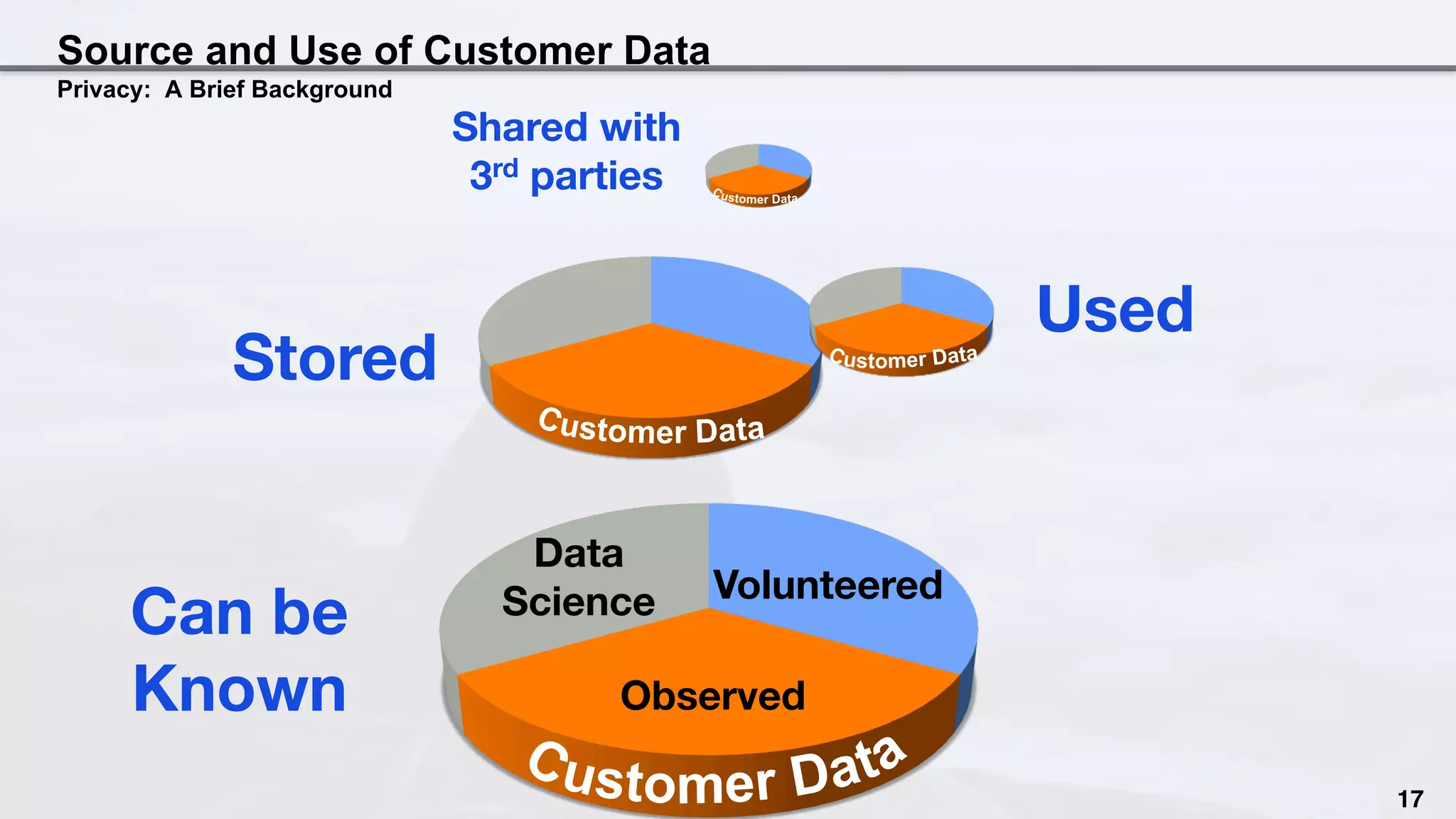
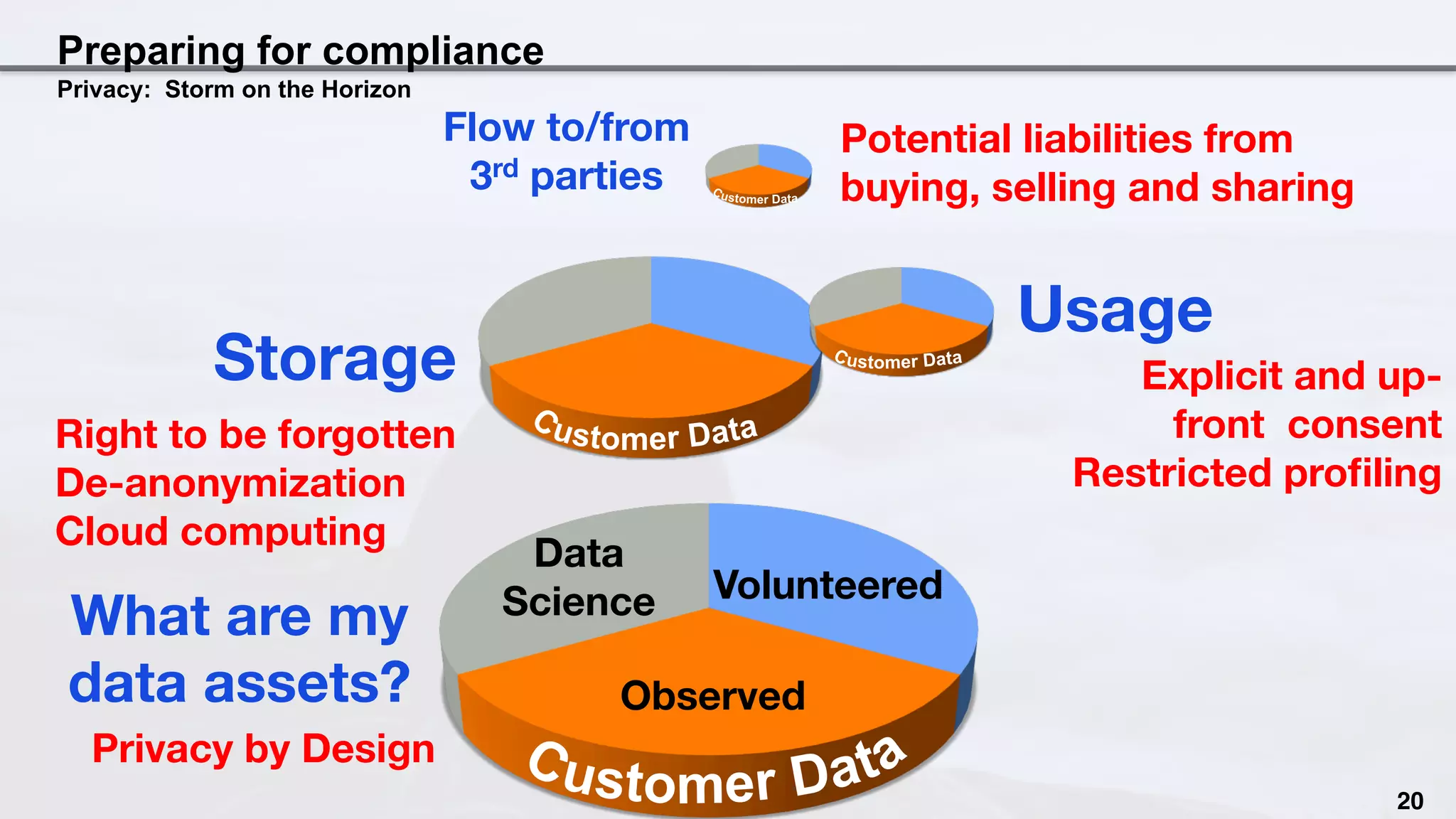
This document discusses the intersection of privacy considerations and data science, emphasizing the importance of understanding data usage and ensuring compliance with privacy legislation. It highlights case studies from companies like Target and Netflix, and outlines best practices for implementing privacy by design in data management. The author calls for organizations to be proactive in auditing their data practices and engaging with privacy experts to mitigate potential privacy violations.