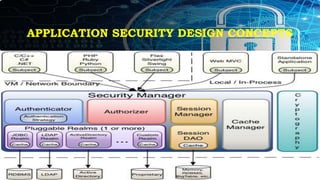
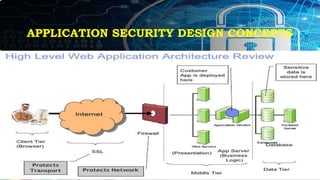
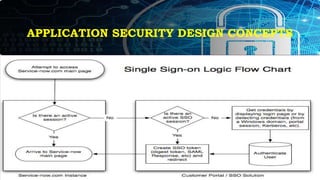
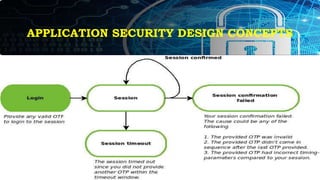
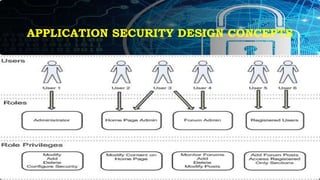
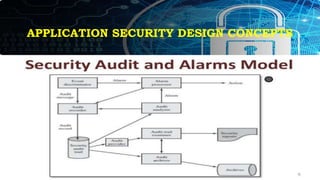
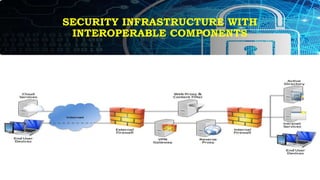
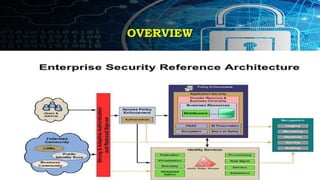
This document provides an overview of key concepts for application security design. It discusses the importance of incorporating security throughout the application development lifecycle. It outlines several security design aspects that should be considered, including authentication, authorization using roles, session management, and implementing a secure access layer. It also emphasizes the importance of security testing, code reviews, and conducting risk assessments and assurance testing prior to deployment. Finally, it discusses how to establish security guidelines and build a centralized security infrastructure with interoperable components to provide identity, authentication, authorization and other security services across applications in a standardized way.








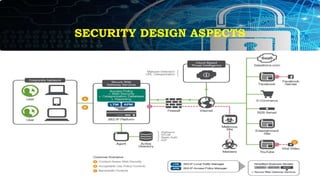

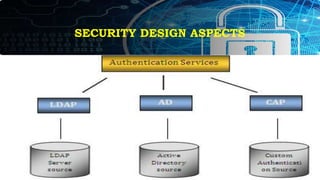



![SECURITY DESIGN ASPECTS
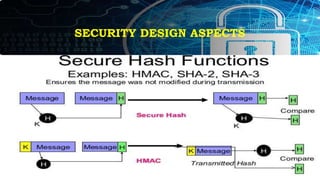
Integrity:
• Integrity is ‘the property that data has not been changed, destroyed, or lost in an
unauthorized or accidental manner’.
• Incorporating integrity into an application will inform the recipient of data modification
by unauthorized users during storage or transmittal.
• Various hash methods such as SHA-1 or MD5 can provide the integrity component.
• Confidentiality is ‘the property that information is not made available or disclosed to
unauthorized individuals, entities, or processes [i.e., to any unauthorized system entity]’.](https://image.slidesharecdn.com/securitydesignconcepts-170322132501/85/Security-Design-Concepts-16-320.jpg)