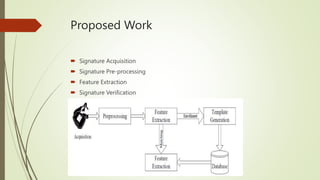
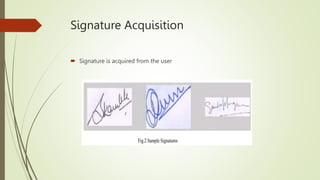
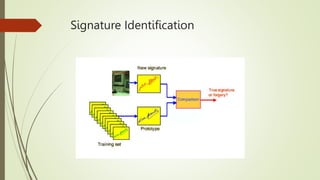
The document discusses the importance of handwritten signature verification for computer security in financial transactions, highlighting its advantages as a cost-effective, reliable, and unobtrusive method. It outlines the challenges of online signature identification, including the need to differentiate between consistent and varying aspects of signatures, and presents a proposed workflow involving signature acquisition, pre-processing, feature extraction, and verification. Additionally, it mentions relevant applications in banking and identification, alongside the necessary hardware and software requirements for implementation.