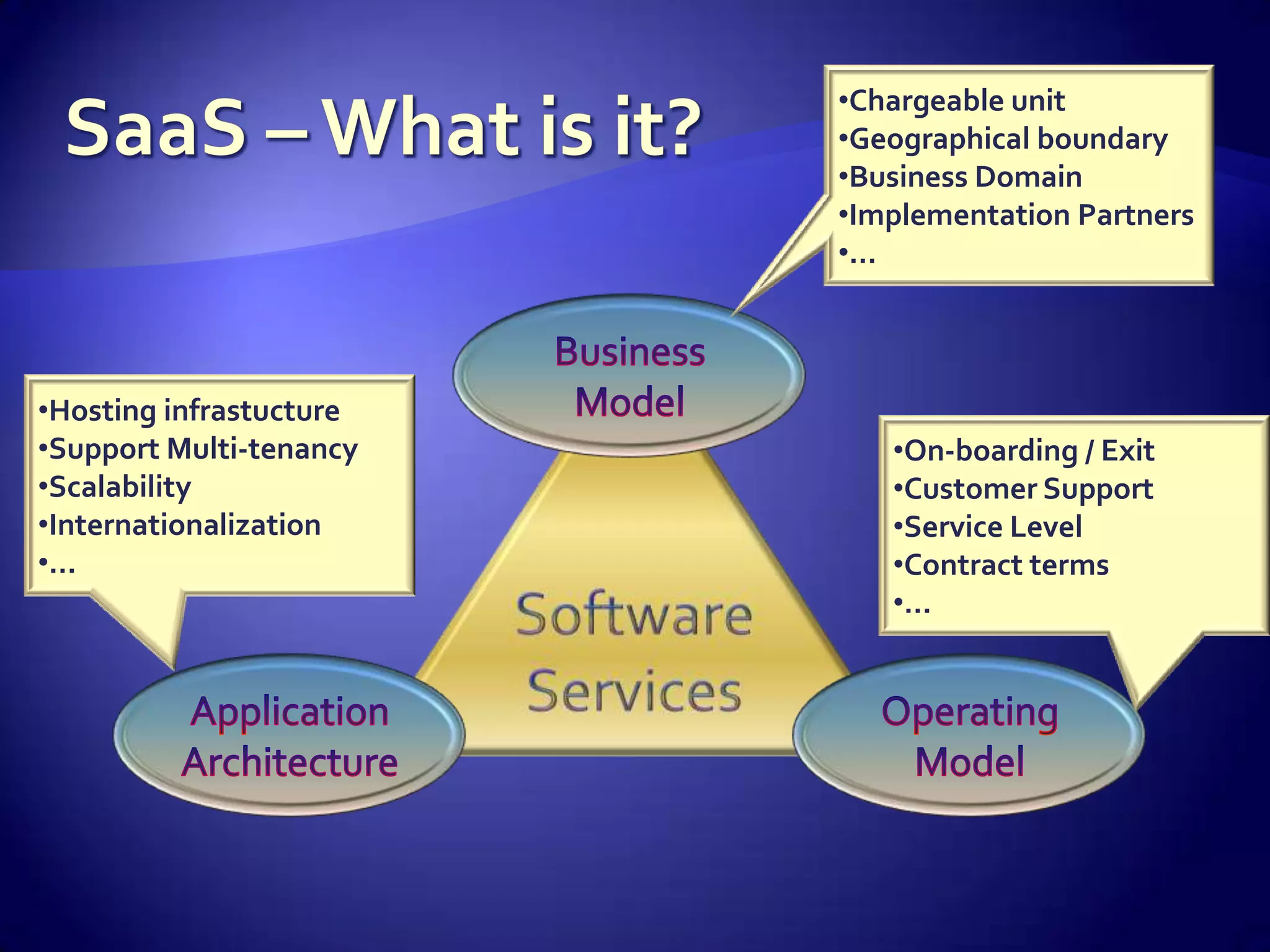
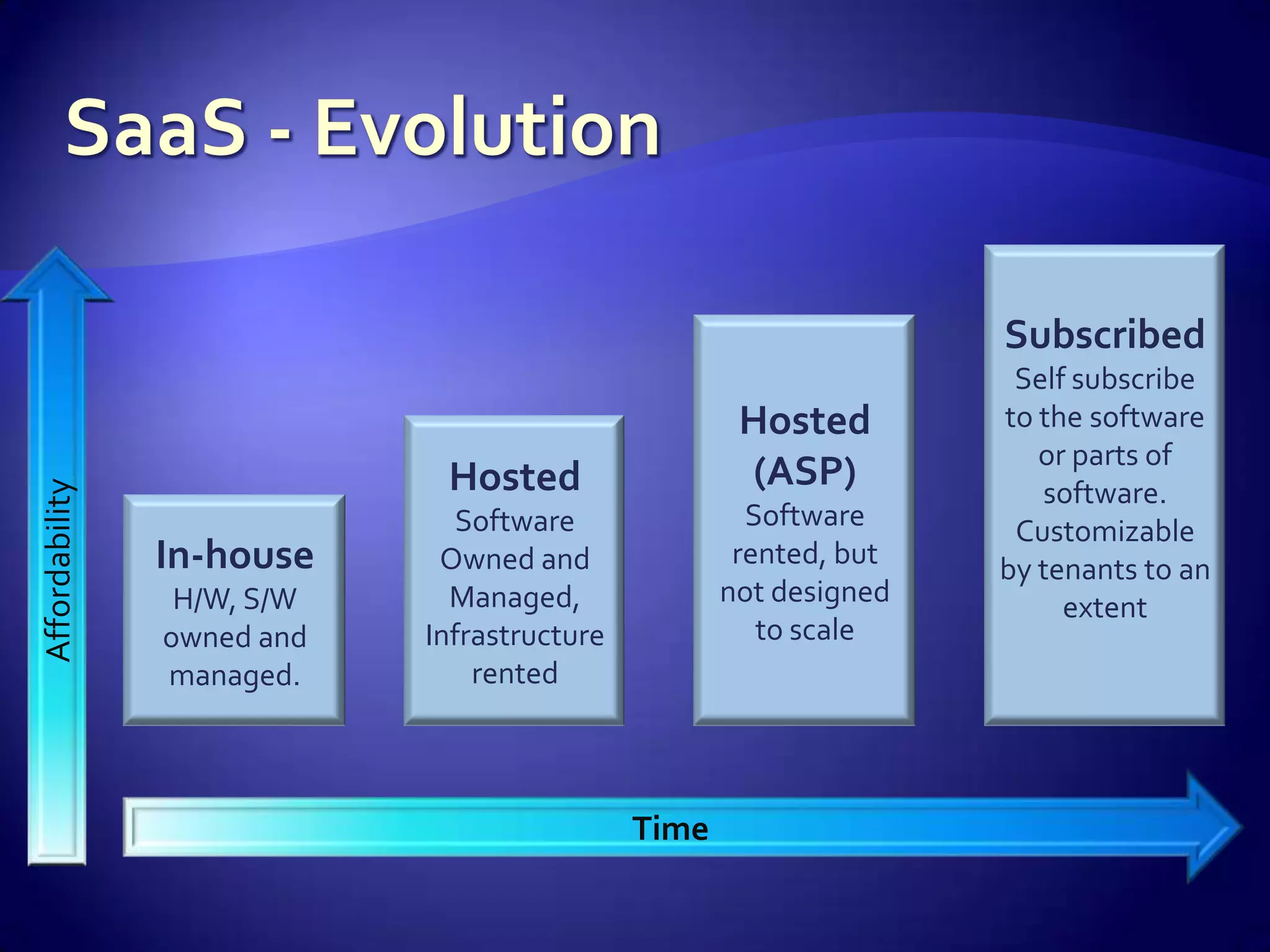
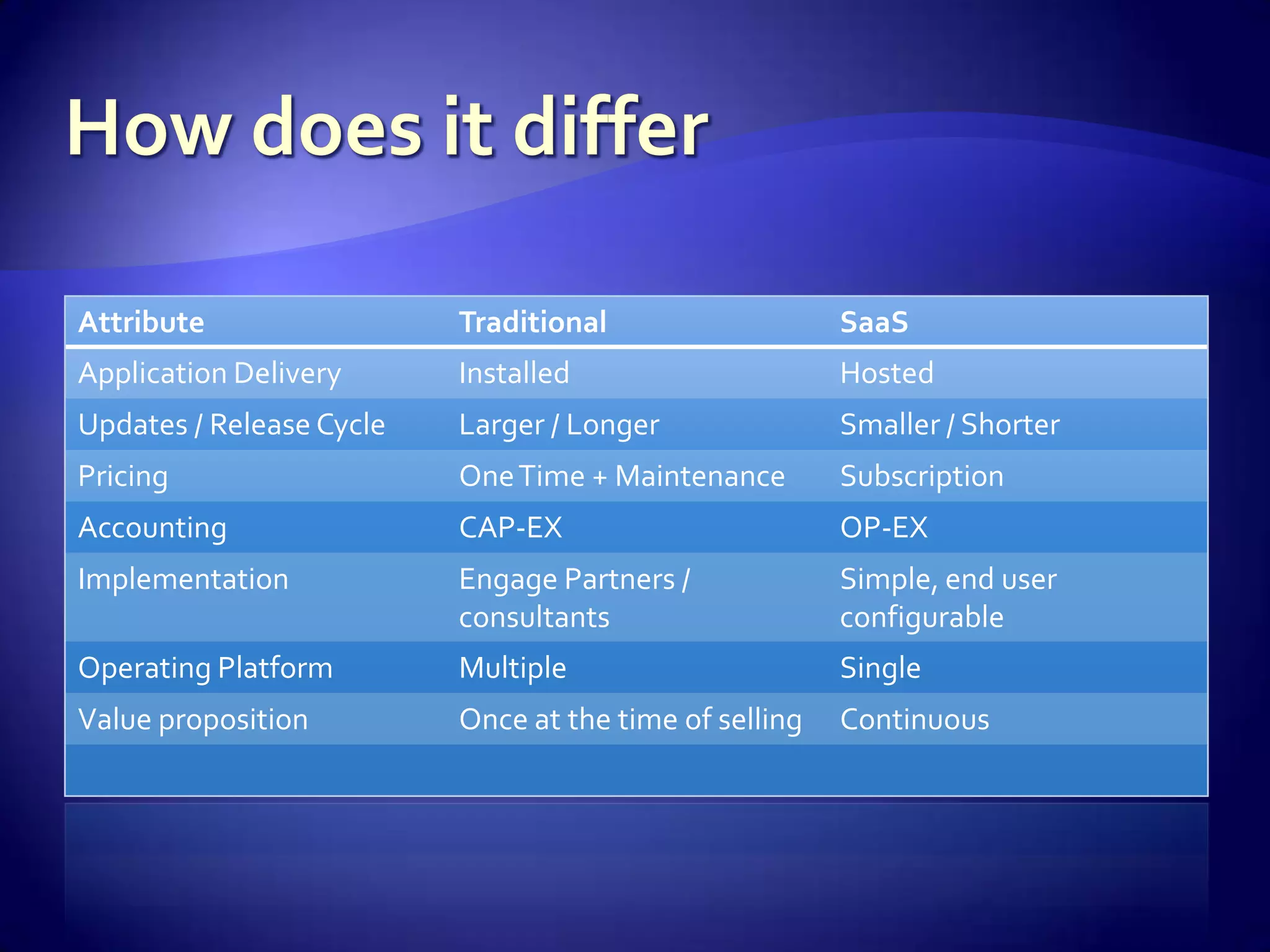
