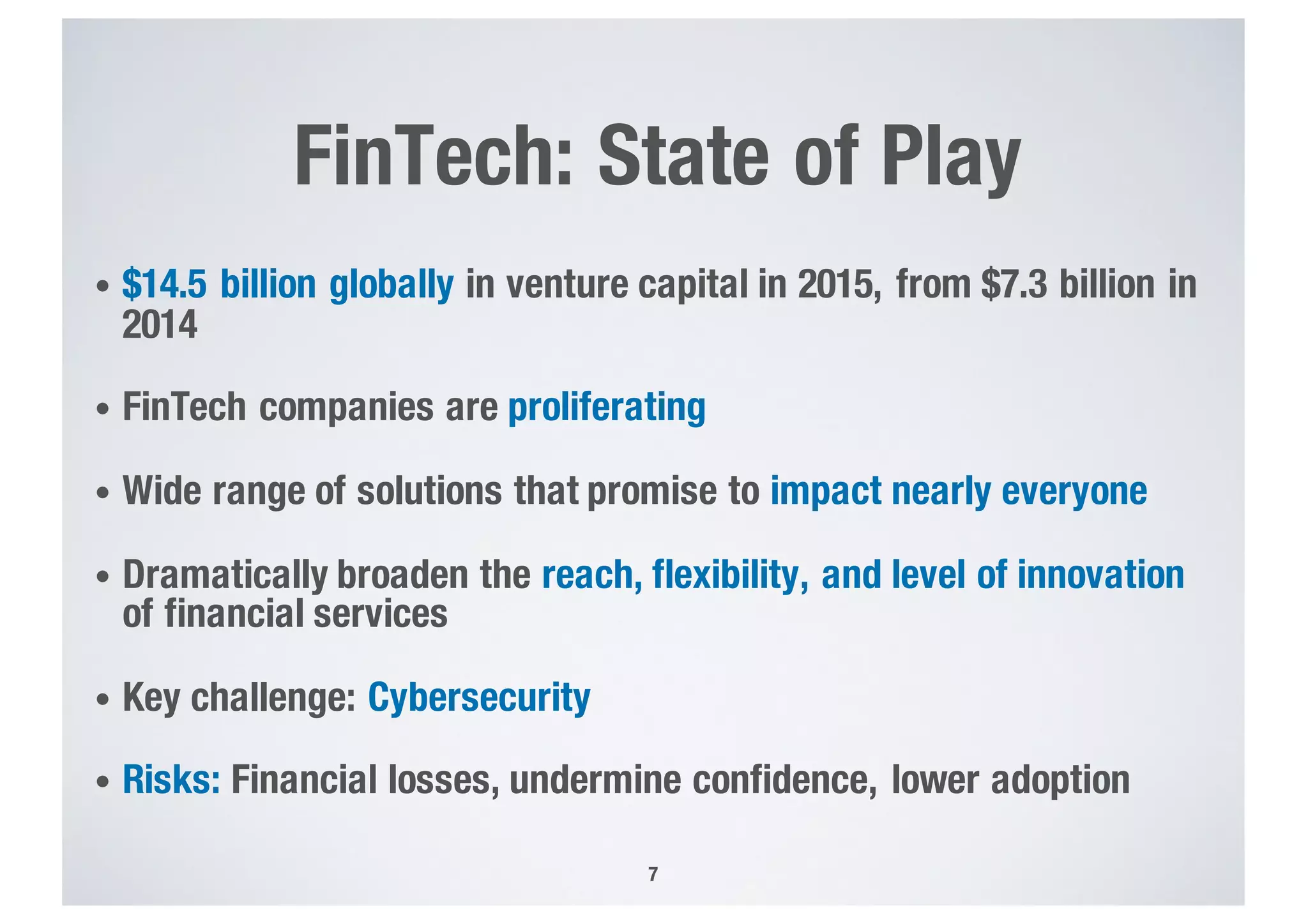
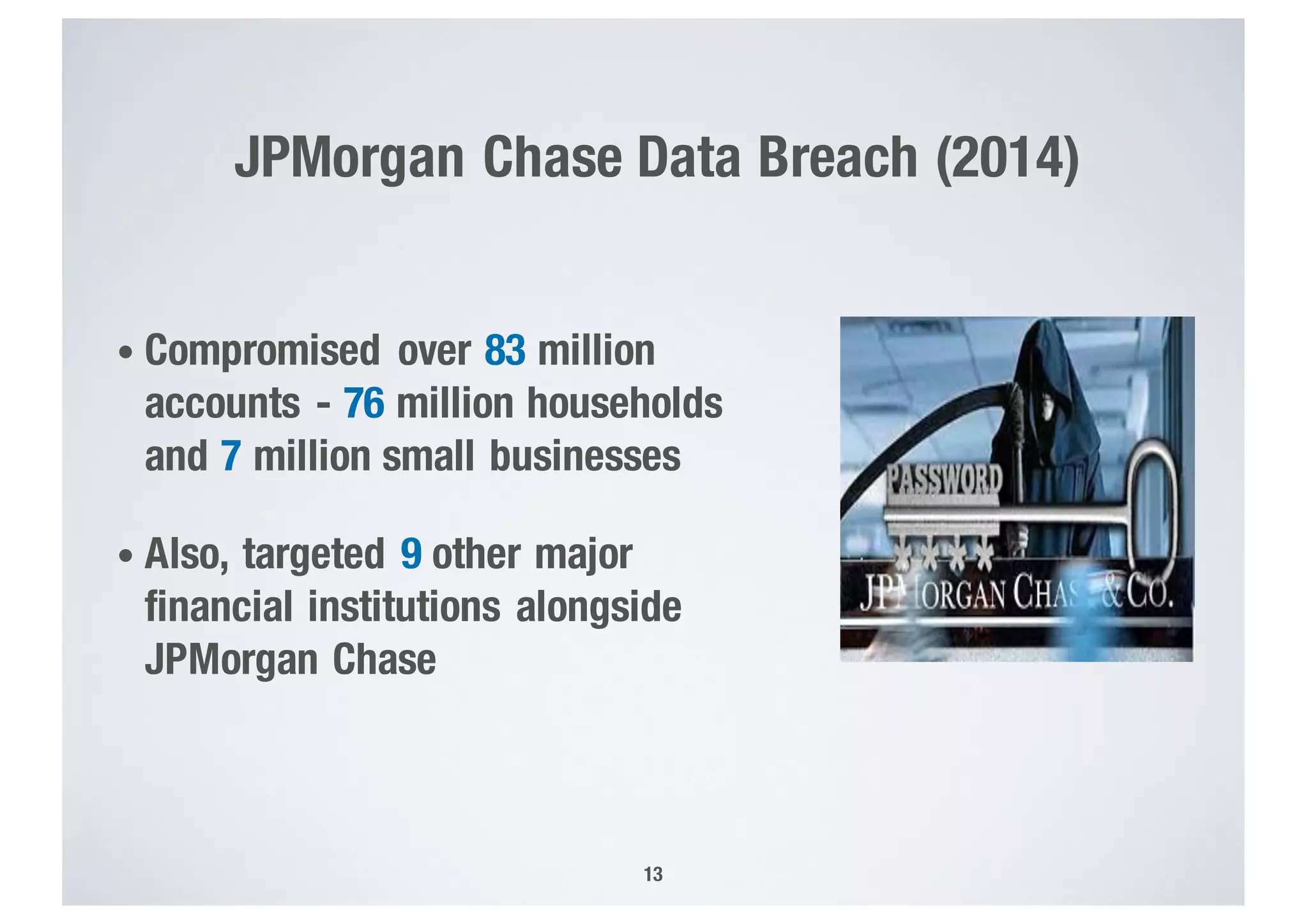
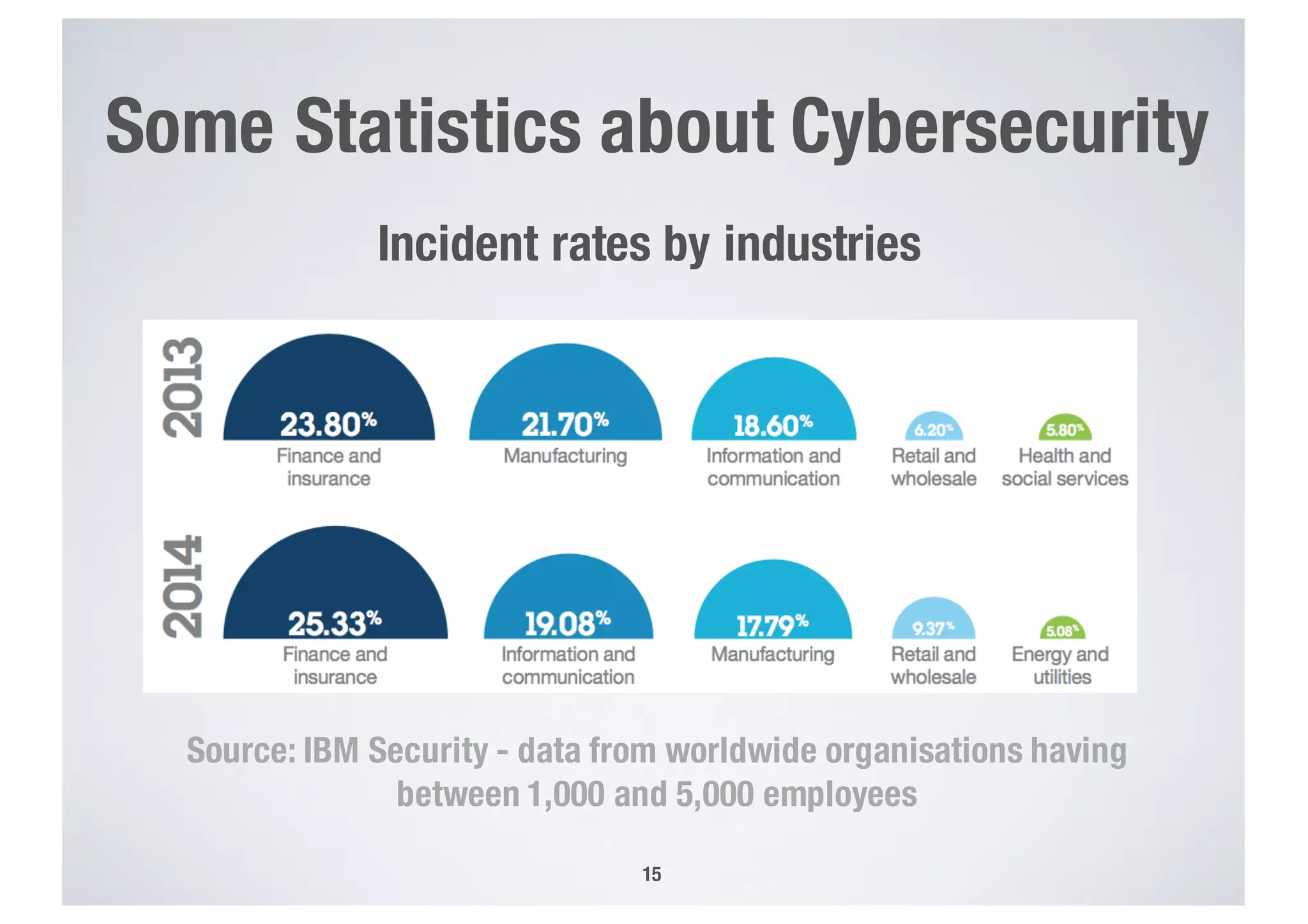
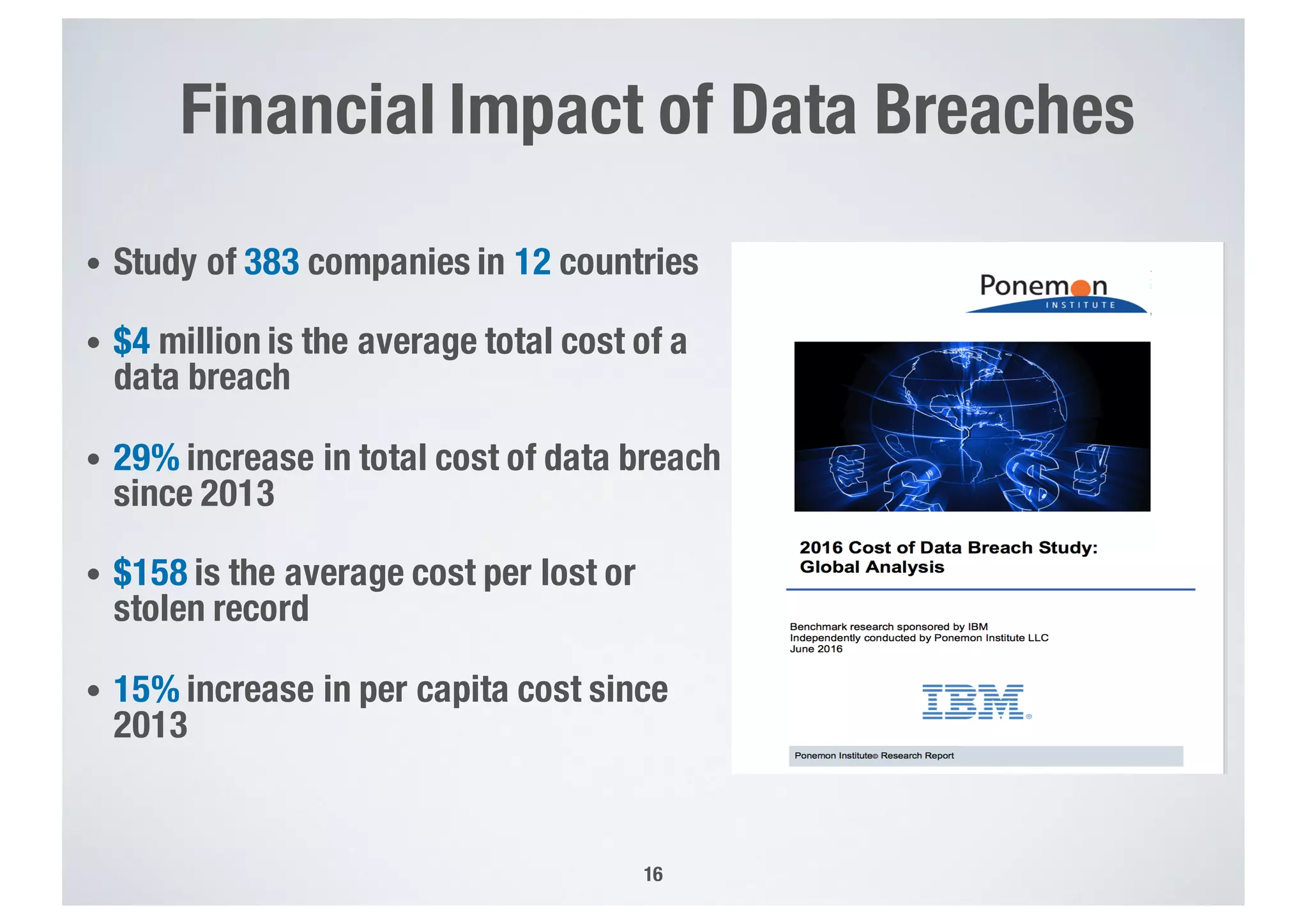
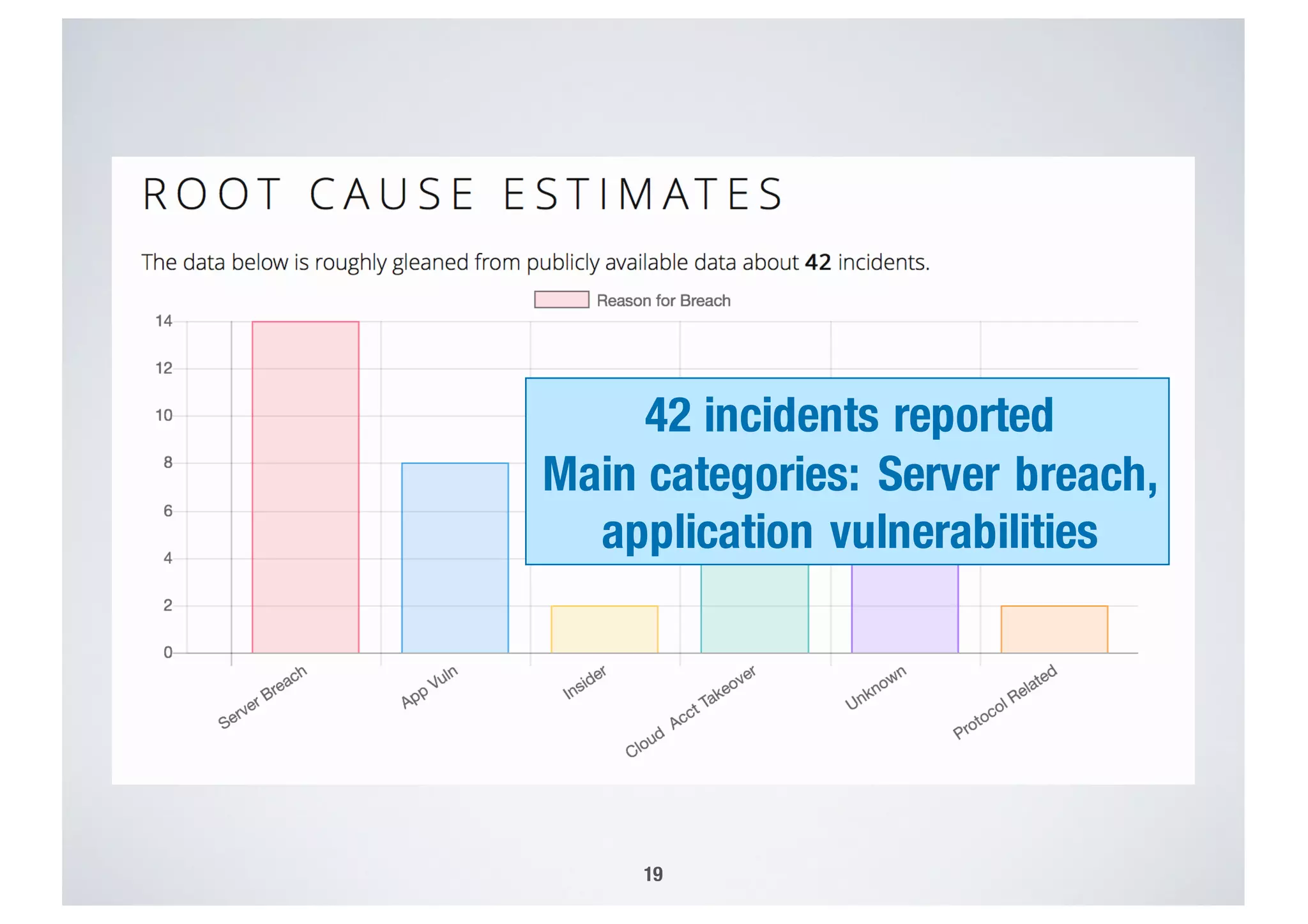
