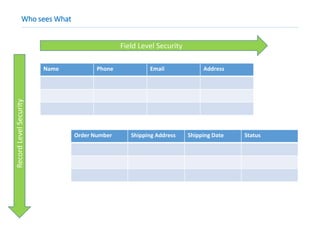
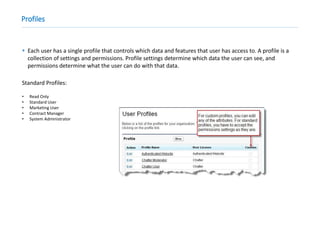
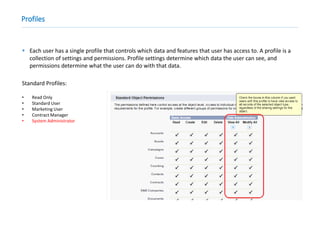
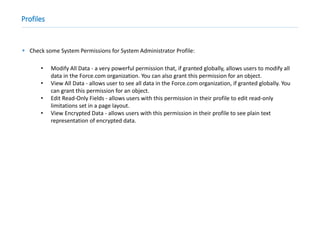
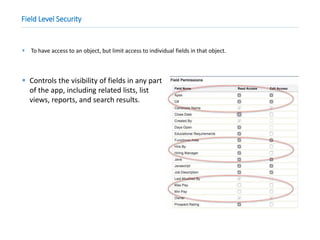
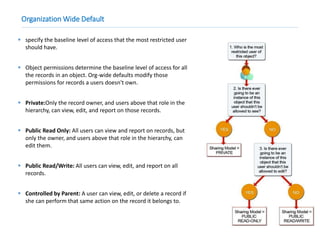
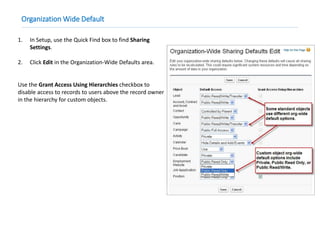
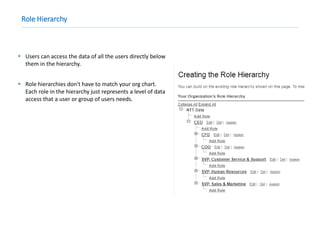
This document provides an overview of Salesforce sharing and visibility settings including profiles, permission sets, field level security, record level security, organization wide defaults, and role hierarchies. It discusses how profiles control user access and permissions. Permission sets extend user access without changing profiles. Field level security controls field visibility. Record level security and organization wide defaults specify default sharing while role hierarchies ensure managers have access to subordinate records.