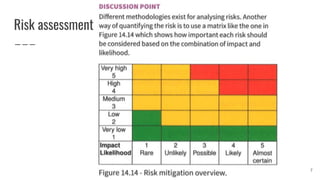
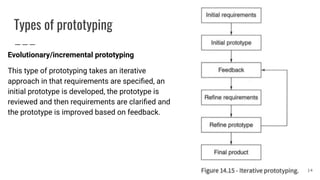
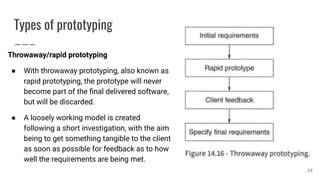
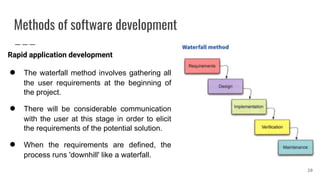
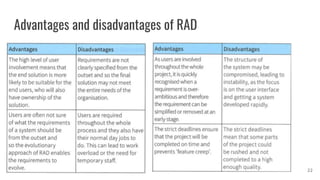
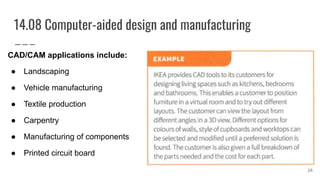
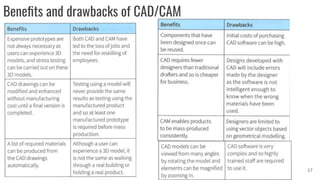
This document discusses project management and computer-aided design and manufacturing. It begins by explaining the importance of disaster recovery planning and risk assessment when unexpected events occur. It then discusses prototyping software solutions, different development methods like rapid application development and waterfall, and the benefits of computer-aided design and manufacturing applications.