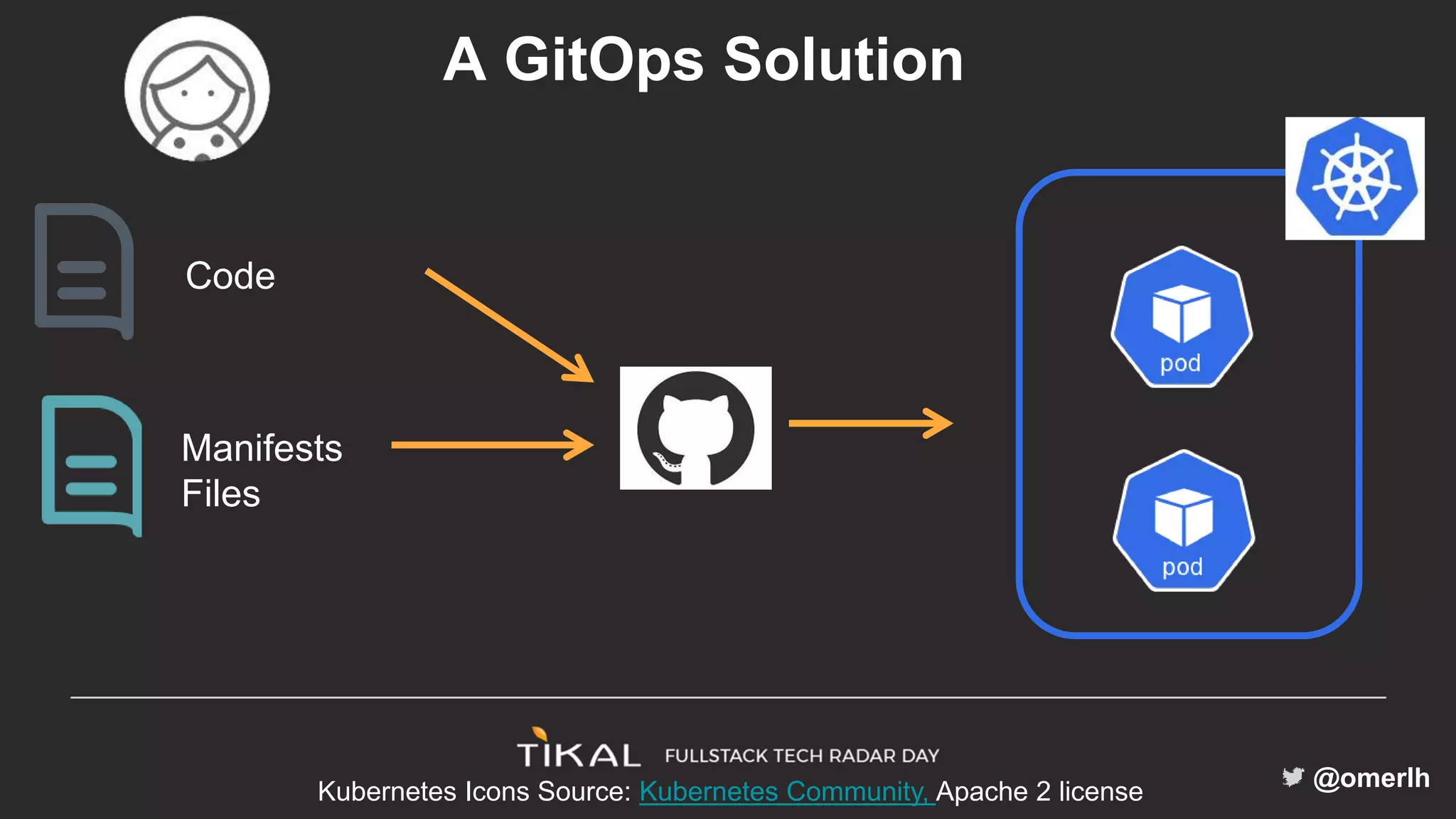
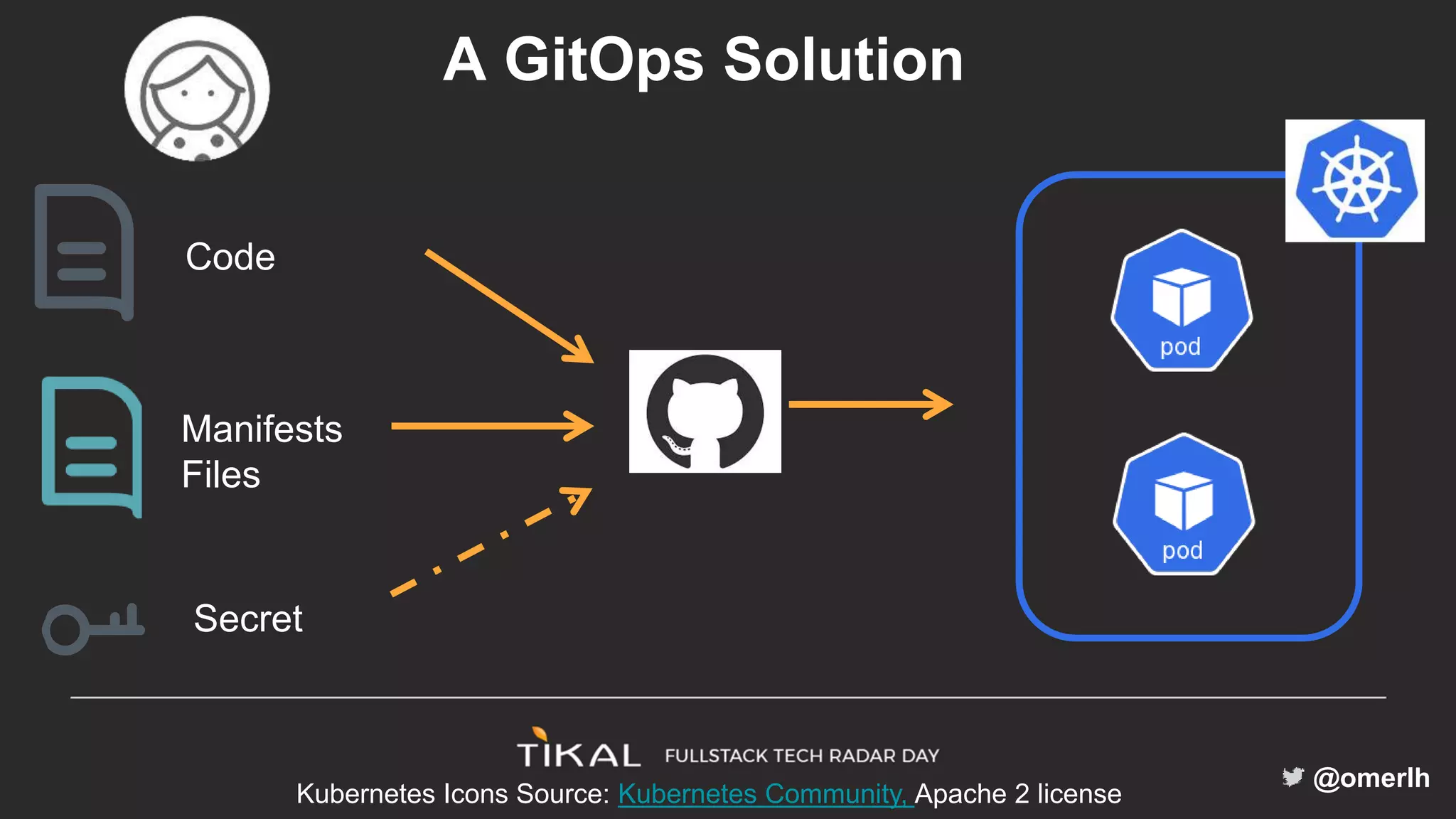
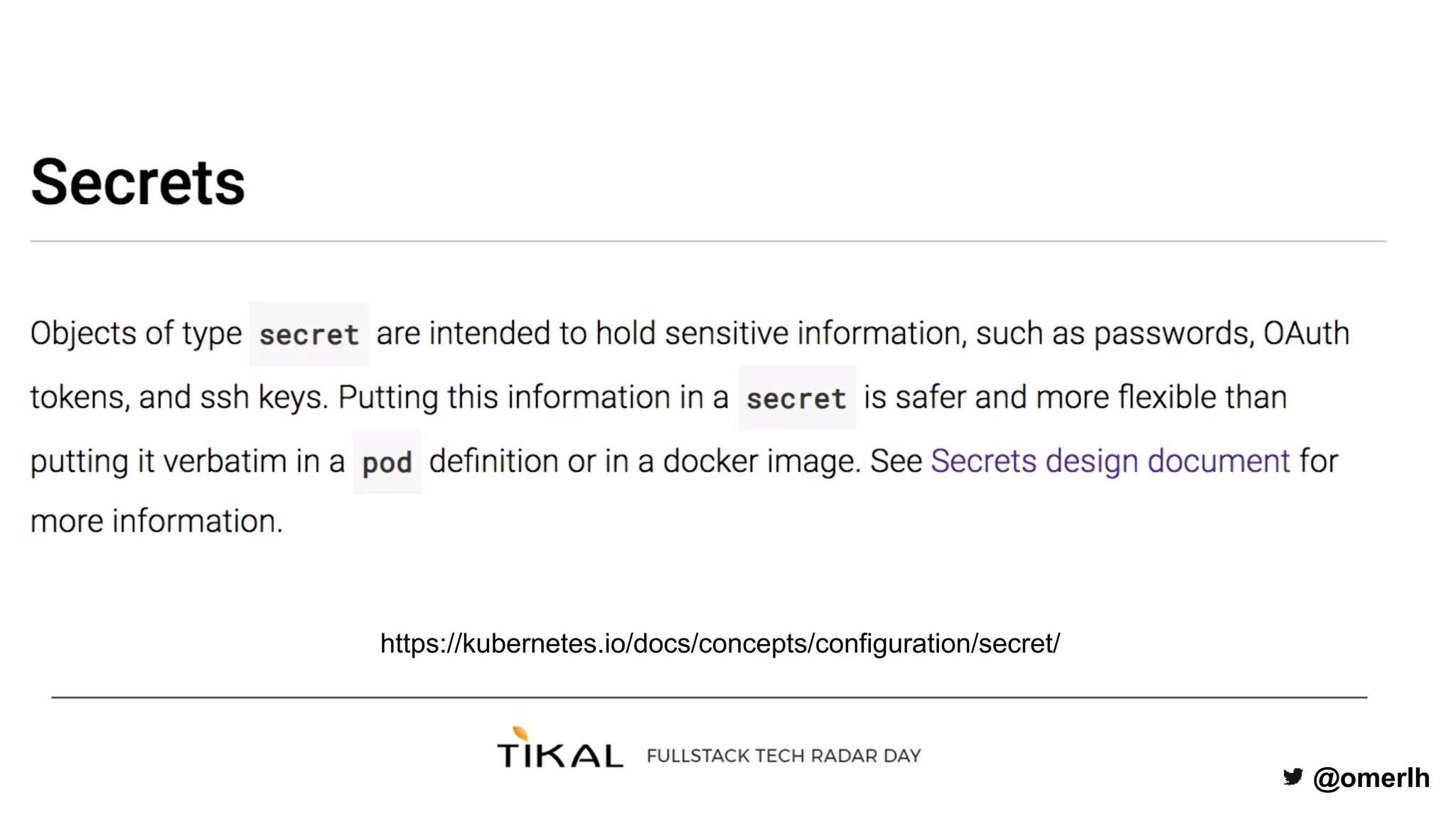
