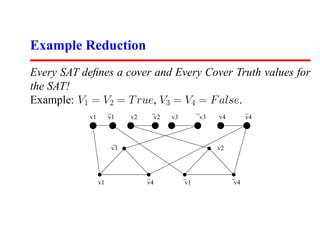
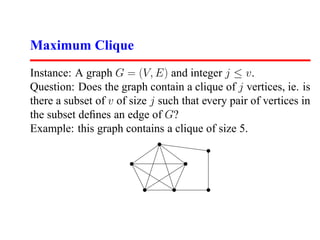
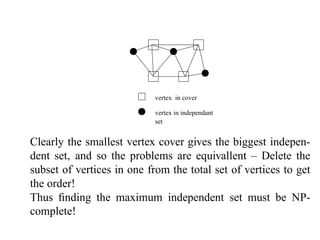
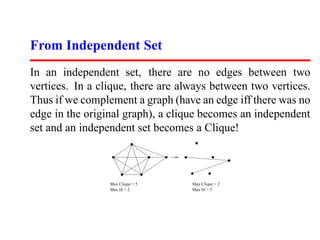
This document summarizes a lecture on satisfiability and NP-completeness. It introduces the satisfiability problem and shows that 3-SAT, the problem of determining if a Boolean formula consisting of clauses with 3 literals can be satisfied, is NP-complete by reducing SAT to it. It then shows other problems like vertex cover and maximum clique are NP-complete by reducing 3-SAT to them. Reductions preserve the computational difficulty of problems.