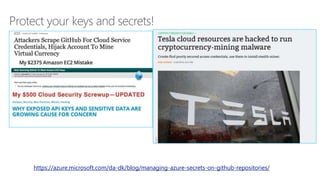
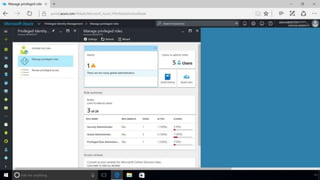
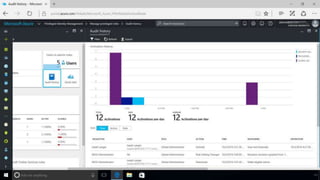
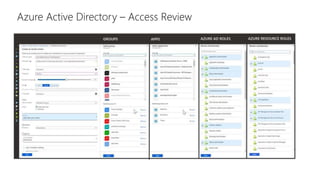
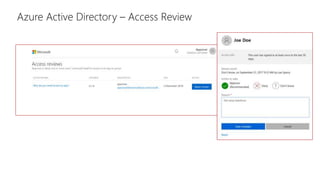
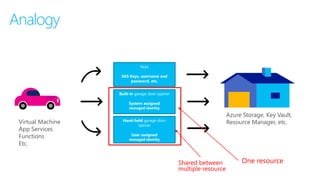
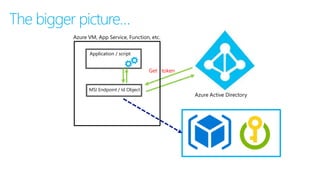
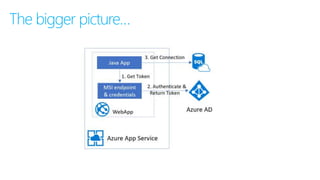
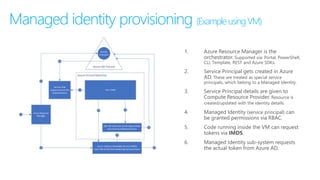
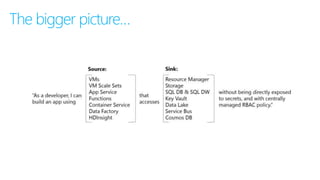
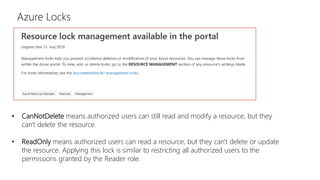
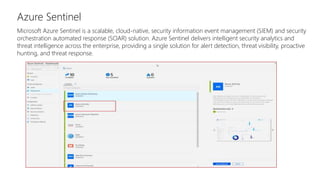
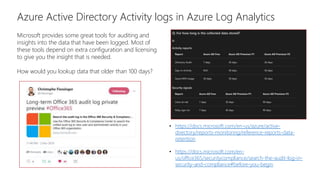
This document discusses basic governance in Azure, including Azure AD PIM, Azure Locks, and Azure AD Access Review. It provides an overview of Azure Sentinel for security information and event management. It also discusses managing secrets with Azure Key Vault and using managed identities for Azure resources.