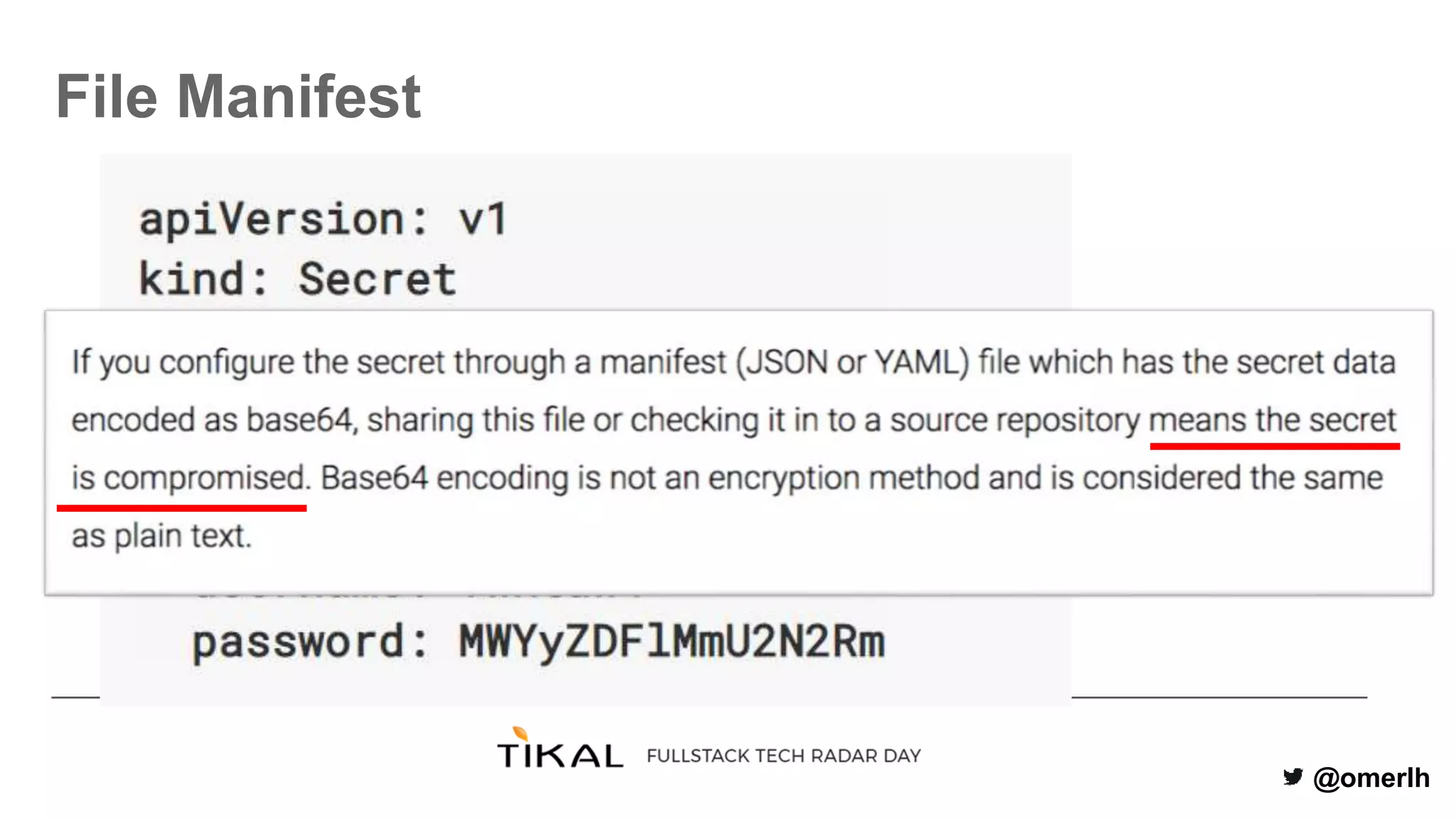
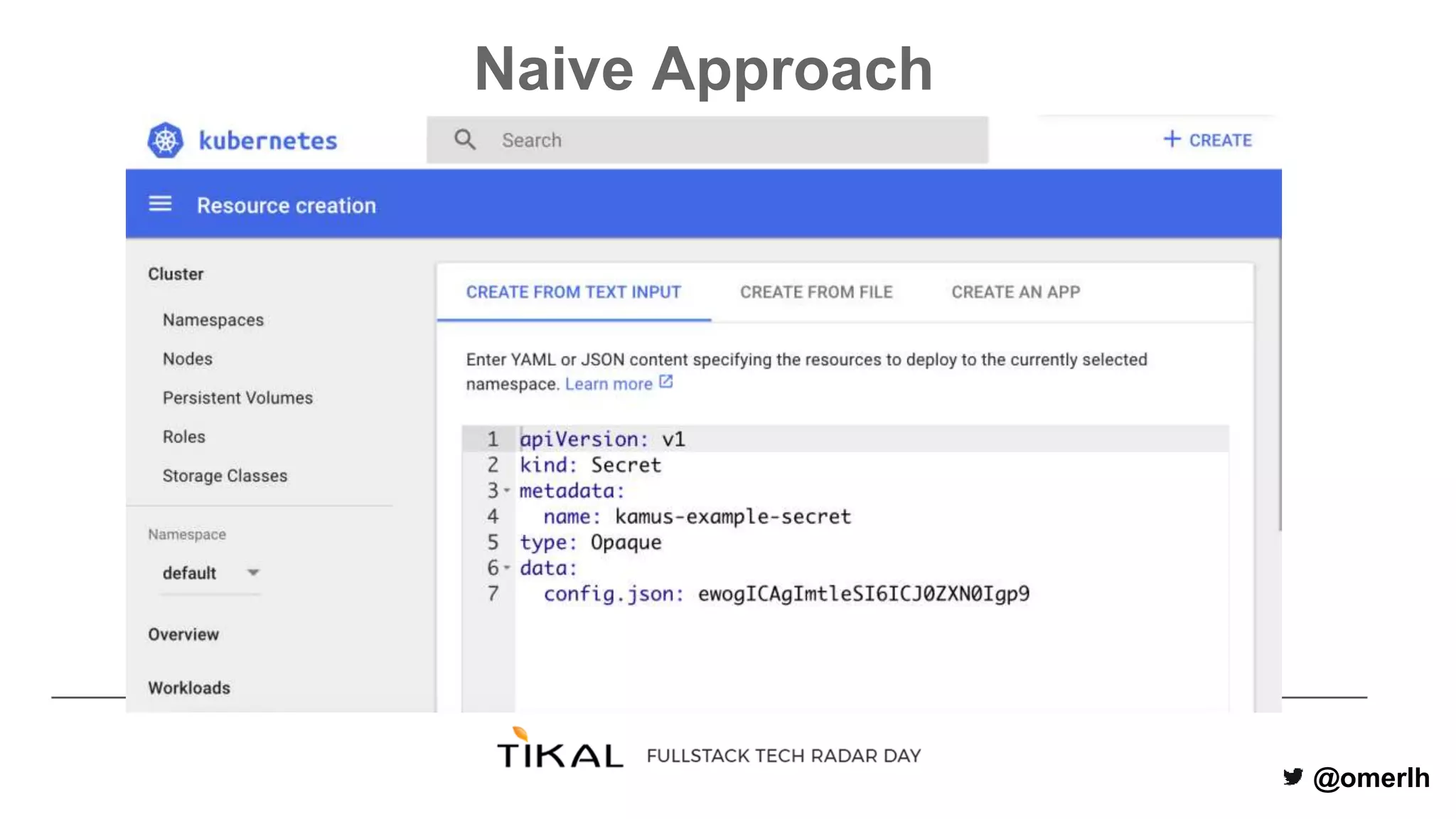
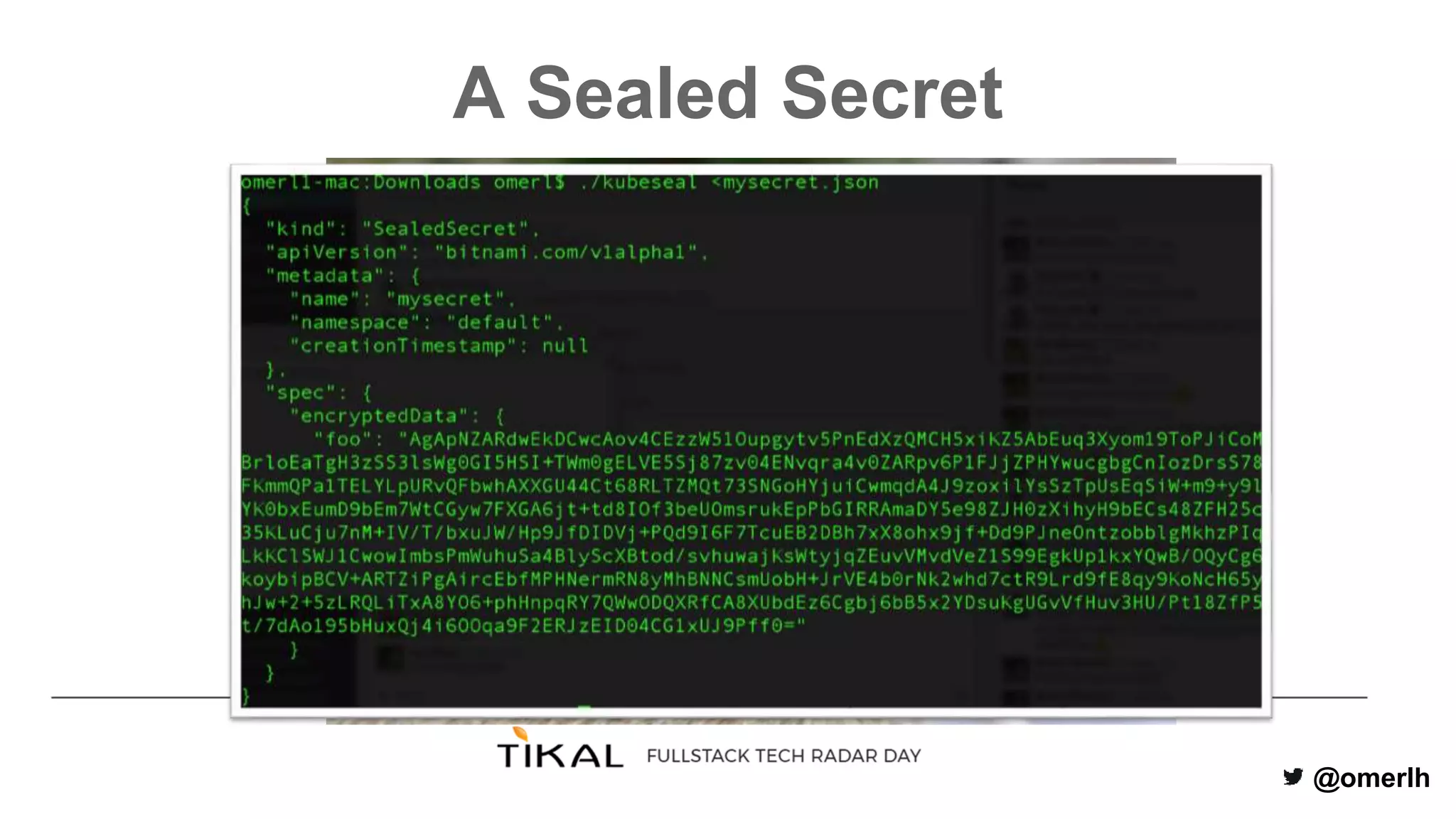
