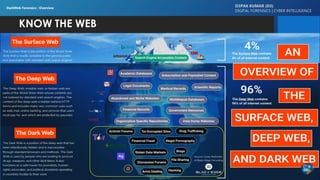
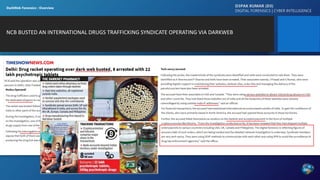
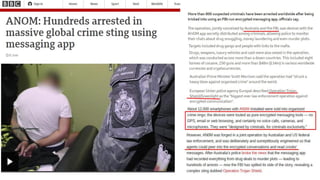
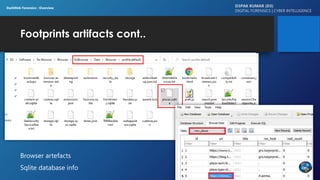
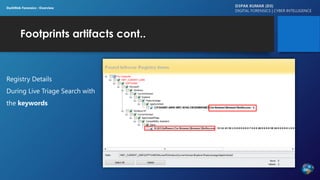
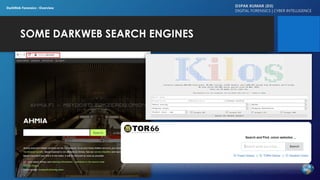
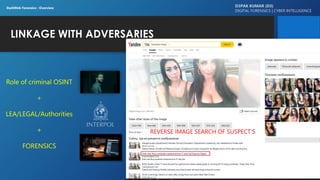
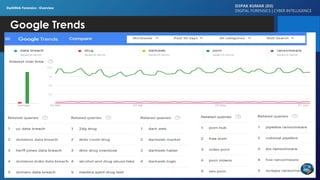
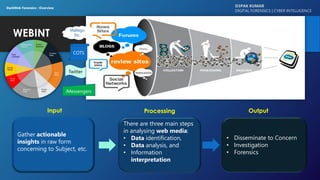
The document discusses dark web forensics, highlighting the prevalence of cyber crimes such as financial fraud, hacking, and data breaches. It details various tools and technologies used for anonymity in the dark web, alongside notable examples of illegal marketplaces and criminal activities. The presentation emphasizes the need for proper forensic procedures, legal coordination, and international cooperation in combating cyber threats.