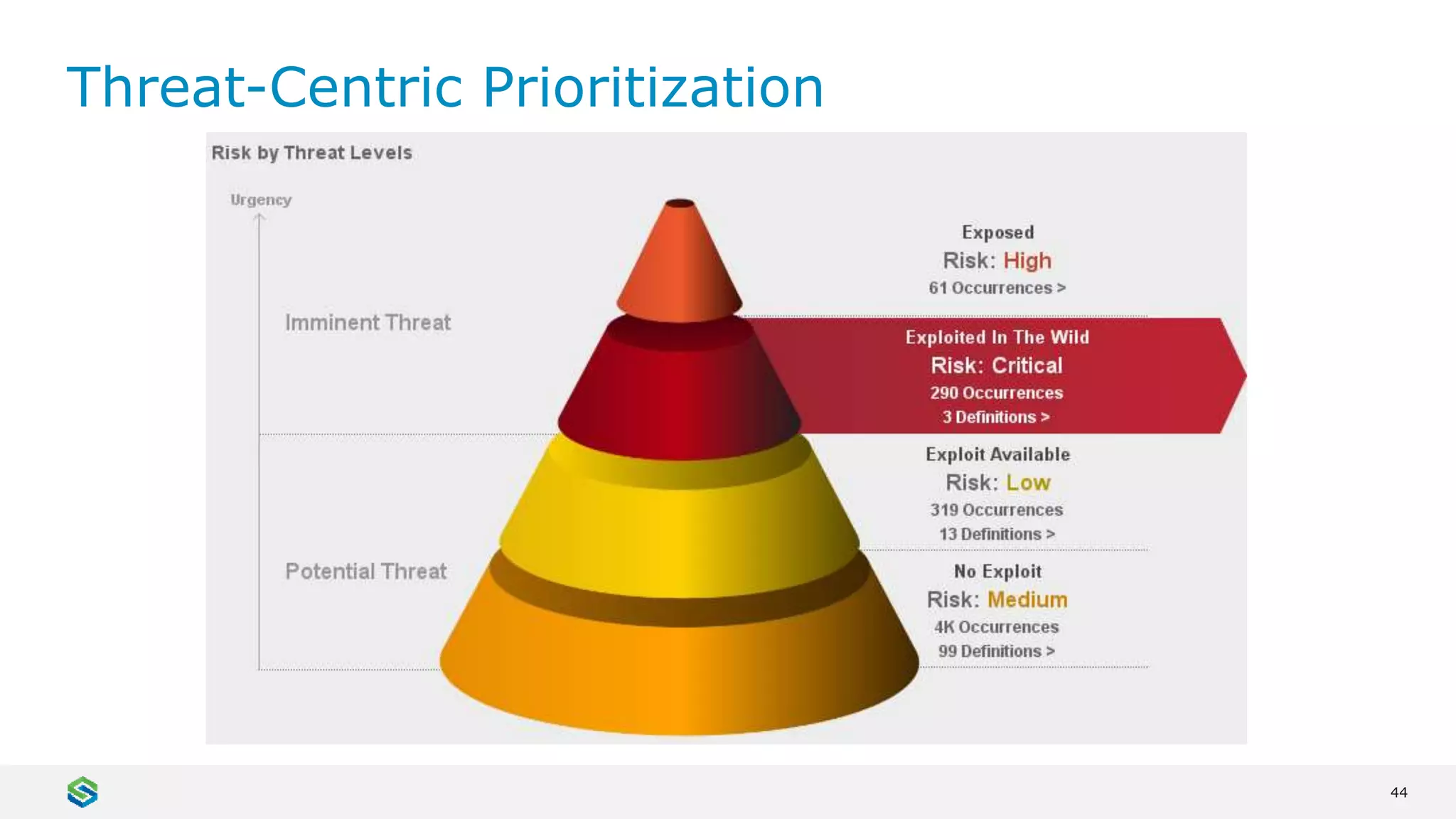
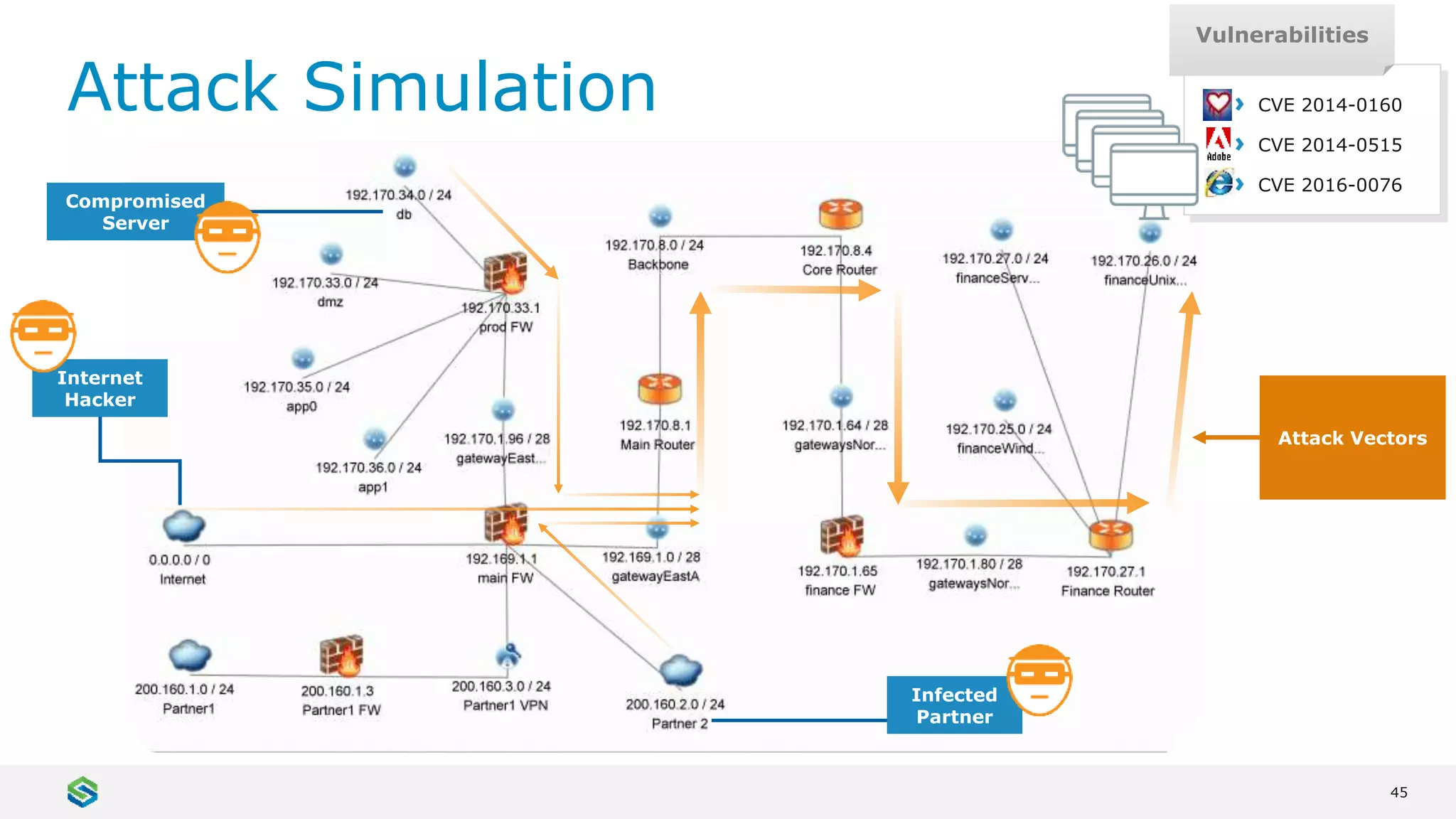
Skybox Security provides cybersecurity solutions including attack surface visualization, security policy management, vulnerability and threat management, and firewall assurance. Their solutions help organizations gain visibility of their entire IT and OT networks across physical, virtual, cloud and industrial environments. They identify vulnerabilities, misconfigurations, and risky access rules. Skybox integrates with over 120 technologies and has over 700 active customers globally across various industries.