Embed presentation
Download to read offline

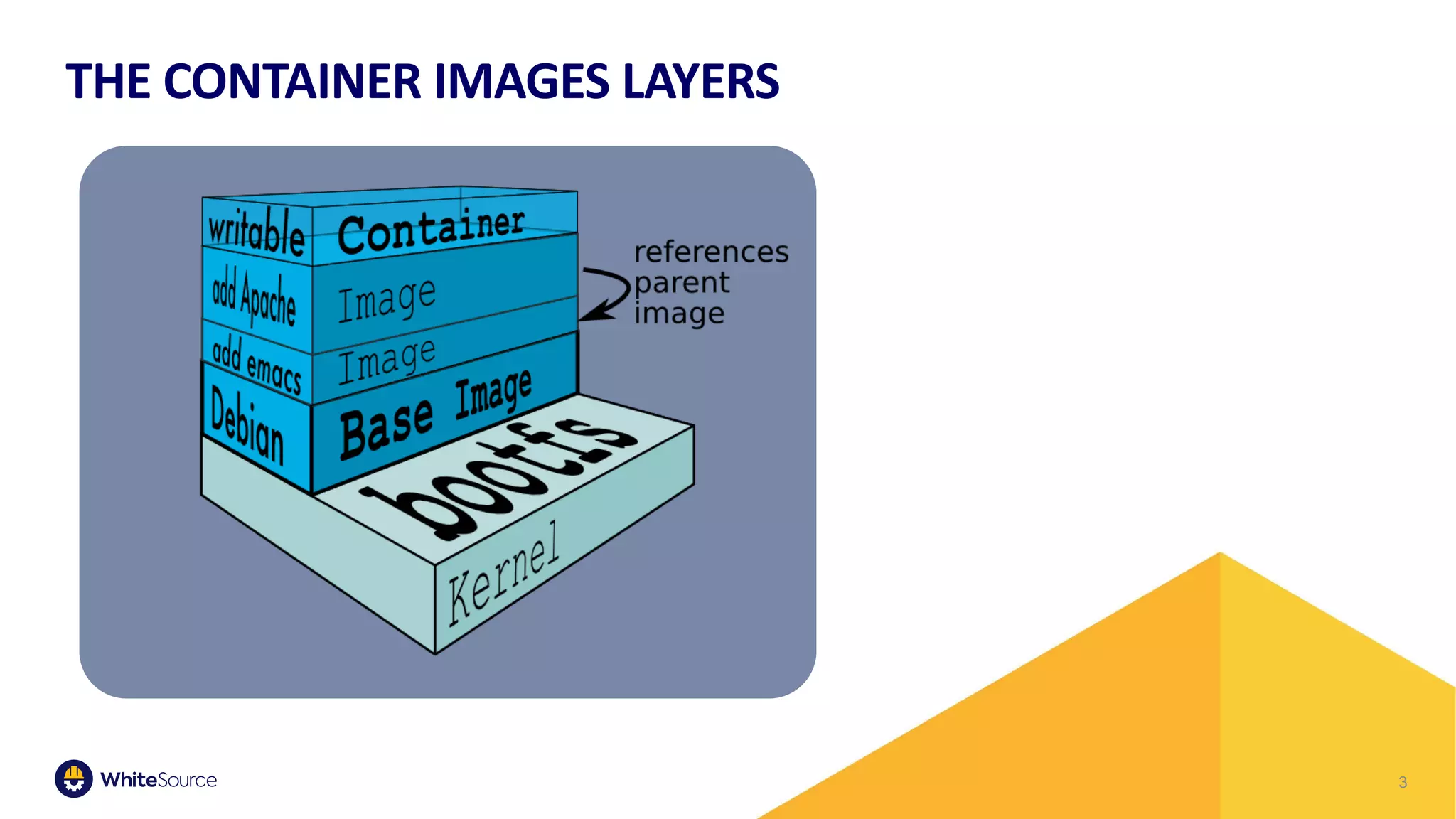
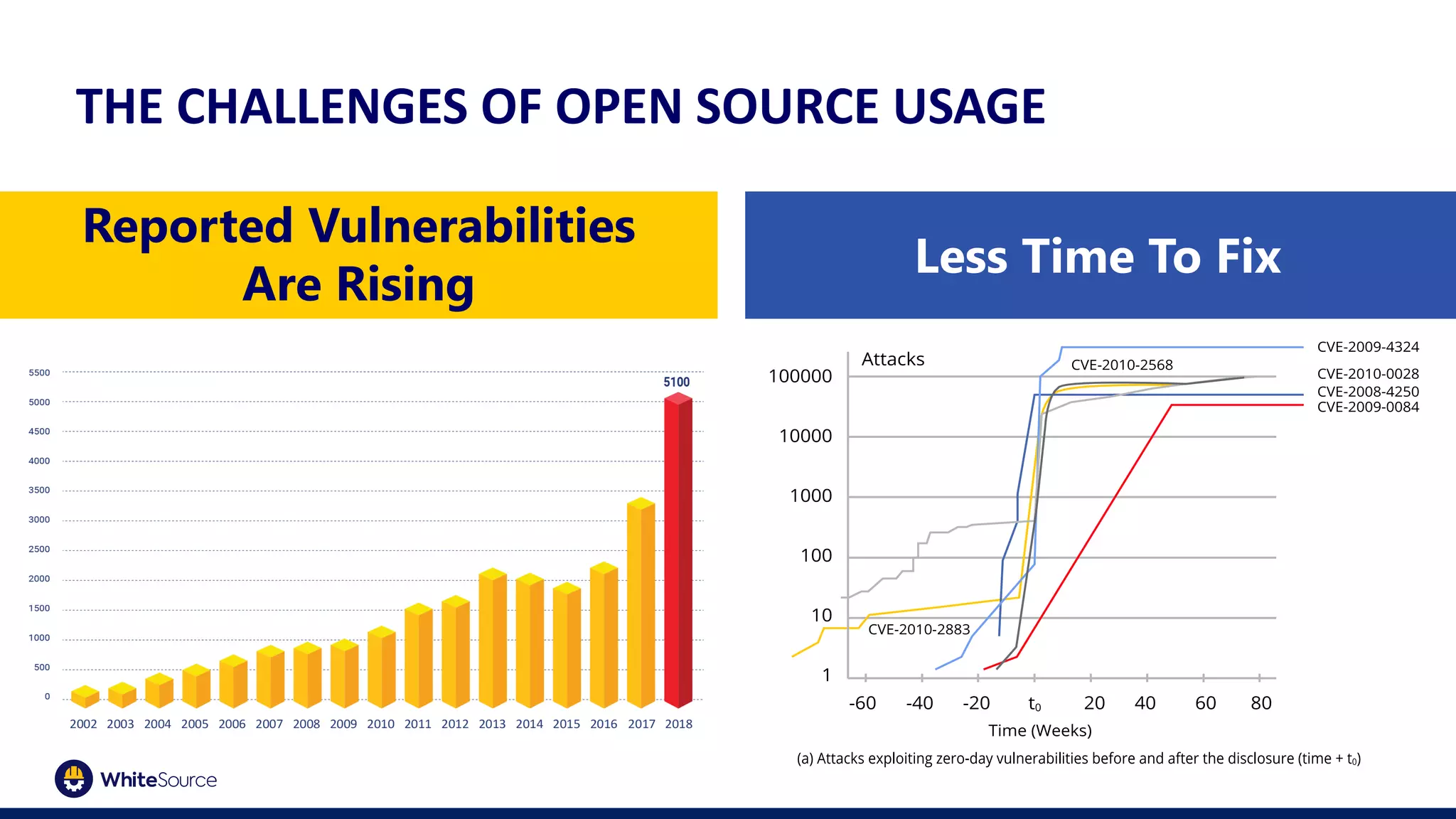