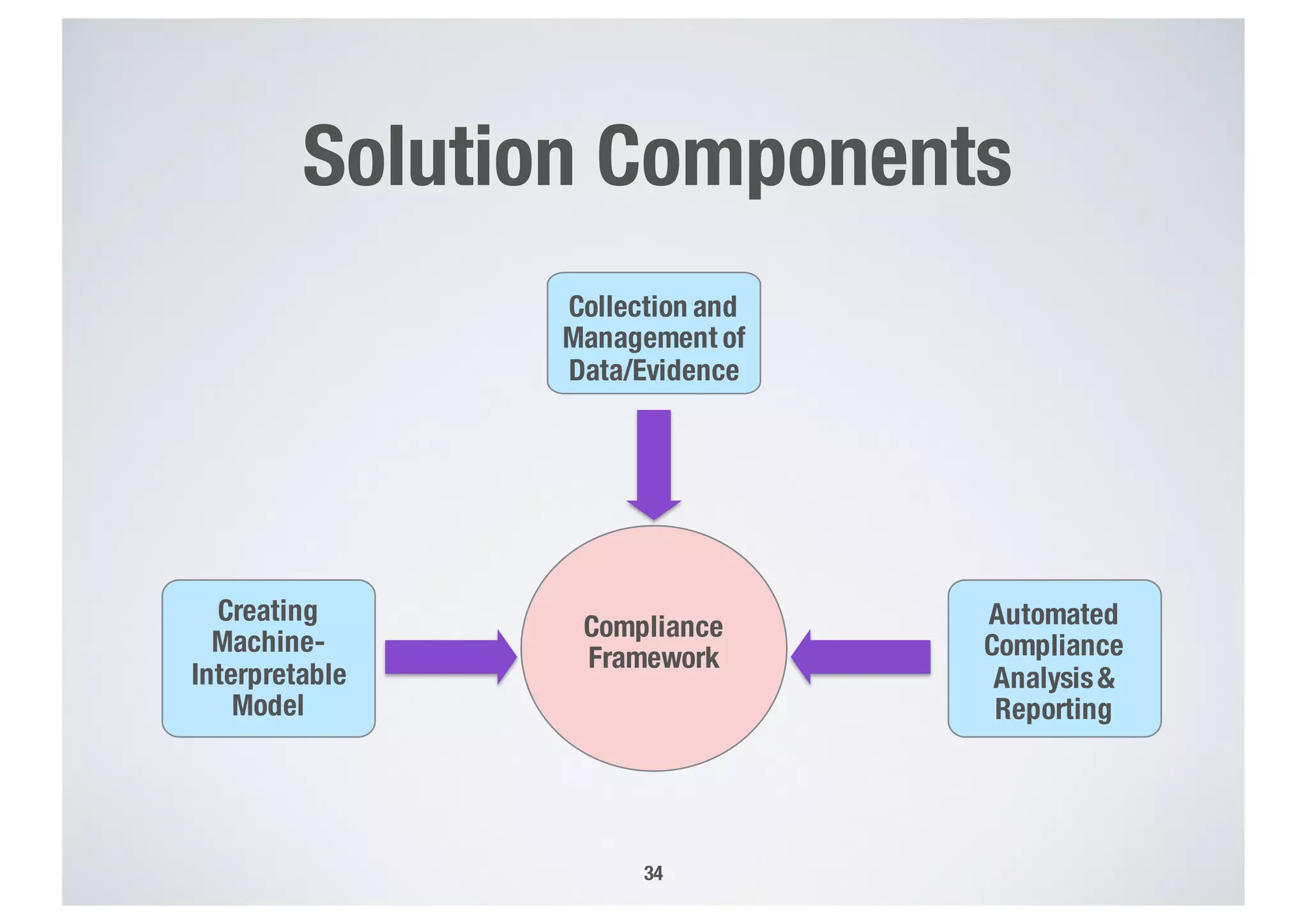
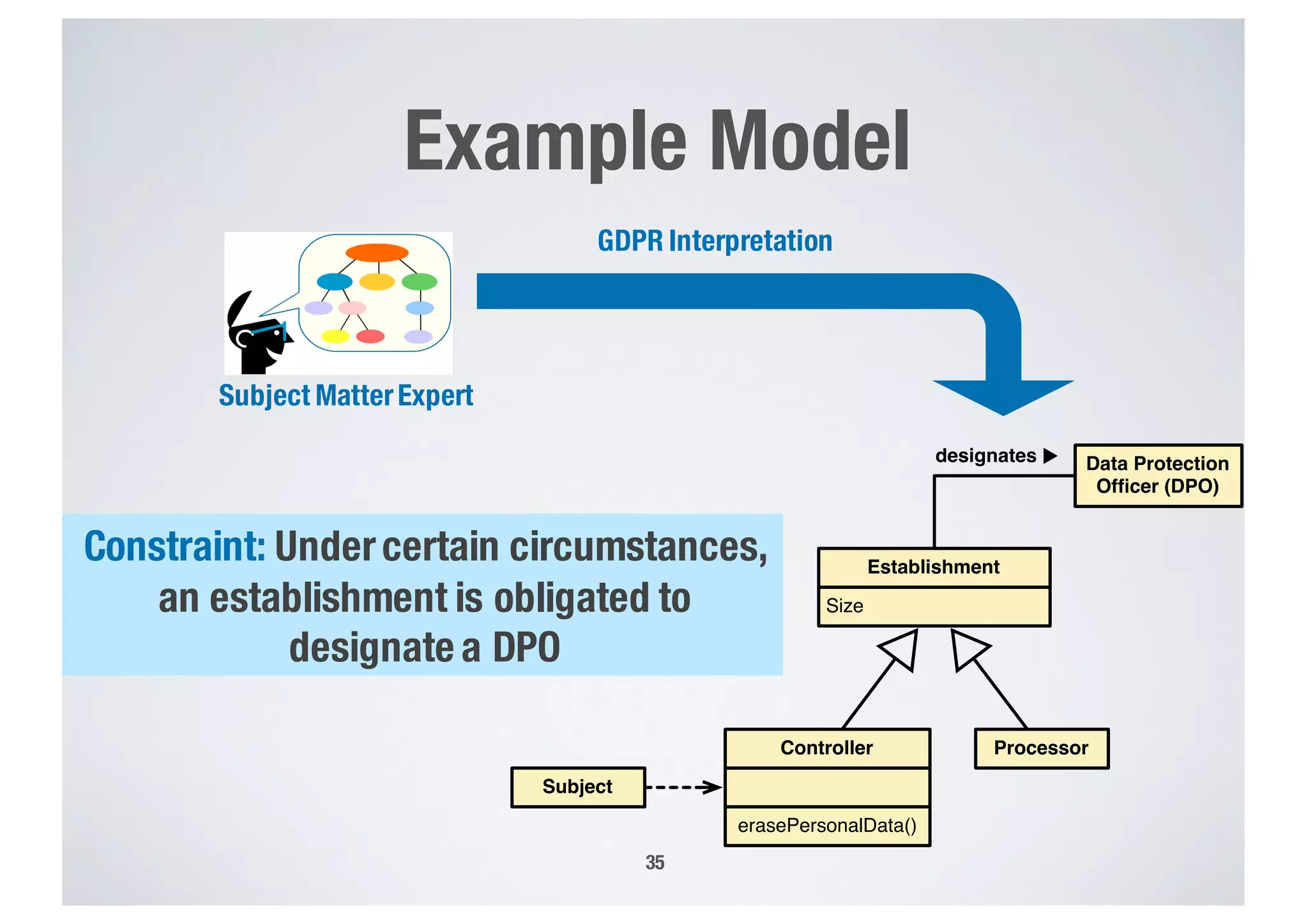
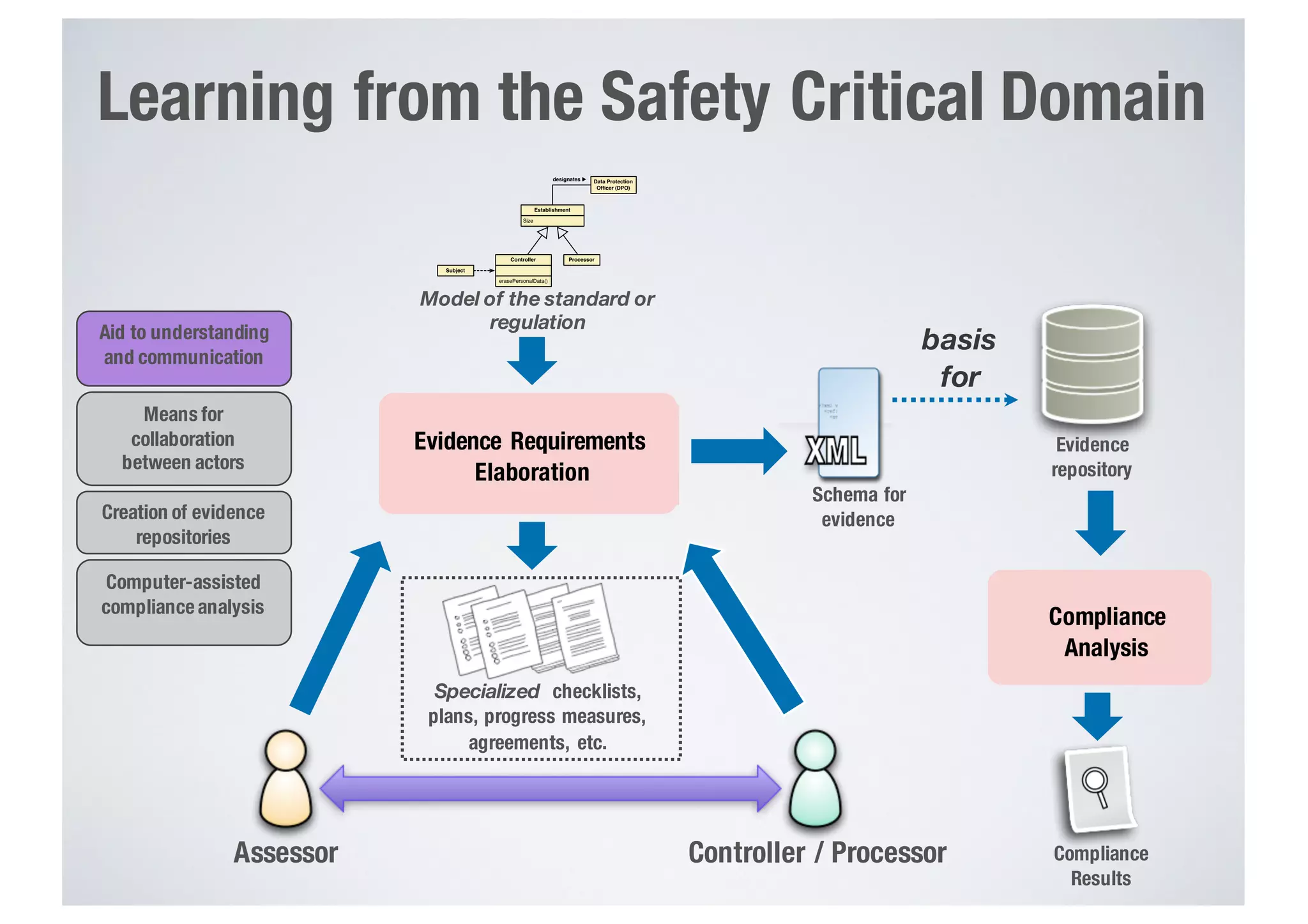
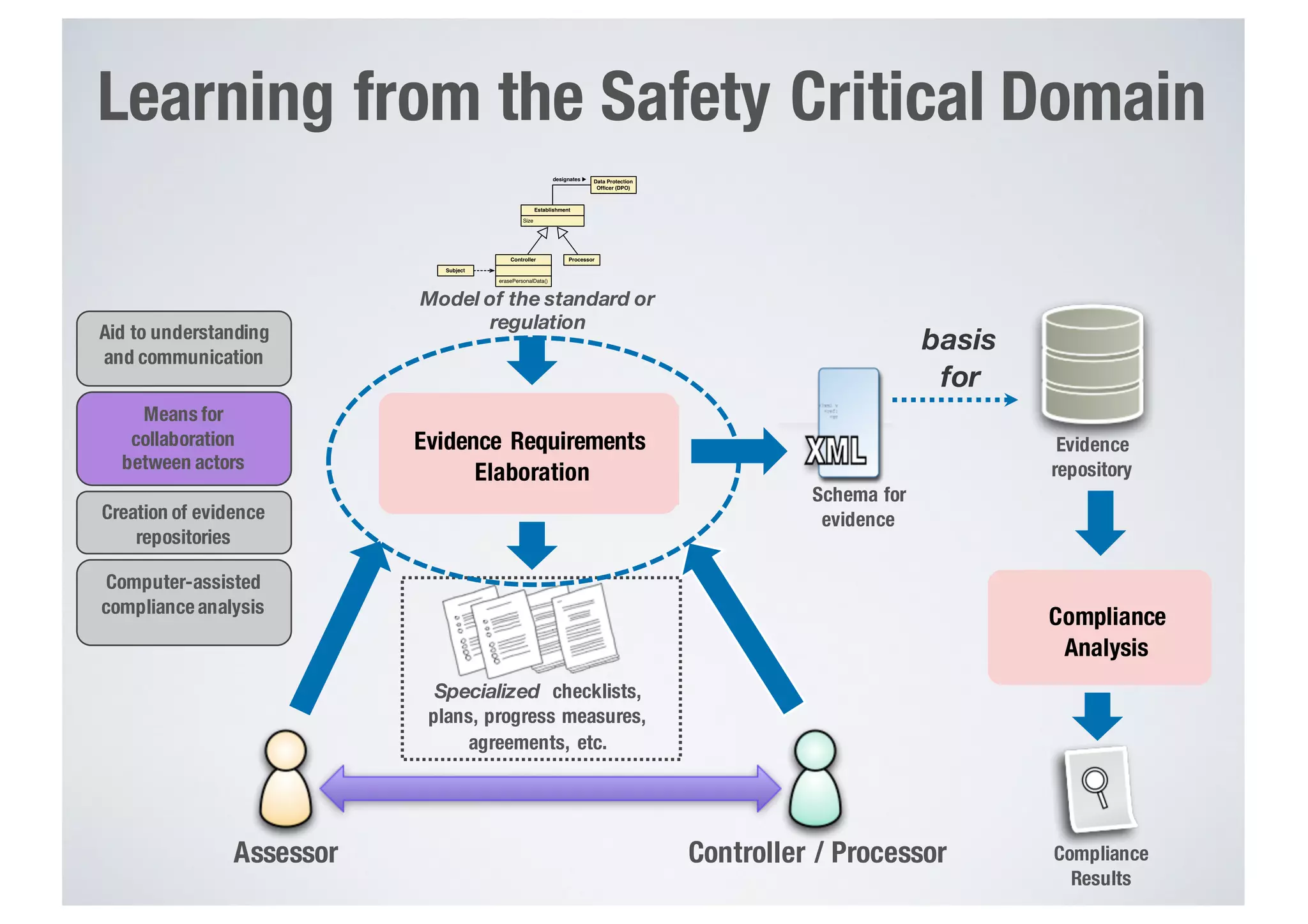
