This document is a project report that proposes developing a web application to securely store files on a cloud server using hybrid cryptography. It aims to address data security and privacy issues for cloud storage. The application would use a hybrid cryptography technique combining symmetric and asymmetric encryption to encrypt files before uploading them to the cloud. Only authorized users with decryption keys would be able to access and download encrypted files from the cloud server. The report outlines the problem statement, objectives, methodology, design, and implementation of the proposed application to provide secure file storage on the cloud.

















![CHAPTER 2
LITERATURE SURVEY
The proposed system has been implemented after extensively studying various related works
in hybrid cryptography, steganography, attribute-base encryption and cloud-oriented dis-
tributed file storage.
2.1 Hybrid Cryptography
A hybrid cryptosystem is a protocol using multiple ciphers of different types together, each
to it’s best advantage. One common approach is to generate a random secret key for a
symmetric cipher, and then encrypt this key via an asymmentric cipher using the recipient’s
public key. The message itself is then encrypted using the symmetric cipher and the secret
key. Both the encrypted secret key and the encrypted message are then sent to the recipient.
[1] proposes the cryptography technique translates original data into an unreadable form.
The cryptography technique is divided into symmetric-key cryptography and public-key
cryptography. This technique uses keys to translate data into an unreadable form. So only
authorized persons can access data from the cloud server. Cipher-text data is visible for all
people. In the existing system, a single algorithm is used for data encryption and decoding
purposes. But the use of a single algorithm is not accomplished high-level security. If we
use a single symmetric key cryptography algorithm then we have to face a security problem
because this type of algorithm applies a single key for data encryption and decryption. So
the key transmission problem occurs while sharing key into a multi-user environment. Public
key cryptography algorithms accomplish high security but the maximum delay is needed for
data encryption and decryption.
7](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-18-320.jpg)

![system is done using java language. File encoding and decoding time is calculated with the
help of java programming. File encryption and decryption time is calculated for only text
file with comparison of existing AES and Blowfish algorithms. File size is given in MB for
AES algorithm. That is 1MB, 2MB, 4MB and 8MB.For encryption and decryption time
calculation of blowfish algorithm for given file size 100KB, 200KB, 400KB and 800KB is
calculated in sec.
2.2 Steganography
Steganography is the technique of hiding secret data within an ordinary, non-secret, file or
message in order to avoid detection; the secret data is then extracted at its destination. [1]
also proposes steganography to hide the secret data existing into an envelope. In this tech-
nique existence of data is not visible to all people. Only valid receiver knows about the
data existence. Text steganography technique is used to produce high security for data.
Secret data of user hide into text cover file. After adding text into text cover file, it looks
like normal text file. If text file found by illegitimate user, then he cannot get sensitive
data. If illegitimate user tries to recover original data than large amount of time is used
for text encryption and decryption. Advantage of text steganography technique is providing
security to text. Minimum space is essential for text steganography as compare to image
steganography. [1] uses three-bit LSB technique for image steganography. Sensitive data of
user is hidden into cover image. We can hide huge amount of data/key into image using
LSB steganography technique.
2.3 Attribute-Based Encryption
Attribute-based encryption is a type of public-key encryption in which the secret key of a
user and the ciphertext are dependent upon attributes, [2] proposes this method of encryp-
tion. Distributed computing empowers pervasive access of the information assets. Remote
information stockpiling and Outsourced designation calculation and so on., these are the
9](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-20-320.jpg)