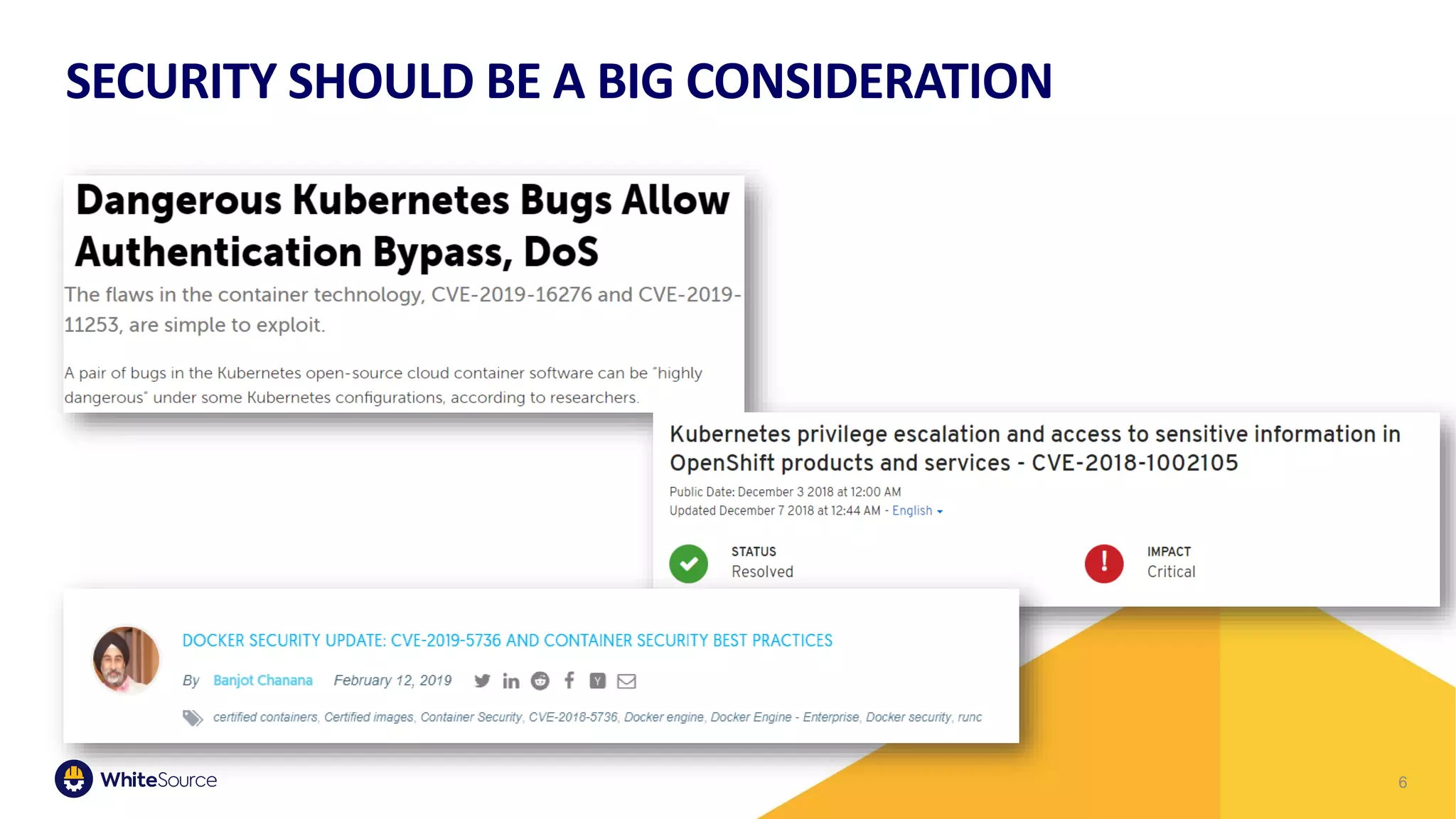

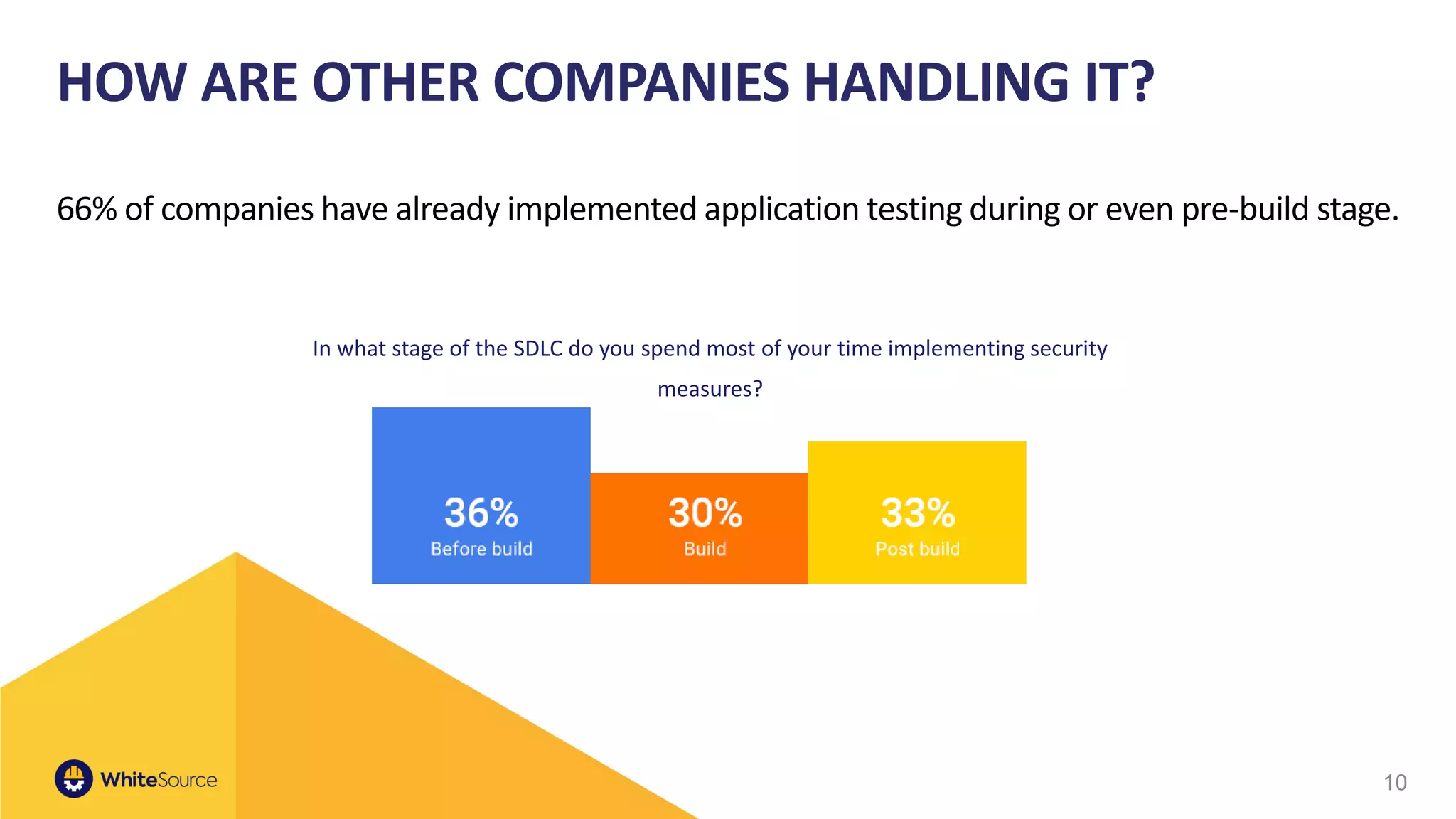
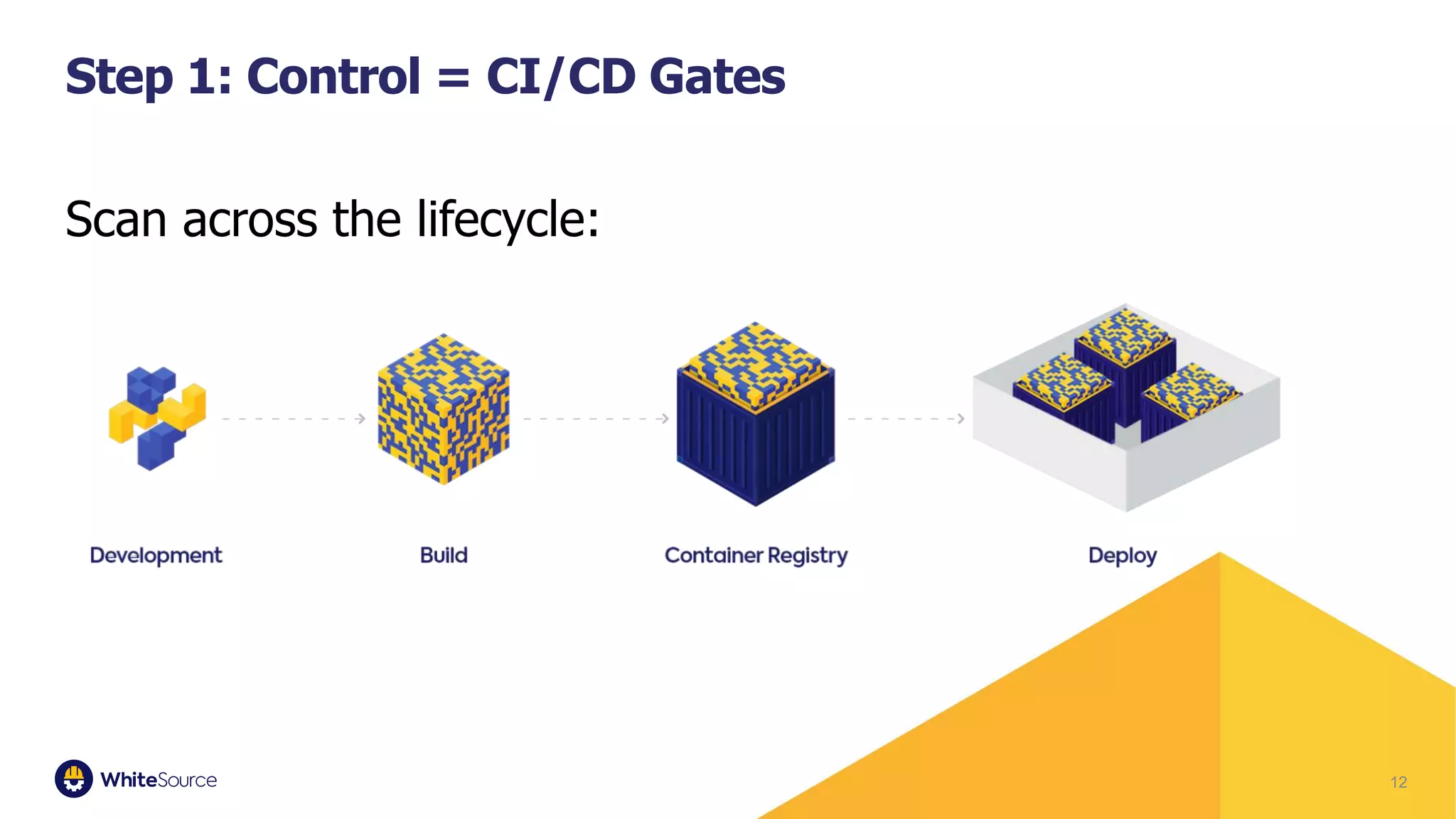