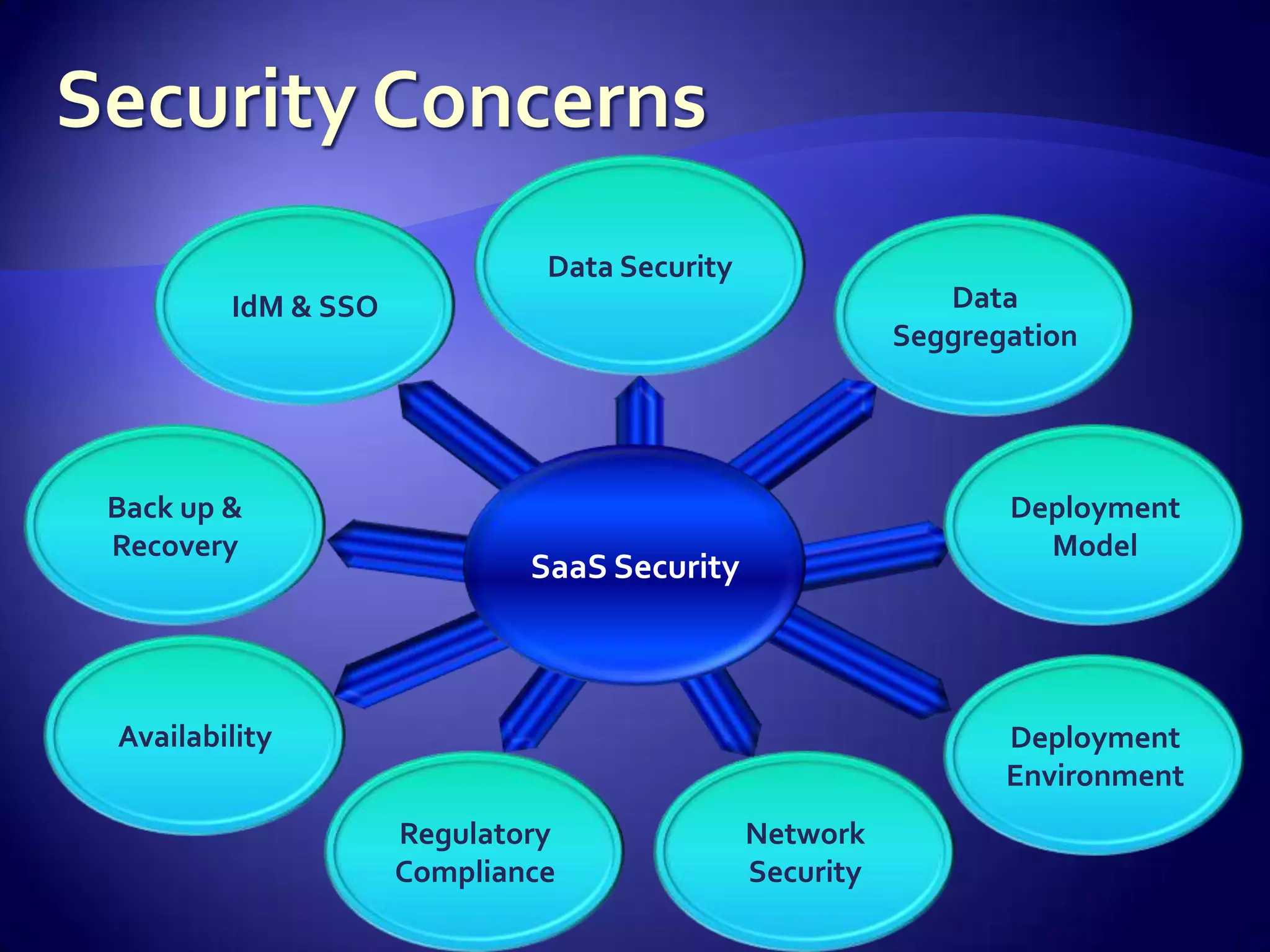
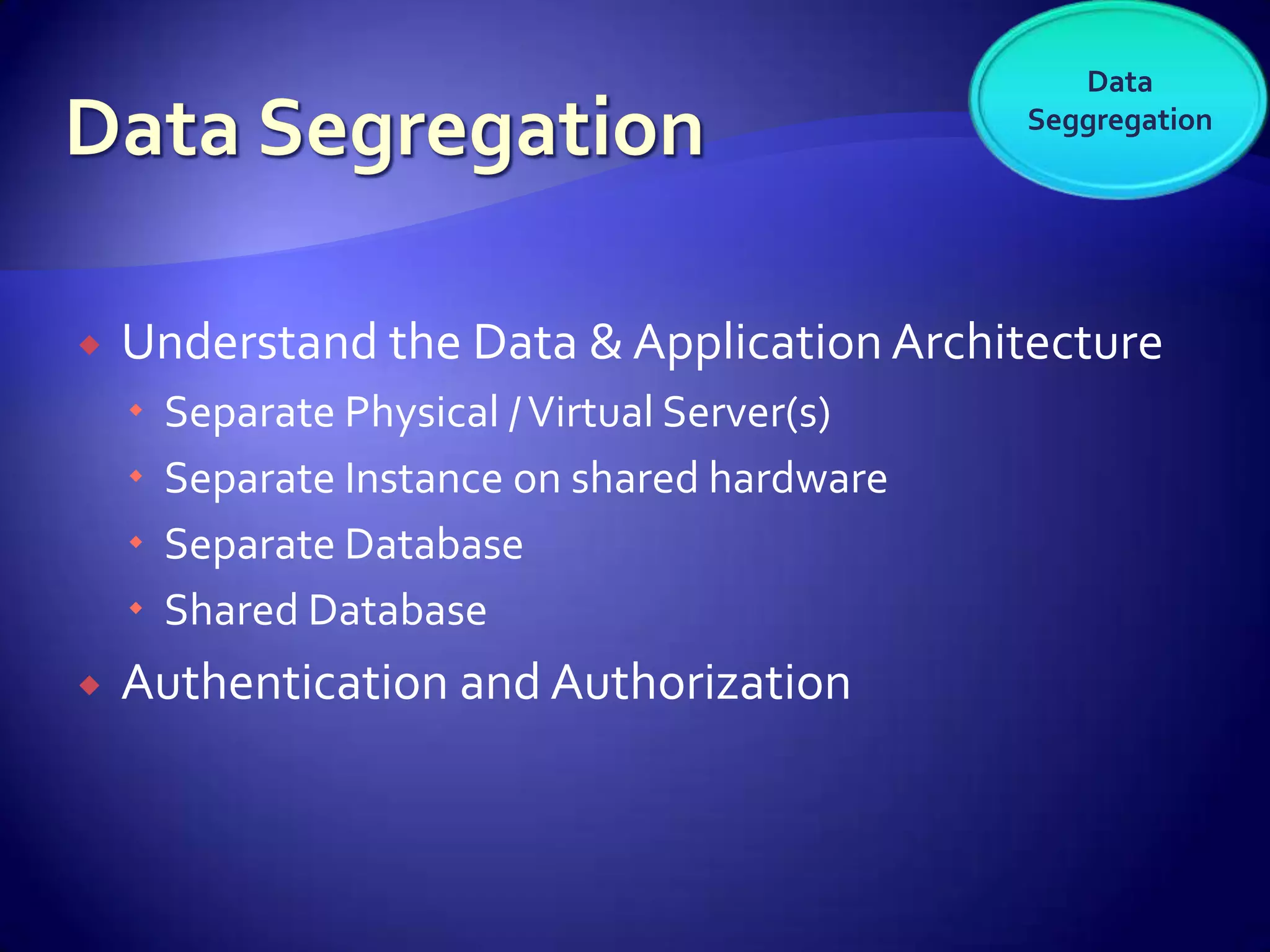
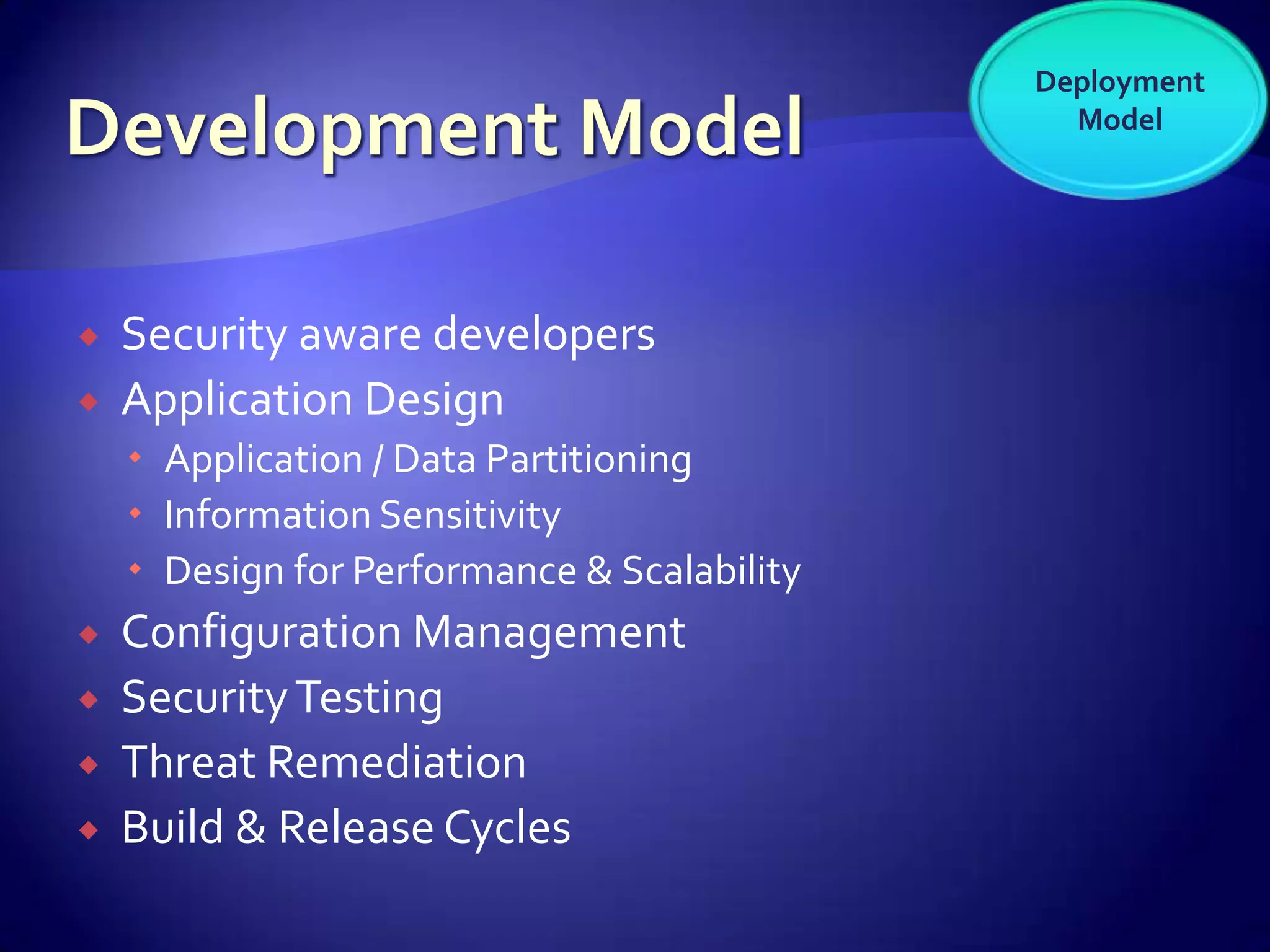