![there considerably presently sit tight two issues. The individuals regardless you quit offering
on that one may be their need no improvement to understanding CP-ABE for every one
circuits, which may be conceptually closer ought widespread passage control. Those inverses
might be identifier with those efficiency, since the individuals exiting out ABE arrangement
will make simply A contact encryption representative. Thus, it may be clearly at present
sits tight a pivotal open issue for framework A proficient ring round CPABE arrangement.
The steps in uploading and downloading of files propsed in [2] are as follows -:
1. Encrypting party who upload file (i.e. .txt) his encrypted data will be stored in the
cloud and generate public and master Key.
2. Authority attribute key generator (i.e. Public, Private, Master) center (trusted third
party).
3. User’s decrypting party who download file select attribute and encrypted file.
4. User’s decrypting party who outsources the most overhead computation to the cloud
Using Public and Own Private Key.
5. System generate public, private and master key based on key attribute.
6. Decrypt file using encrypted file using public key and private key.
7. User verify file using MAC value. To check that downloaded file is correct file or not.
Figure 2.1: Uploading File
11](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-22-320.jpg)
![Figure 2.2: Downloading File
2.4 Owner Defined Attribute Encryption
The owner defined attribute-based encryption allows a data owner to define the access control
policy and enforce it, [3] proposes the owner defined attribute-based encryption and stores
data in different cloud servers. The phrase Cloud specifies to a Network or Internet. In
another term, we can say that Cloud is something, which is present at remote location.
Cloud computing is commonly used technology in the IT infrastructure. Cloud computing
offers more storage capacity. Use advanced computer skills to learn and solve problems.
Cloud computing is a long-dreamed vision of the usefulness of the computer, which is present
on the Internet to accumulate, store data rather than a personal computer or hard drive.
Currently, cloud computing technology is mainly used to store large amounts of data. In
this environment, cloud servers consider different types of services, such as remote processing
of information and processing of outsourced delegation data. Cloud Computing used to
controlling, aligning, and obtaining the hardware and software resources remotely. The
cloud server used to insert a wide range of information, which can only be accessed by
authorized users. In the delegation process, servers are used to manage and determine data
based on user requirements. The result shows, attribute-based encryption. However, there
are some problems and queries regarding the previous related works. For example, during
the delivering or publishing data, the cloud servers can edit the text and provide fake result.
In addition to cost savings, the cloud server can state that eligible users are not allowed
to access any of the file. Access policies are also not very flexible when converting plain
text to encrypted text. Because the circuits are used to provide a secure access structure, a
construction is provided to design the encryption based on attributes of cryptographic text
criteria with the established time interval.
12](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-23-320.jpg)
![In [3] system, every time the owner uploads a file, it is labelled with a set of attributes
that include an access structure (department, work profile, experience) also time, date and
location given. Our system is adding three different locations for a time interval. For
accessing file which is uploaded by owner, user should be present in one of these locations
and within the time interval which is given by owner. If all this attribute gets matched
then file be downloaded by user. The user can decrypt the encrypted text and download
the file if all the attributes match the owner’s set of attributes. This system is combined
with a verifiable calculation, confidentiality in which only the authorized user/owner can
access the data, detailed access controls. It also gives us the guarantee of the correction of
the delegated computer results. Furthermore, this scheme achieves feasibility and efficiency.
Taking the organization’s data exchange as an example where the attributes are department,
work profile, experience, time, date, location. Owner is one who wants to send file and user
is one who will able to access the information within a file given by owner. The condition is
that the file must be accessible to the user that meets the established requirements.
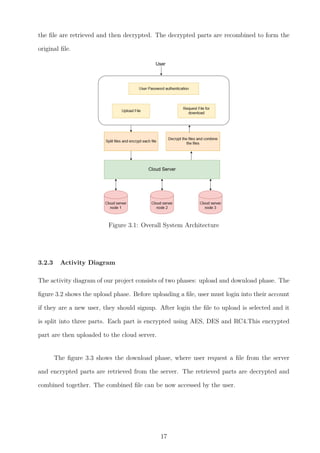
When the file is stored on the cloud, it must be in a secure form, or security must
be provided. So, let’s divide a file into fragments. Each node will only store a fragment
for a single file. It gives the guarantee that even if the attacker hacked any file, no valid
information will be given to the attacker. We will get any individual fragment that does
not contain the appropriate information. The nodes that store each of the fragments are
separated from the concept of T-coloring. When using T-coloring, the attacker will not be
able to guess the position of the other fragments.
2.5 Cloud Oriented Distributed and Encrypted File Storage (CODEFS)
In the paper written by [4] found that Data outsourcing to a third-party control, as is done in
cloud computing, gives rise to security concerns. The data might get modified or be subjected
change due to frequency of attacks by other users and cloud nodes. And, so high security
measures are required to protect data within the cloud. In the proposed methodology of
paper [4], Cloud Oriented Distributed and Encrypted File Storage (CODE-FS), the file is
13](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-24-320.jpg)

![CHAPTER 3
METHODOLOGY
3.1 Data
The data in this project is the file uploaded by the user. In this project, we are considering
the text files only. The file formats like .txt and .csv are used as our input data. Also, we
had restricted the size of the file we handle to 40 MB. The reason for enforcing the restriction
is mainly because the larger file will take more time to upload. Since the file upload speed
is low, we will only consider the file size of 40 MB as maximum. The processing of text files
is more any other file. The application mainly takes text files of size less than or equal to 40
MB.
3.2 Design
3.2.1 Requirement Analysis
The project mainly uses three components for the system to be implemented. The compo-
nents like web framework, database and cloud server.
Web Framework : In this project we mainly use two web frameworks like bootstrap [5]
and Django [6]. The later one supports python which is used as our server-side scripting
language. The latest bootstrap framework is used to design user interface of our system.
Database : Database is a major part of our project to store files and login credentials. In
this project we use MySQL database in AWS RDS.We use different database servers to store
files separately and all this database will be MySQL database deployed in different locations
of AWS RDS.
15](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-26-320.jpg)








![Figure 4.3: Test Plan 3.
Figure 4.4: Test Plan 4.
4.3 Discussion
The source code for our proposed system has been made available in GitHub under the open
source license [7]. The proposed system is a web application and our web application can
be viewed and also can use it for storing text files. The URL to check the web application
is at [8] .
25](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-36-320.jpg)


![REFERENCES
[1] Punam V Maitri and Aruna Verma. “Secure file storage in cloud computing using
hybrid cryptography algorithm”. In 2016 International Conference on Wireless Com-
munications, Signal Processing and Networking (WiSPNET), pages 1635–1638. IEEE,
2016.
[2] Ms Snehal Rathod, SA Ubale, and Sulabha S Apte. “Attribute-Based Encryption Along
with Data Performance and Security on Cloud Storage”. In 2018 International Con-
ference on Information, Communication, Engineering and Technology (ICICET), pages
1–3. IEEE, 2018.
[3] Supriya Kute and SB Javheri. “Implementation of Secure File Storage on Cloud with
Owner-Defined Attributes for Encryption”. In 2018 Fourth International Conference on
Computing Communication Control and Automation (ICCUBEA), pages 1–6. IEEE,
2018.
[4] Mihir Manek, Aditi Chhadwa, Kinjal Shah, Manish Potey, and Mehvash Khan. “Cloud
Oriented Distributed and Encrypted File Storage (CODE-FS)”. In 2018 Fourth Interna-
tional Conference on Computing Communication Control and Automation (ICCUBEA),
pages 1–5. IEEE, 2018.
[5] https://getbootstrap.com/docs/4.4/getting-started/introduction/.
[6] https://docs.djangoproject.com/en/3.0/.
[7] https://github.com/ALINBABU/SECRY.
[8] https://secrycloud.tech.
28](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-39-320.jpg)
![[9] https://aws.amazon.com/.
[10] https://medium.com/saarthi-ai/ec2apachedjango-838e3f6014ab.
29](https://image.slidesharecdn.com/projectfinalreport-200709124106/85/Project-final-report-40-320.jpg)