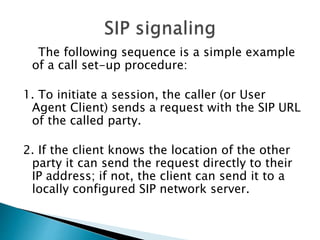
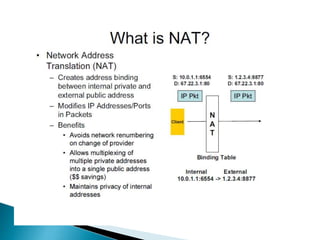
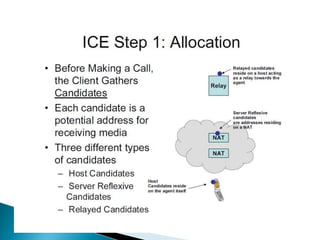
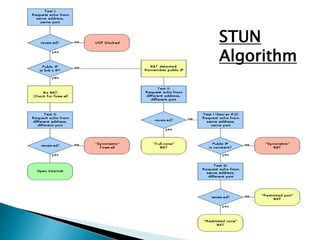
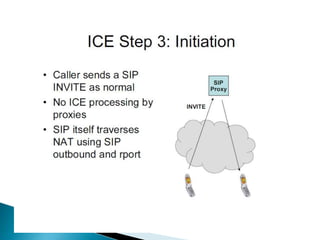
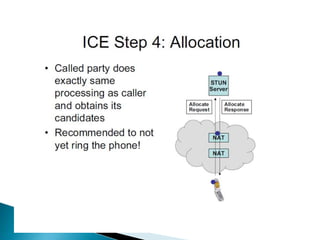
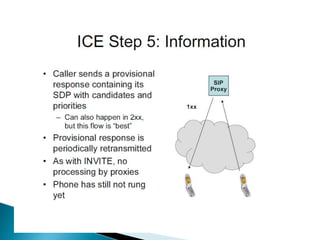
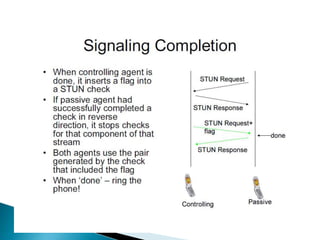
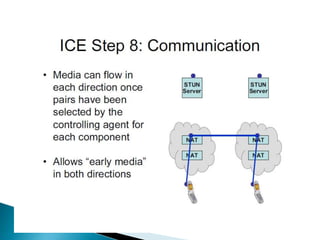
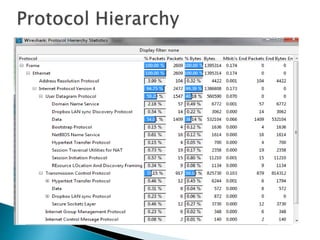
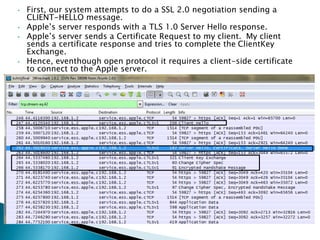
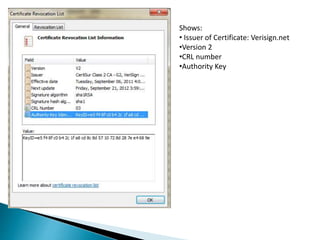
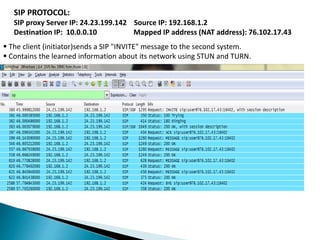
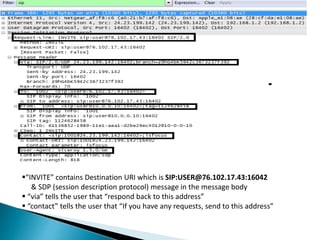
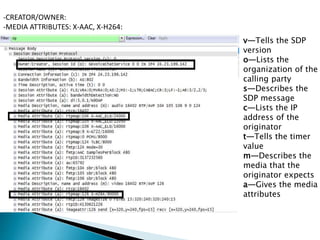
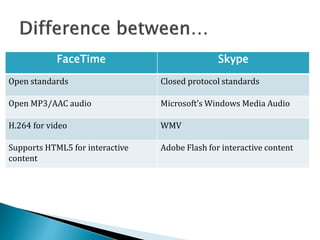
The document describes a video calling software application that operates exclusively on Apple devices using VoIP protocols such as SIP, with supporting technologies like STUN, TURN, and ICE for traversing networks. It details the call setup procedure, the methods used in SIP for managing sessions, and the underlying network interactions involved in establishing a connection. Additionally, it covers the use of RTP for real-time data transmission and the algorithmic processes involved in connecting users via NAT techniques.