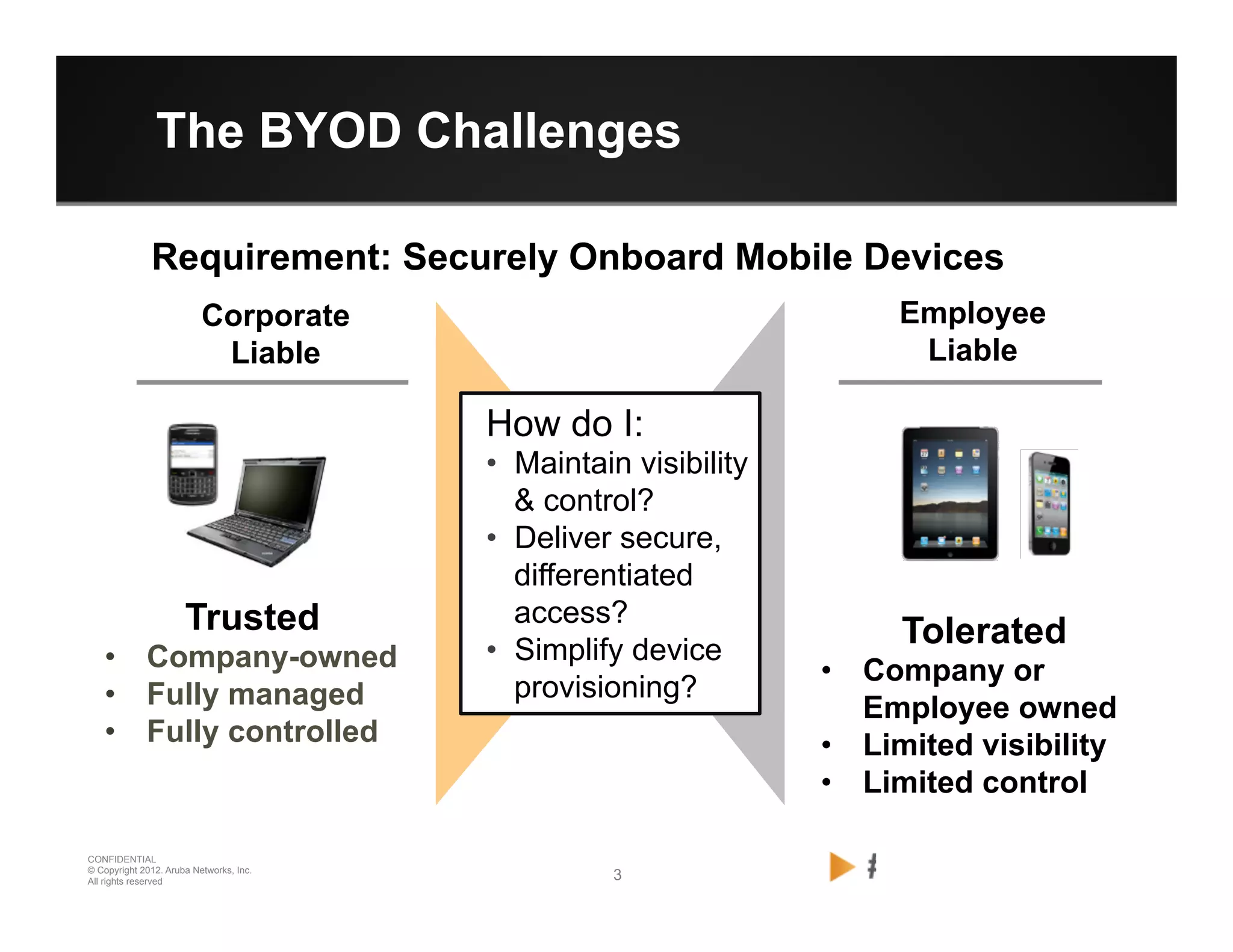
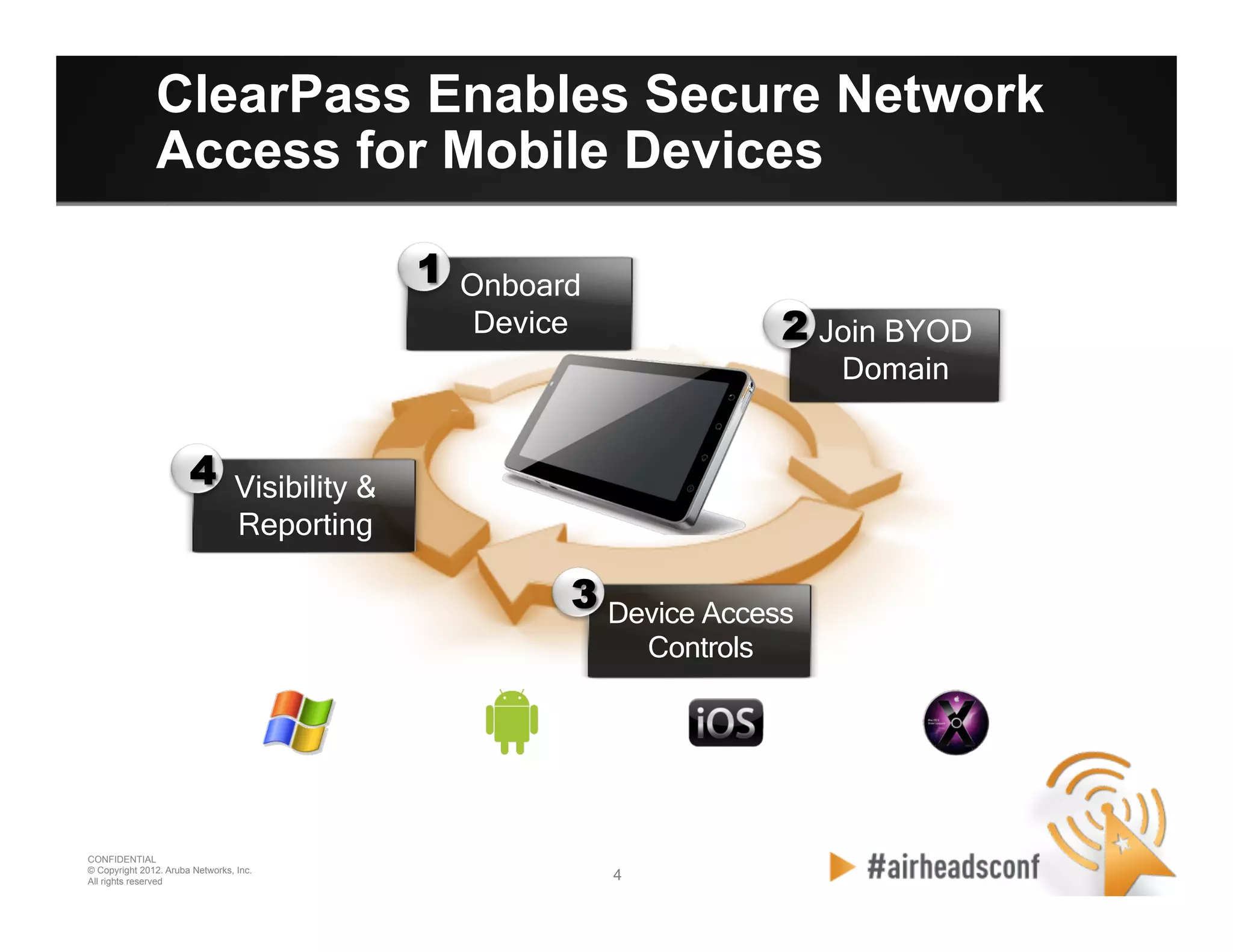
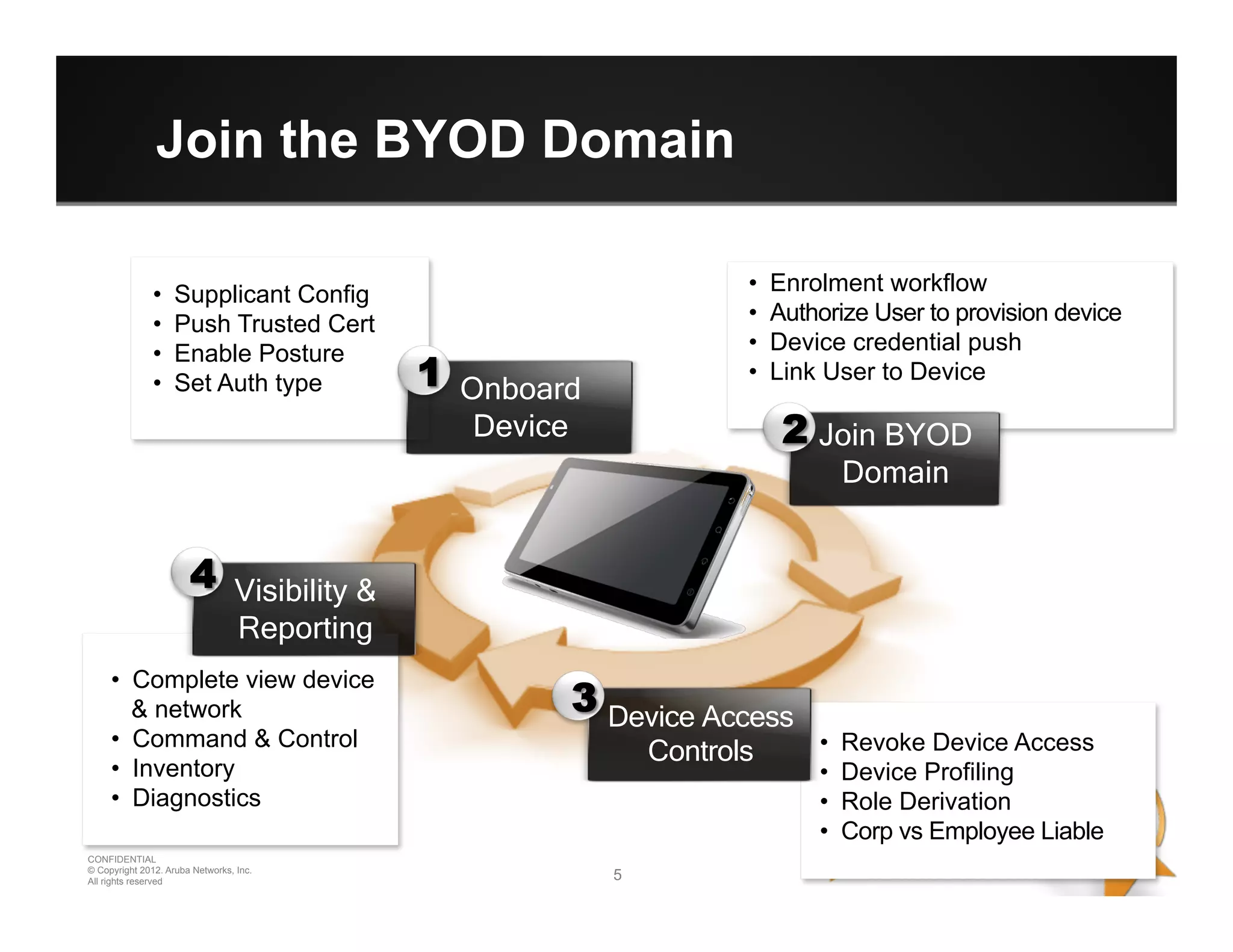