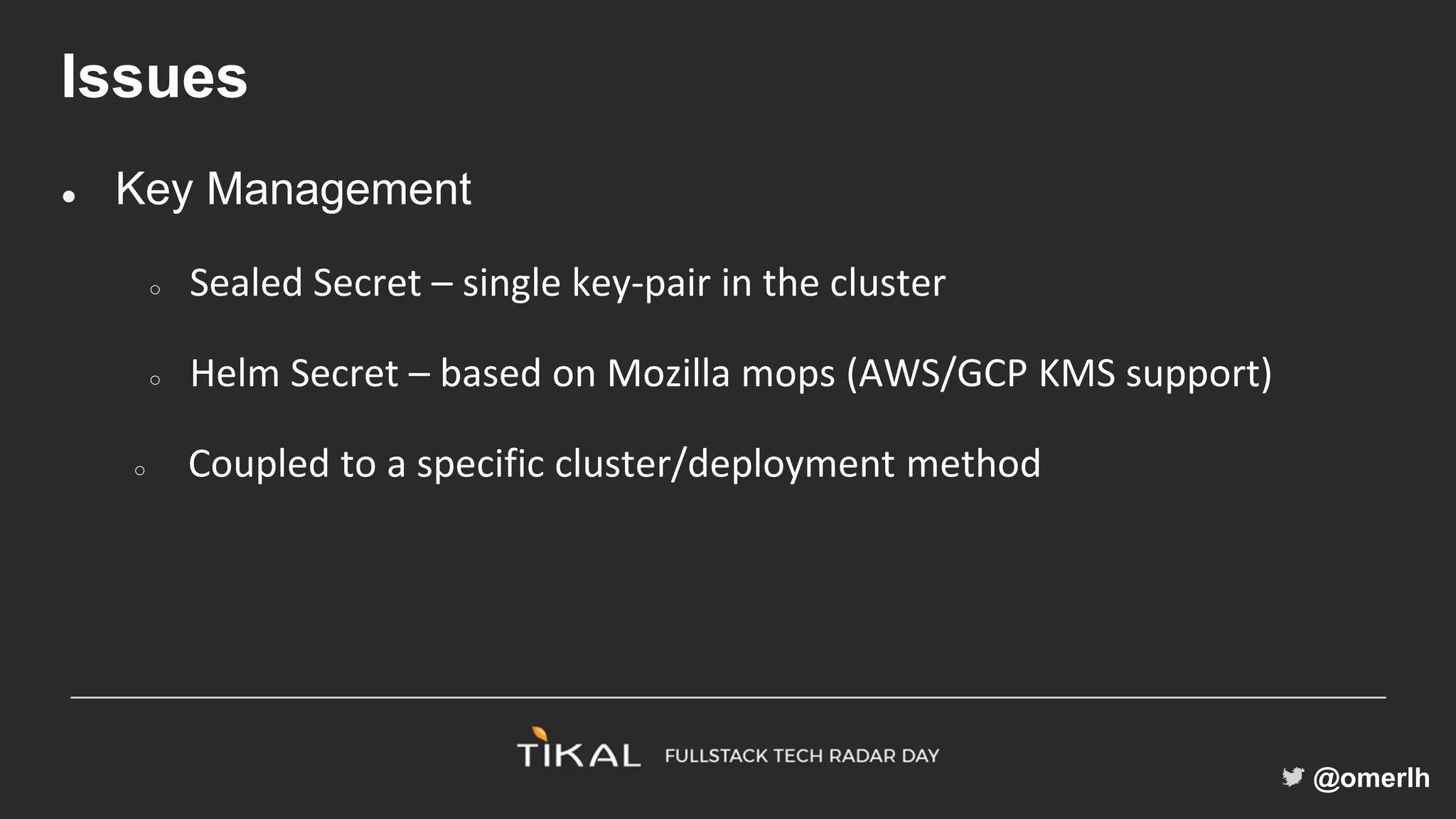
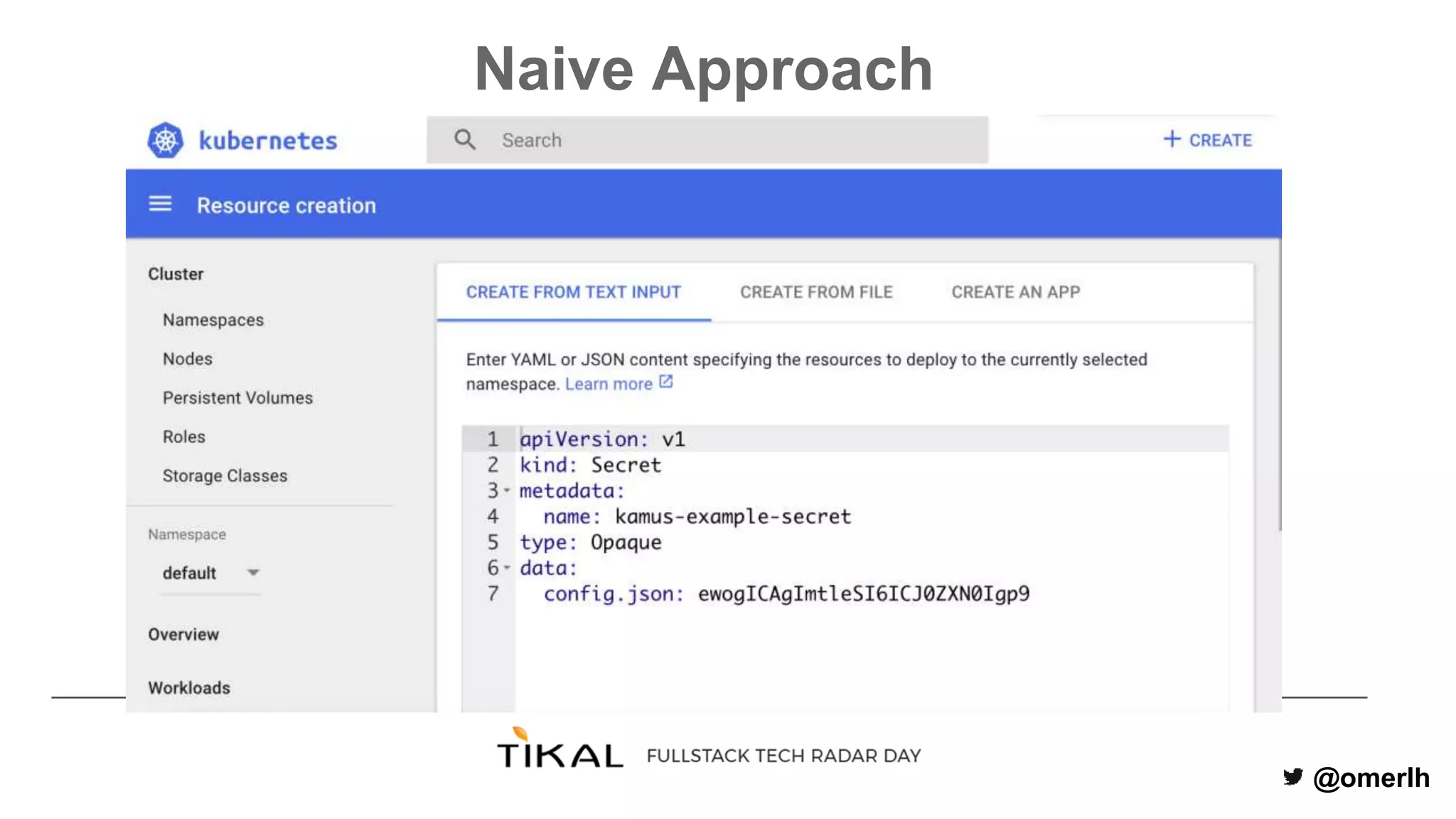
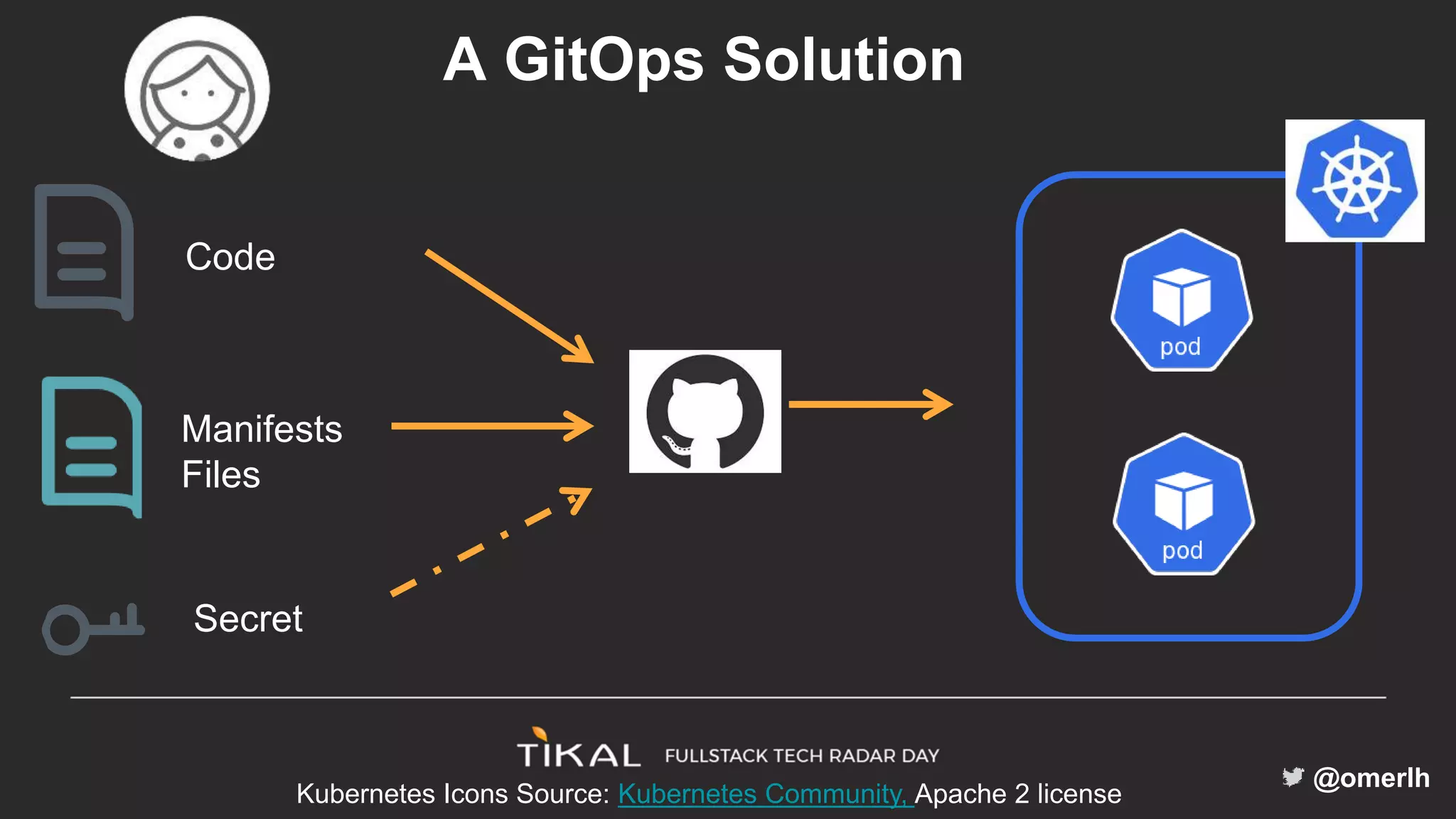
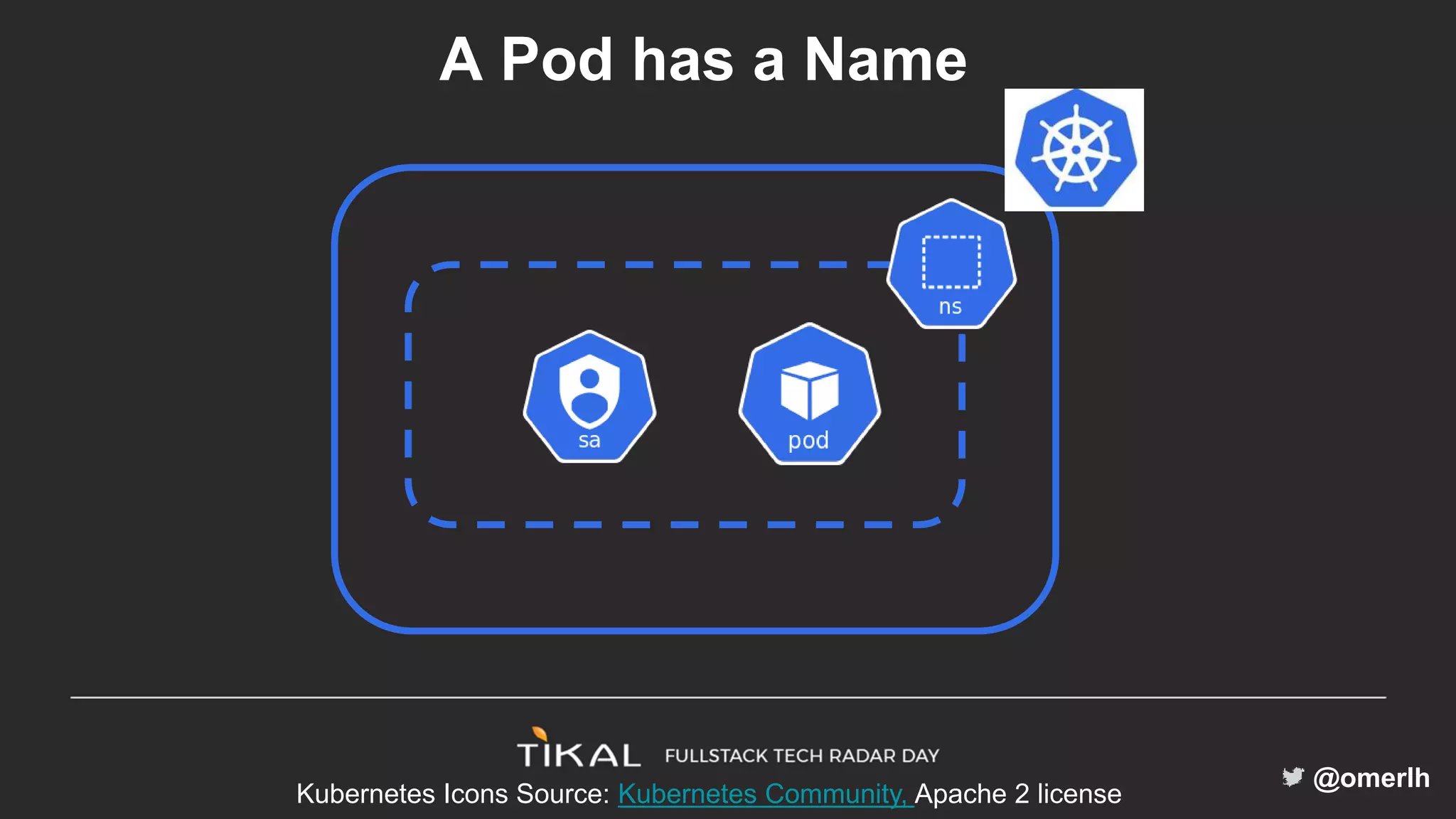
