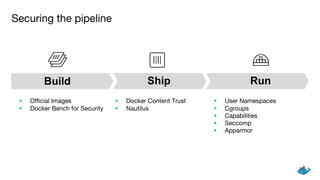
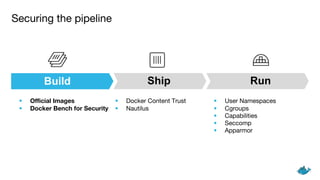
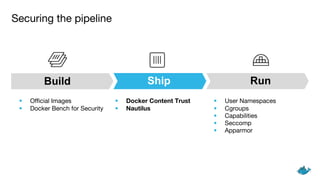
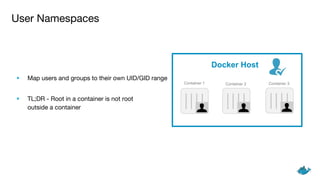
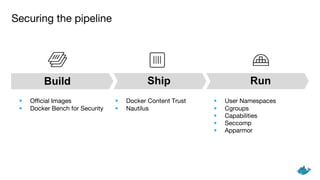
The document outlines security measures for container management, emphasizing the importance of using official images, Docker Bench for Security, and Docker Content Trust. It highlights key technologies such as user namespaces, cgroups, capabilities, seccomp, and AppArmor to ensure a secure pipeline during the build, ship, and run phases. The content stresses the need for auditing, vulnerability scanning, and systematically managing resource usage for effective container security.