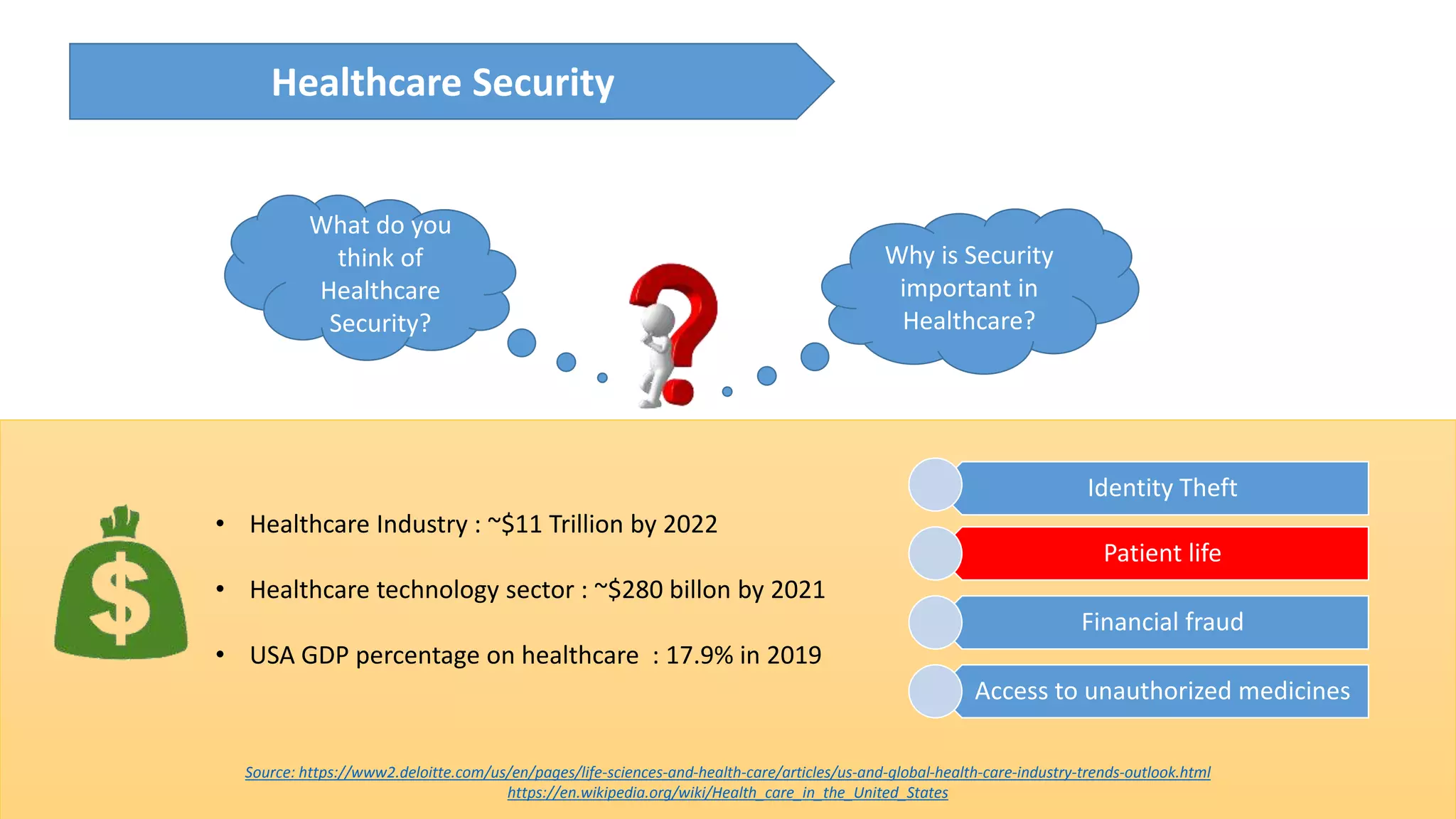
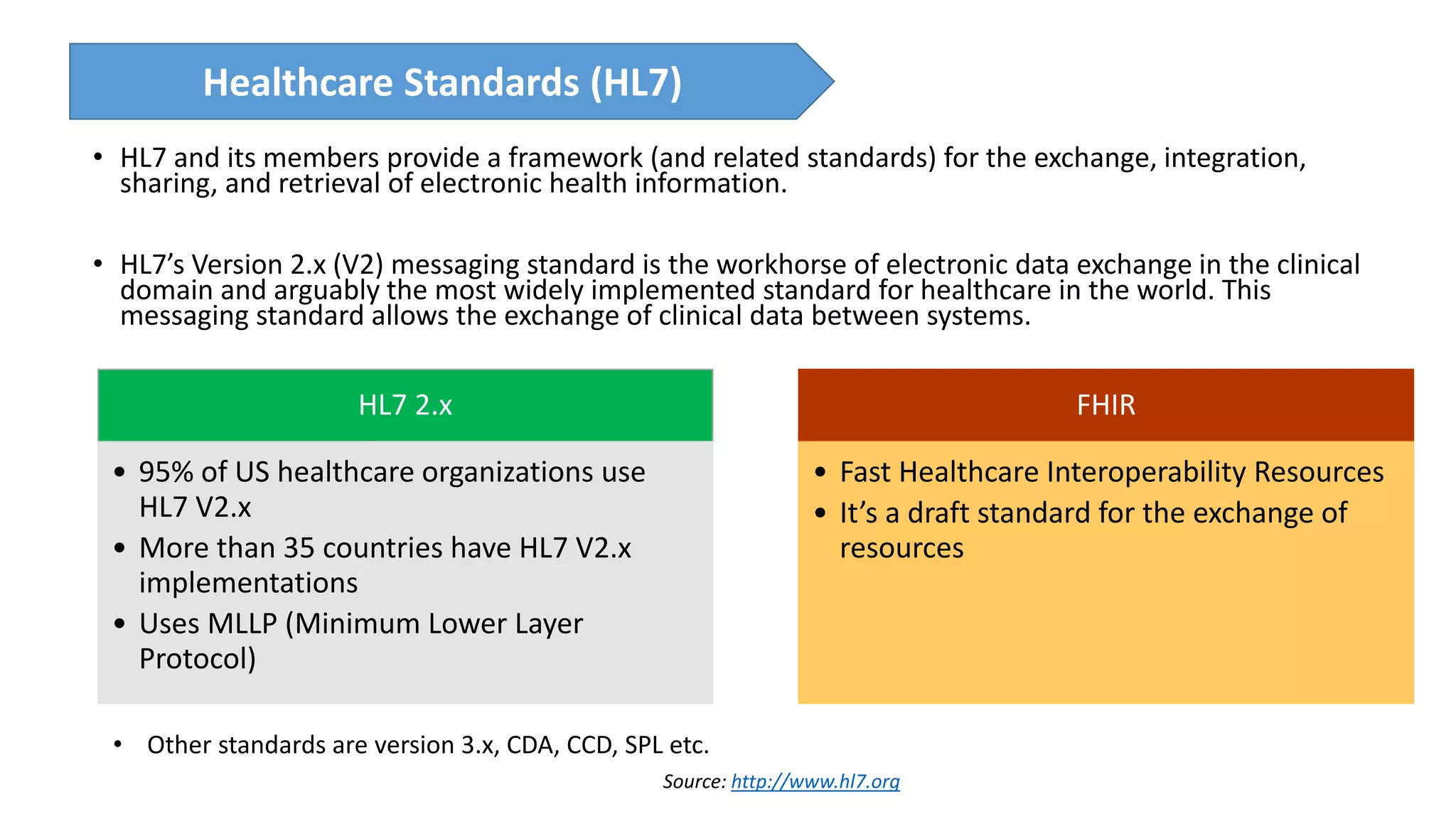
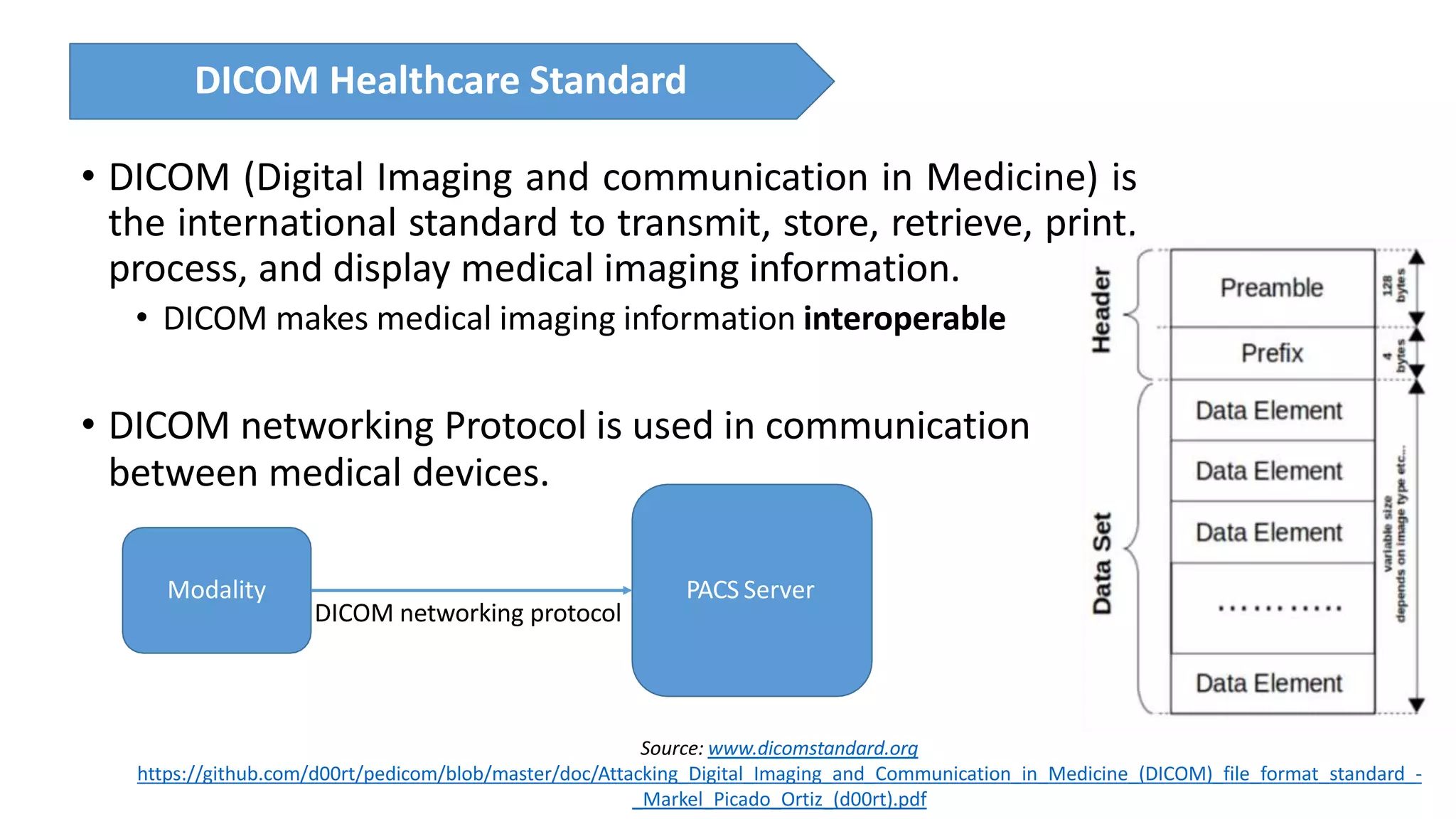
