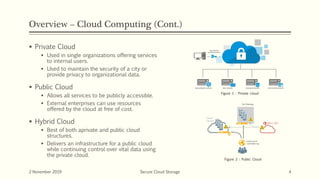
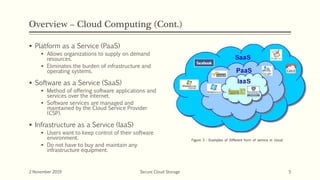
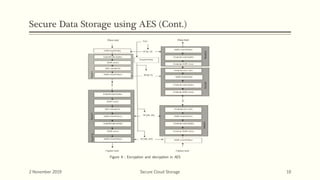
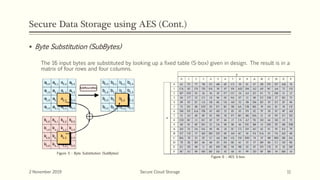
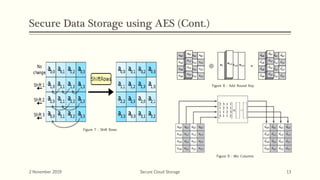
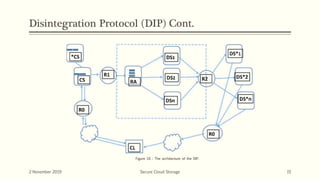
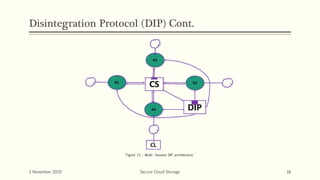
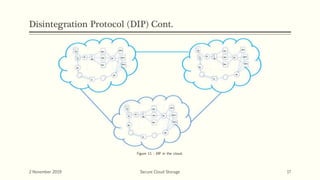
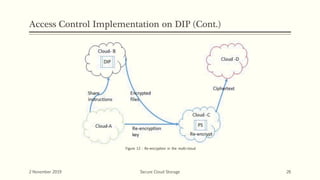
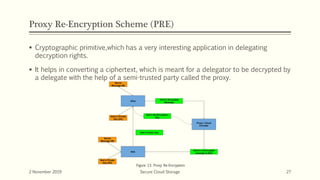
The document discusses secure cloud storage. It proposes using the Disintegration Protocol (DIP) to securely store data across multiple cloud servers. DIP distributes data fragments and services across different servers. Access control mechanisms like login credentials and security questions are implemented on DIP. The document also discusses using AES encryption for secure data storage and the Proxy Re-Encryption Scheme (PRE) to allow secure sharing of encrypted data files between cloud users.