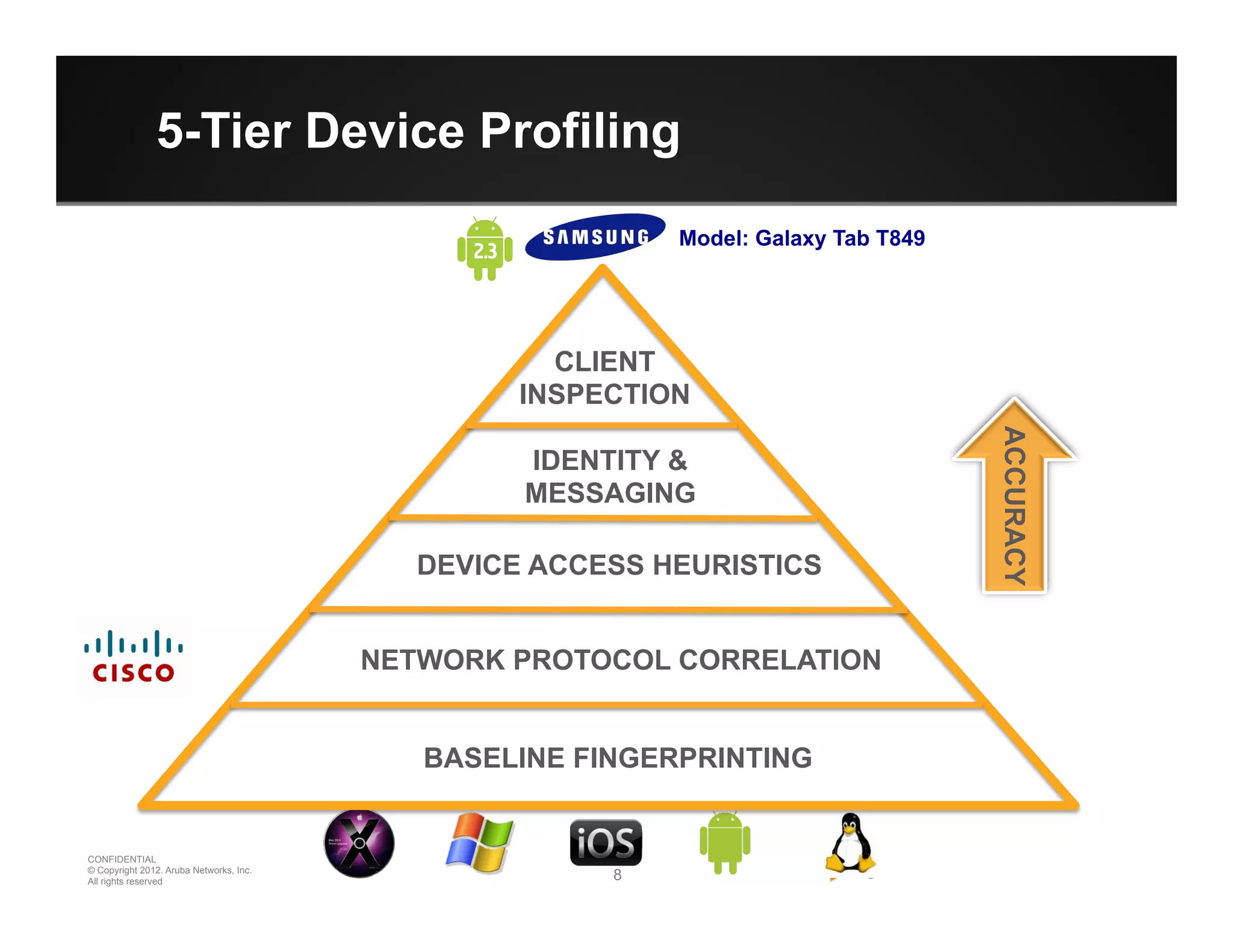
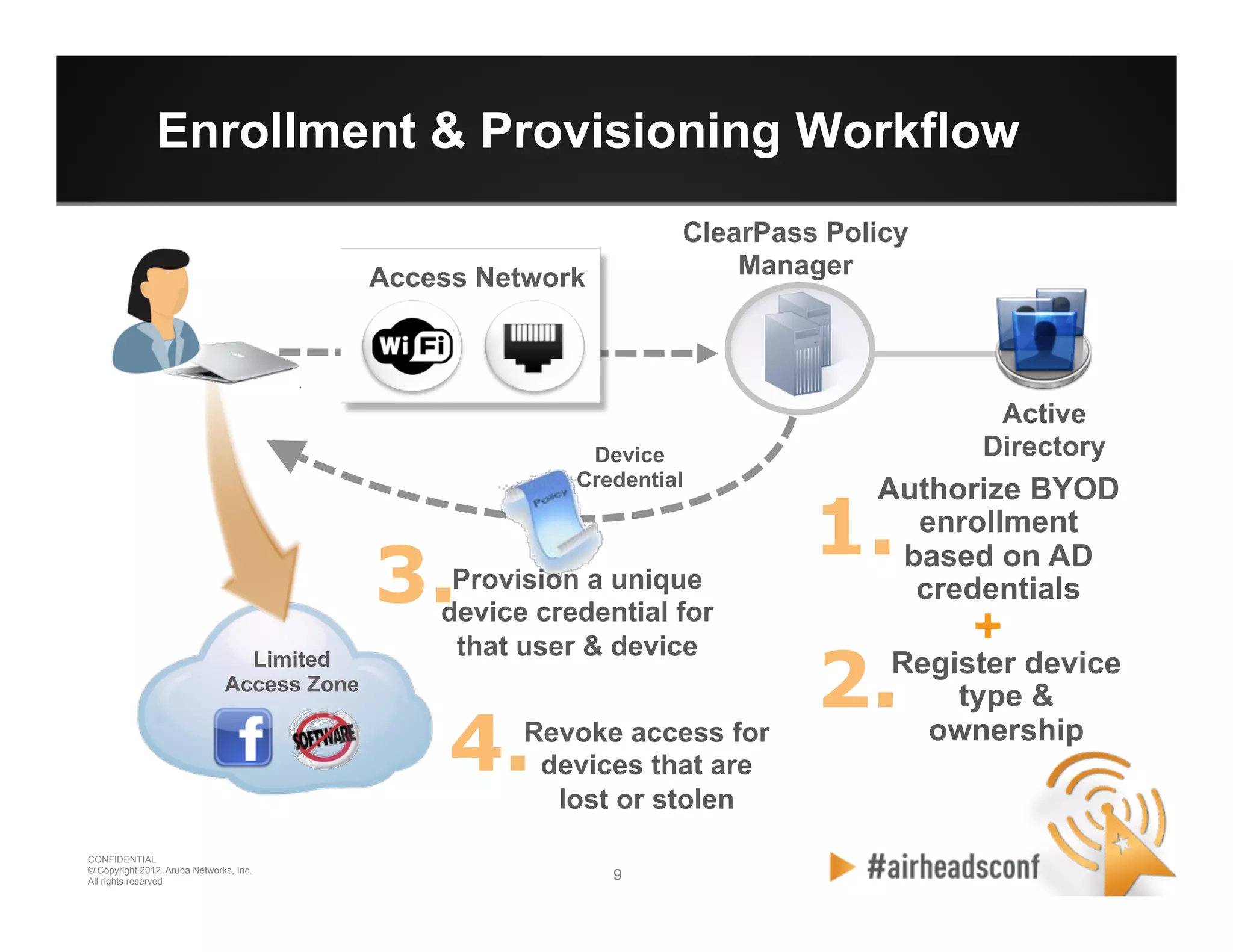
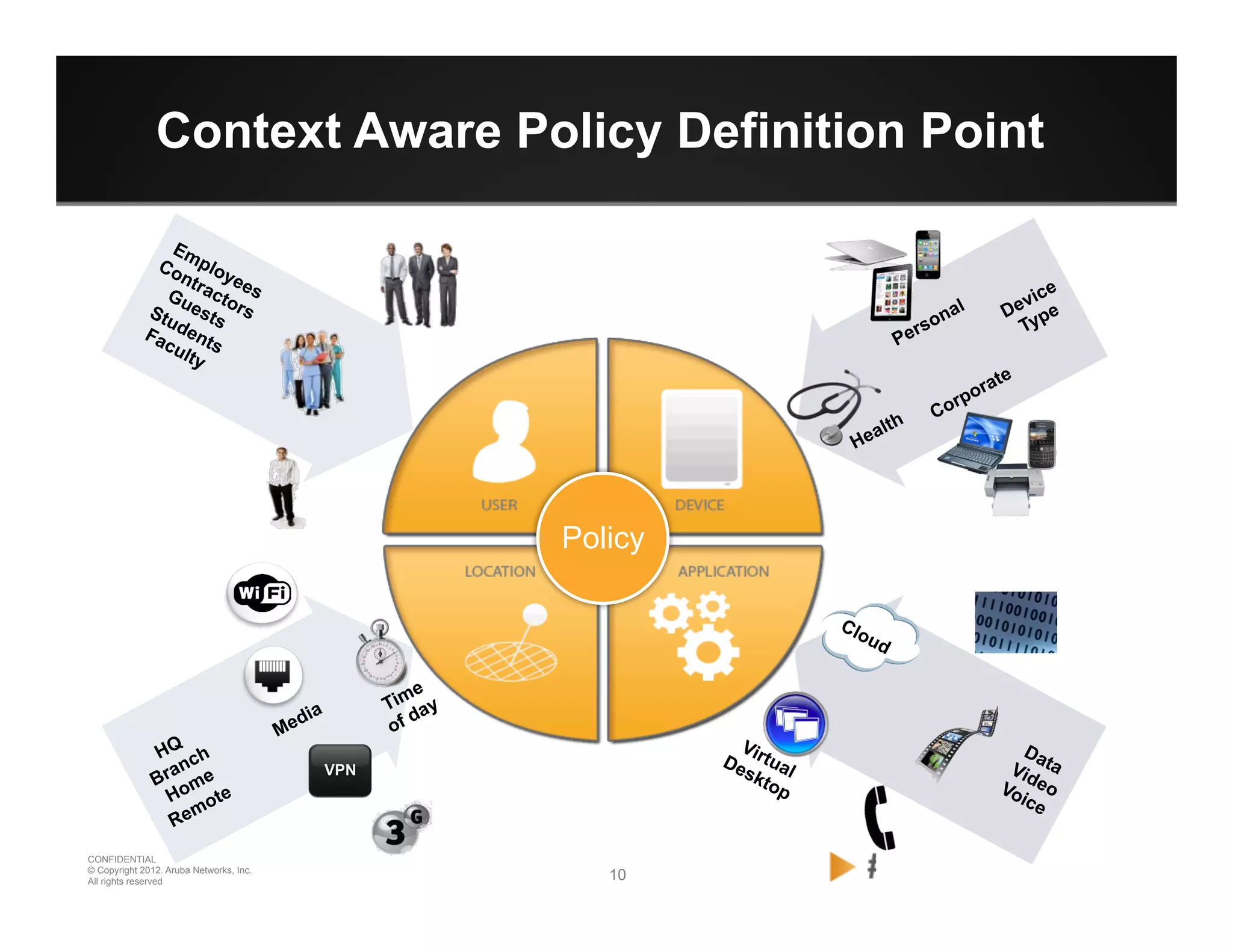
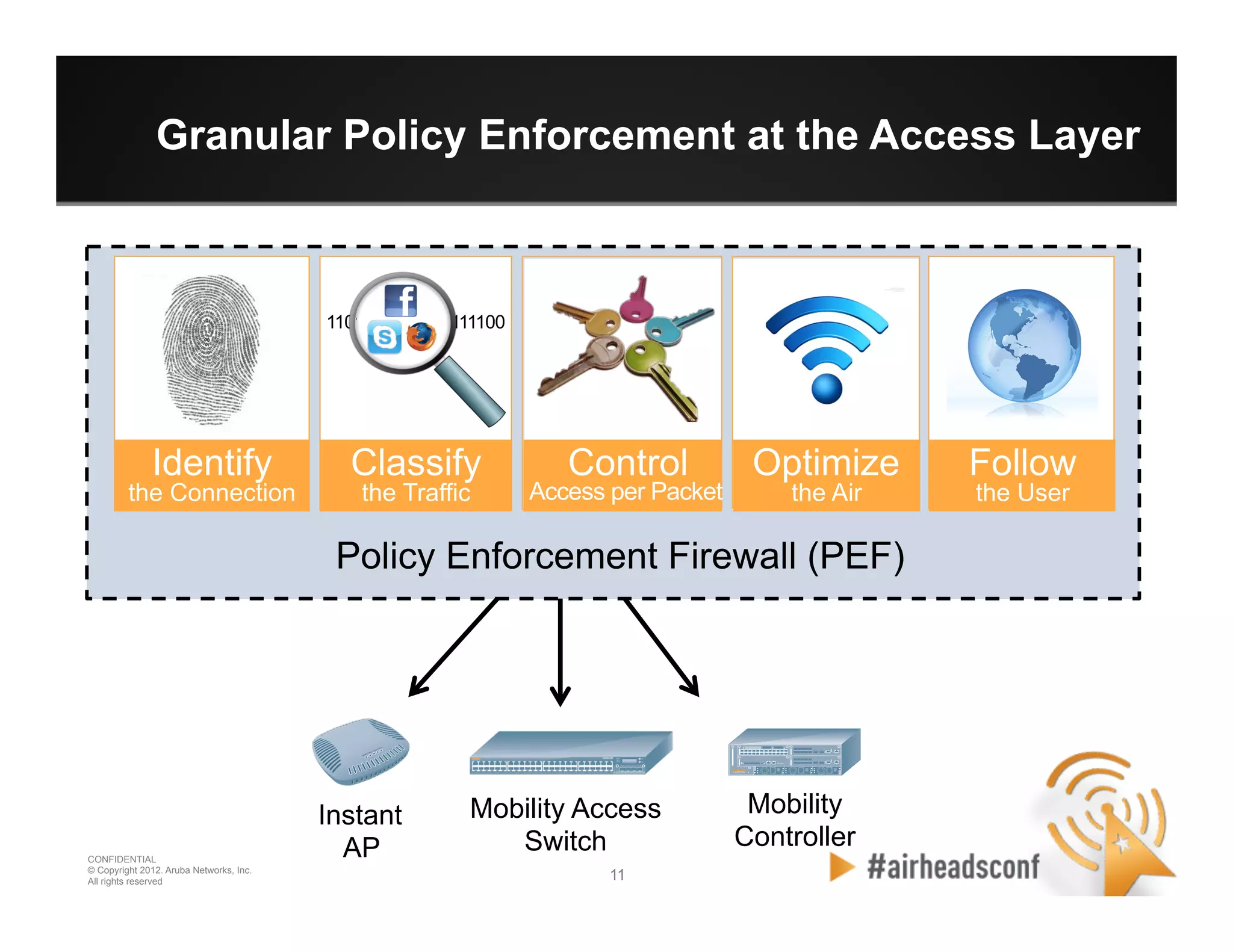