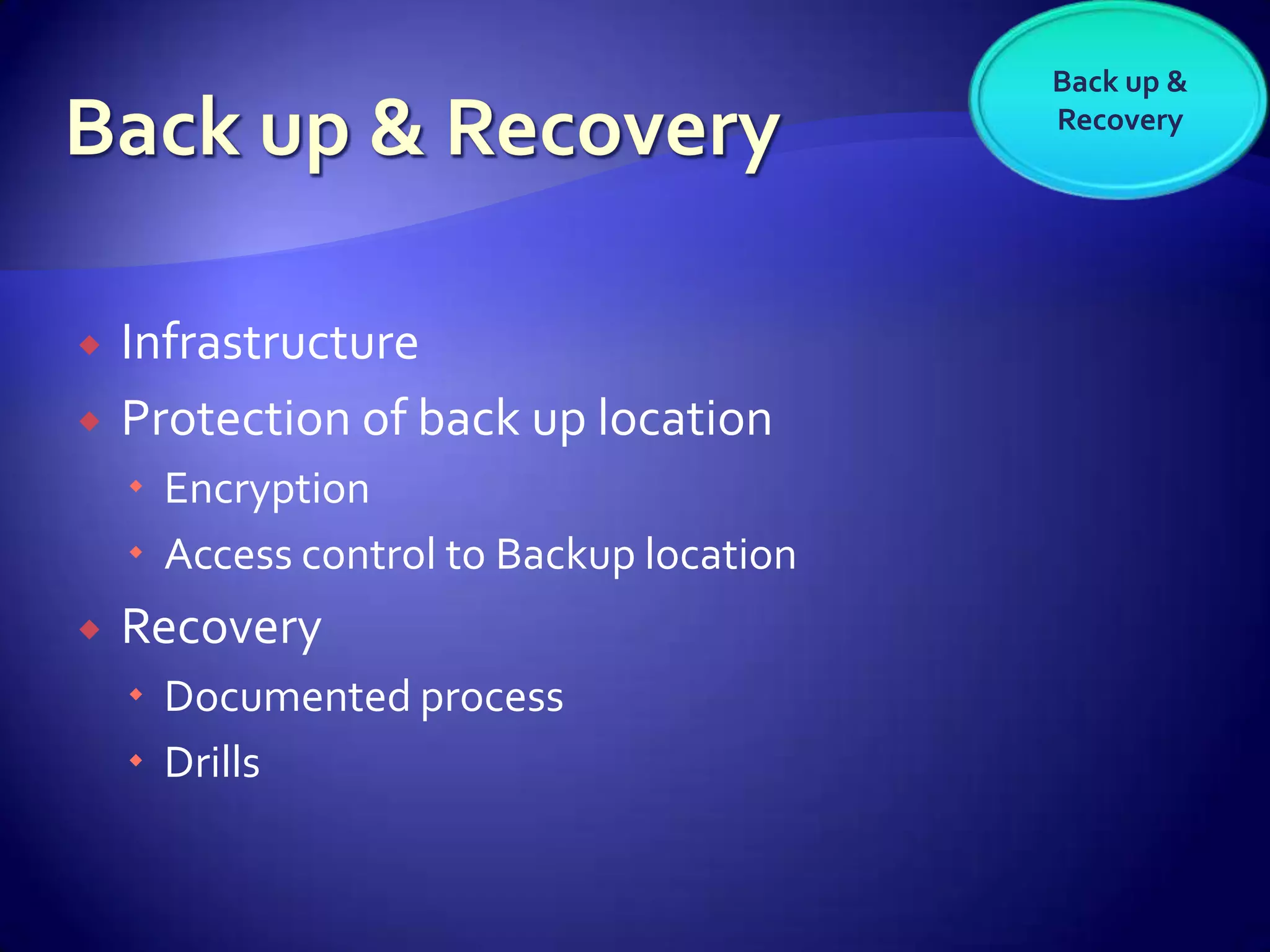
The document discusses various aspects of software as a service (SaaS) architecture, including multi-tenancy, scalability, customer support, and implementation strategies. It emphasizes the importance of security, regulatory compliance, and operational control within cloud environments, along with the transition from traditional software models to subscription-based services. Additionally, it outlines the design considerations for application security, data management, and customer retention strategies.