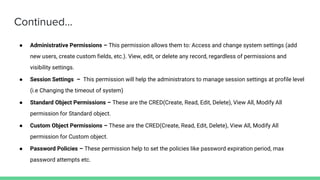
The document discusses Salesforce profiles and permission sets, detailing their definitions, types, features, and key aspects. Profiles determine user access and actions on the platform, while permission sets extend user access without changing profiles. Additionally, it introduces permission set groups as a mechanism for managing user entitlements effectively.