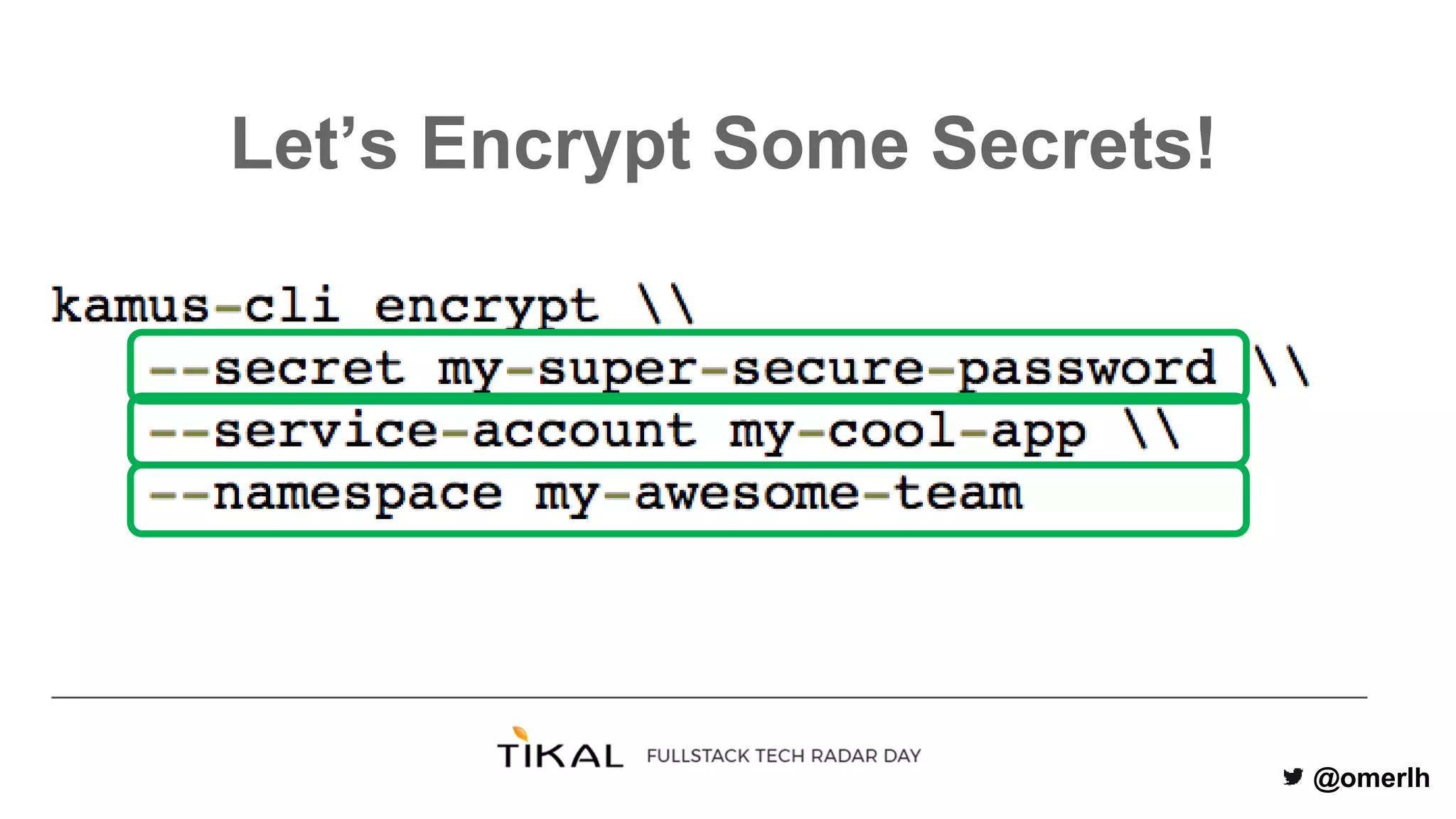
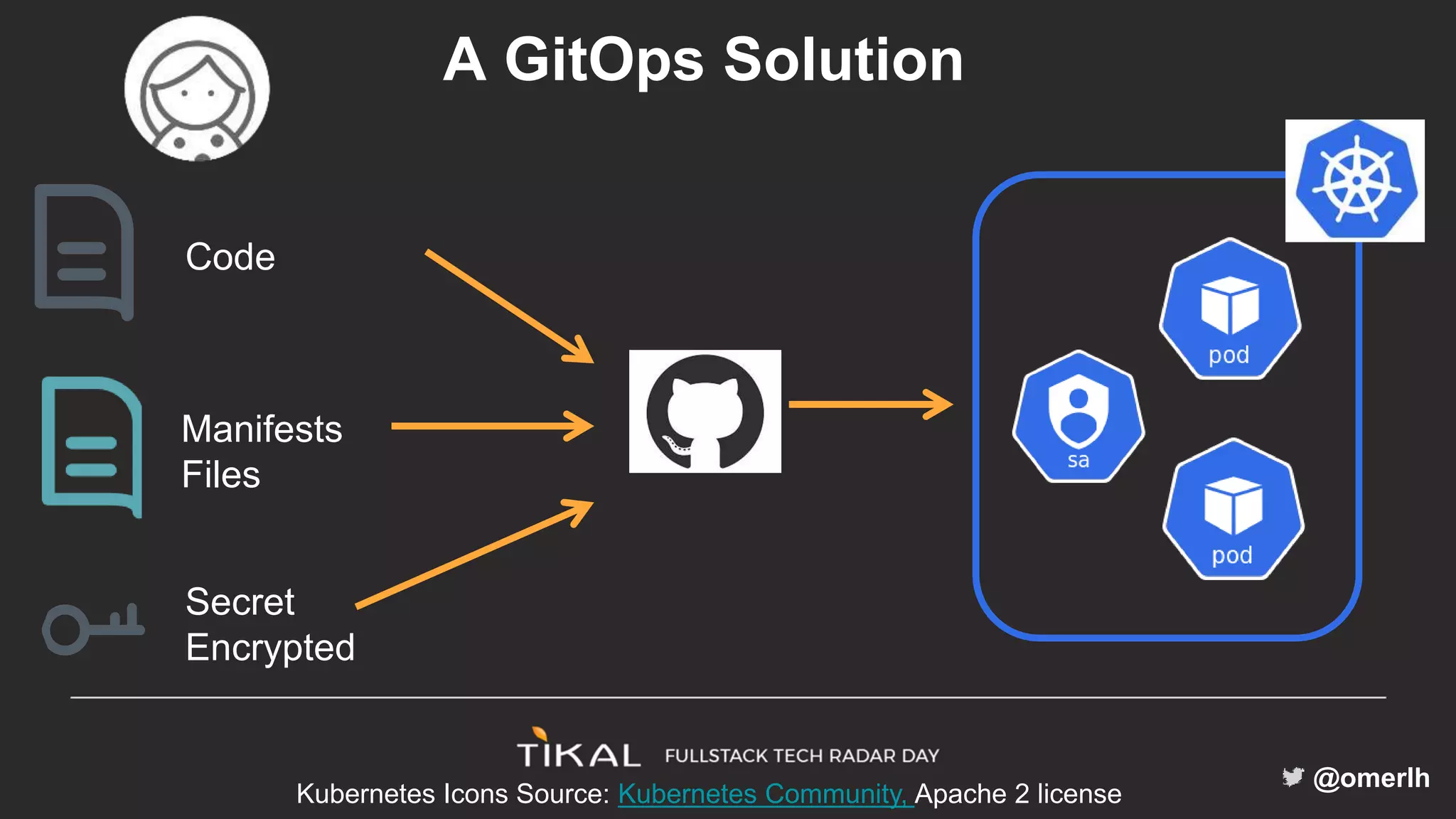
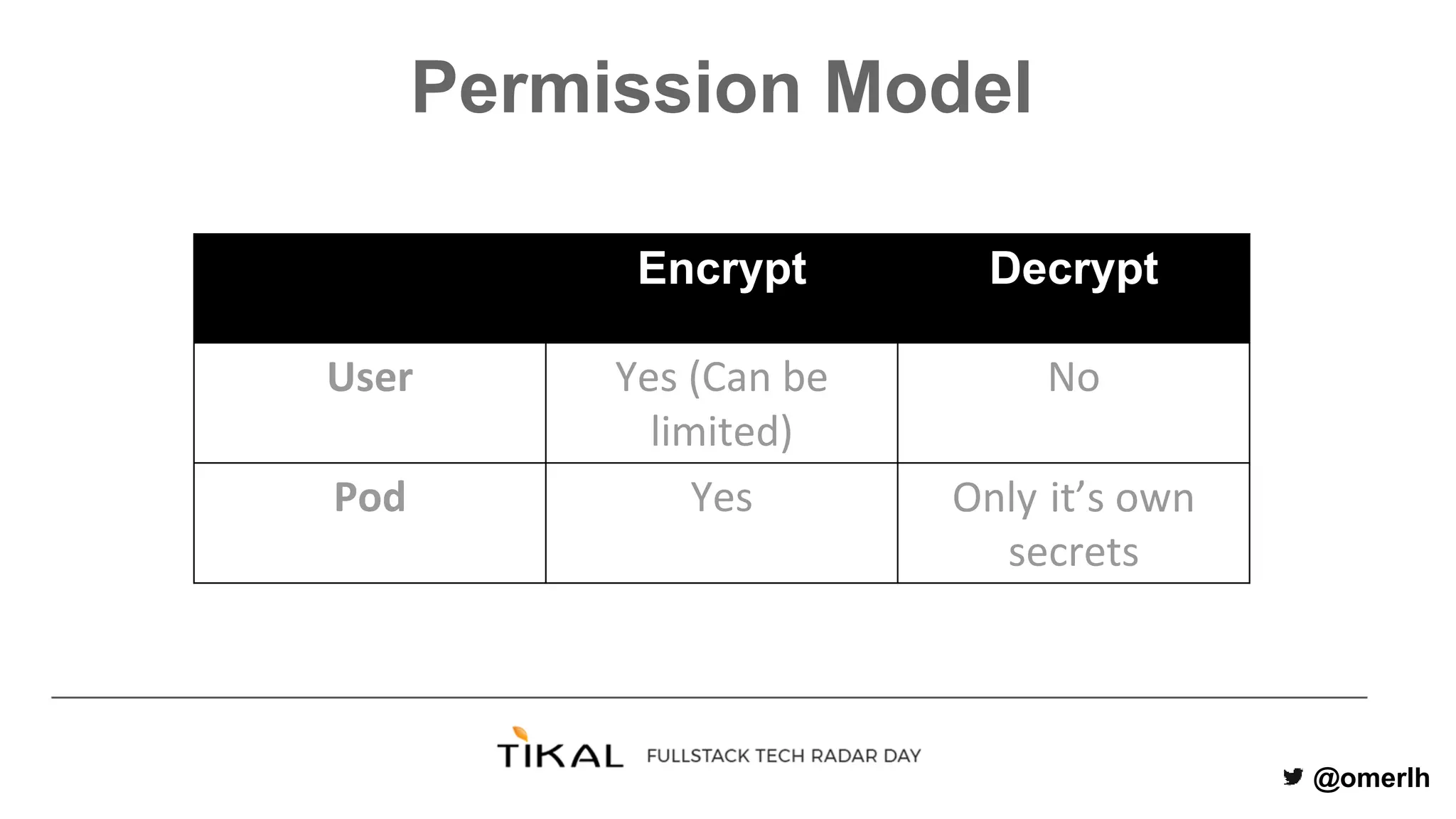
