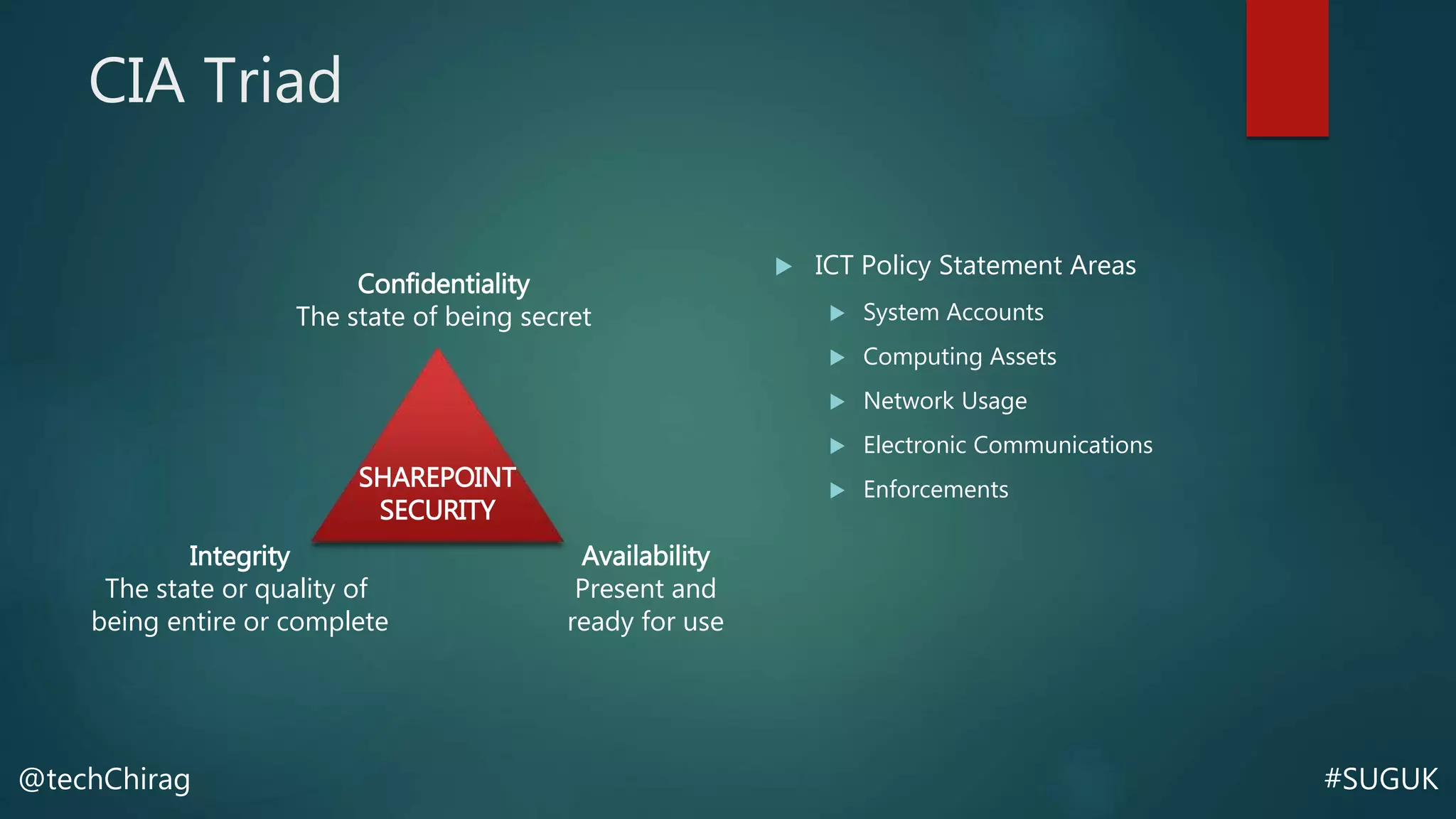
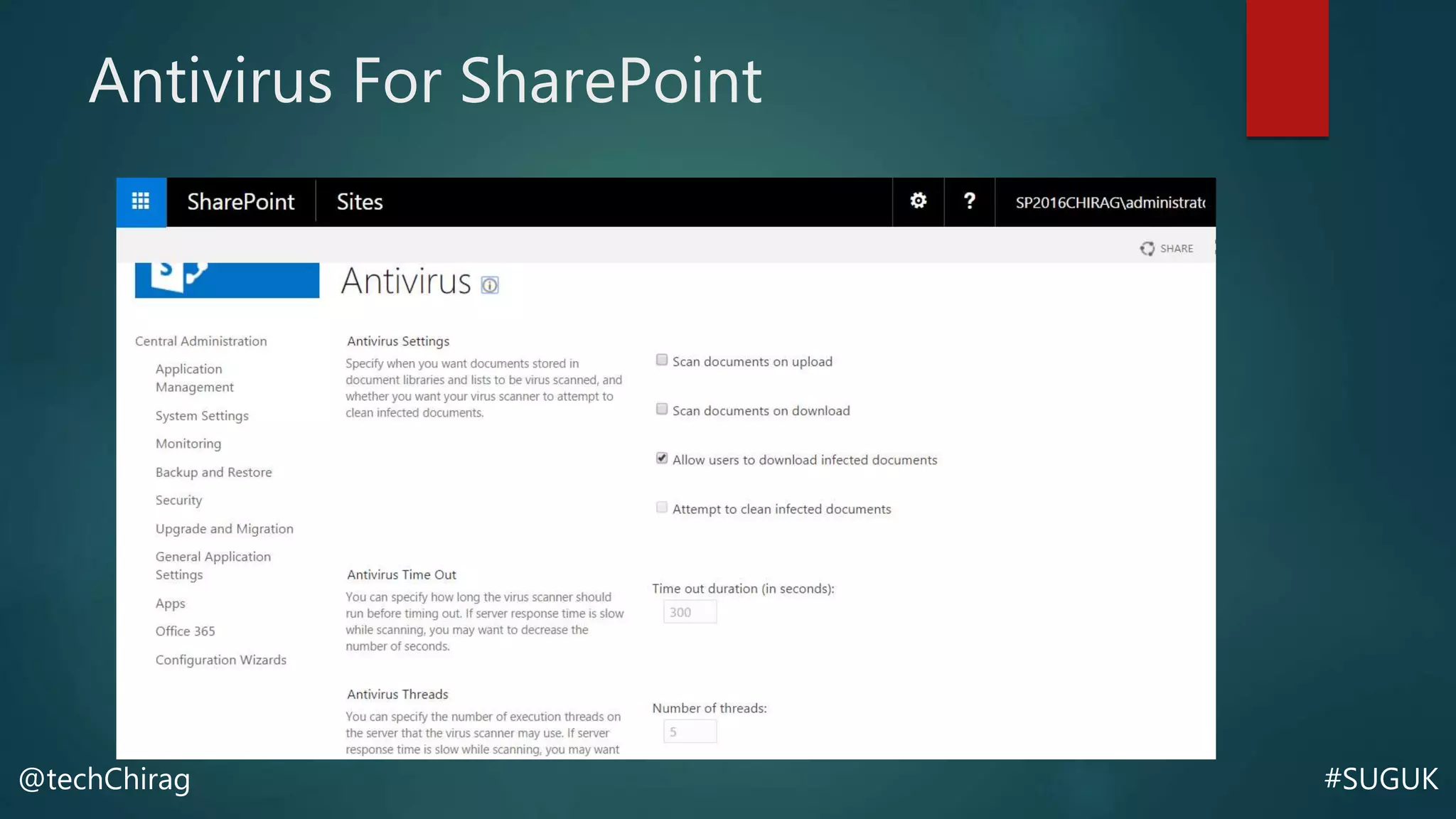
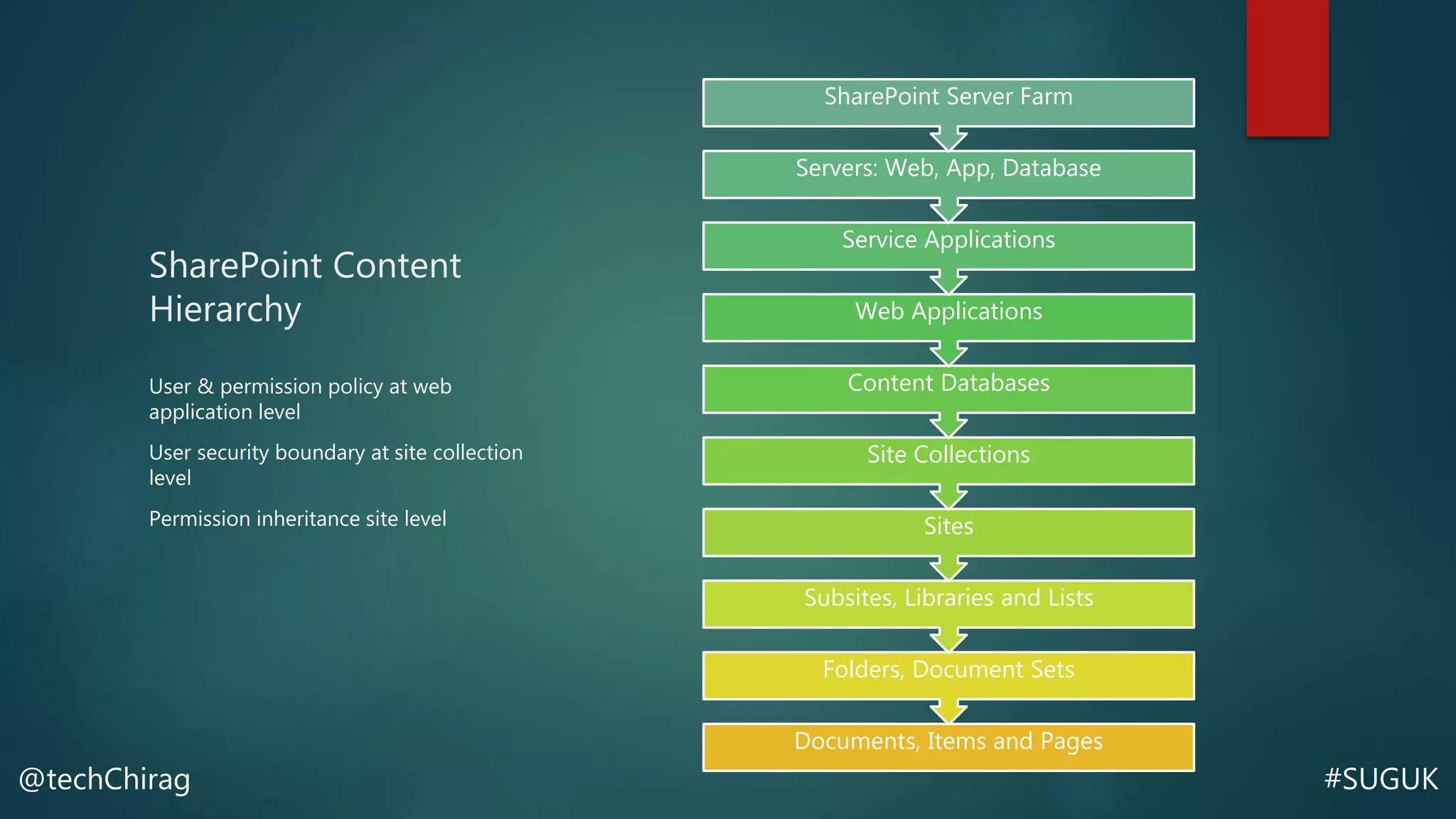
