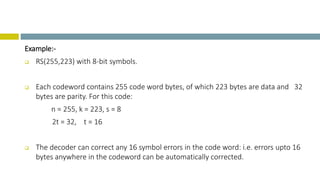
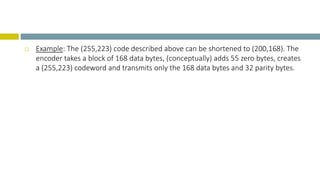
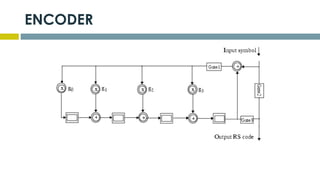
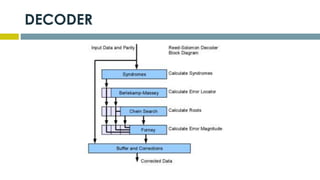
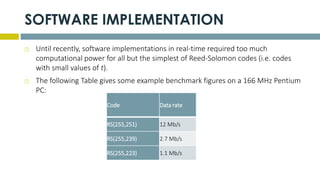
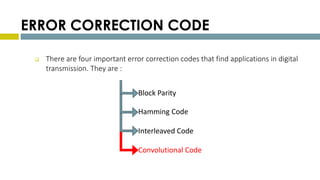
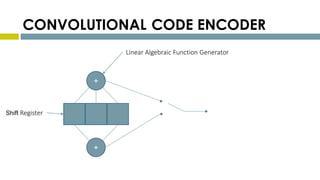
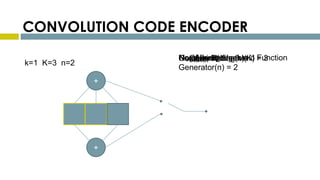
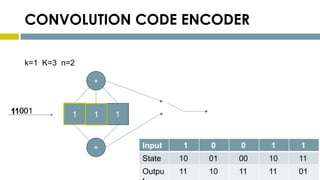
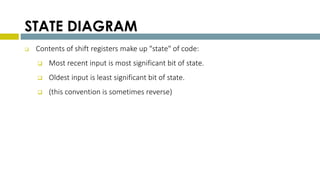
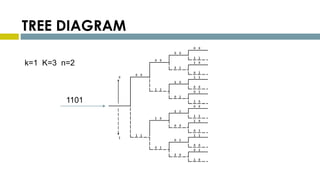
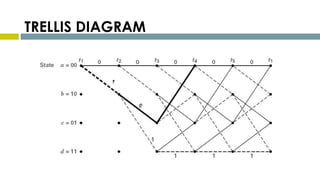
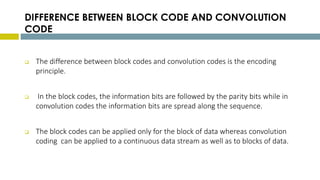
This document provides an overview of Reed-Solomon codes and convolutional codes. It describes the key properties and components of Reed-Solomon codes, including how they encode messages by dividing them into blocks and adding redundancy. It also explains convolutional codes use shift registers and linear algebraic functions to encode redundant information. The document compares block and convolutional codes and discusses factors like coding rate and constraint length that impact their performance.