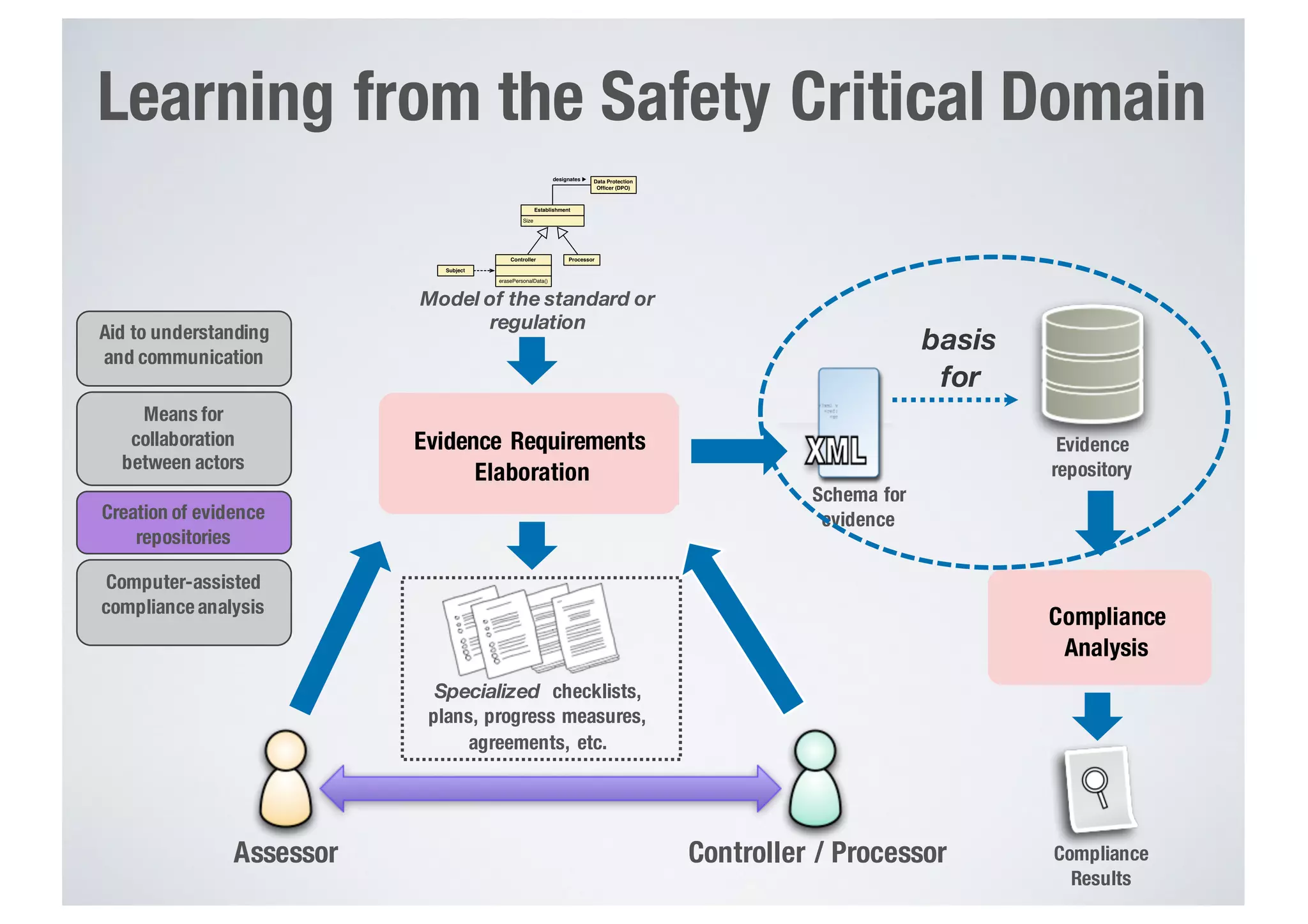
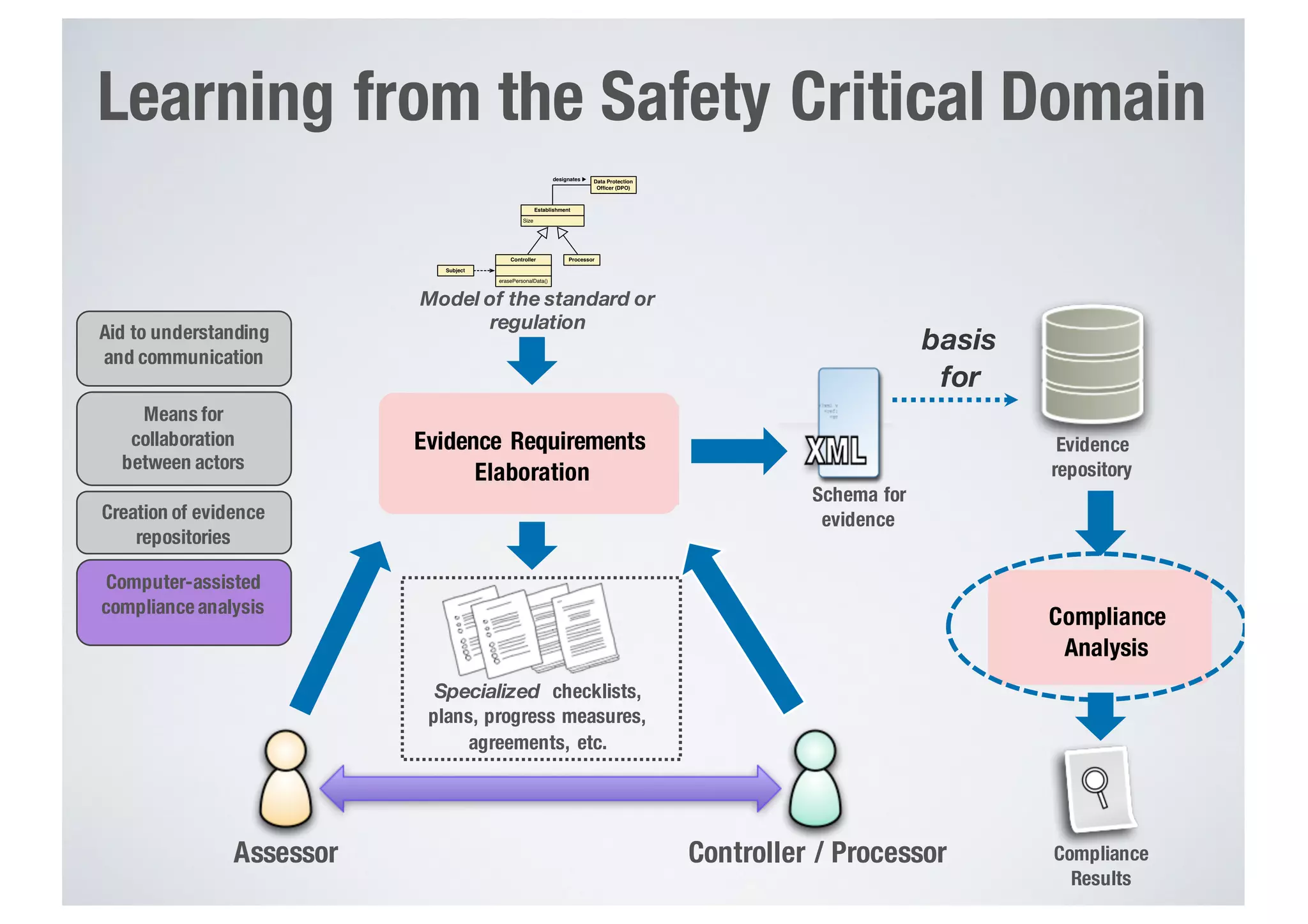
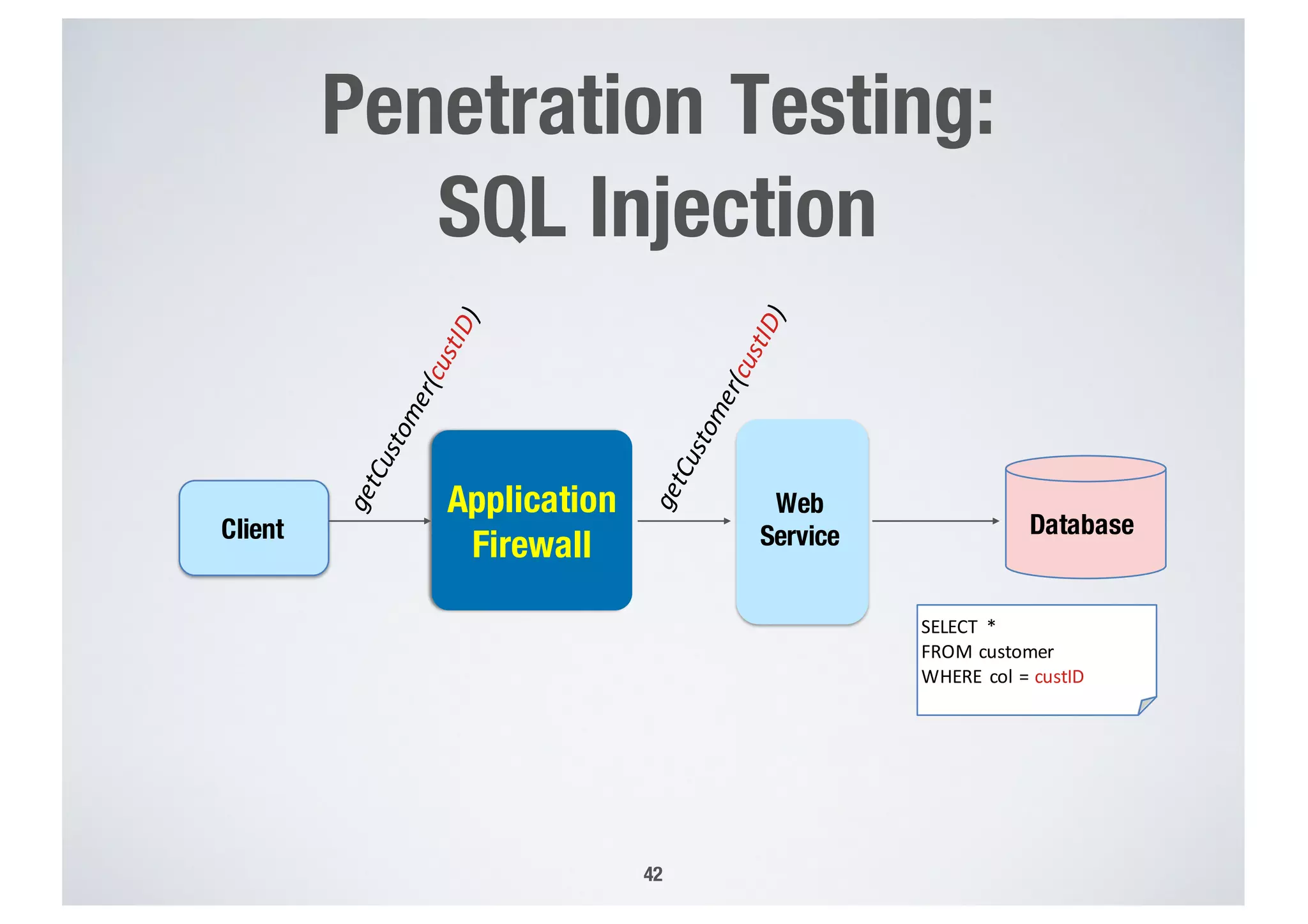
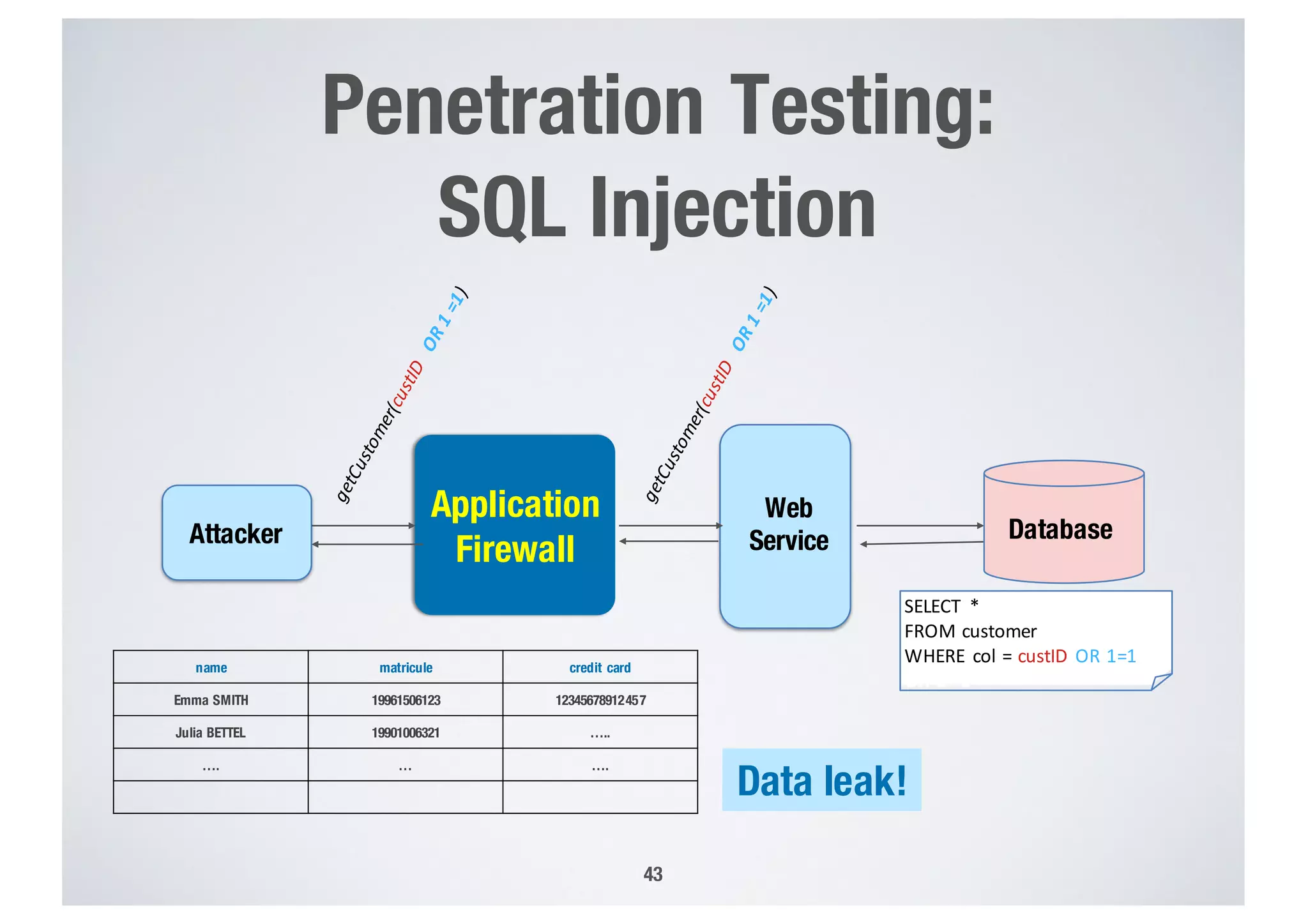
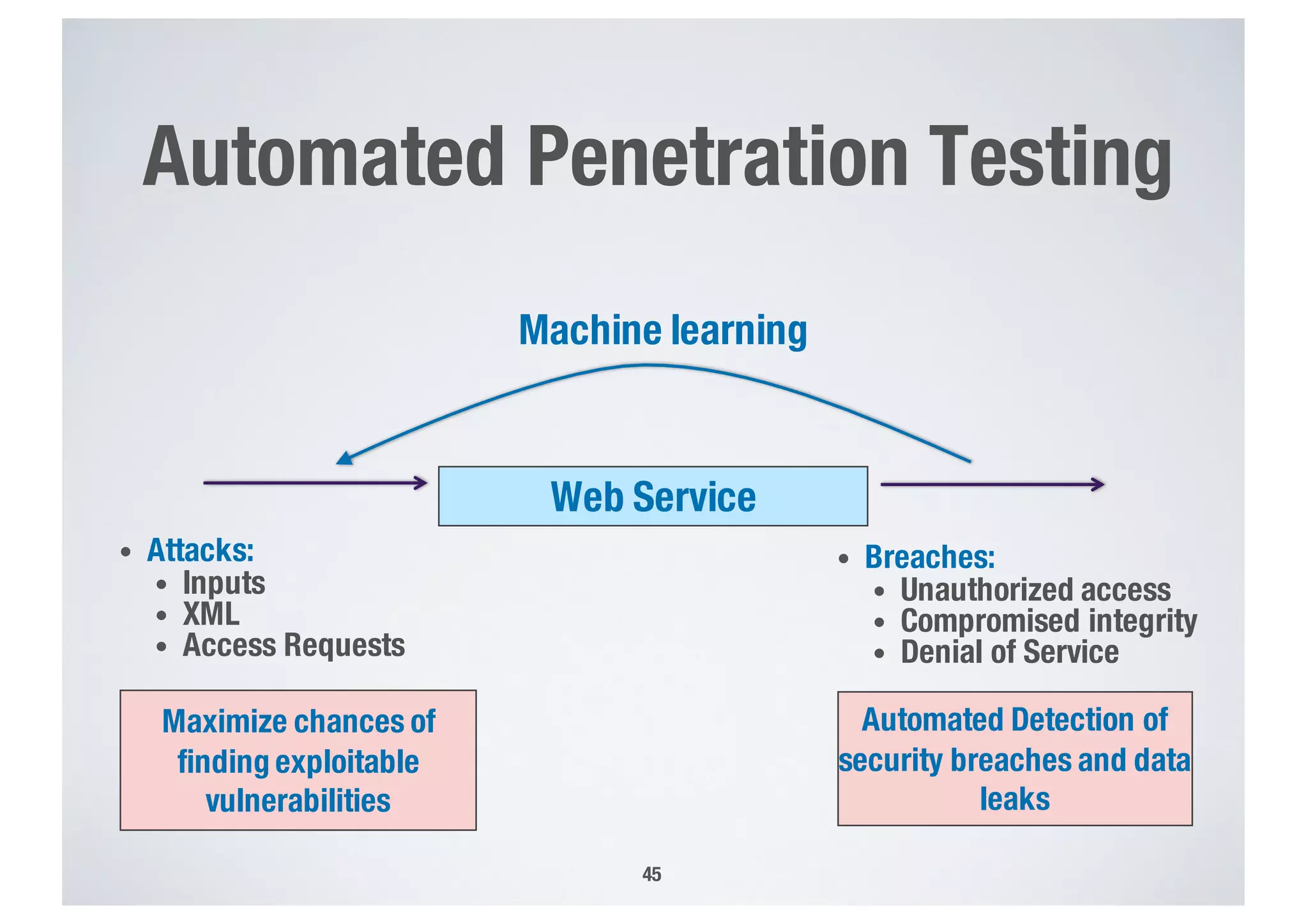