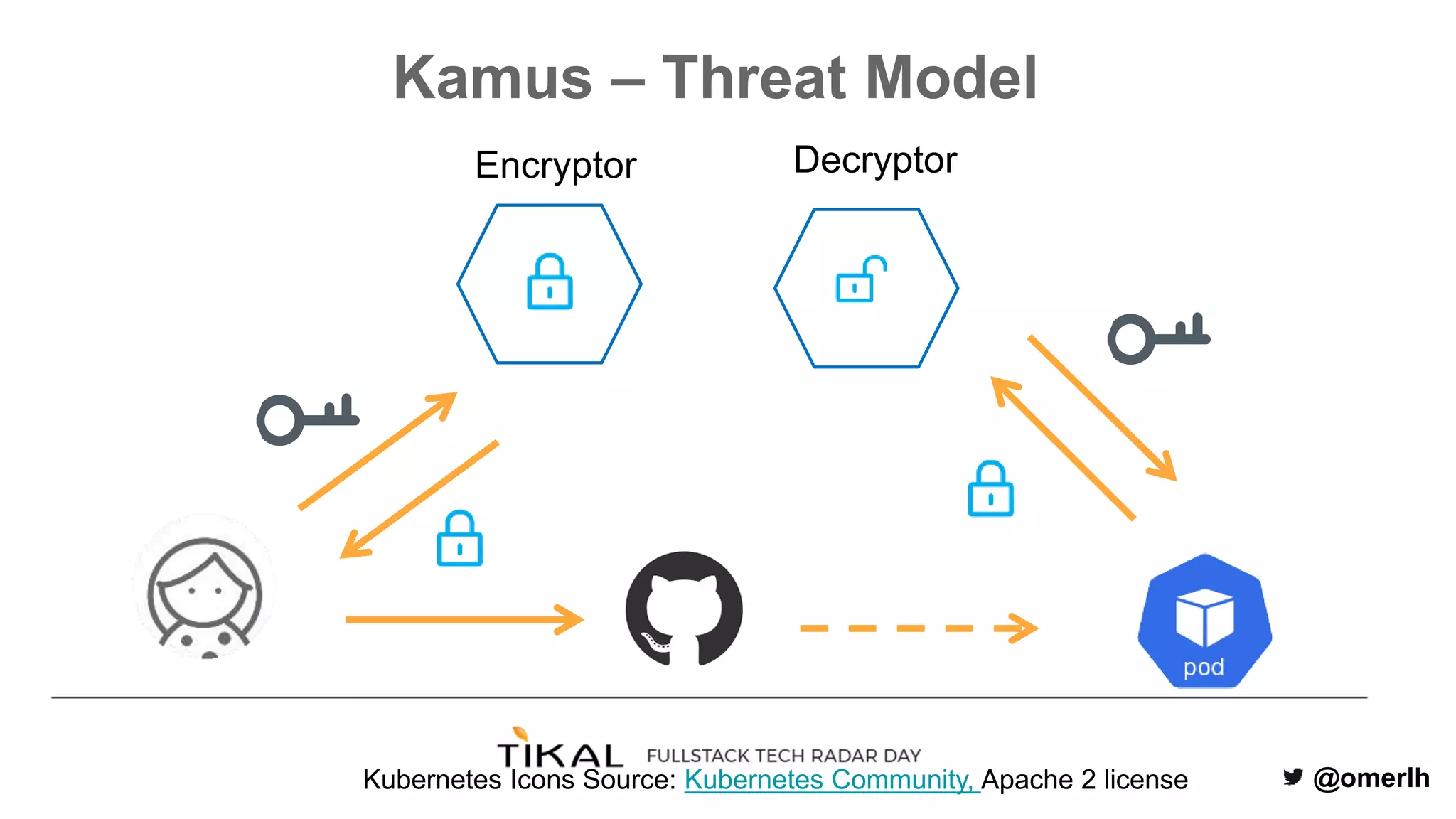
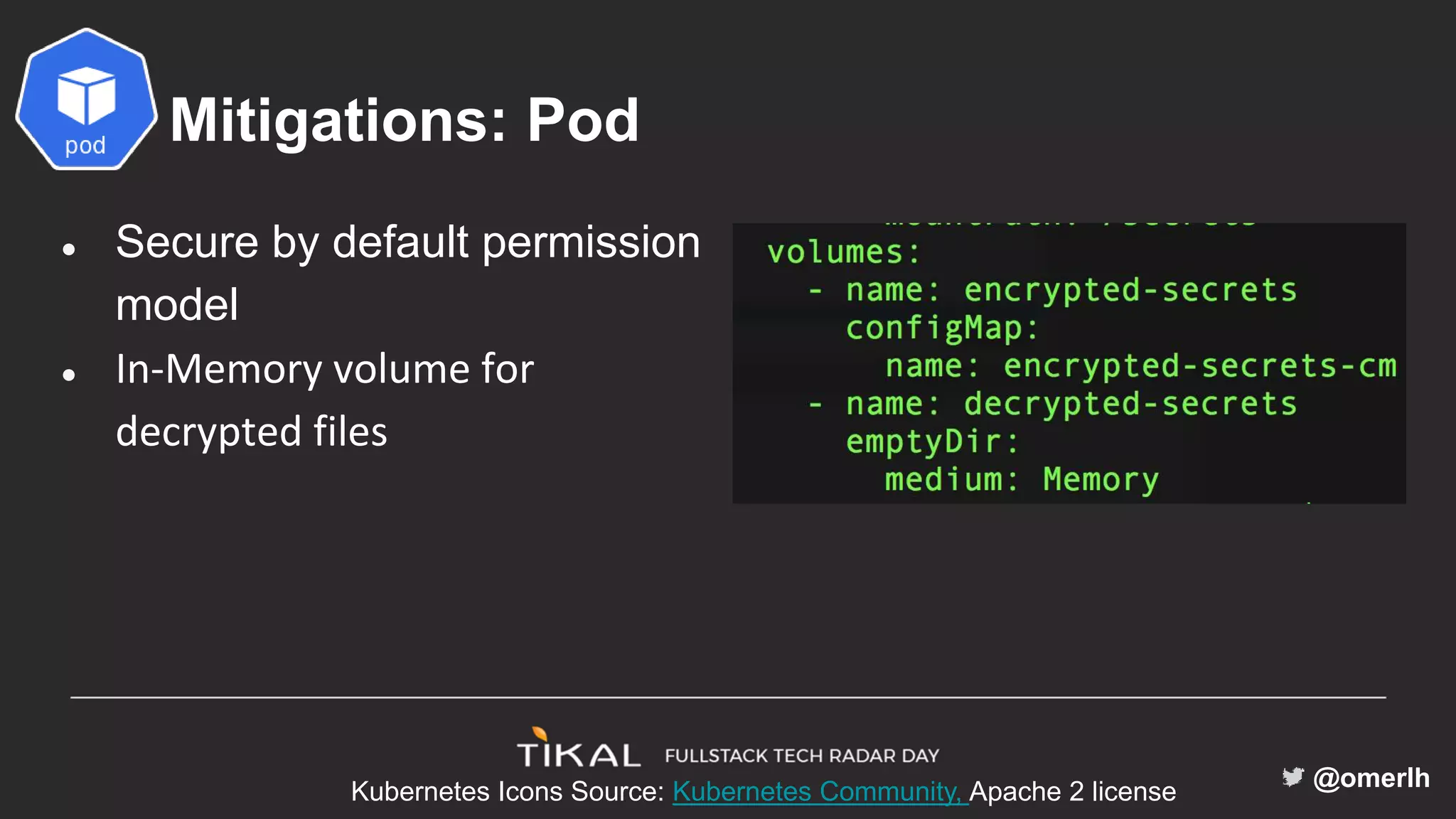
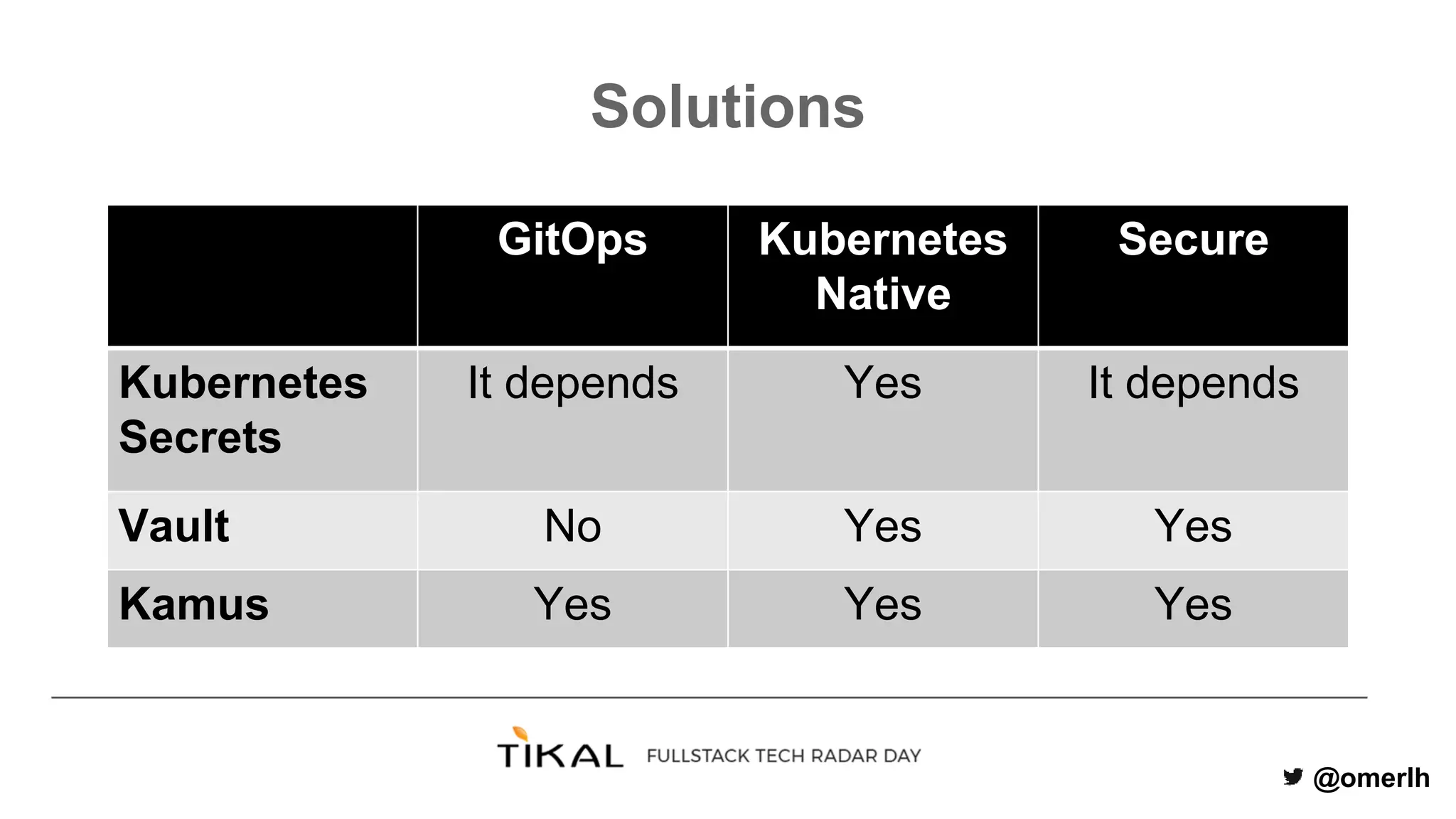
The document discusses various methods for managing secrets in Kubernetes, highlighting the importance of security and integration with GitOps. It contrasts several approaches including Kubernetes Secrets, HashiCorp Vault, and Kamus, outlining their features and limitations. Kamus is presented as a potential solution that meets the requirements of being GitOps-compatible, Kubernetes-native, and secure.