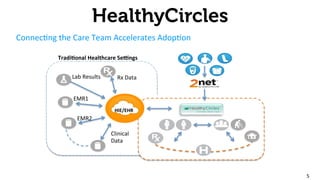
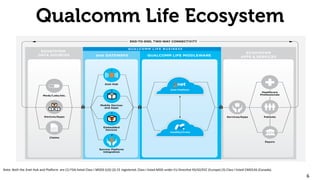
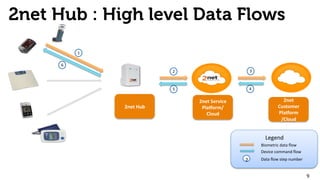
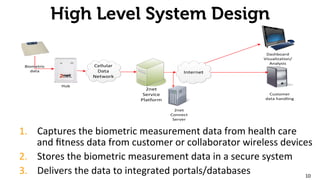
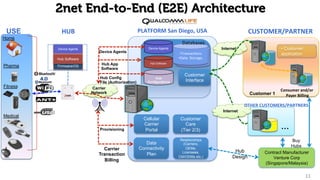
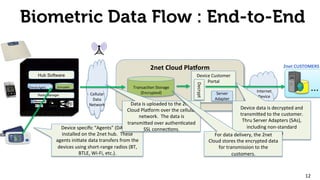
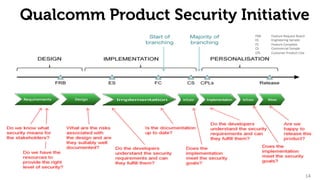
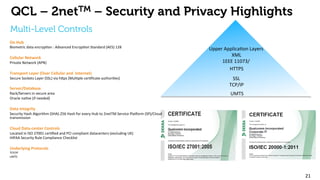
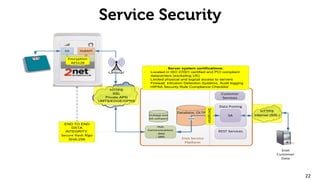
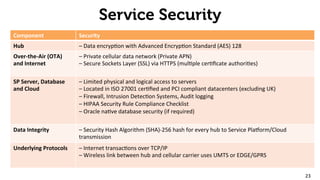
The document provides an overview of the 2net system, including its product overview describing how biometric data flows from devices to the cloud platform, as well as its security and privacy features leveraging Qualcomm's expertise in network operations. Key aspects covered include the 2net hub, cloud platform, and end-to-end data flows, as well as Qualcomm's focus on proactive data protection, cybersecurity initiatives, and use of a premier enterprise wireless data platform.