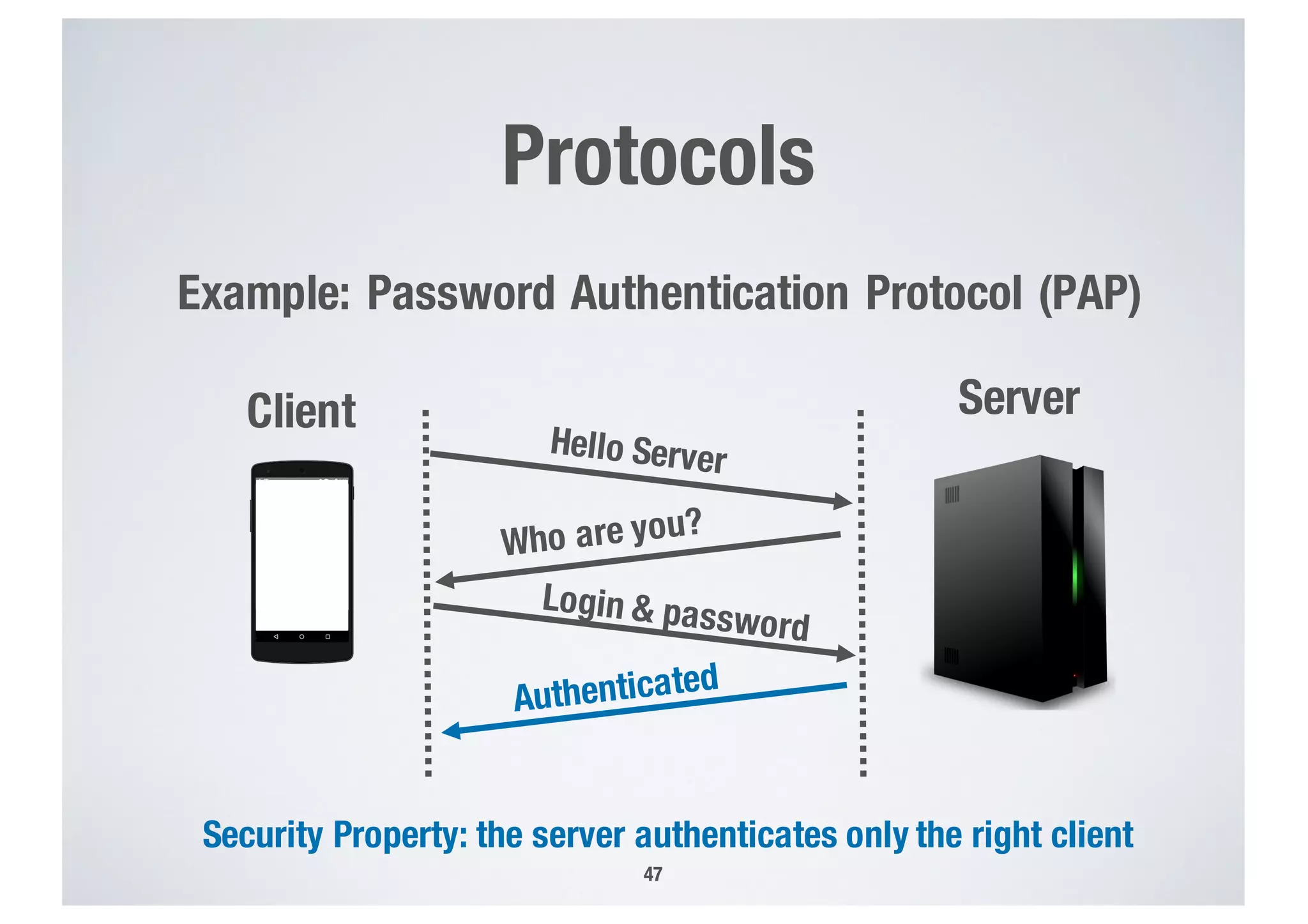
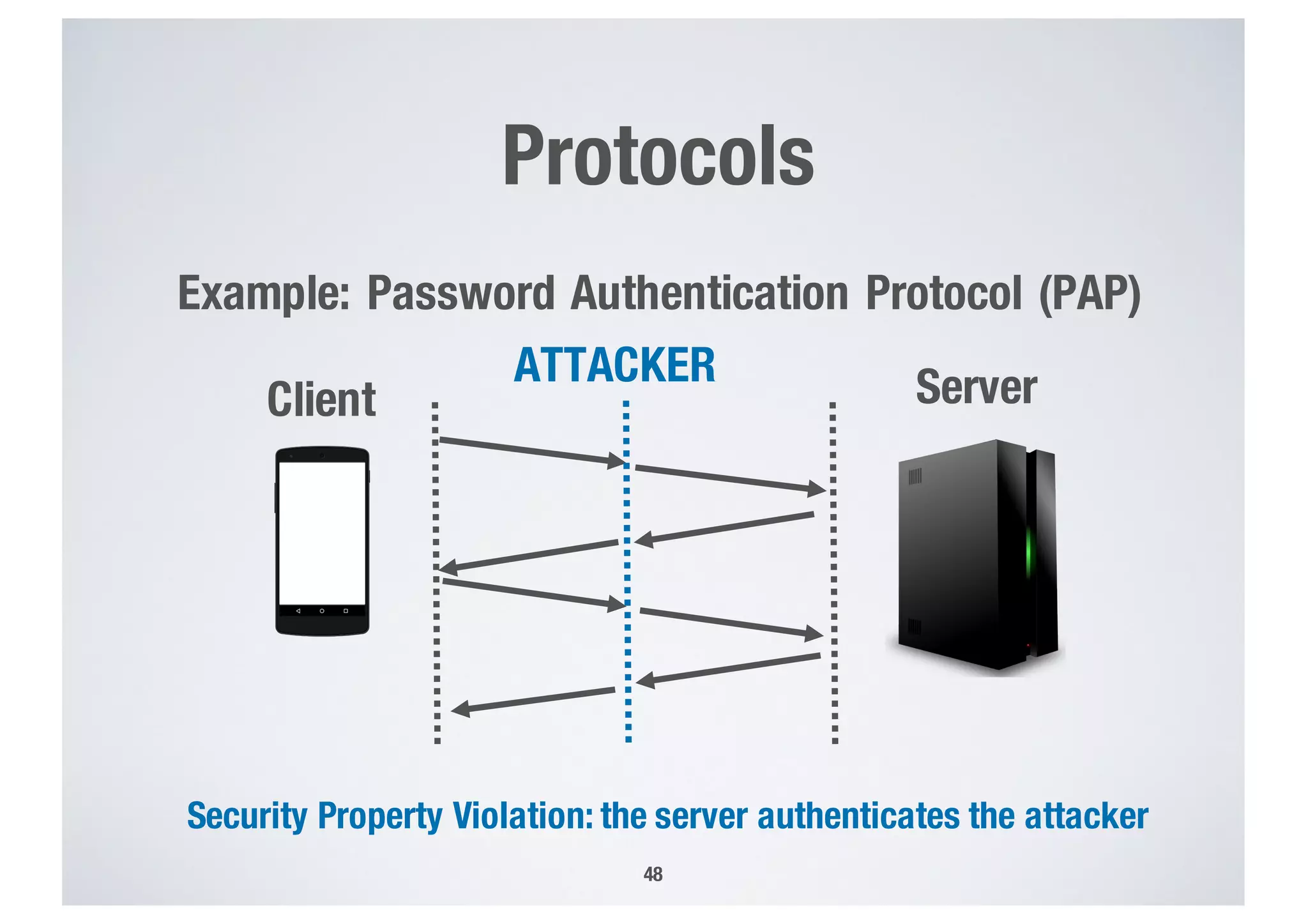
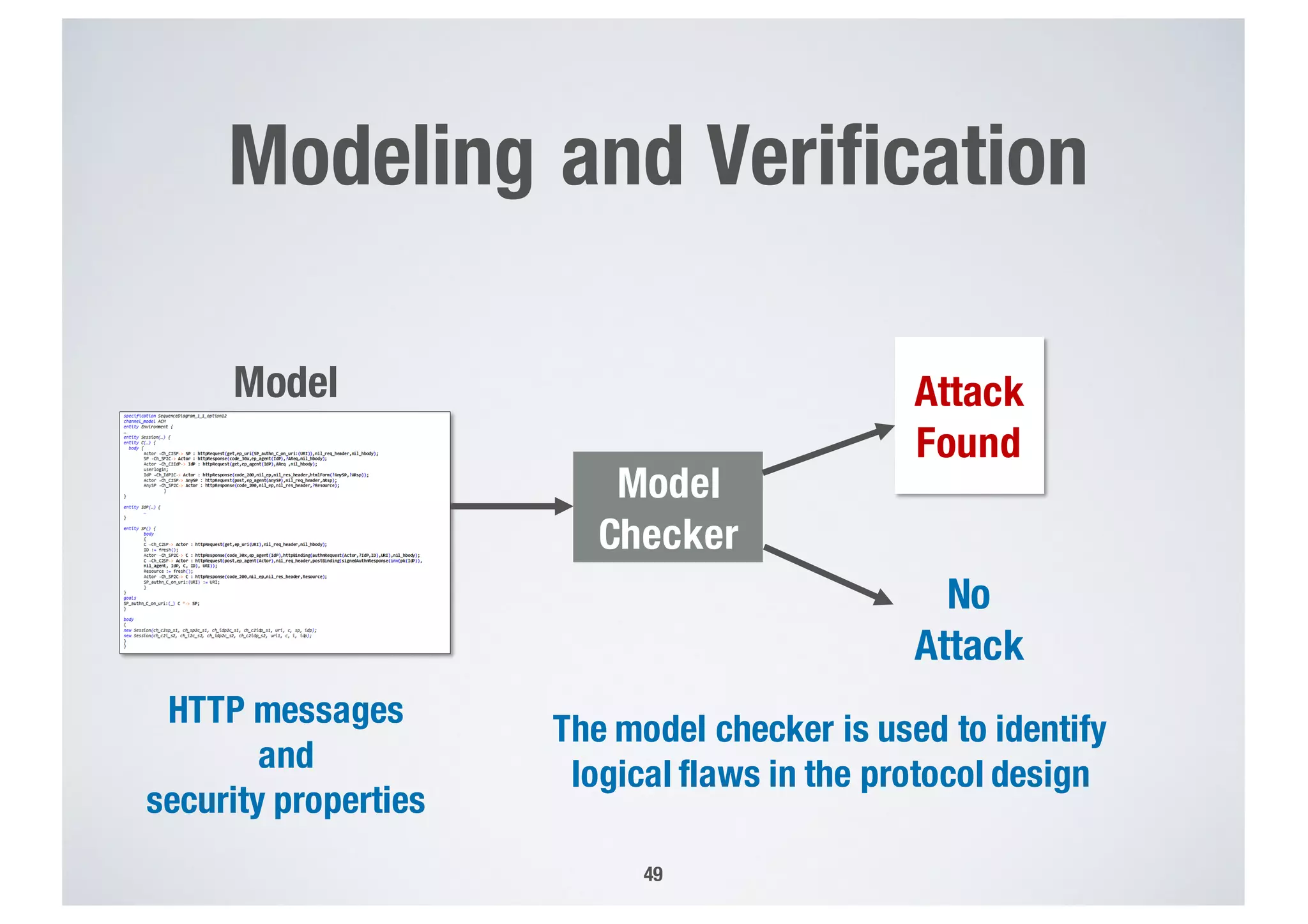
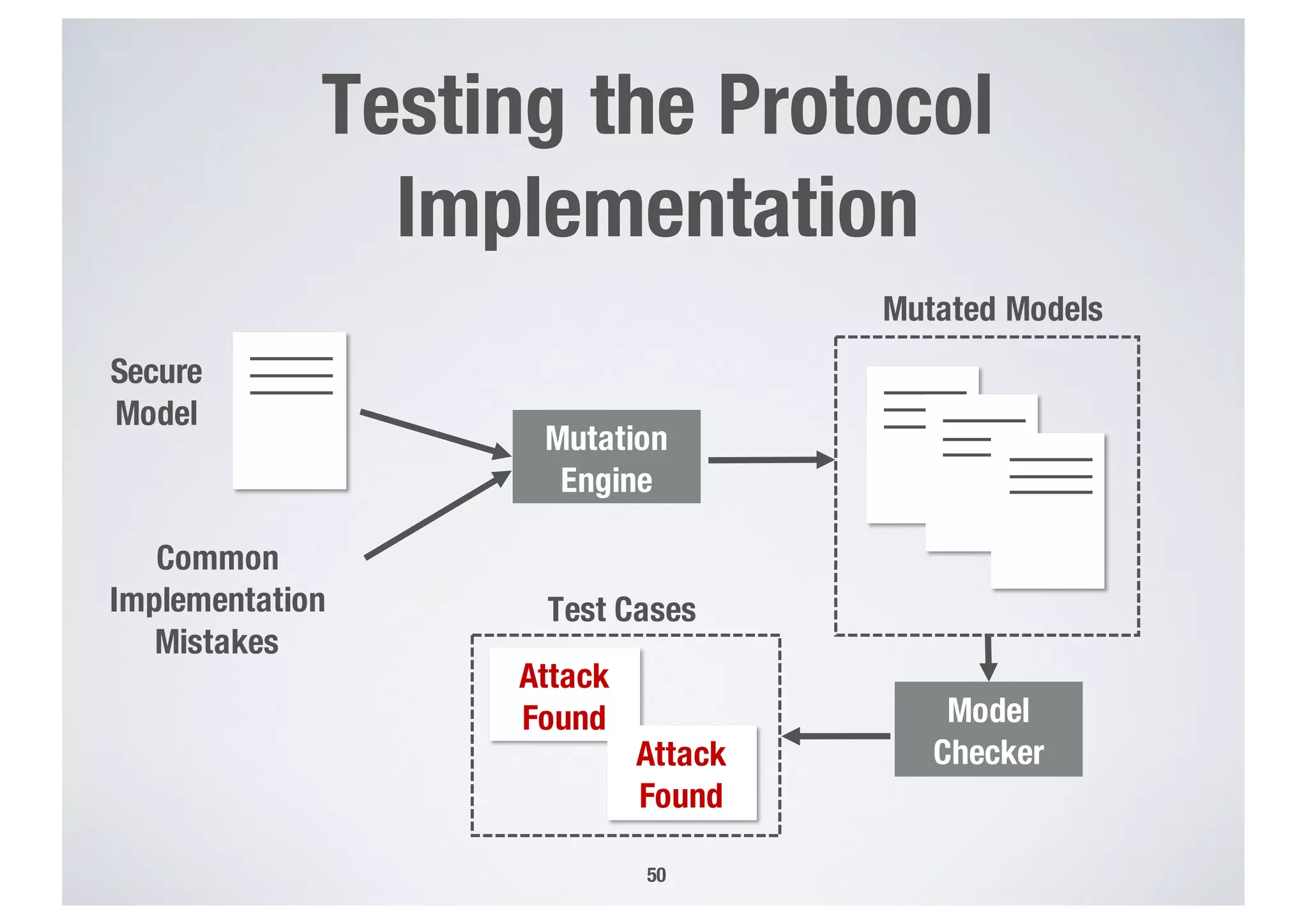
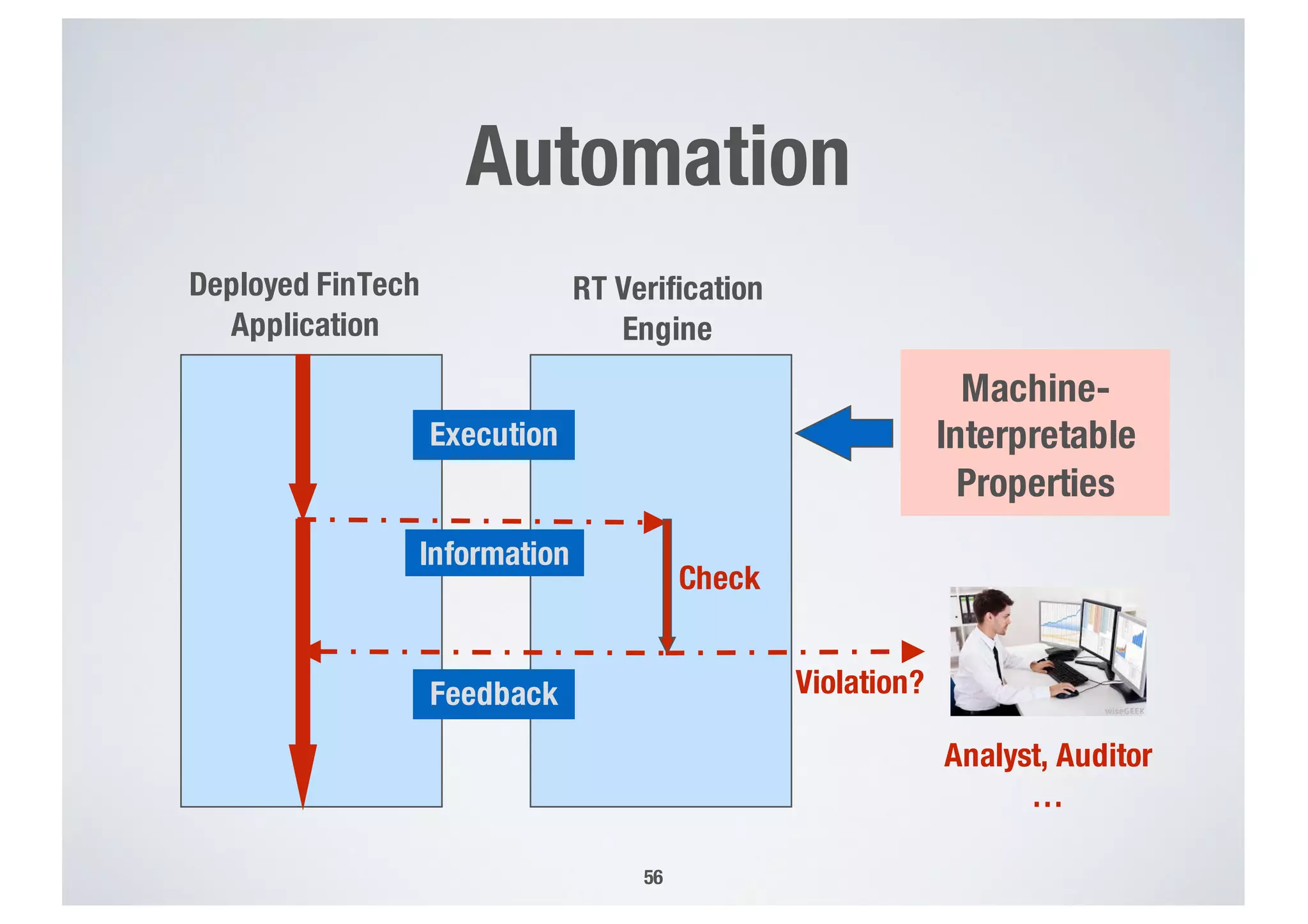