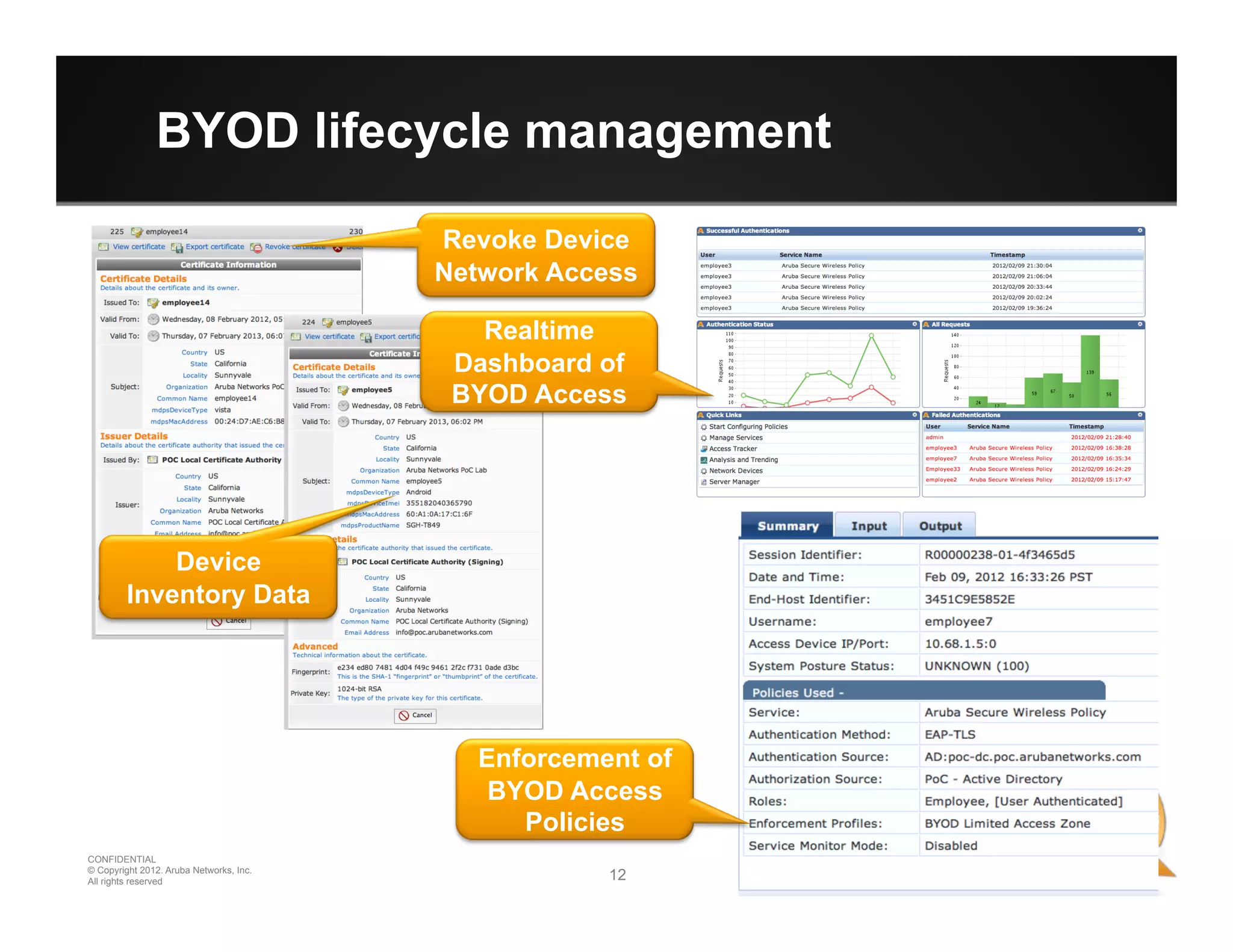
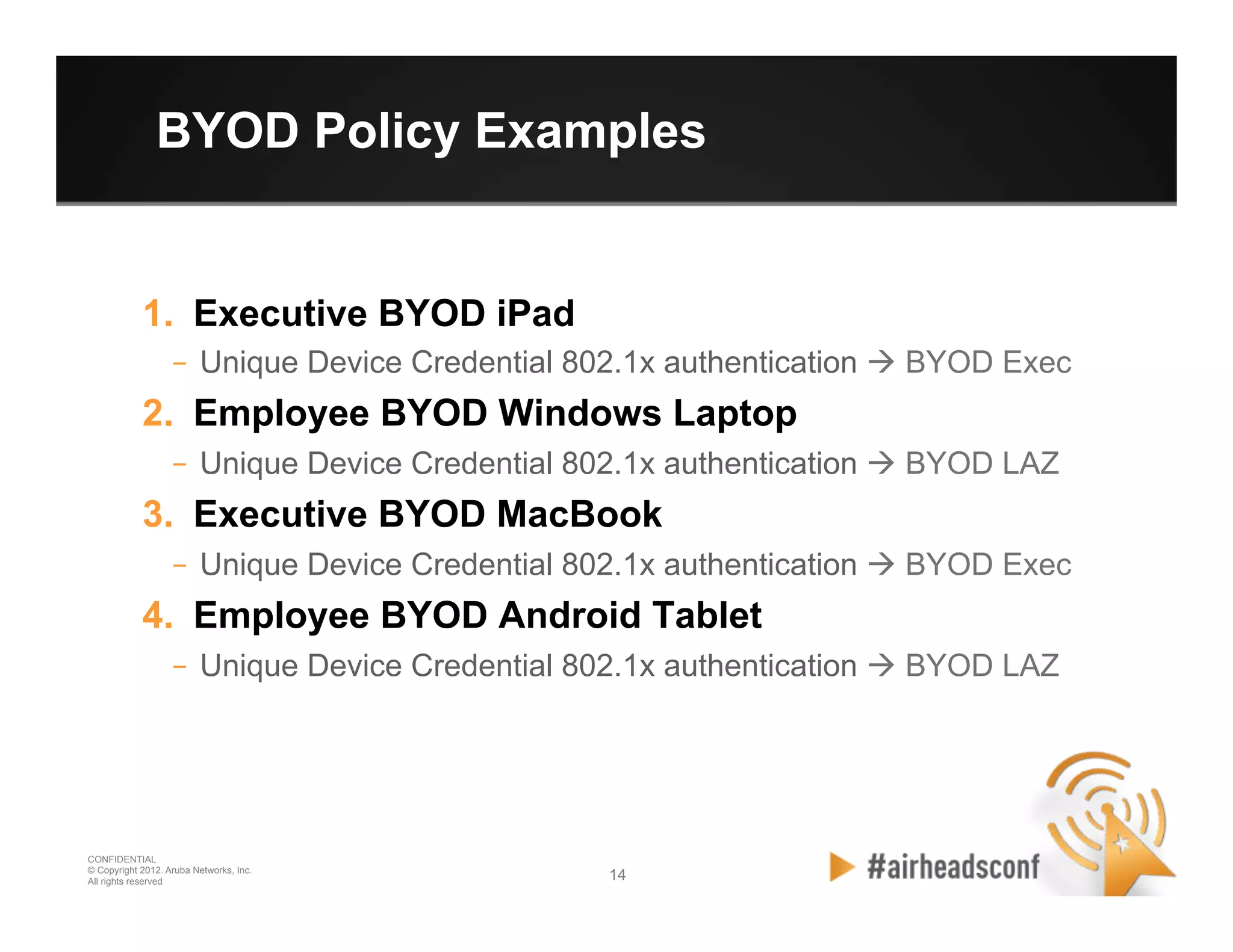
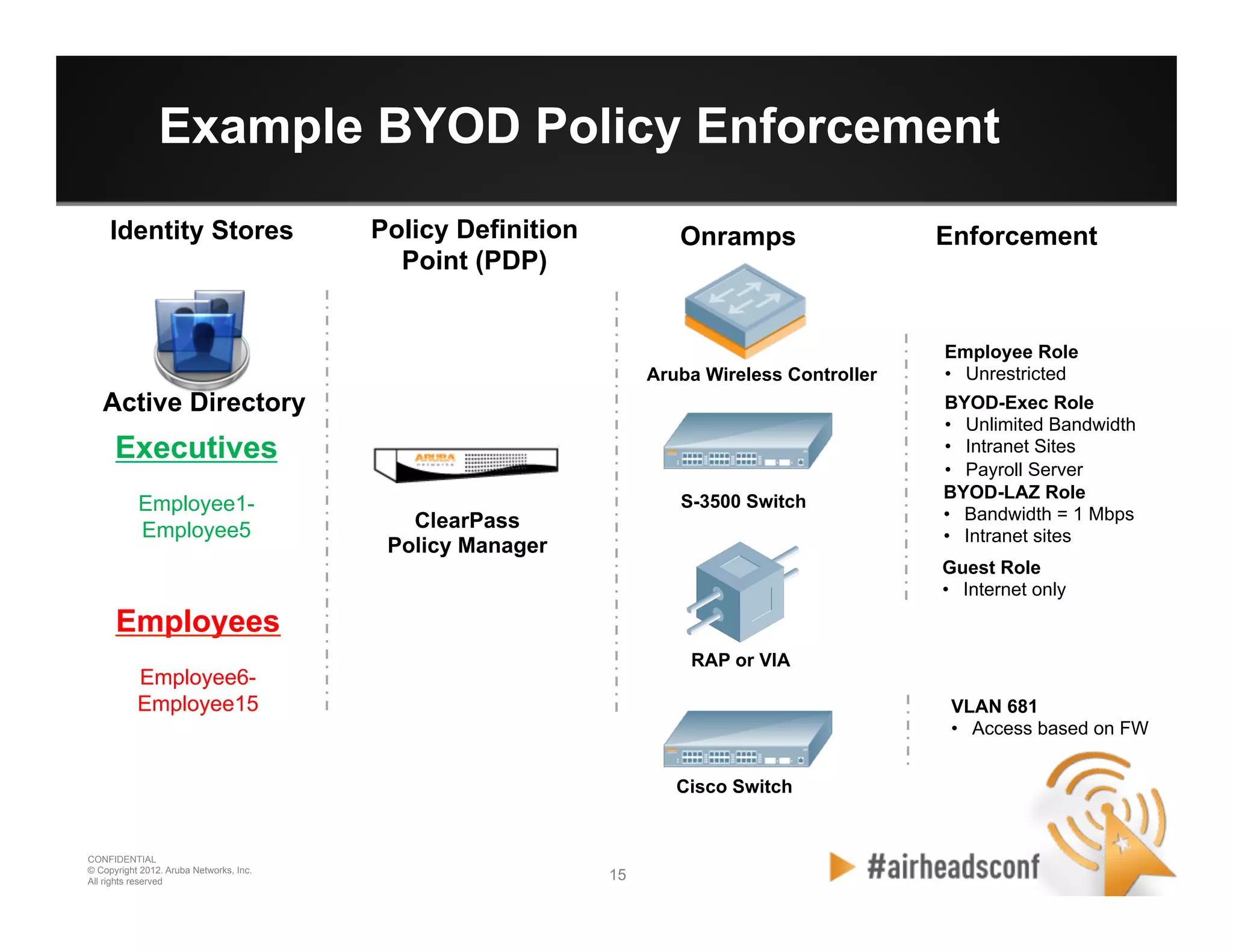
