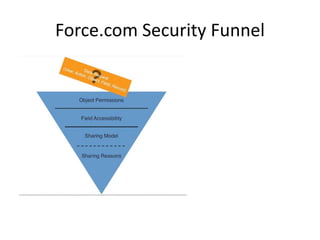
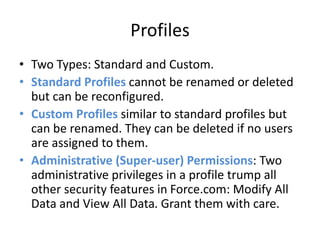
This document provides an overview of Force.com database security. It discusses how security is implemented through profiles and permissions rather than coding. Key aspects covered include profiles and their permissions, field level security, record ownership, sharing models, and how to implement the security model.