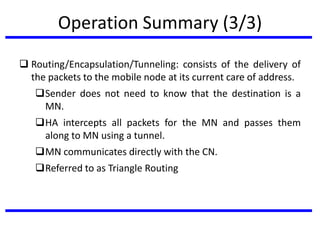
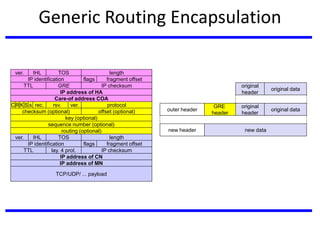
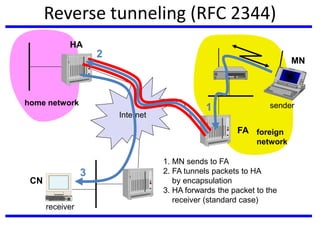
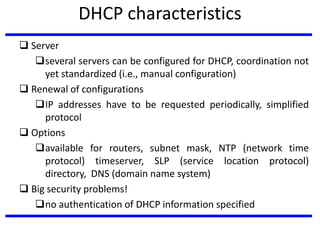
The document discusses mobile communication units, focusing on Mobile IP and its role in providing network layer mobility. It explains key concepts like dynamic host configuration, routing protocols, and how Mobile IP enables seamless connectivity for mobile nodes while addressing challenges such as consistent IP addressing and packet routing. The document also covers the operational mechanisms, requirements, and encapsulation methods crucial for Mobile IP functionality.