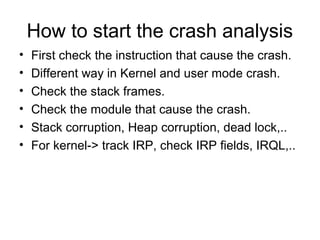
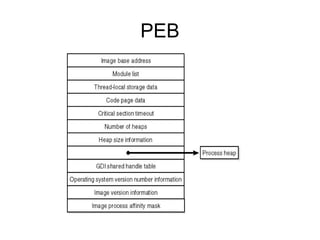
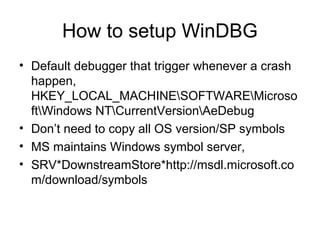
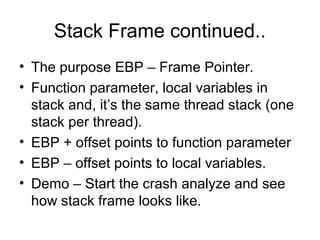
This document provides an overview of Windows user-mode debugging concepts like processes, threads, stack frames, and the WinDbg debugging tool. It discusses how to set up WinDbg and analyze crashes through examples like examining stack frames, debugging a simple crash, and commands commonly used in WinDbg. The document concludes with demonstrating how to analyze an IMA service crash using a memory dump.




![Let’s analyze a simple crash.
• 0:000> u Simple_App_Crash3!CSimpleAppCrash3Dlg::OnBnClickedButton1
• Simple_App_Crash3!CSimpleAppCrash3Dlg::OnBnClickedButton1 [d:sisimonworking
areapresentationswindbgsimple app crash3simple app crash3simple app crash3dlg.cpp
@ 154]:
• 00401580 55 push ebp - First Push EBP to stack
• 00401581 8bec mov ebp,esp Set new ebp as current esp
• 00401583 83ec14 sub esp,14h make enough room for local variable
• 00401586 894dec mov dword ptr [ebp-14h],ecx <- Copy the this pointer to stack
first element for the current stack frame
• 00401589 c745f400000000 mov dword ptr [ebp-0Ch],0 one of the local var to 0
• 00401590 c745fc0a000000 mov dword ptr [ebp-4],0Ah Another local var to 10
• 00401597 c745f80f000000 mov dword ptr [ebp-8],0Fh Another local var to 15
• 0040159e cc int 3 Our hard coded break point](https://image.slidesharecdn.com/windowsdebugging-sisimon-121205101619-phpapp01/85/Windows-debugging-sisimon-11-320.jpg)
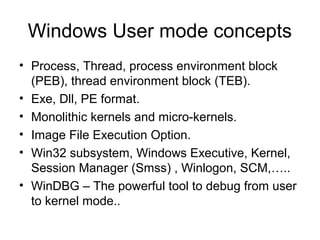
![• 0:000> u
• Simple_App_Crash3!CSimpleAppCrash3Dlg::OnBnClickedButton1+0x1f
[d:sisimonworking areapresentationswindbgsimple app crash3simple app
crash3simple app crash3dlg.cpp @ 160]:
• 0040159f 8b45f4 mov eax,dword ptr [ebp-0Ch]
• 004015a2 50 push eax push first arg to stack
• 004015a3 8b4df8 mov ecx,dword ptr [ebp-8]
• 004015a6 51 push ecx push second arg to stack
• 004015a7 8b55fc mov edx,dword ptr [ebp-4]
• 004015aa 52 push edx push third arg to stack
004015ab 8b4dec mov ecx,dword ptr [ebp-14h] set the this pointer to ecx
• 004015ae e82d000000 call Simple_App_Crash3!CSimpleAppCrash3Dlg::Add
(004015e0) call Add( unseen this in ecx, arg1, arg2, arg3)](https://image.slidesharecdn.com/windowsdebugging-sisimon-121205101619-phpapp01/85/Windows-debugging-sisimon-12-320.jpg)
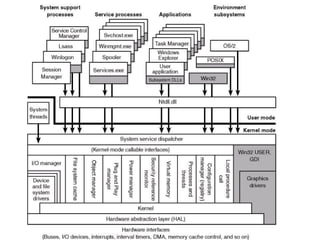
![• 0:000> u Simple_App_Crash3!CSimpleAppCrash3Dlg::Add
• Simple_App_Crash3!CSimpleAppCrash3Dlg::Add [d:sisimonworking
areapresentationswindbgsimple app crash3simple app crash3simple app crash3dlg.cpp
@ 166]:
• 004015e0 55 push ebp push new ebp
• 004015e1 8bec mov ebp,esp set new ebp and current esp
• 004015e3 51 push ecx push this to stack
• 004015e4 894dfc mov dword ptr [ebp-4],ecx
• 004015e7 8b45fc mov eax,dword ptr [ebp-4]
• 004015ea c7407464000000 mov dword ptr [eax+74h],64h set
• this->variable=100
• 004015f1 6838344000 push offset Simple_App_Crash3!
