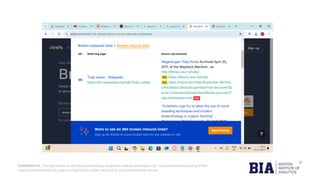
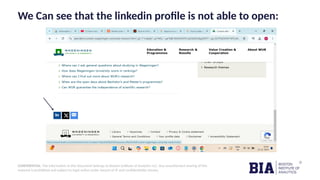
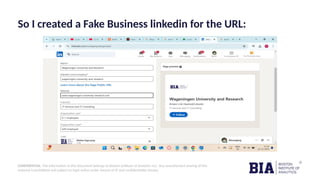
The document reports on broken link hijacking (BLH), a web security vulnerability where attackers exploit inactive hyperlinks to redirect users to malicious sites. It includes a case study on a specific website, example.com, and presents mitigation strategies, emphasizing the need for regular link maintenance and monitoring. The findings highlight the potential impacts of BLH, including reputational damage and legal consequences, and advocate for proactive measures to enhance web security.