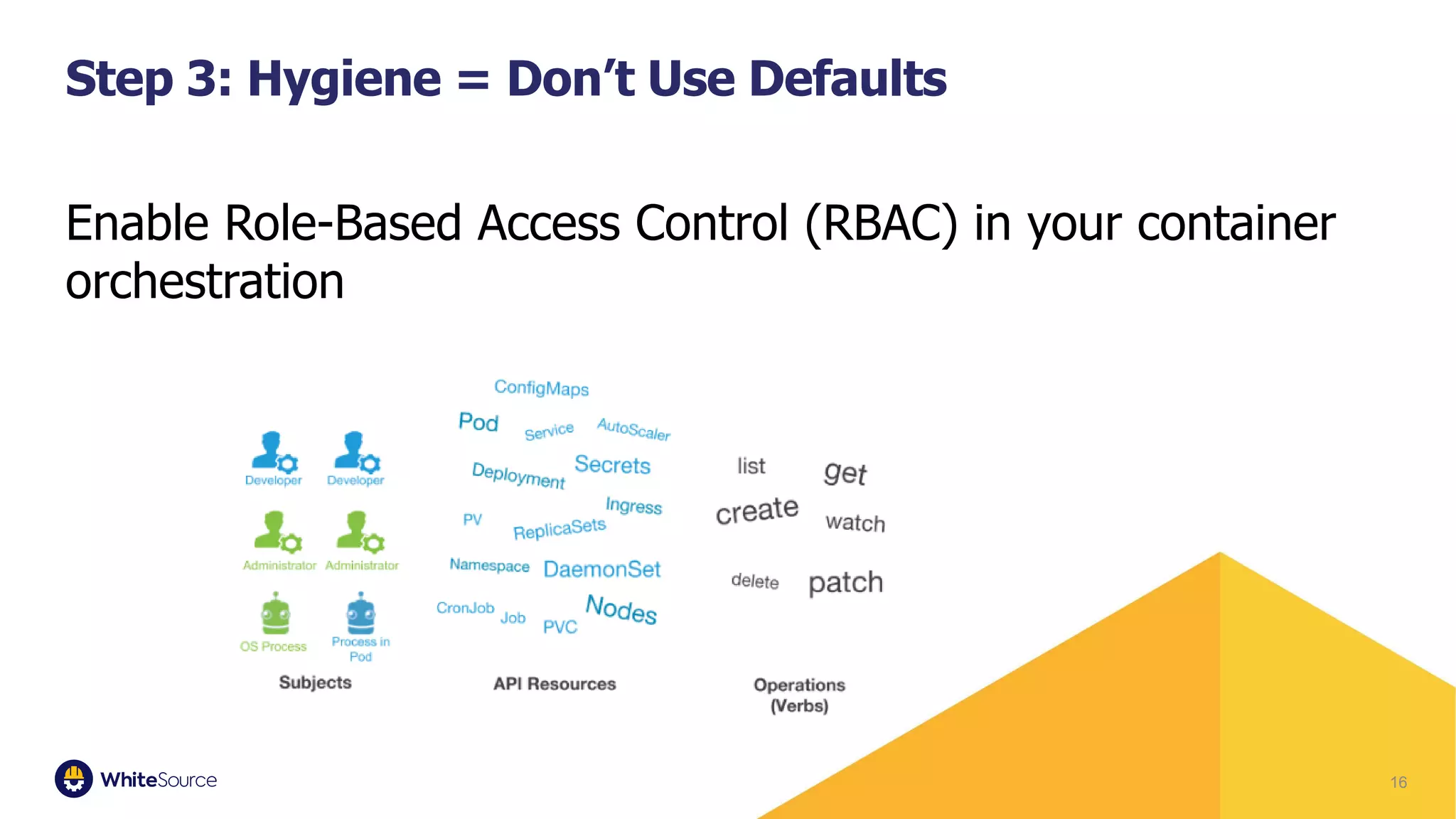





The document discusses the barriers to container security and strategies for overcoming them, emphasizing the importance of security throughout the software development lifecycle (SDLC). It outlines key steps such as control through CI/CD gates, using trusted sources, ensuring hygiene, and monitoring deployments. Rising costs associated with fixing security issues are highlighted, along with the increasing trend of companies implementing security measures early in the development process.





