CSimpleAppCrash3App::`vftable'+0xd8 (00403438)
• 004015f6 ff15a4324000 call dword ptr [Simple_App_Crash3!_imp__printf (004032a4)]](https://image.slidesharecdn.com/windowsdebugging-sisimon-121205101619-phpapp01/85/Windows-debugging-sisimon-13-320.jpg)
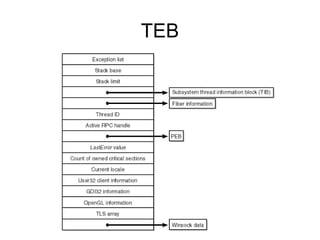
![• 0:000> r
• eax=00000000 ebx=00000111 ecx=0013fe74 edx=00000000 esi=00403444 edi=00000001
• eip=0040159e esp=0013f860 ebp=0013f874 iopl=0 nv up ei pl nz na pe nc
• cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206
• Simple_App_Crash3!CSimpleAppCrash3Dlg::OnBnClickedButton1+0x1e:
• 0040159e cc int 3
• 0:000> dds 0013f860
• 0013f860 0013fe74
• 0013f864 7e41b788 USER32!GetParent+0x59
• 0013f868 00000000
• 0013f86c 0000000f
• 0013f870 0000000a
• 0013f874 0013f884 push current ebp to stack, set new ebp as esp Stack Frame - 1
• 0013f878 7c1746cc MFC71!_AfxDispatchCmdMsg+0x3d [f:vs70builds3077vcmfcatlshipatlmfcsrcmfccmdtarg.cpp @ 89]
• 0013f87c 00403444 Simple_App_Crash3!CSimpleAppCrash3Dlg::messageMap
• 0013f880 0013fe74
• 0013f884 0013f8b4 push current ebp to stack, set new ebp as esp Stack Frame - 2
• 0013f888 7c171915 MFC71!CCmdTarget::OnCmdMsg+0x10a [f:vs70builds3077vcmfcatlshipatlmfcsrcmfccmdtarg.cpp @ 396]
• 0013f88c 0013fe74
• 0013f890 000003e8
• 0013f894 00000000
• 0013f898 00401580 Simple_App_Crash3!CSimpleAppCrash3Dlg::OnBnClickedButton1 [d:sisimonworking
areapresentationswindbgsimple app crash3simple app crash3simple app crash3dlg.cpp @ 154]
• 0013f89c 00000000
• 0013f8a0 00000035
• 0013f8a4 00000000
• 0013f8a8 0013fe74
• 0013f8ac 000003e8
• 0013f8b0 00000000
• 0013f8b4 0013f8d8 push current ebp to stack, set new ebp as esp, Stack Frame - 3
• 0013f8b8 7c14db36 MFC71!CDialog::OnCmdMsg+0x1b [f:vs70builds3077vcmfcatlshipatlmfcsrcmfcdlgcore.cpp @ 88]
• 0013f8bc 000003e8
• 0013f8c0 00000000
• 0013f8c4 00000000
• 0013f8c8 00000000
• 0013f8cc 000003e8
• 0013f8d0 0013fe74
• 0013f8d4 00000000
• 0013f8d8 0013f928
• 0013f8dc 7c175cd8 MFC71!CWnd::OnCommand+0x51 [f:vs70builds3077vcmfcatlshipatlmfcsrcmfcwincore.cpp @ 2549]](https://image.slidesharecdn.com/windowsdebugging-sisimon-121205101619-phpapp01/85/Windows-debugging-sisimon-14-320.jpg)