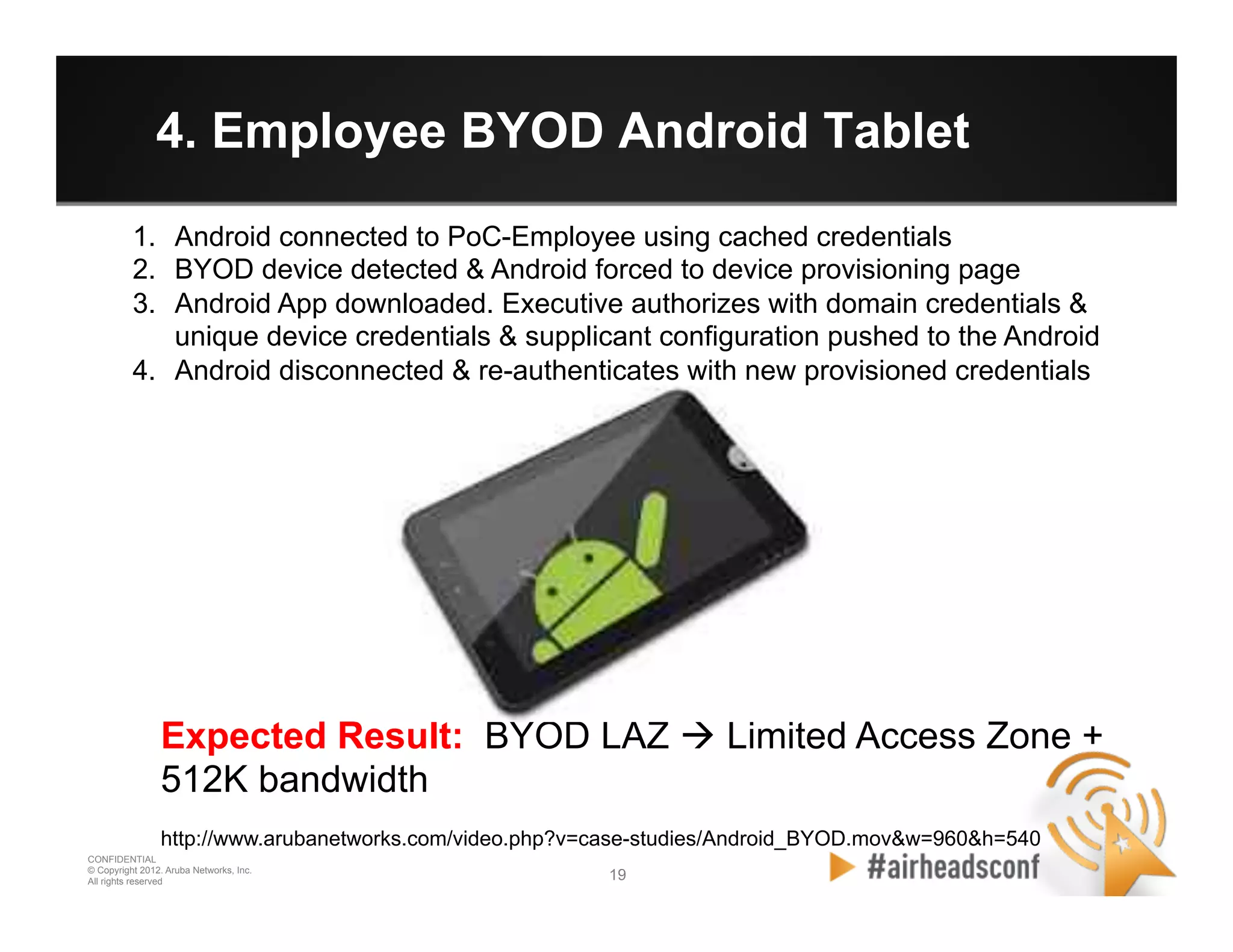
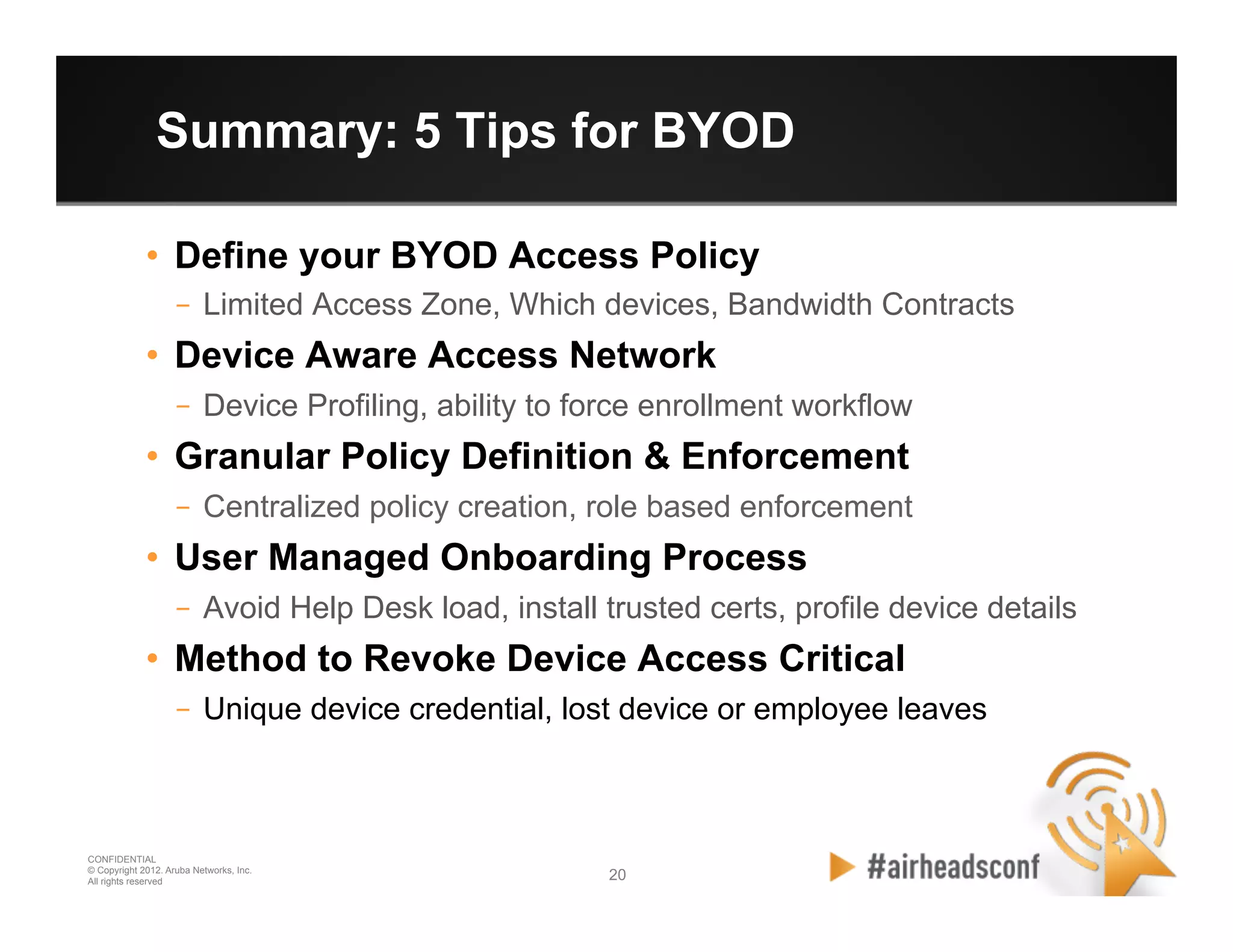
The document discusses how to securely onboard and manage personal devices on a corporate network through BYOD (Bring Your Own Device). It describes ClearPass for enabling network access for mobile devices by joining a BYOD domain, applying device access controls and visibility/reporting. ClearPass allows enrolling devices, provisioning credentials, linking users to devices, enforcing policies based on device/user attributes and revoking access when needed. The document provides examples of applying different access policies and network zones for executive vs employee devices like iPads, laptops and tablets.