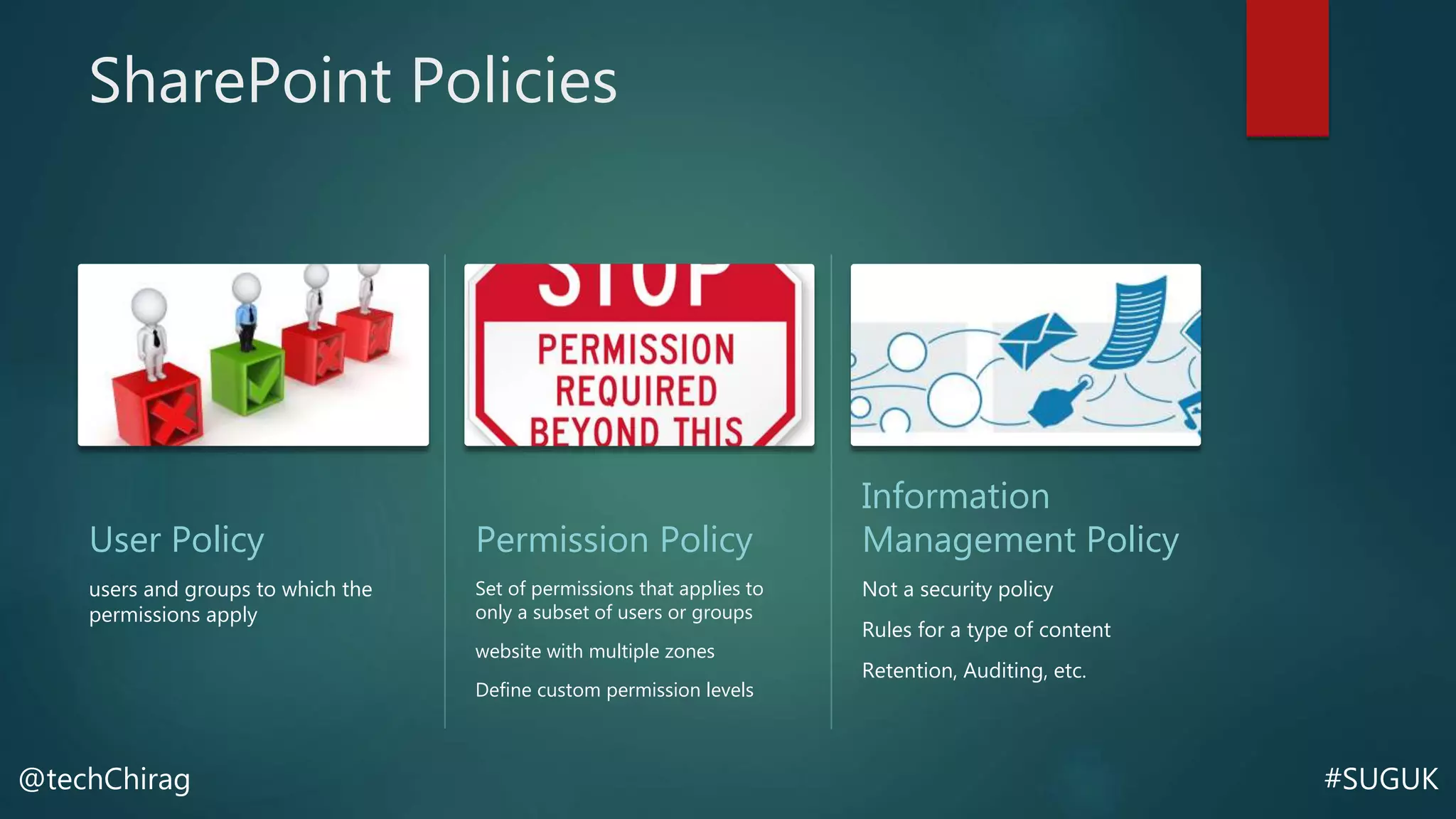
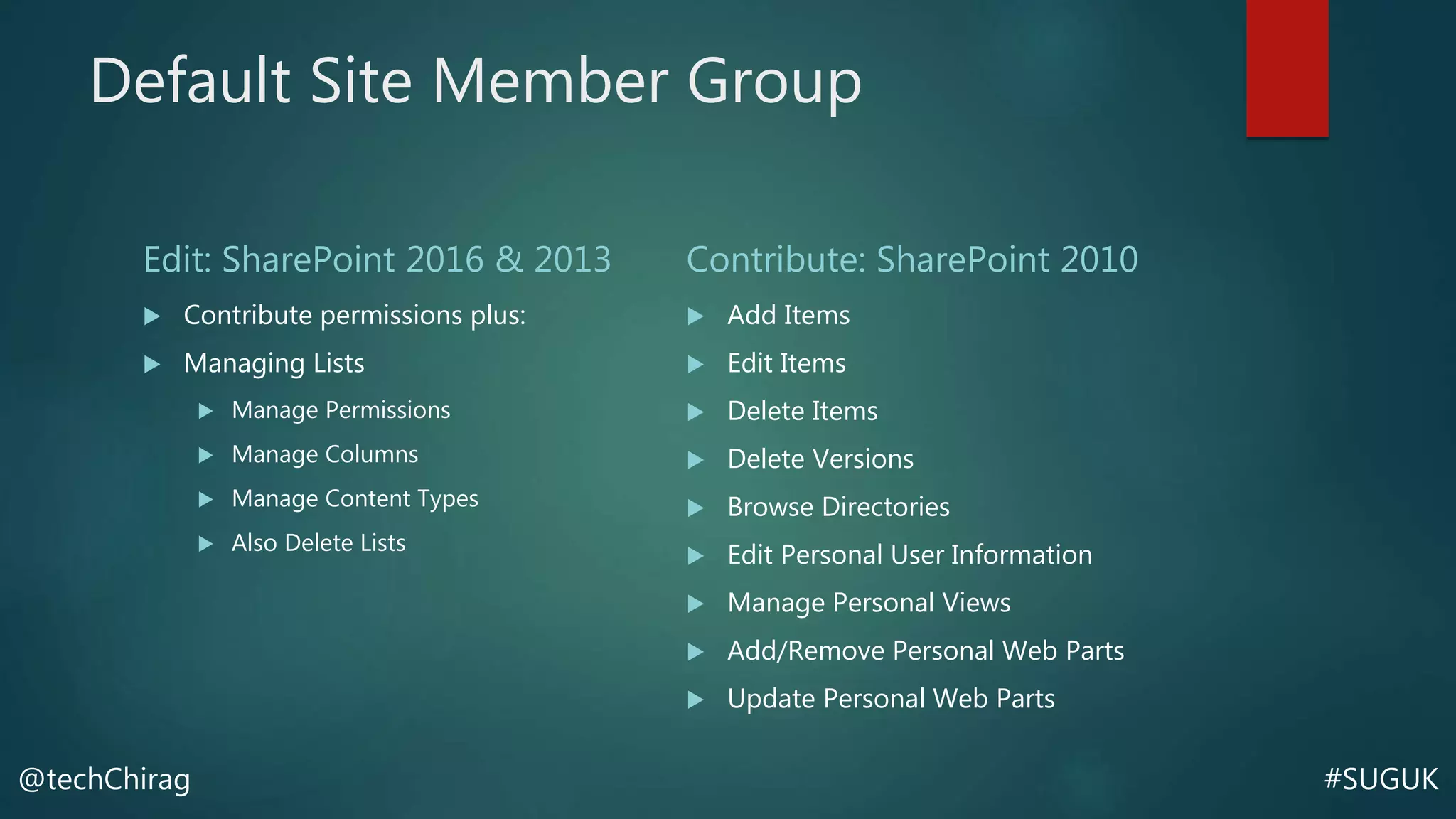
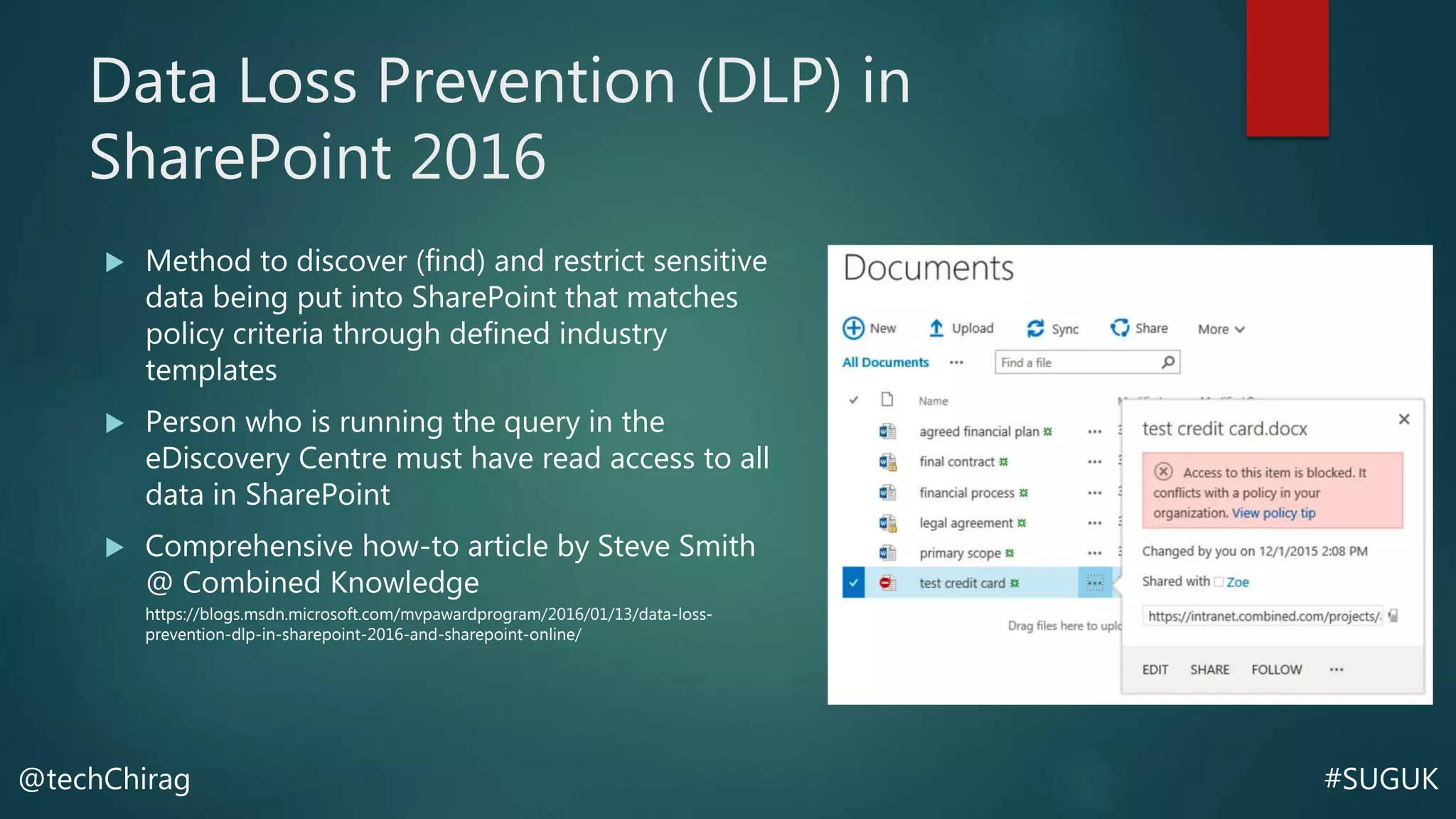