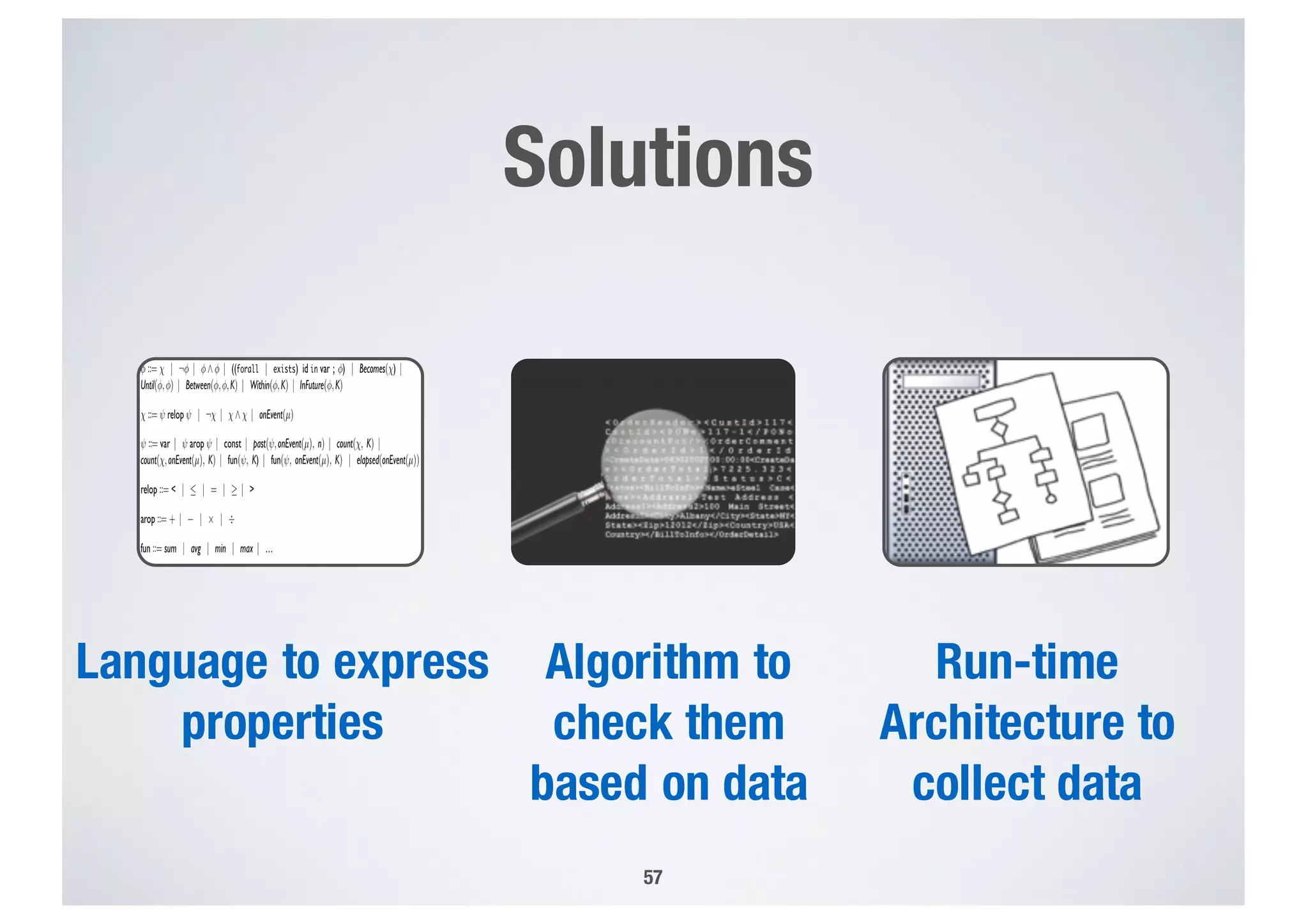
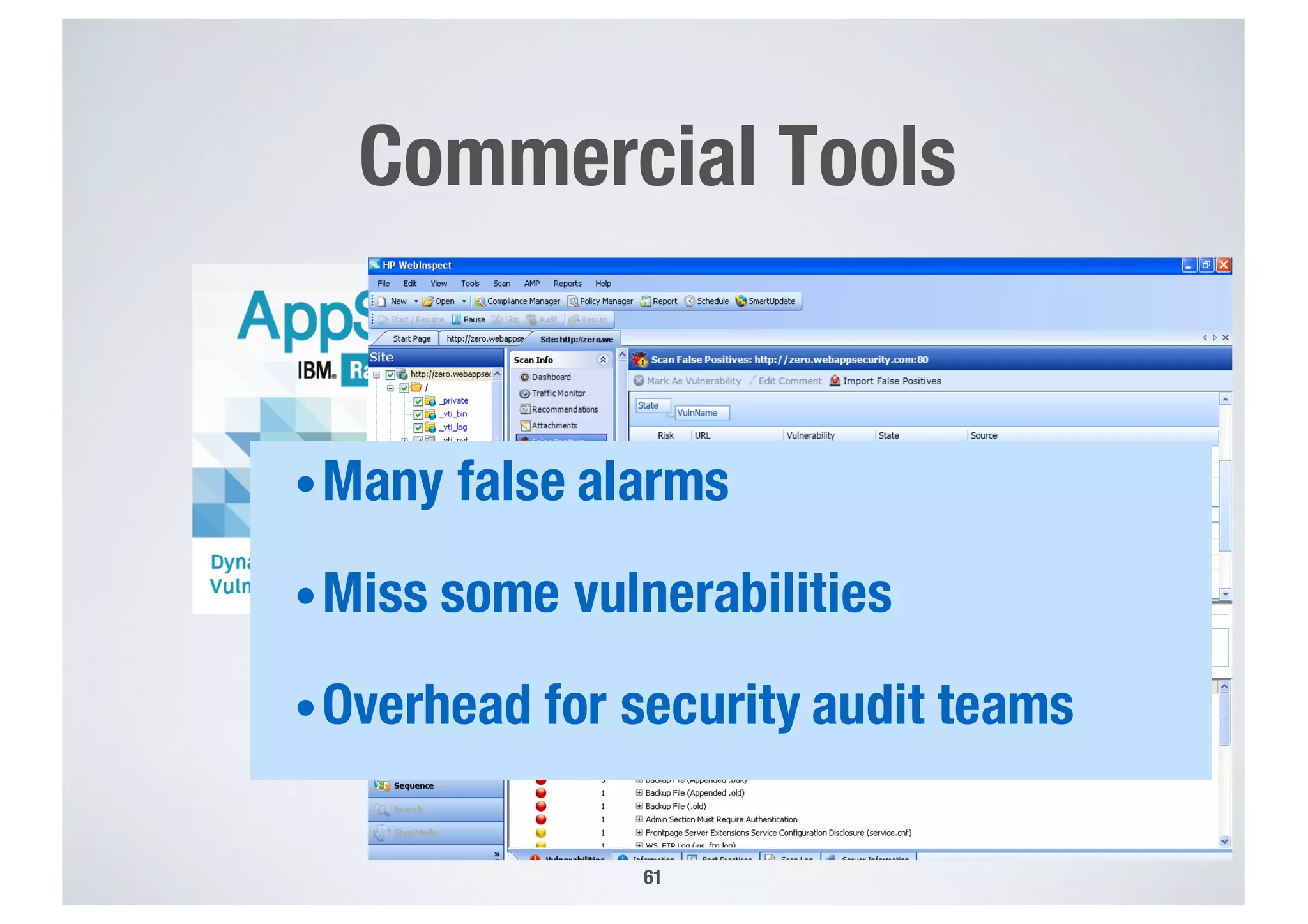
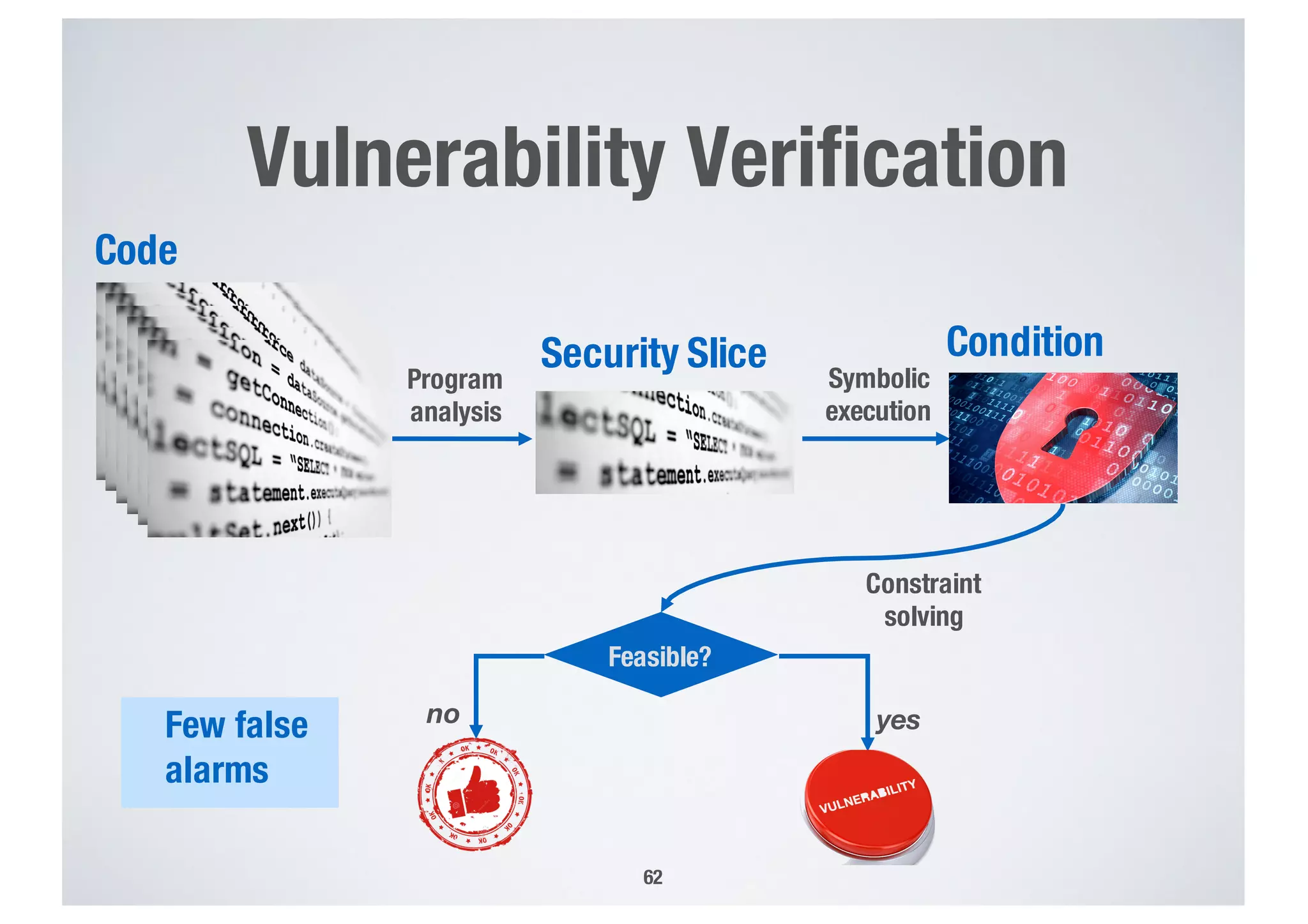
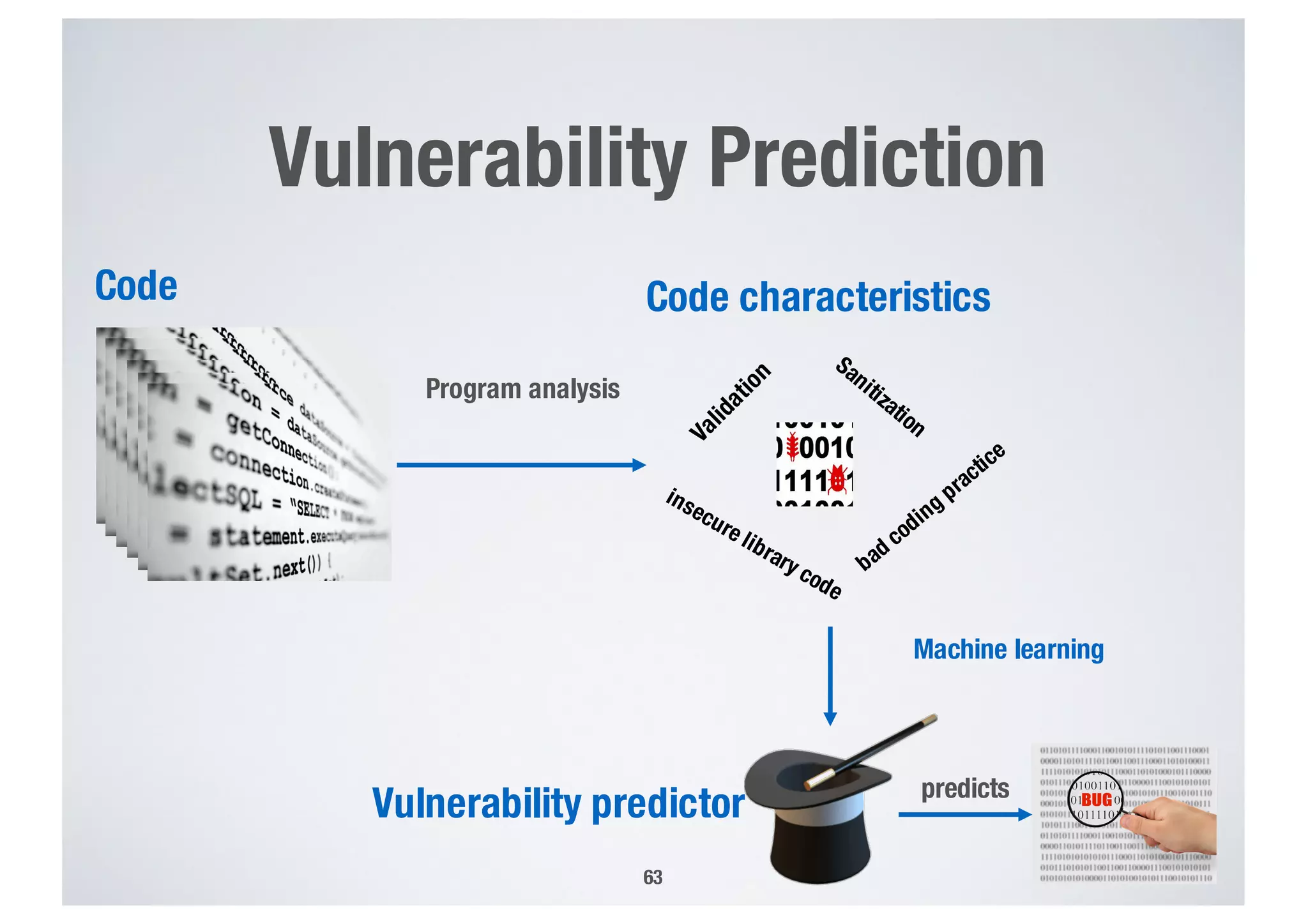
