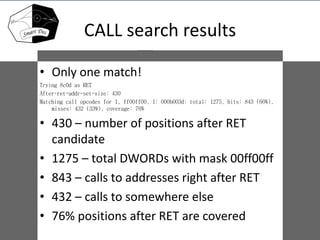
This document discusses reverse engineering a binary program for an unknown custom virtual machine. Through analyzing byte frequencies and instruction patterns, the authors were able to deduce key aspects of the virtual machine's architecture like the calling convention, return instruction, jump instructions, register usage, and arithmetic operations. Their approach involved heuristics-based searching to find common instruction encodings without any prior knowledge of the processor. While limited to simple analysis, this showed it is possible to gain a high-level understanding and decompose a binary without documentation. The authors develop the SmartDec decompiler to help with further reverse engineering virtual machine binaries.





![Search space
• Architecture search space:
– Word byte order: LE, BE
– Instruction encoding: byte stream/WORD
stream/DWORD stream…
– Code/data address space: uniform (von
Neumann), separate (Harvard)
– Code addressing: byte, WORD, …
– Register based, stack based
[WORD – 2 bytes, DWORD – 4 bytes]](https://image.slidesharecdn.com/reverseengineeringofbinaryprogramsforcustomvirtualmachines-150603141434-lva1-app6891/85/Reverse-engineering-of-binary-programs-for-custom-virtual-machines-7-320.jpg)