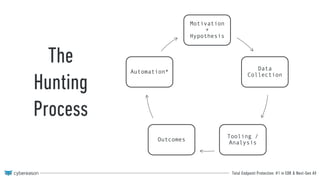
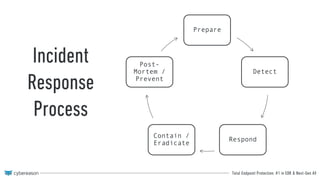
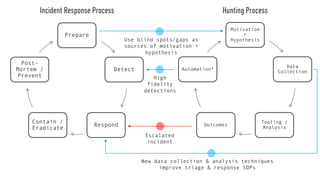
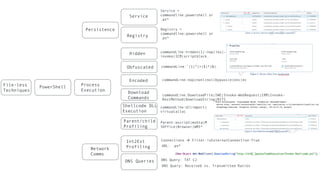
This document discusses maturing a threat hunting program. It provides an overview of threat hunting, including defining the process as proactively discovering undesirable activity to elicit a positive outcome. It reviews the hunting process of having a motivation/hypothesis, collecting data, using tools for analysis, and achieving outcomes. It then discusses how hunting outcomes can improve an incident response process by providing detections, new collection techniques, and prevention capabilities. The document dives deeper into expanded hunting of PowerShell techniques like file-less execution, persistence, network communications, and provides examples of how hunting could escalate incidents or enable prevention controls related to PowerShell.