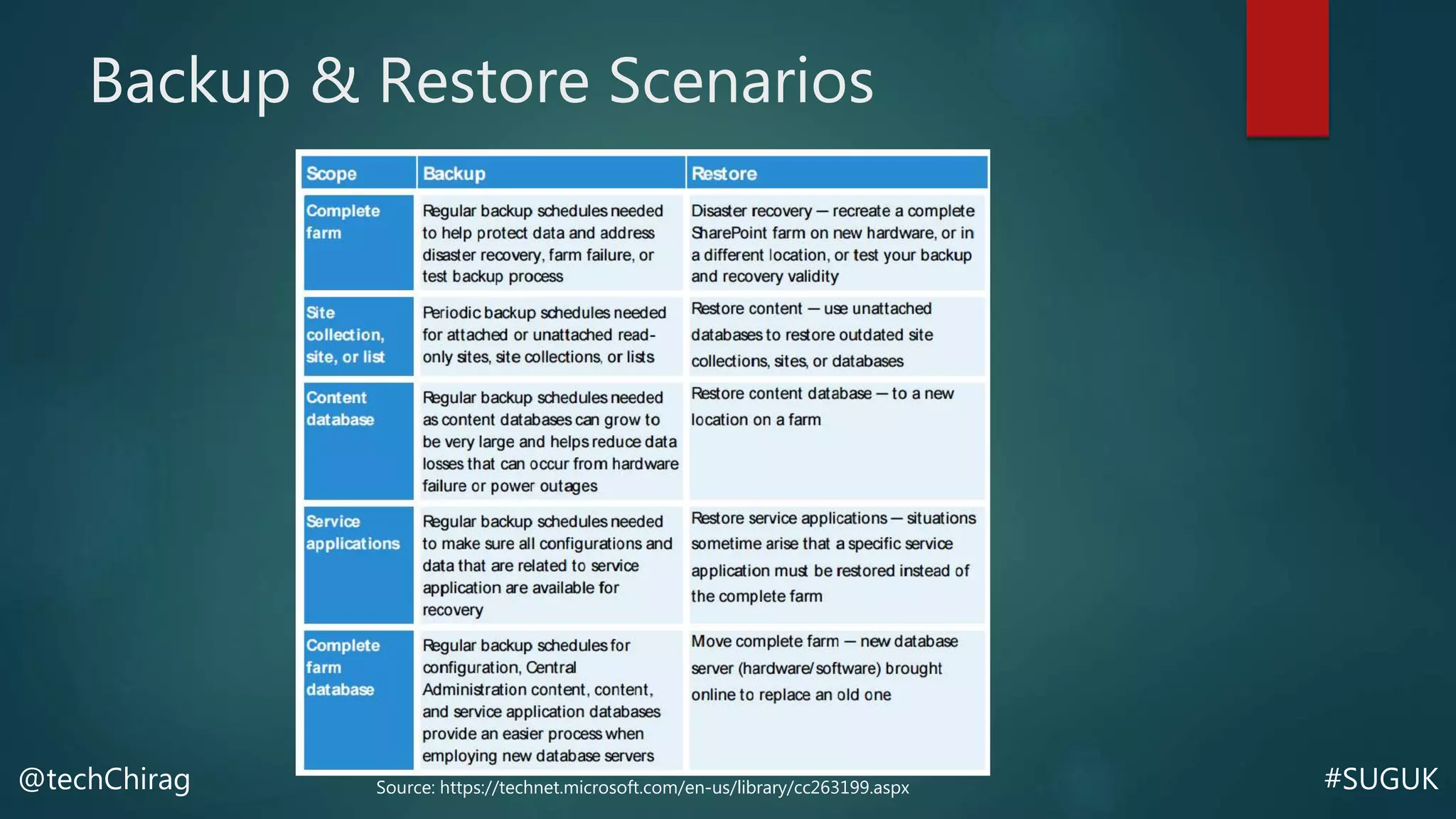
This document summarizes Chirag Patel's presentation on securing the SharePoint environment and content. It discusses key security concepts like the CIA triad of confidentiality, integrity and availability. It provides best practices for platform security, authentication, encryption and antivirus in SharePoint. It also describes the various administrator roles and how to define policies for users, permissions, information management and external sharing. Finally, it covers content security, managing audiences, data loss prevention, backups and restores in SharePoint.