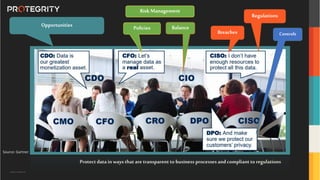
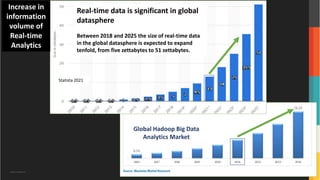
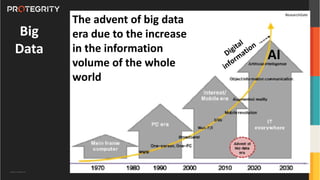
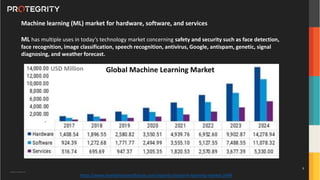
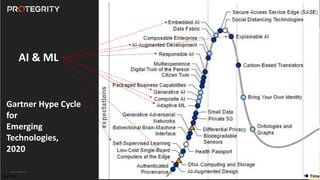
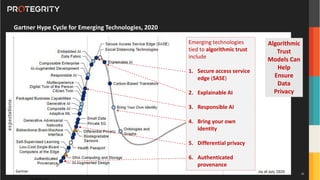
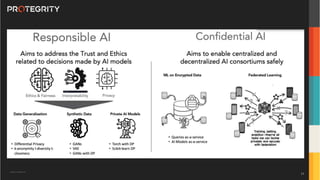
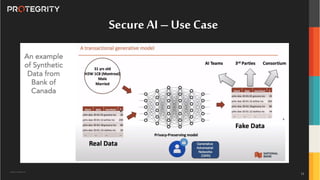
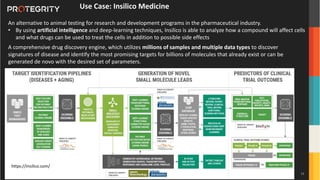
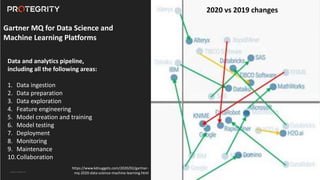
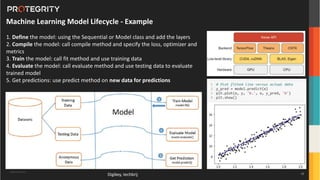
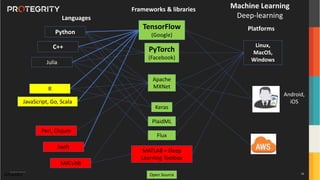
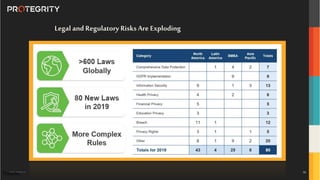
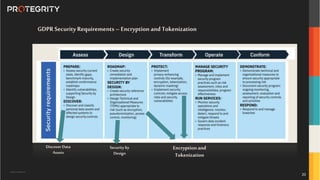
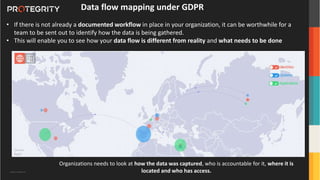
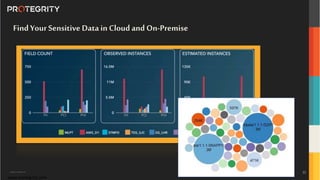
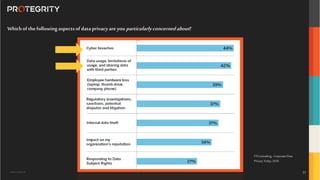
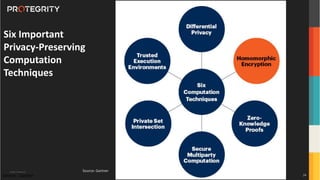
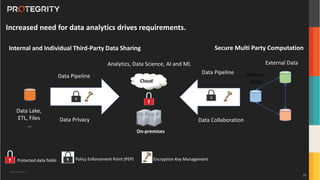
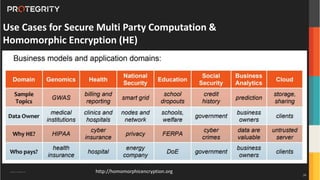
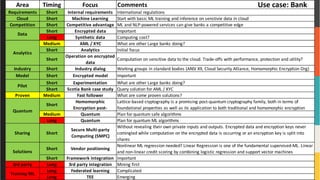
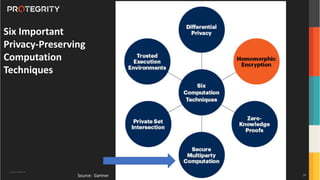
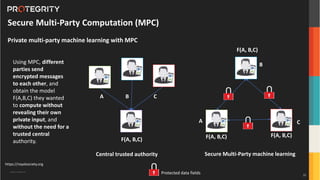
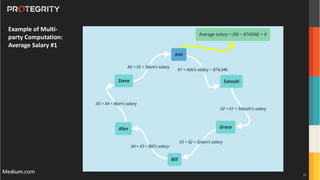
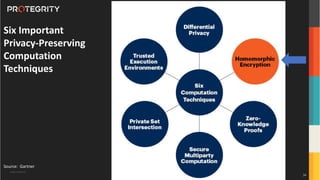
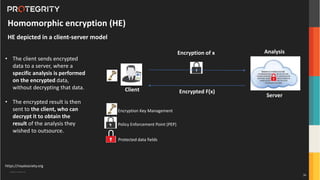
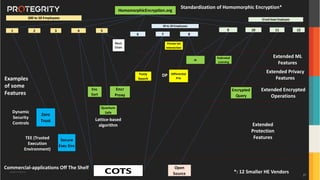
