The document discusses data breaches and relevant laws. It notes an increasing number of data breaches and introduces key laws around data security - the GDPR and NISD. The GDPR requires organizations to implement appropriate security measures to protect personal data and report breaches. It applies broadly to any group processing EU citizens' data or offering goods/services to them. The NISD focuses on essential services and digital service providers, requiring security and reporting of significant incidents. Non-compliance can result in large fines and litigation. Proper precautions such as response planning and legal advice are recommended.






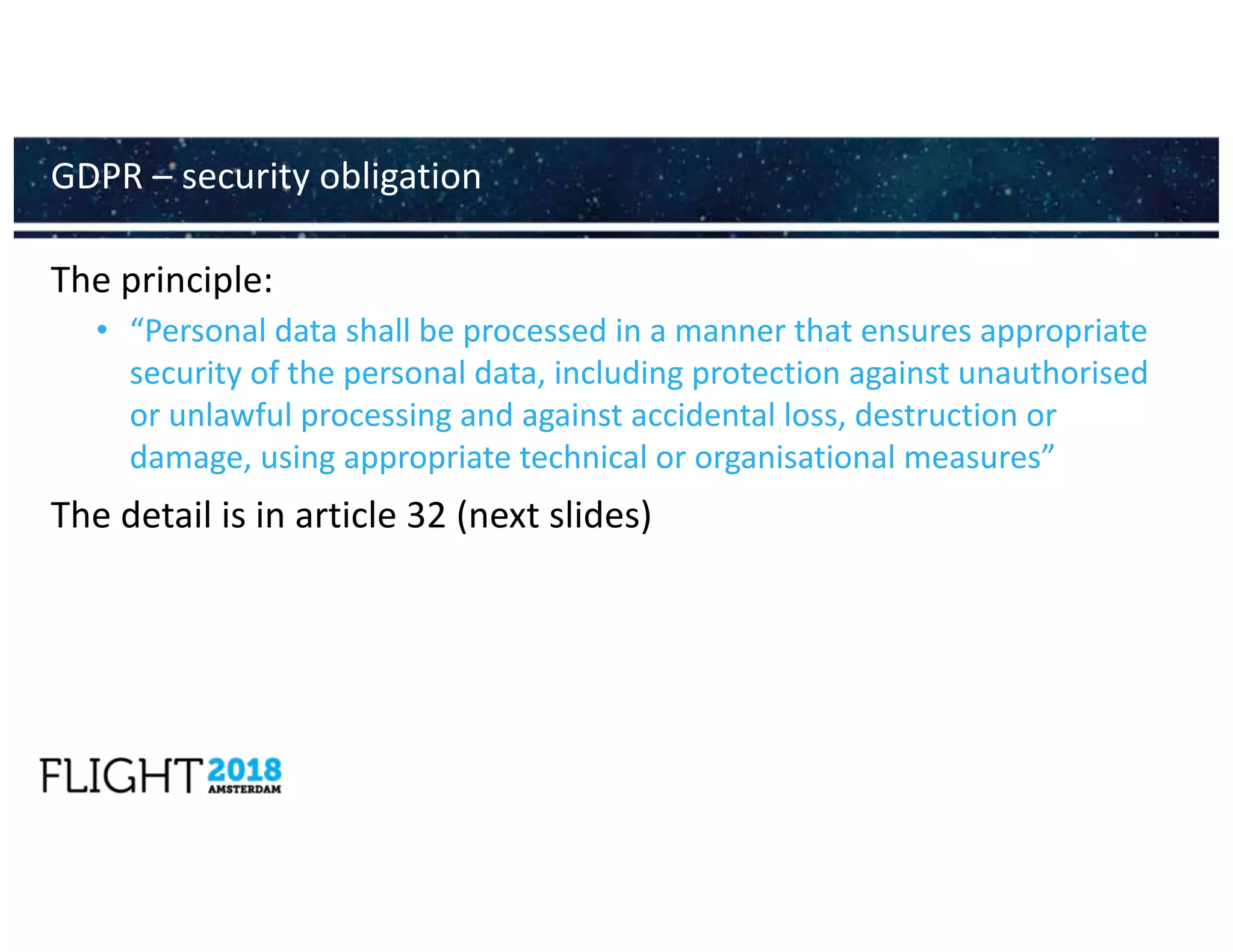


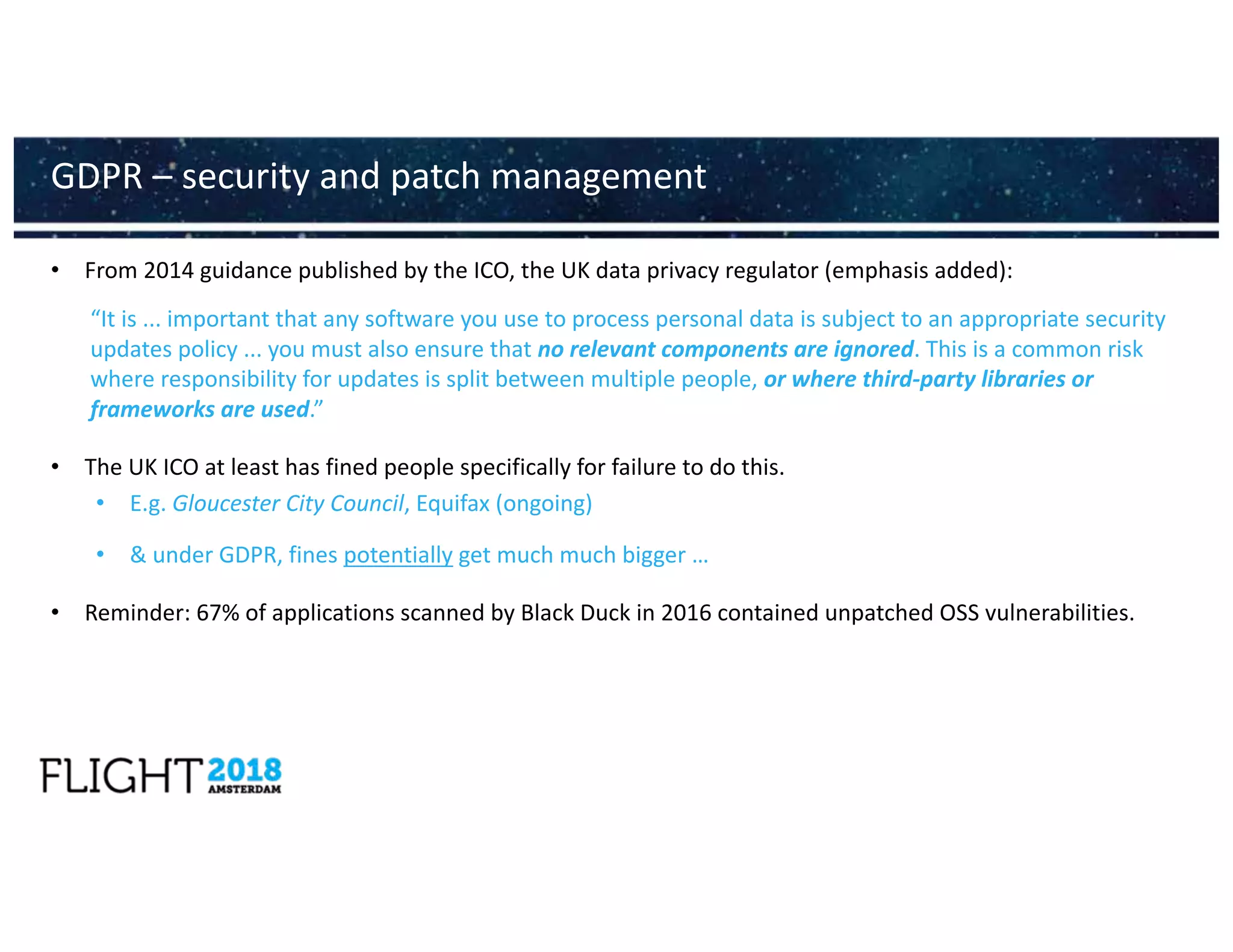
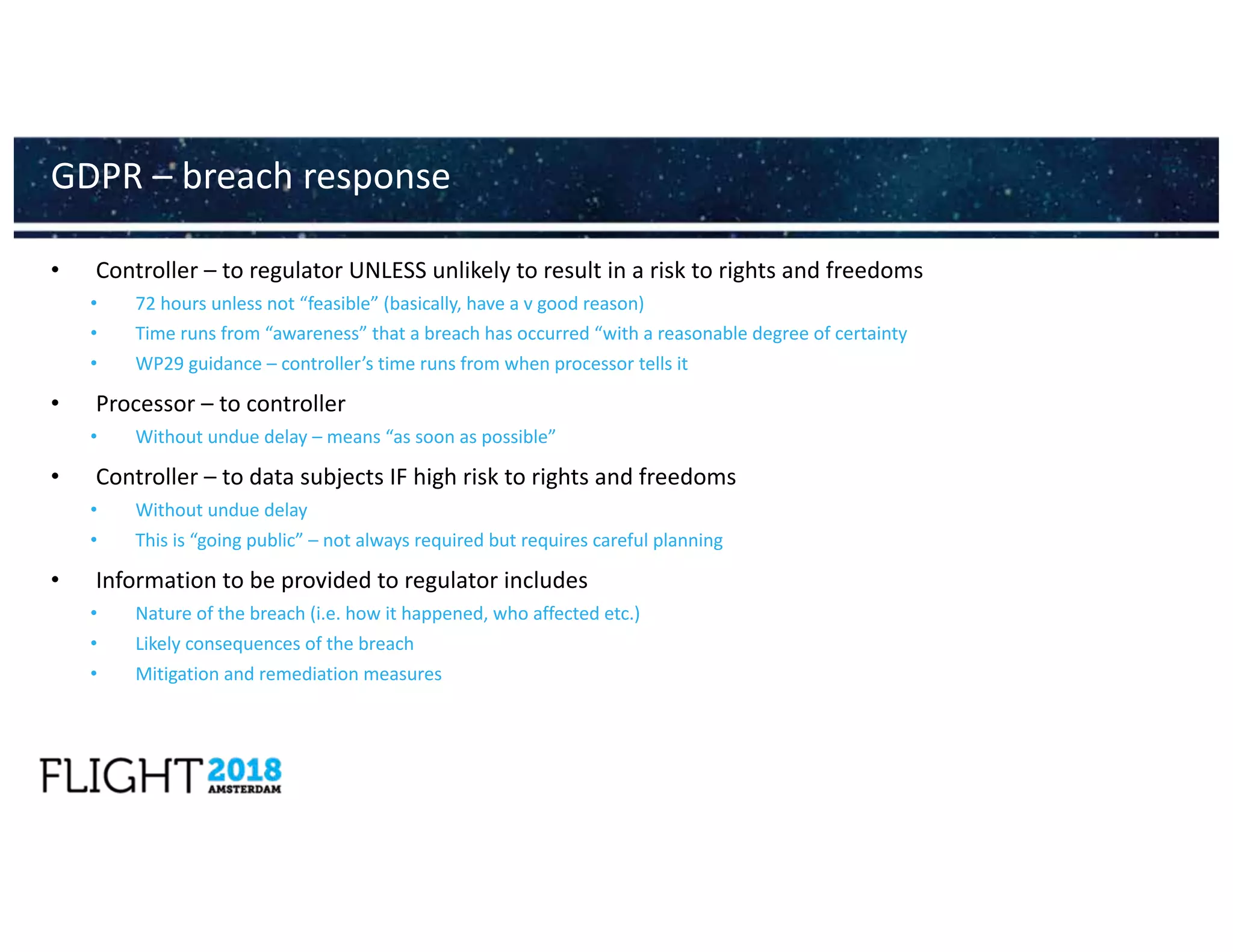



![• Security again similar to GDPR
• “identify and take appropriate and proportionate technical and organisational measures to
manage the risks posed to the security of network and information systems which they use in the
context of offering [digital services as defined previously]”
• Must take into account security of systems and facilities, incident handling, BCDR, monitoring,
auditing and testing, and “compliance with international standards” (ISO27001?)
• “measures to prevent and minimise the impact of incidents affecting the security of their network
and information systems on the [digital services as defined previously] offered within the Union,
with a view to ensuring continuity of those services”
• Must notify competent authority “without undue delay” of “any incident having a substantial impact on
the provision of [their service]”
• There is a draft implementing act kicking around the Commission giving more detail
Digital service providers – security and incident notification](https://image.slidesharecdn.com/irwinmitchellflght201815020926deck96-180621180735/75/FLIGHT-Amsterdam-Presentation-Data-Breaches-and-the-Law-A-Practical-Guide-15-2048.jpg)