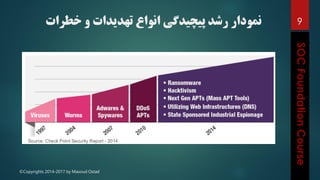
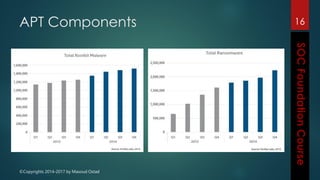
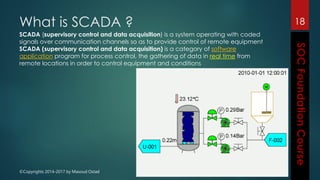
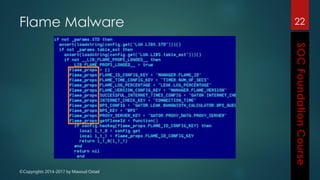
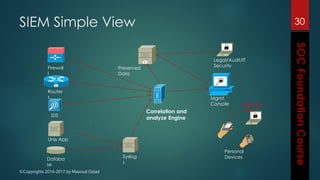
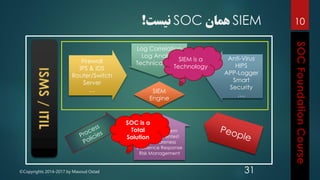
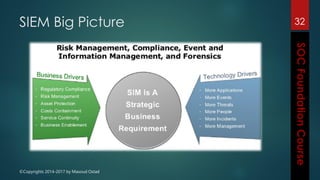
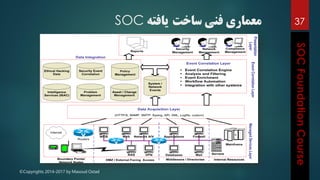
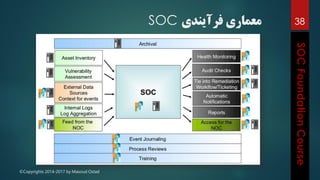
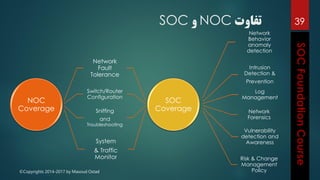
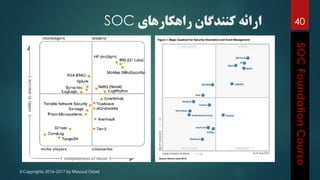
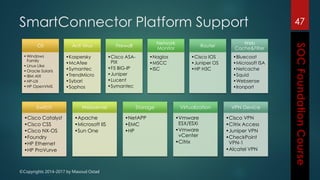
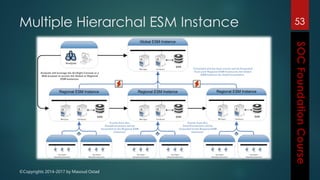
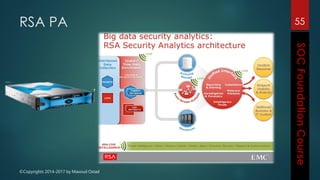
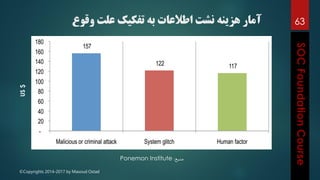
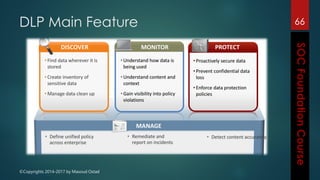
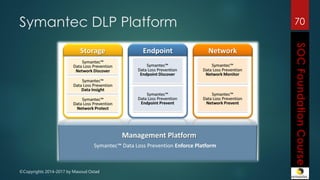
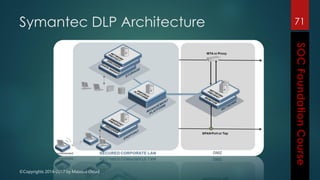
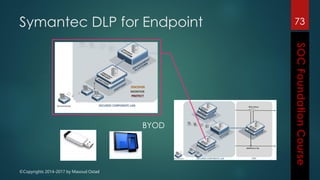
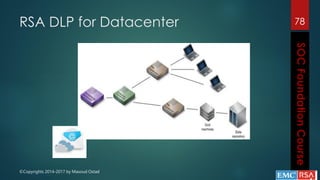
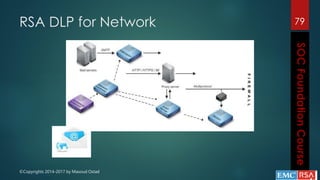
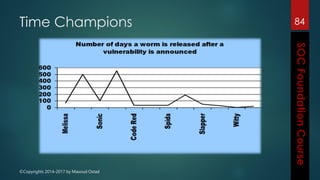
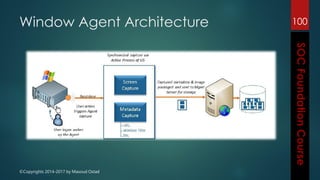
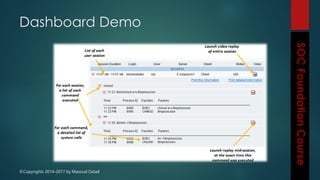
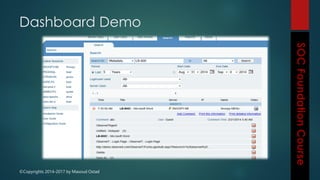
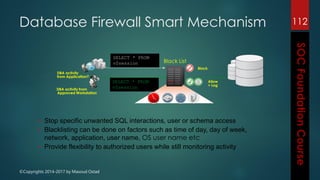
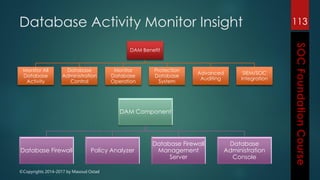
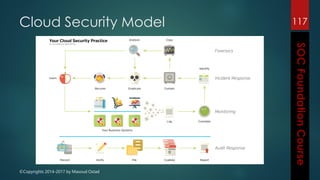
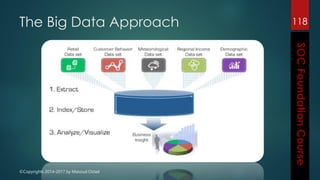
This document outlines the topics that will be covered in a course on security operations centers (SOCs) and security information and event management (SIEM). It discusses traditional security approaches and their weaknesses. It then introduces advanced persistent threats, targeted malware like Stuxnet and Flame, and new mobile threats. The role of SIEM technologies and SOC frameworks for centralized security monitoring, analytics, and response are explained. Key components of SOCs like threat management, vulnerability management, and security intelligence services are also outlined.