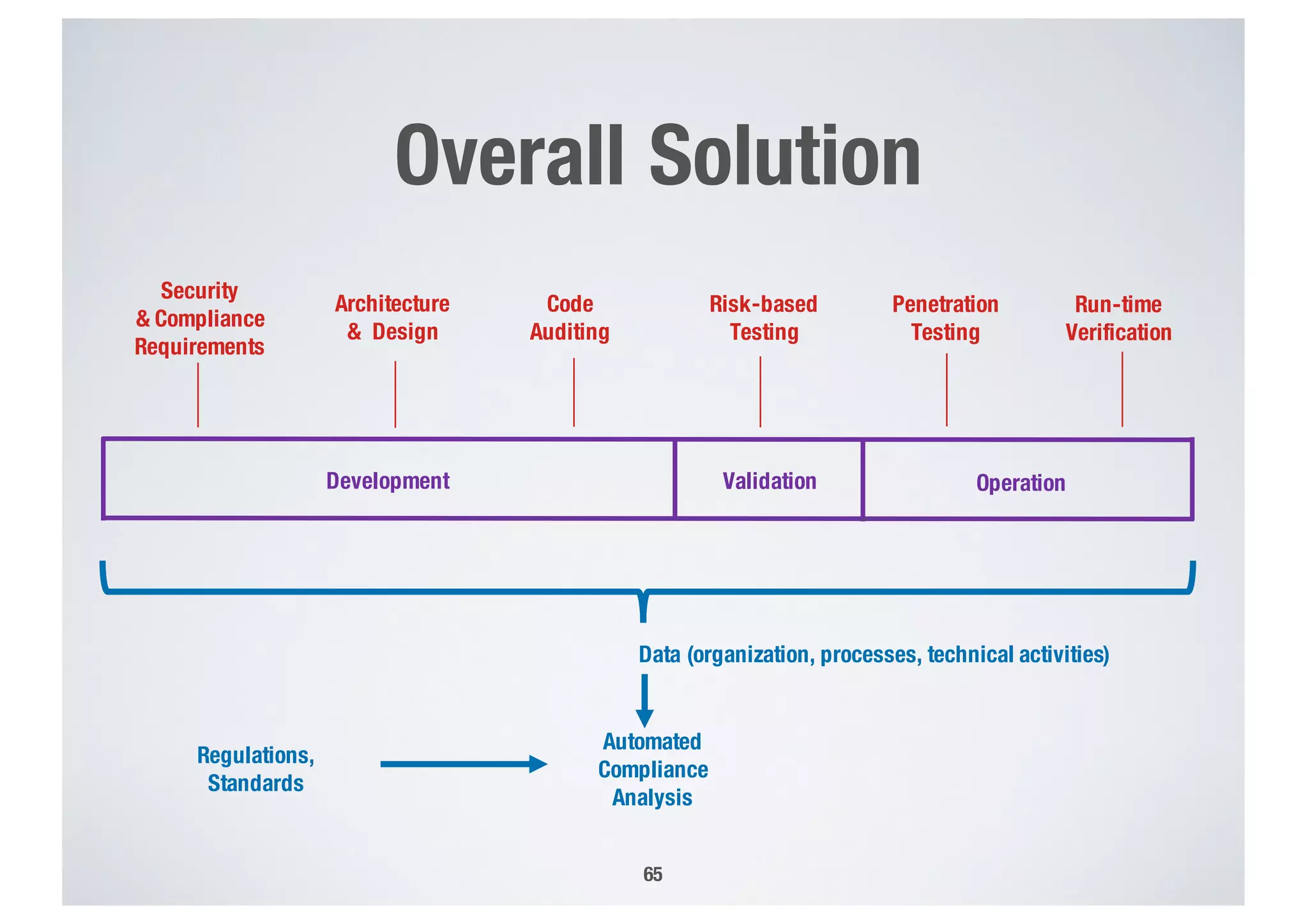
FinTech applications handle sensitive user data and must ensure secure data management and compliance with regulations to avoid breaches. Automated techniques are needed to help with compliance analysis, security testing, and auditing given the complexity and resources required. These include machine-interpretable models of standards, automated testing of applications and protocols, run-time monitoring, and machine learning to predict vulnerabilities. Such techniques can help scale assurance efforts for secure data management in FinTech.