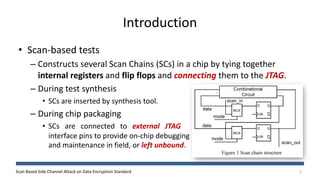
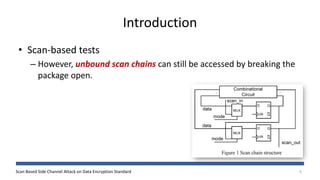
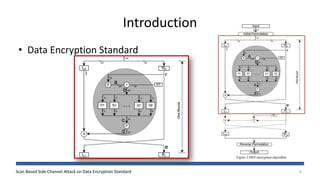
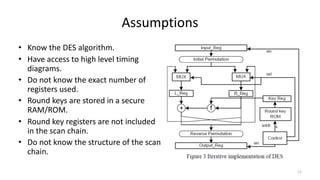
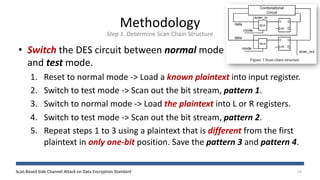
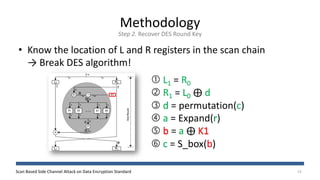
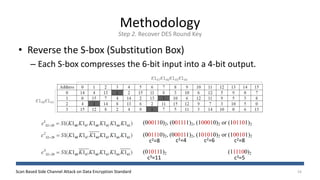
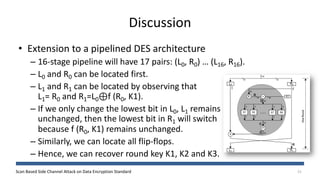
The document discusses a scan-based side channel attack on the Data Encryption Standard (DES), highlighting how scan chains can be exploited to extract secret keys from cryptographic devices. It outlines the assumptions and methodology used to recover both round and user keys through a structured attack process. The authors conclude that this method is effective and requires only a few plaintexts to successfully breach DES encryption.