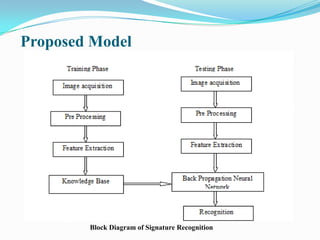
This document presents a proposed methodology for offline signature recognition using global and grid features extracted from signature images. The methodology involves preprocessing signatures, extracting global and grid features using discrete wavelet transforms, training a backpropagation neural network on the features, and classifying signatures based on the trained network. Experimental results show classification accuracy rates ranging from 89-93% for signatures from 10 to 50 individuals. Future work could involve exploring different signature features to potentially improve recognition performance.