This document summarizes a presentation on big data and data reuse given by Bart Custers. It discusses:
1) The Eudeco project which examines big data and data reuse from legal, societal, economic, and technological perspectives across multiple European countries.
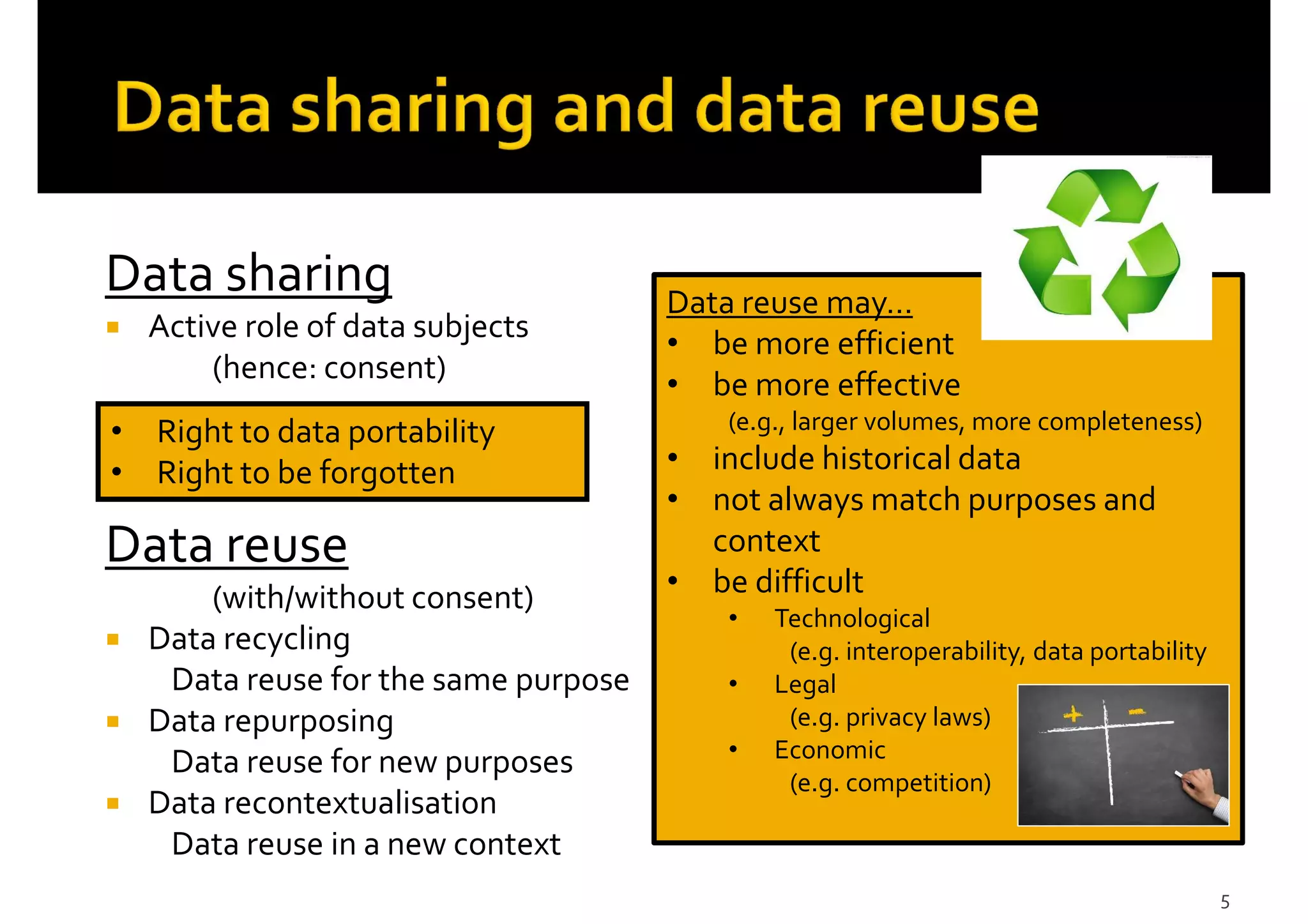
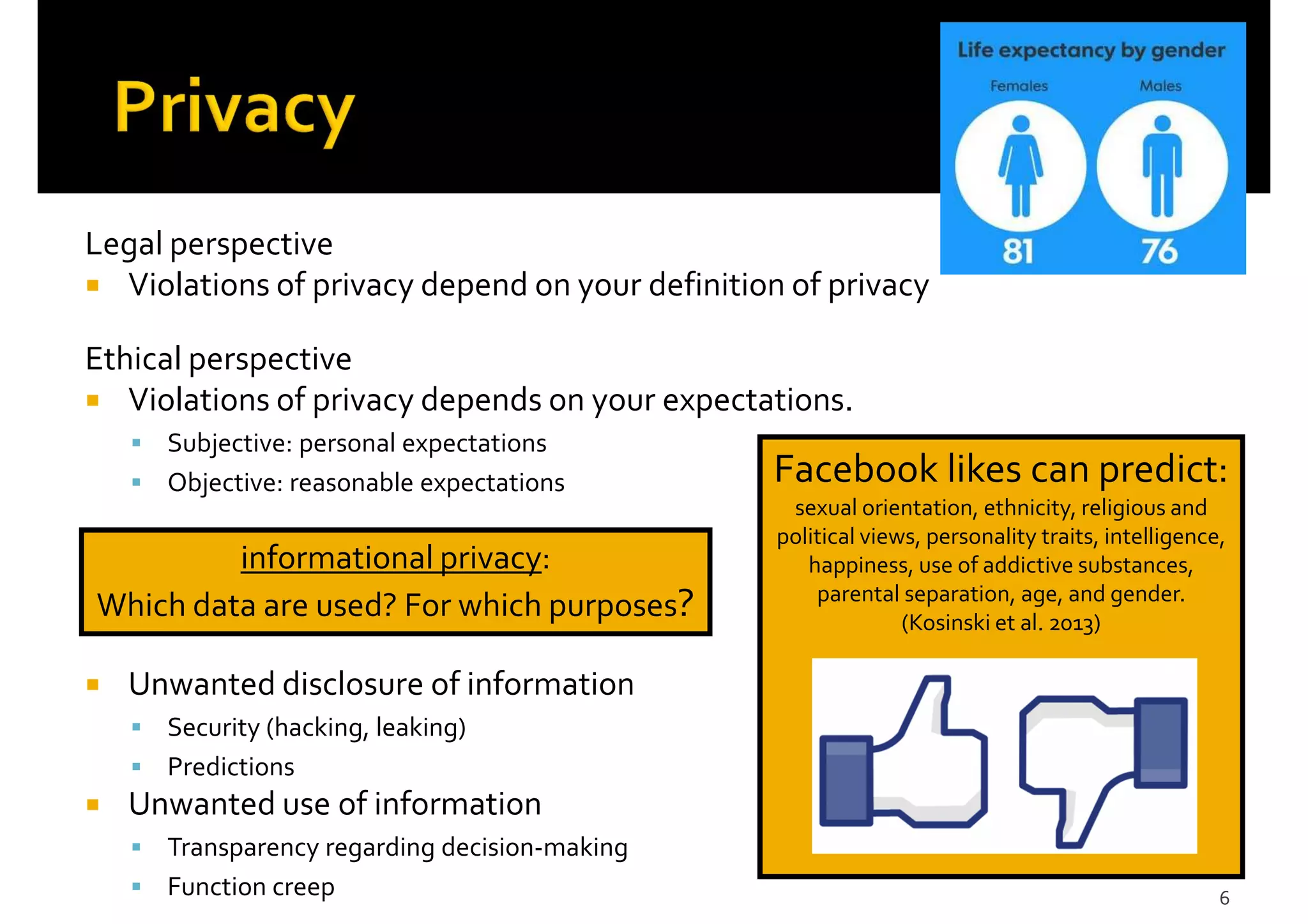
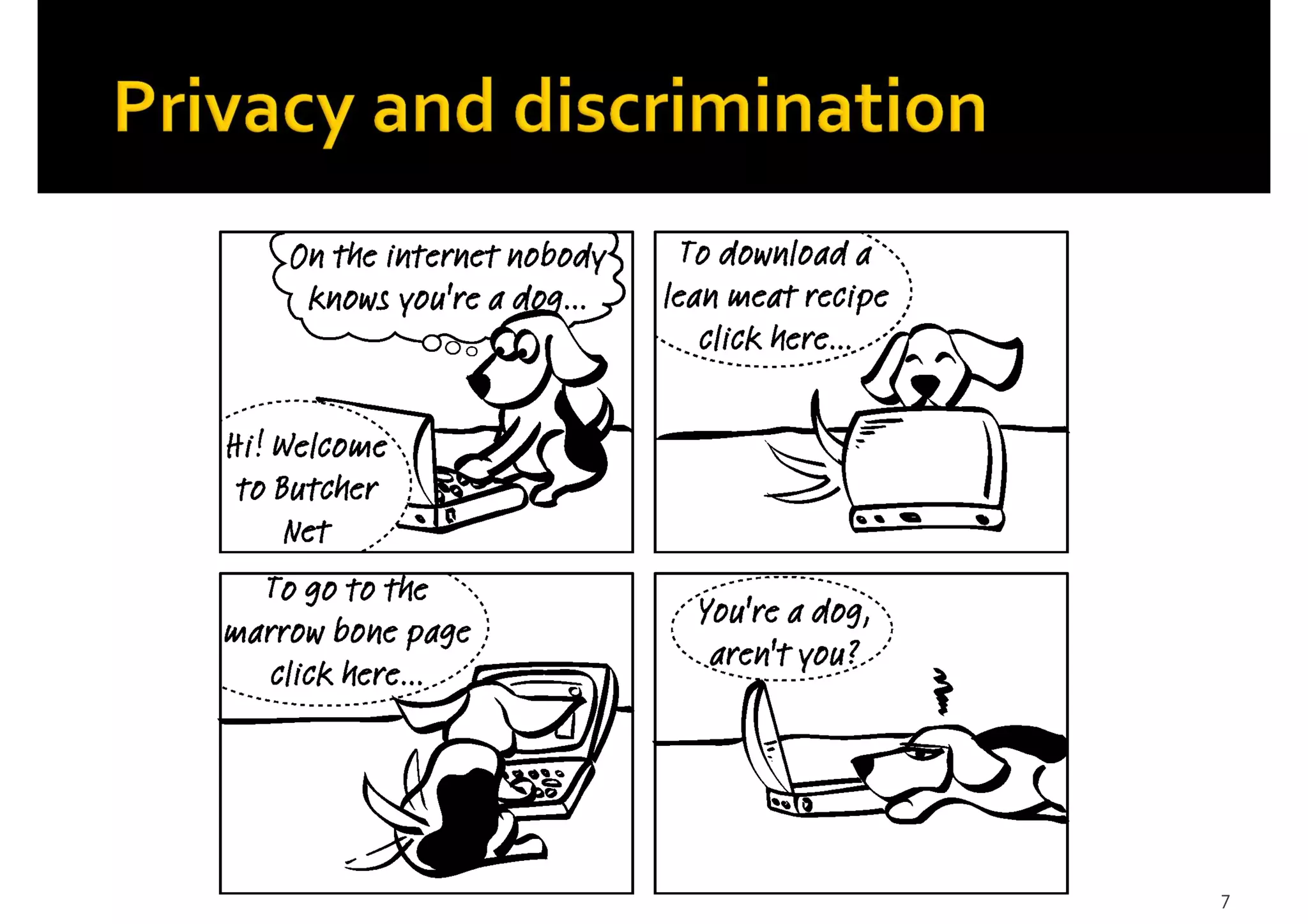
2) Issues with data sharing and reuse, including potential privacy violations, discrimination, lack of transparency, and unintended consequences from new uses of data or placing it in new contexts.
