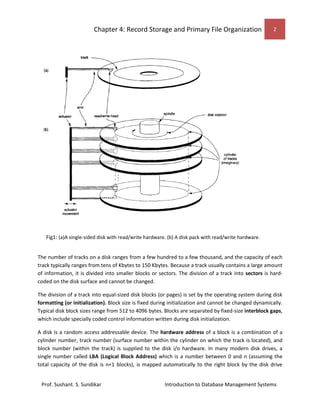
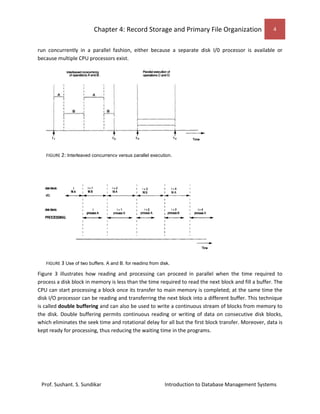
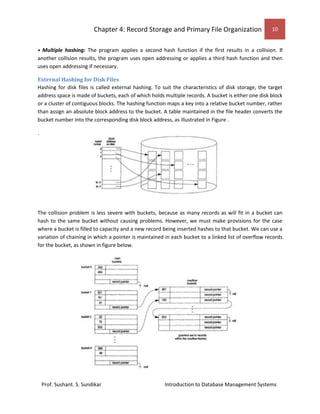
This document discusses record storage and primary file organization in databases. It describes how data is stored physically on storage media like primary storage (RAM) and secondary storage (disks, tapes). Disks allow random access of data blocks through addressing of cylinders, tracks, and blocks, while tapes only allow sequential access. The document discusses buffering of blocks to improve performance of reading and writing multiple blocks from disks. It also describes how records containing fields of data are placed and organized on disk storage.