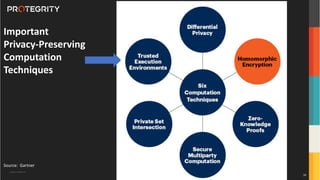
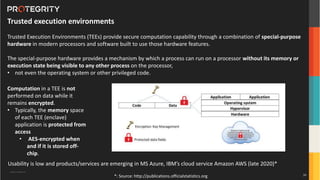
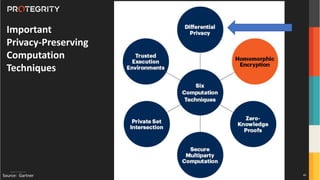
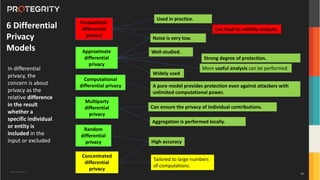
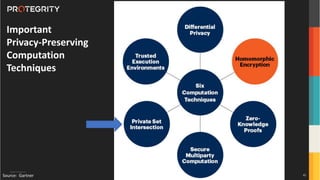
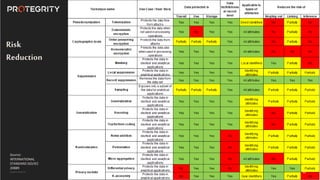
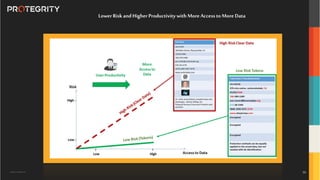
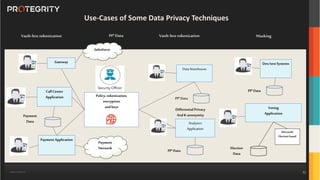
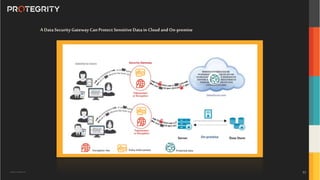
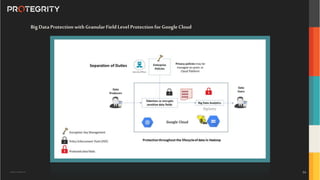
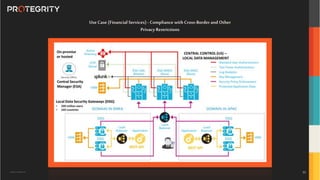
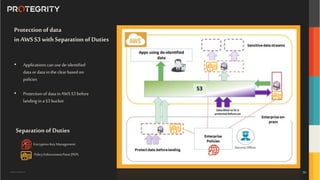
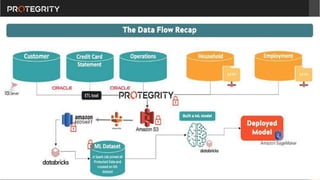
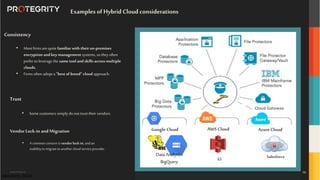
The document discusses various aspects of data security, focusing on privacy-preserving computing concepts such as secure multi-party computation, homomorphic encryption, and differential privacy. It emphasizes the importance of complying with regulations like GDPR and CCPA while leveraging machine learning and big data analytics in various industries. It presents use cases, challenges, and opportunities related to data governance and provides insights into the future of secure data sharing amongst organizations.