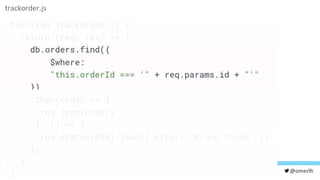
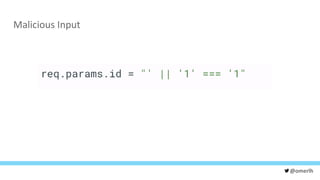
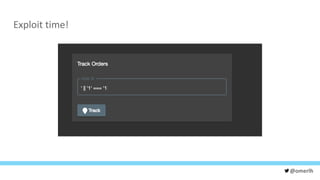
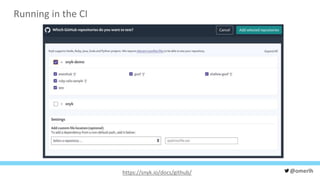
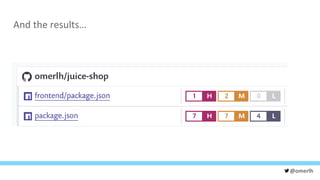
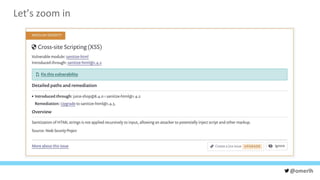
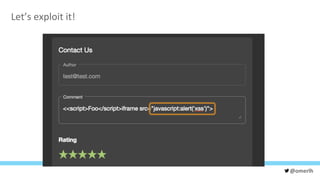
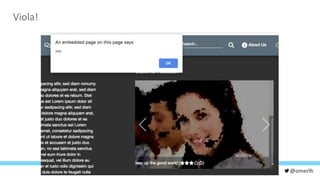
The document discusses various cybersecurity testing techniques, focusing on dynamic and static analysis security testing tools like OWASP ZAP and Nodejsscan. It highlights the risks of common vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF), along with mitigation strategies. The author emphasizes the importance of input sanitization and the need to integrate security testing into continuous integration processes.