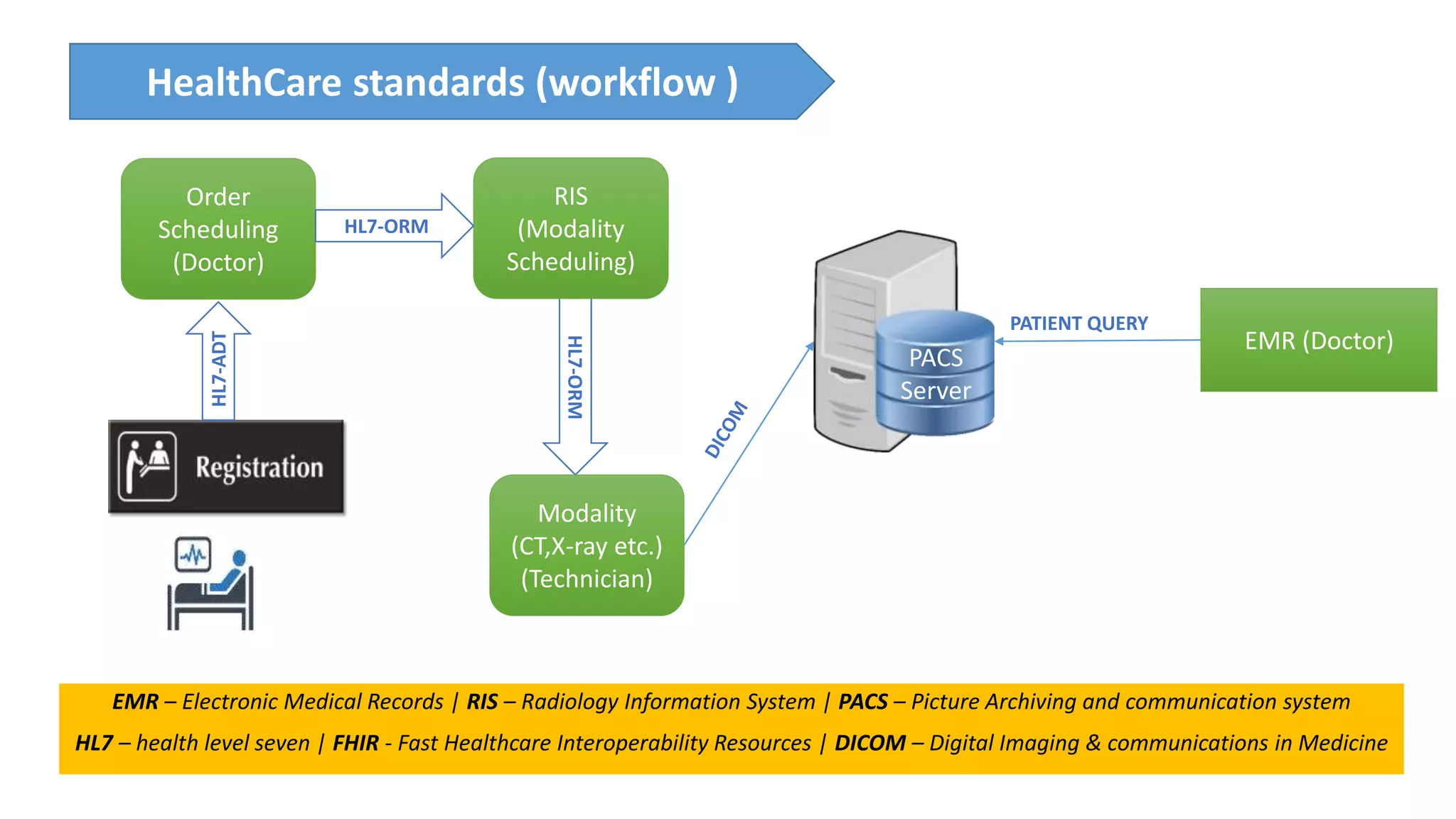
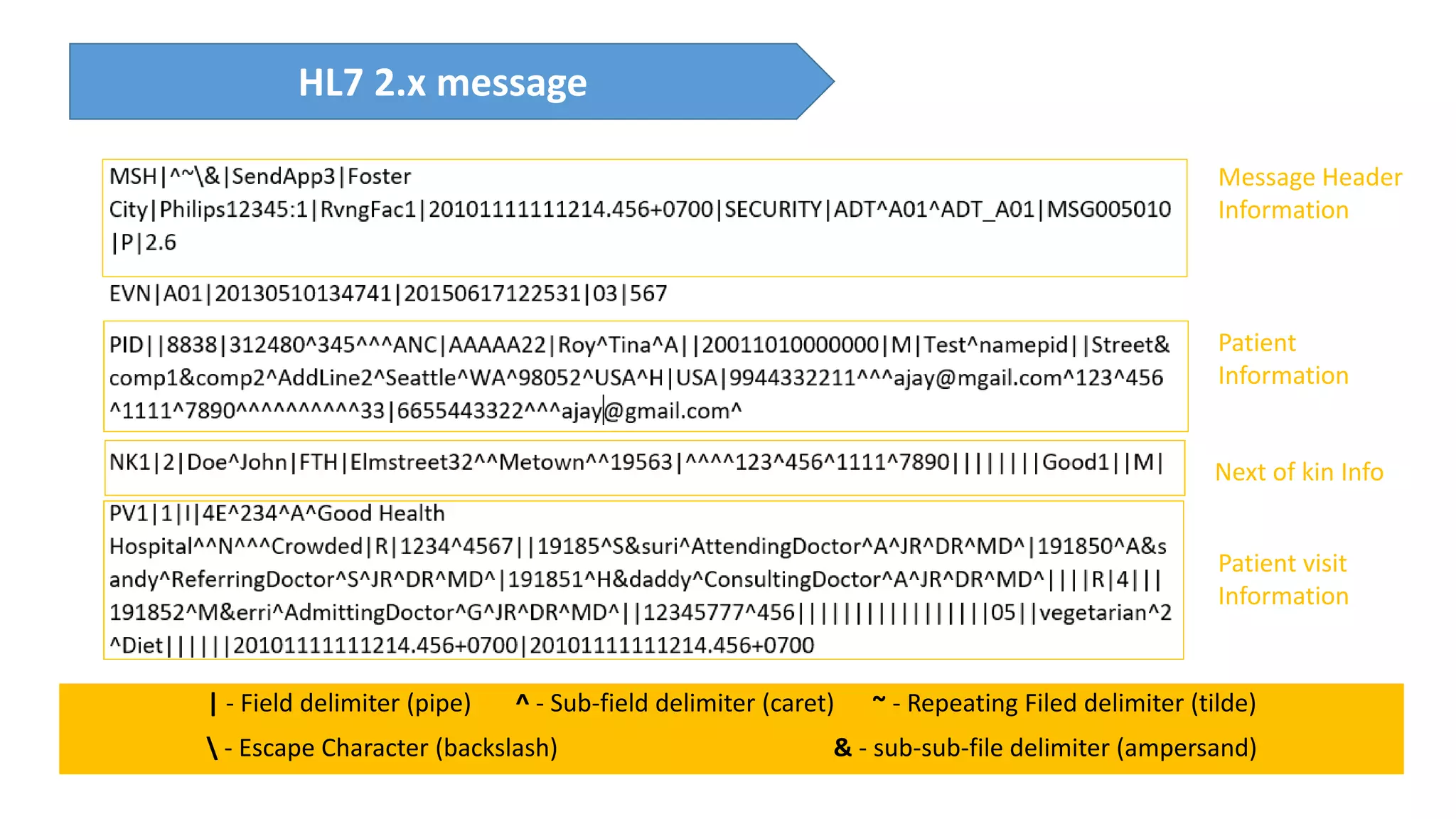
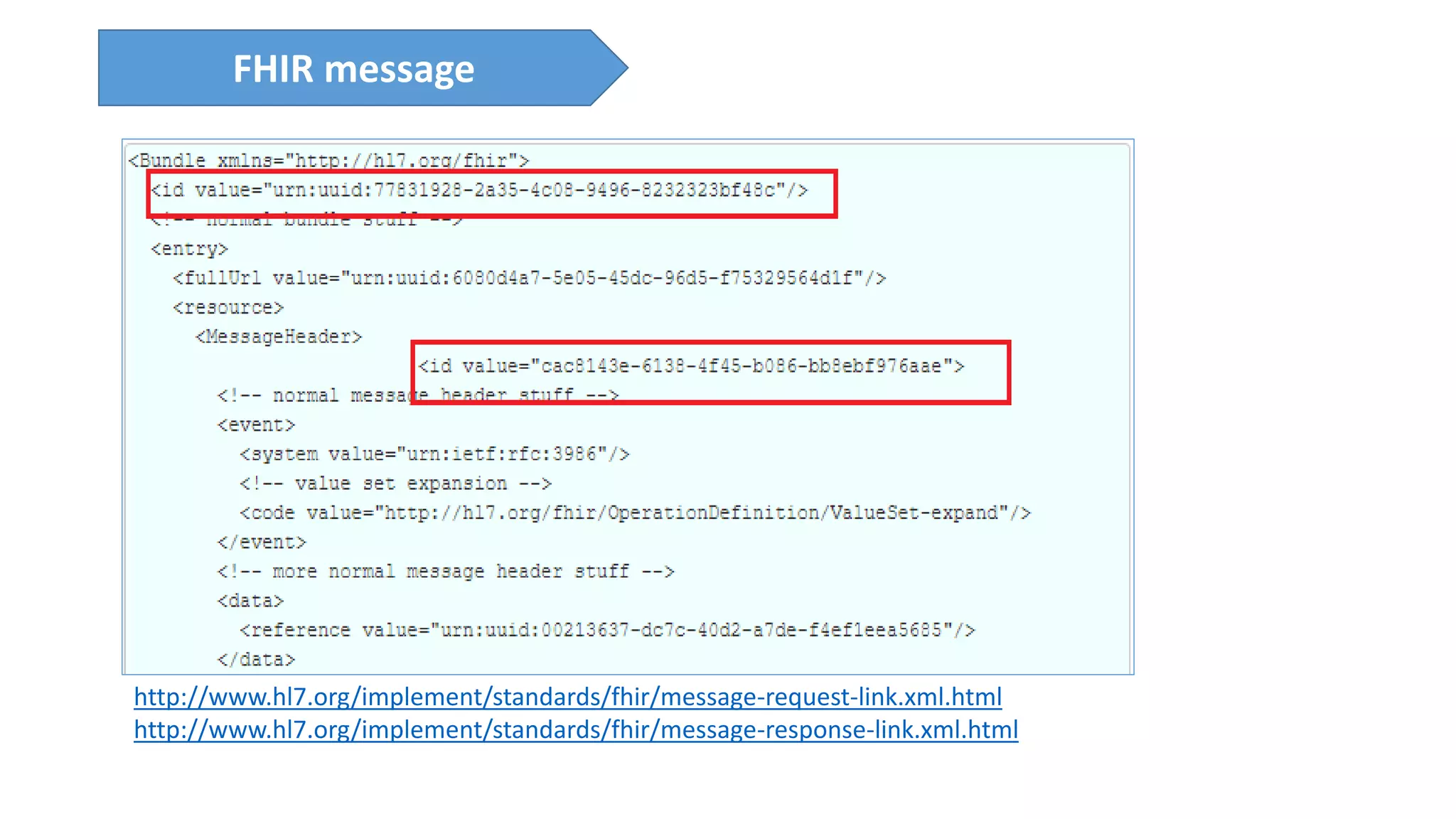
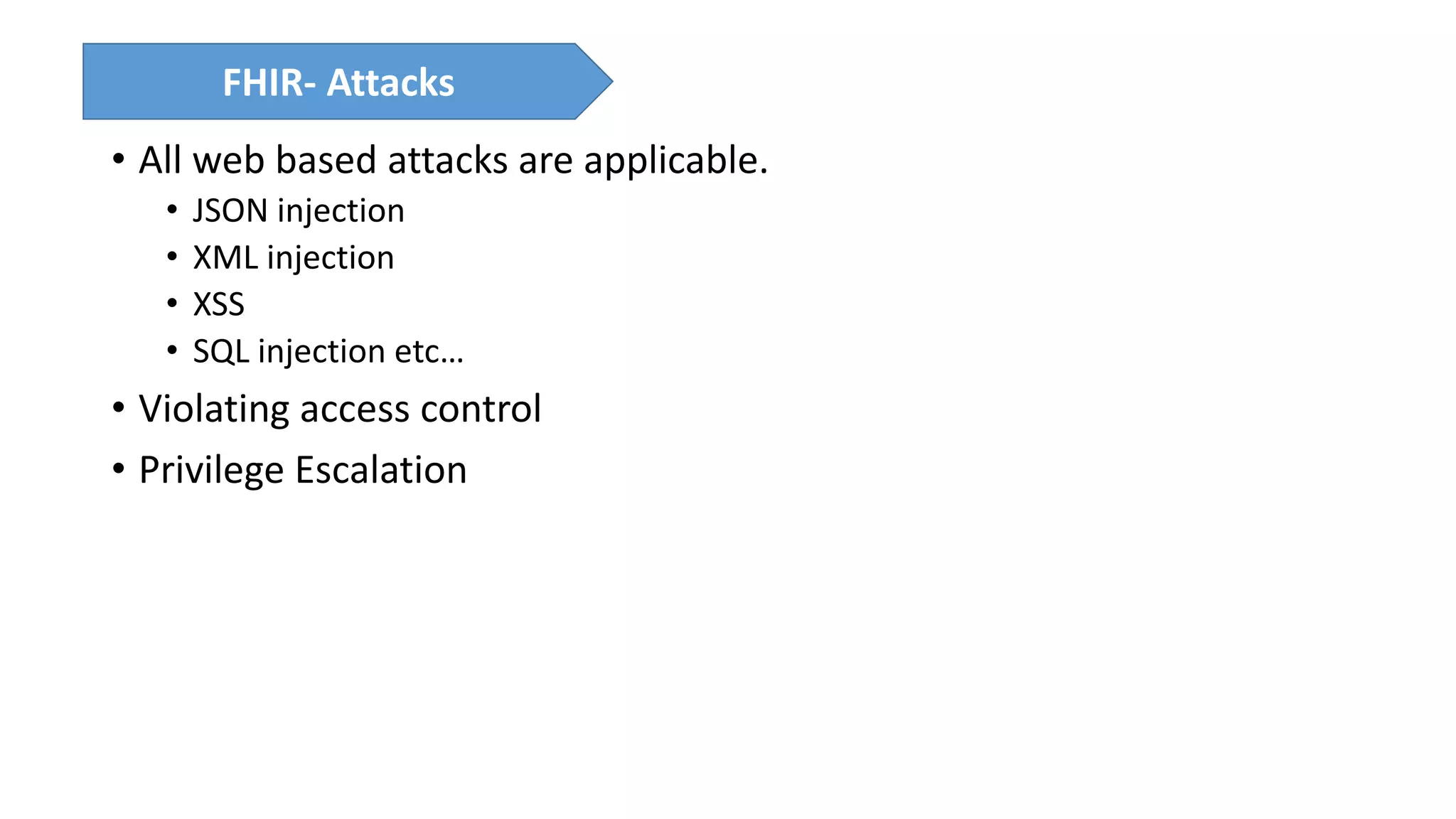
