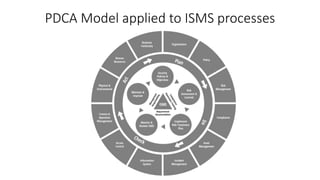
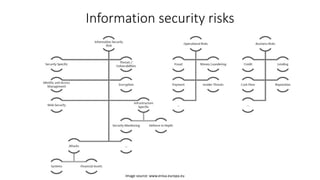
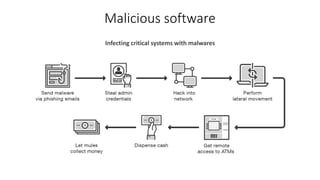
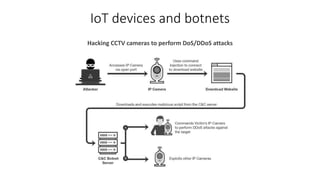
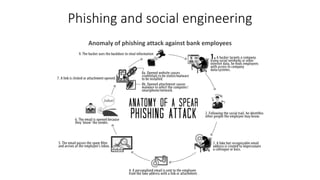
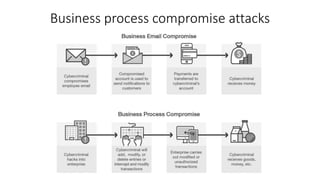
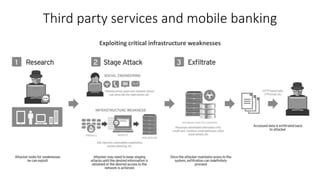
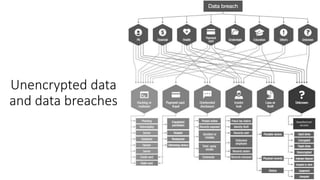
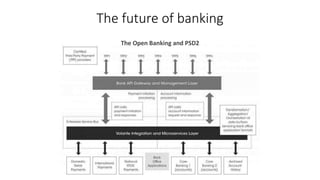
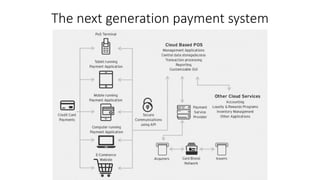
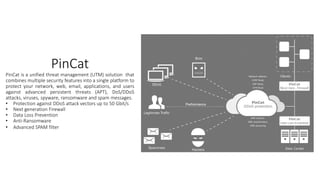
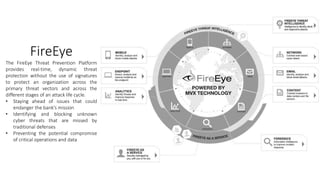
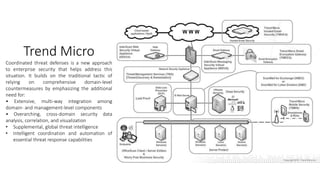
The document outlines the importance of information security management systems in the banking sector, highlighting major threats such as malware, IoT vulnerabilities, and phishing. It discusses future trends in banking security, including biometric authentication and the integration of AI and machine learning for fraud prevention. Additionally, it presents various cybersecurity solutions and tools like Pincat and Maxpatrol, which enhance protection against advanced threats.