1) The document describes a project on signature verification that aims to classify input signatures as genuine or forgeries by matching them to database signatures.
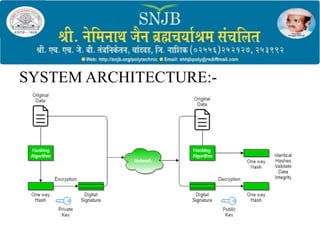
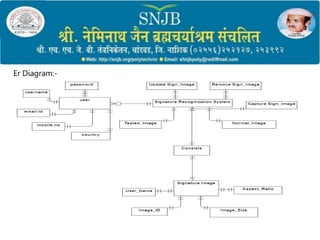
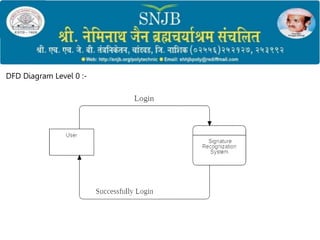
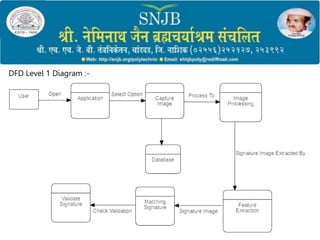
2) It outlines the objectives, methodology, system architecture, and hardware/software requirements which include preprocessing signatures, extracting features, and training a model for verification.
3) The proposed approach uses simple signature matching through Python and PyCharm to provide a language-independent verification with advantages of low cost, little storage needs, and ability to detect forgeries even from signature copies.