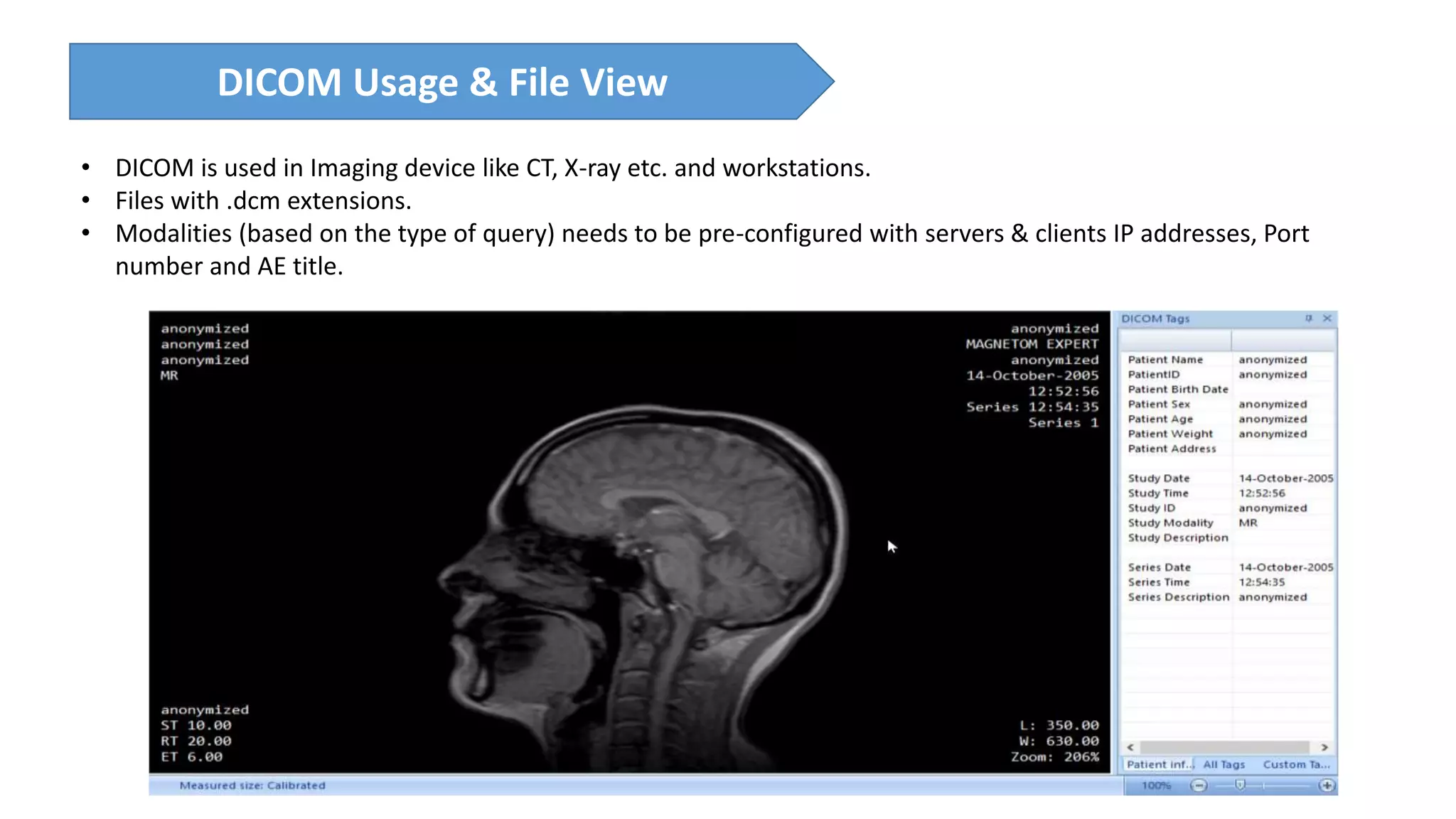
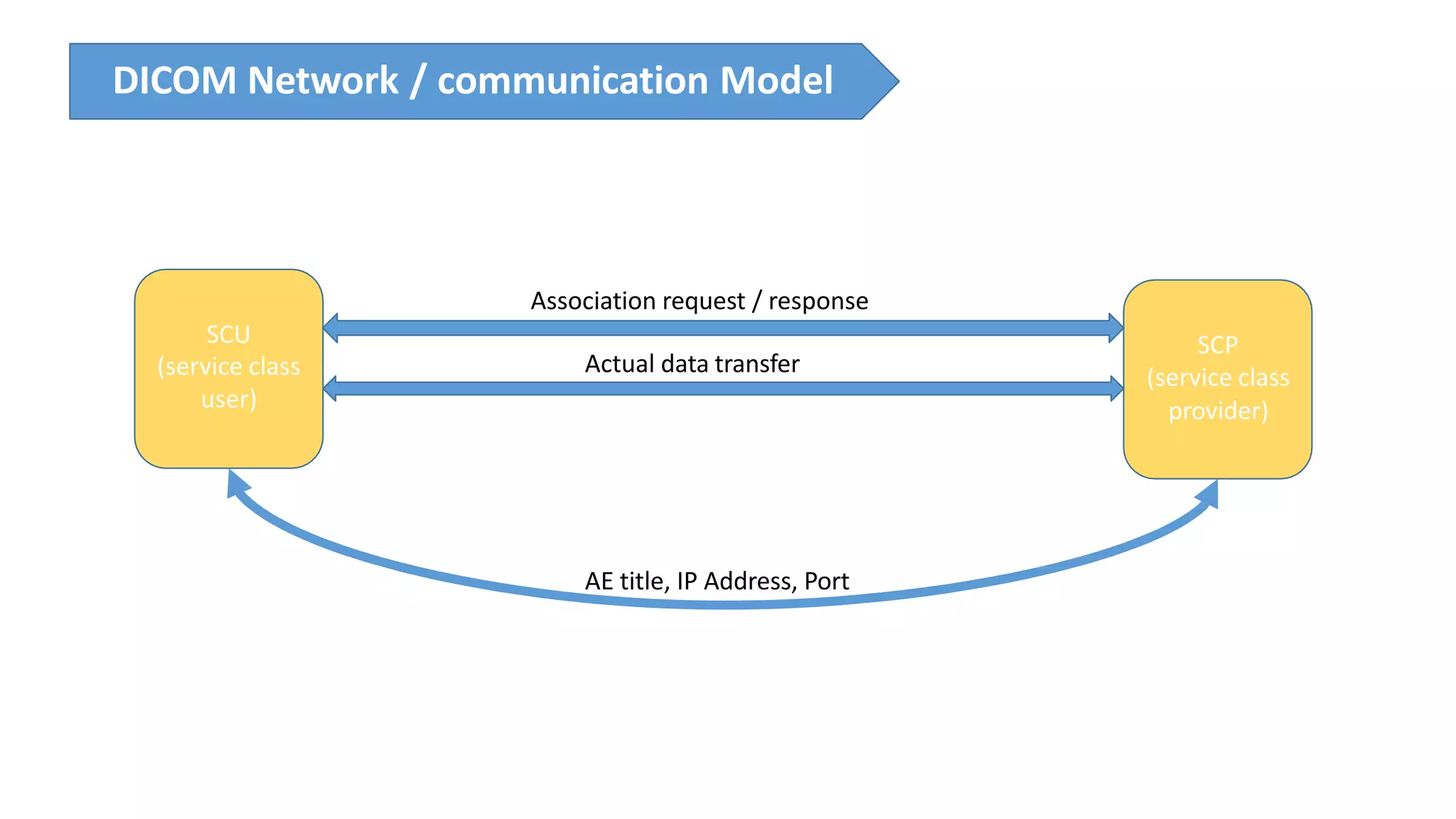
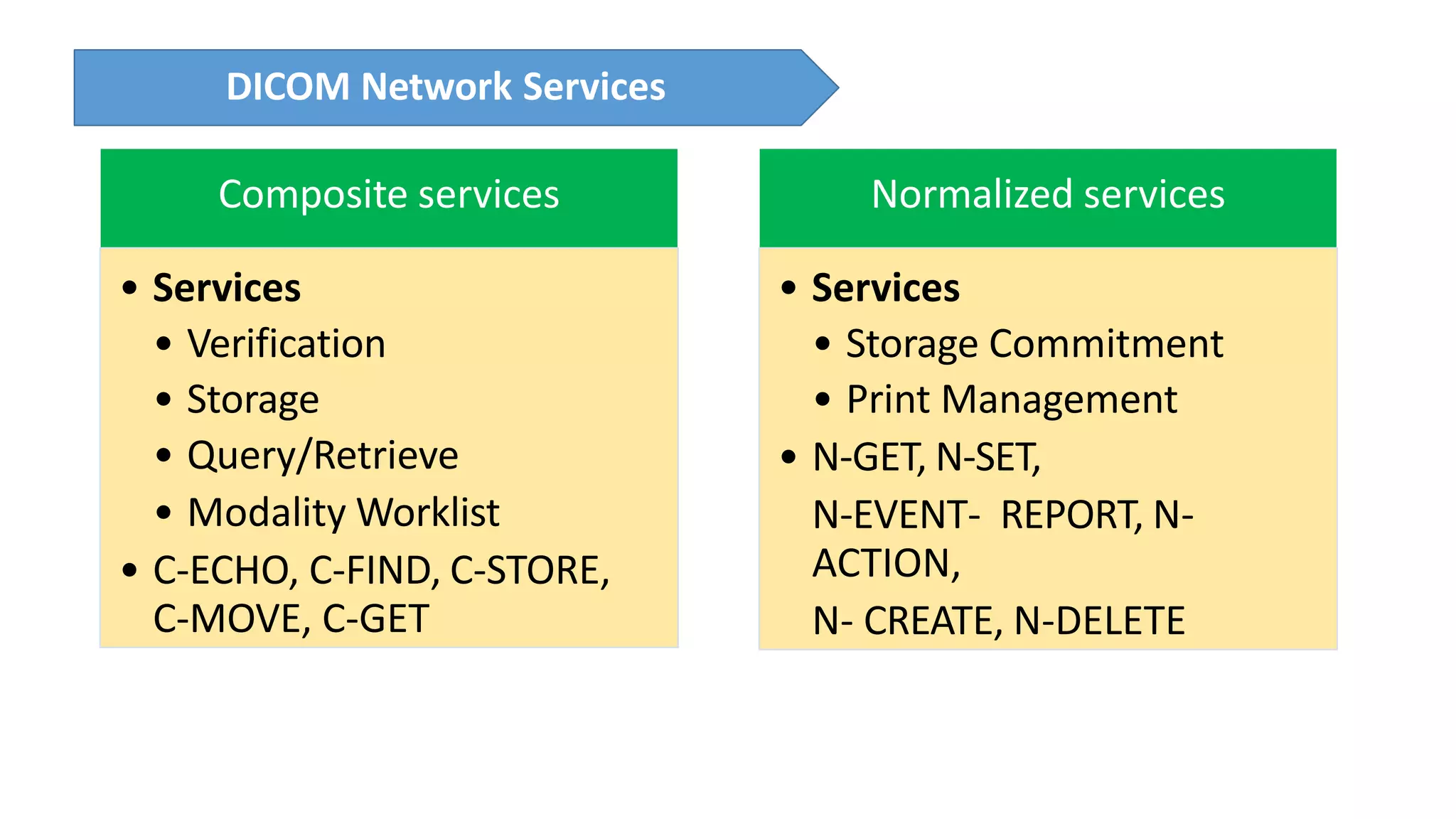
