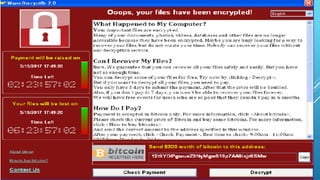
Ransomware is a type of malware that encrypts a victim's files and demands ransom payment in order to decrypt the files. The WannaCry attack in 2017 impacted over 300,000 systems in 150 countries through ransomware. While ransomware uses strong encryption, paying the ransom is not recommended as there is no guarantee files will be recovered. It is best to backup files and keep systems updated with the latest security patches to protect against ransomware infections.