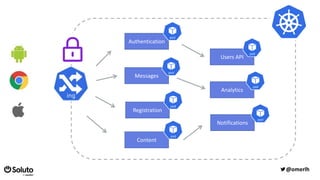
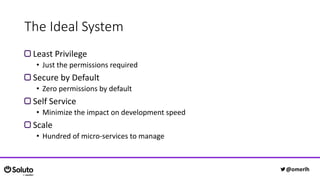
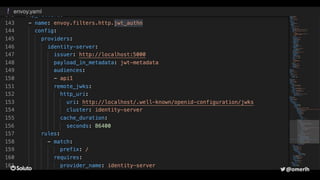
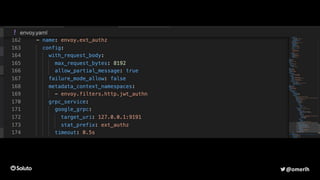
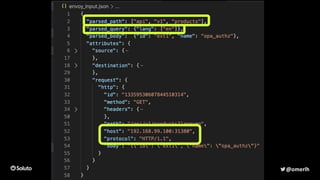
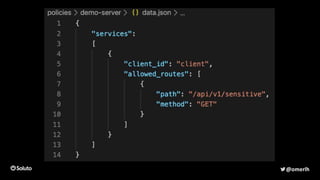
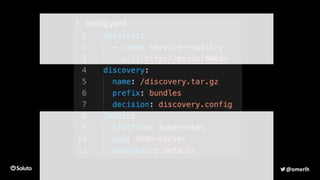
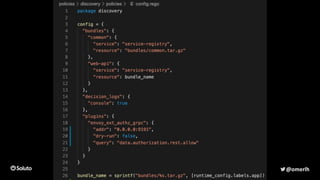
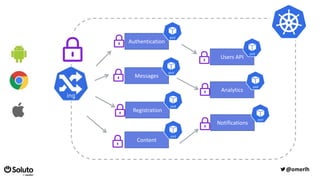
The document discusses the development of a secure and scalable authorization system emphasizing a zero-trust approach and least privilege principles to manage micro-services. It highlights the integration of technologies like Envoy and Open Policy Agent (OPA) for authentication and authorization while focusing on enhancing security measures, logging, and automation. The goal is to enable developers to manage permissions efficiently without hindering their speed or productivity.