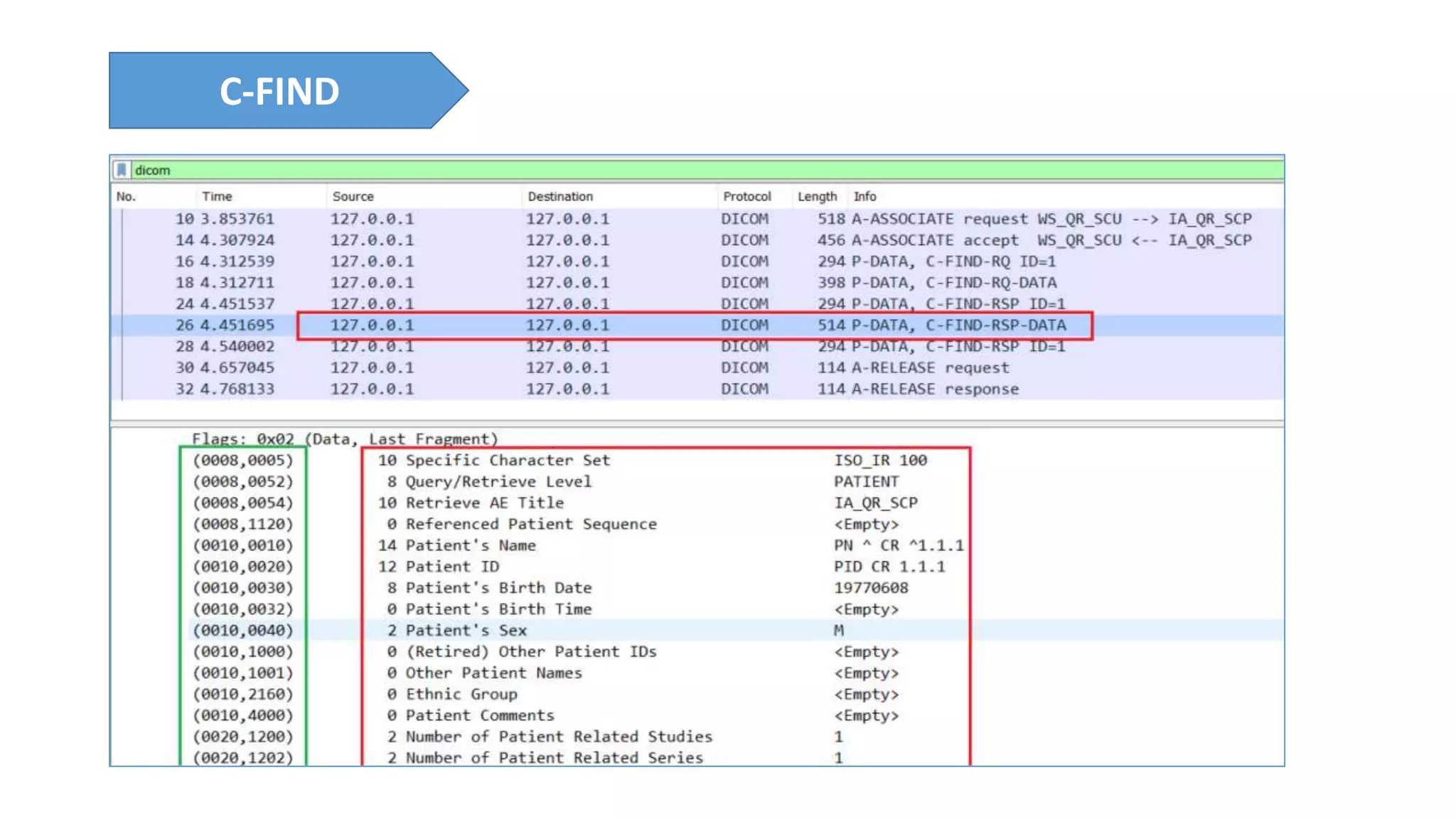
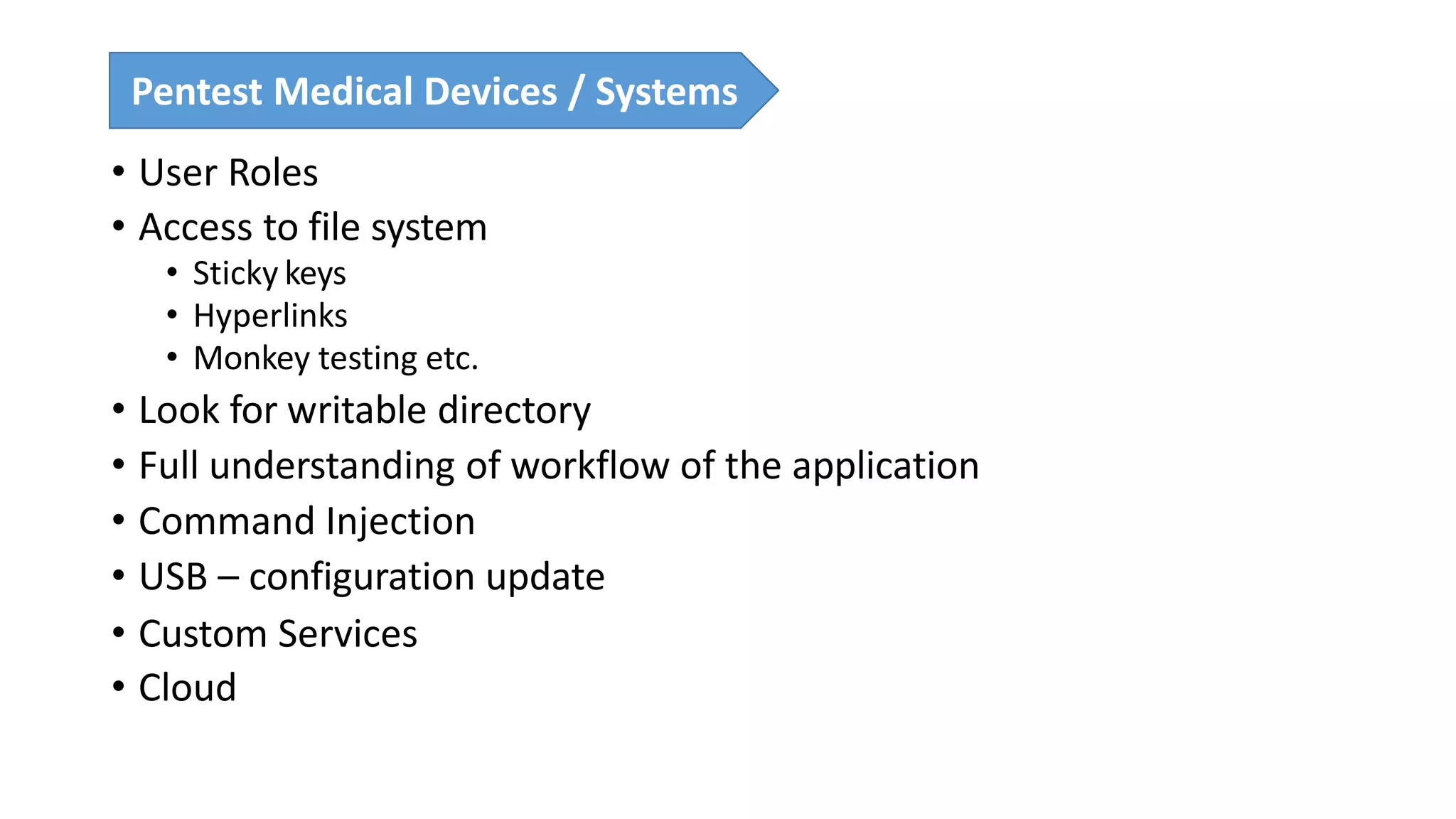
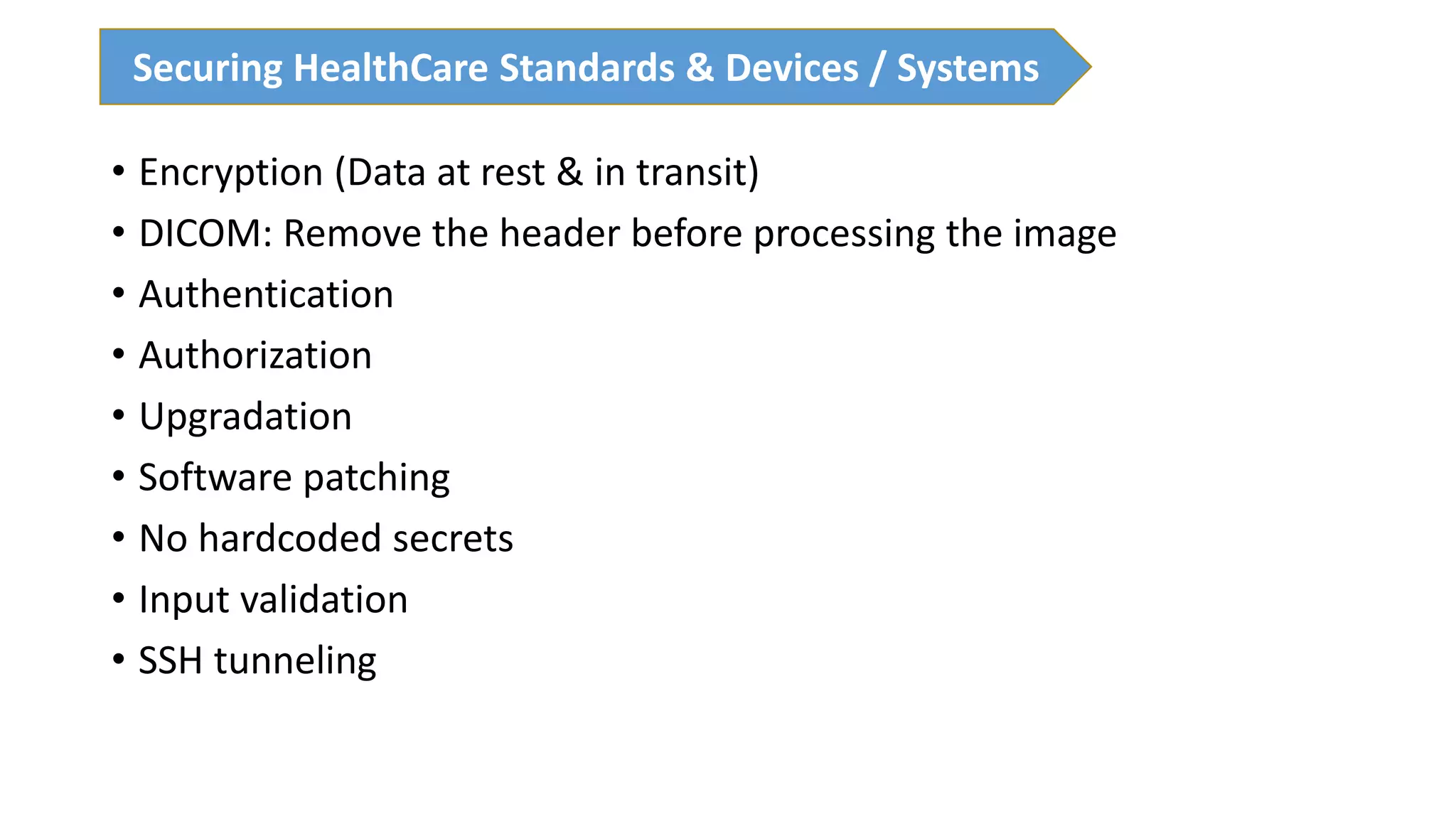
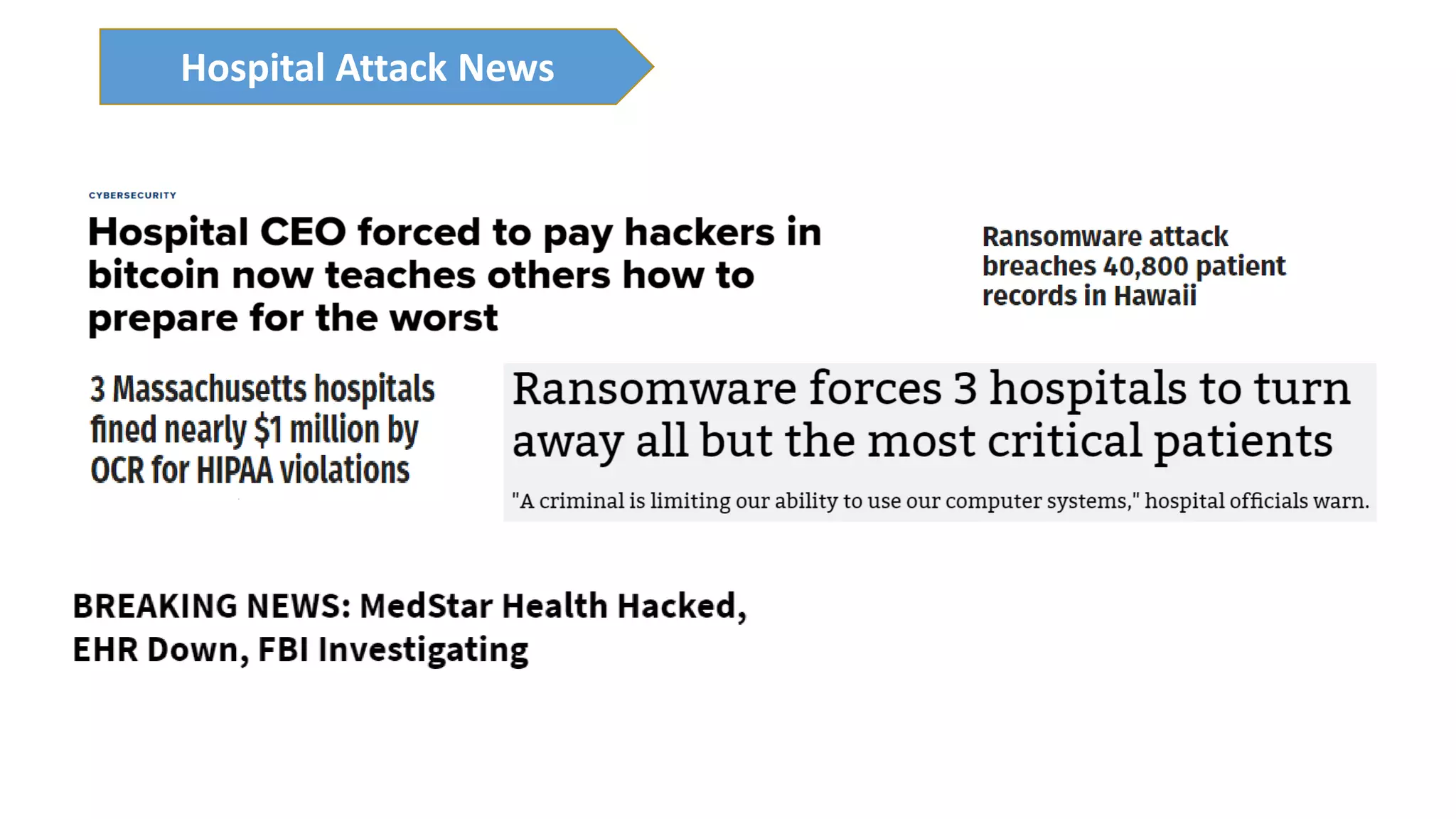
The presentation discusses the importance of healthcare security and provides an overview of various healthcare standards including HL7, FHIR, and DICOM, which facilitate the exchange and management of medical information. It highlights the risks associated with electronic health data, such as identity theft and unauthorized access, while also outlining methodologies for pen-testing medical devices to enhance security. The speaker, Ajay Pratap Singh, emphasizes the need for rigorous security measures to protect healthcare systems and standards from cyber threats.