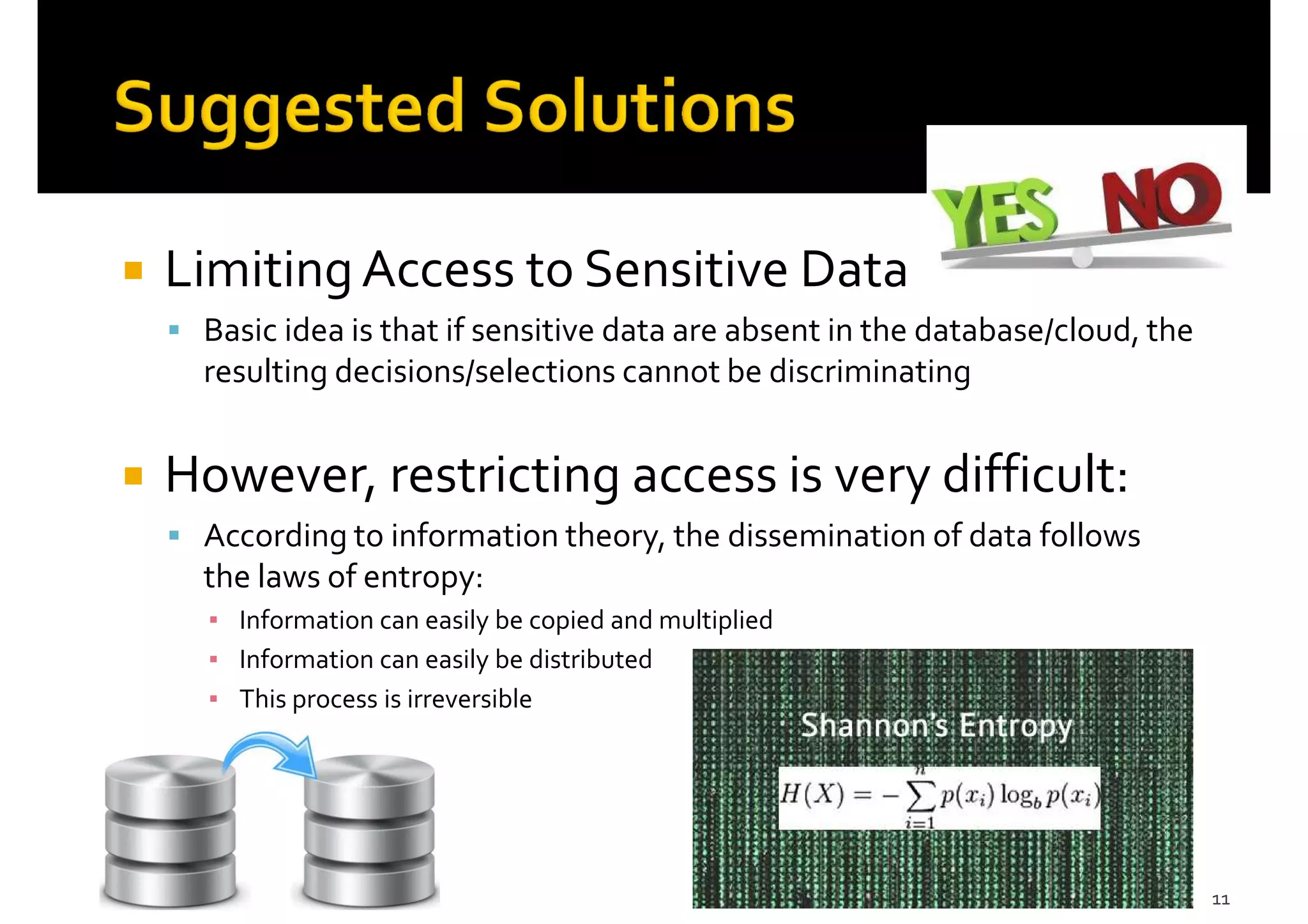
3) Potential solutions discussed, including privacy impact assessments, privacy by design, and new approaches focusing more on transparency and responsibility than restricting data access and use.