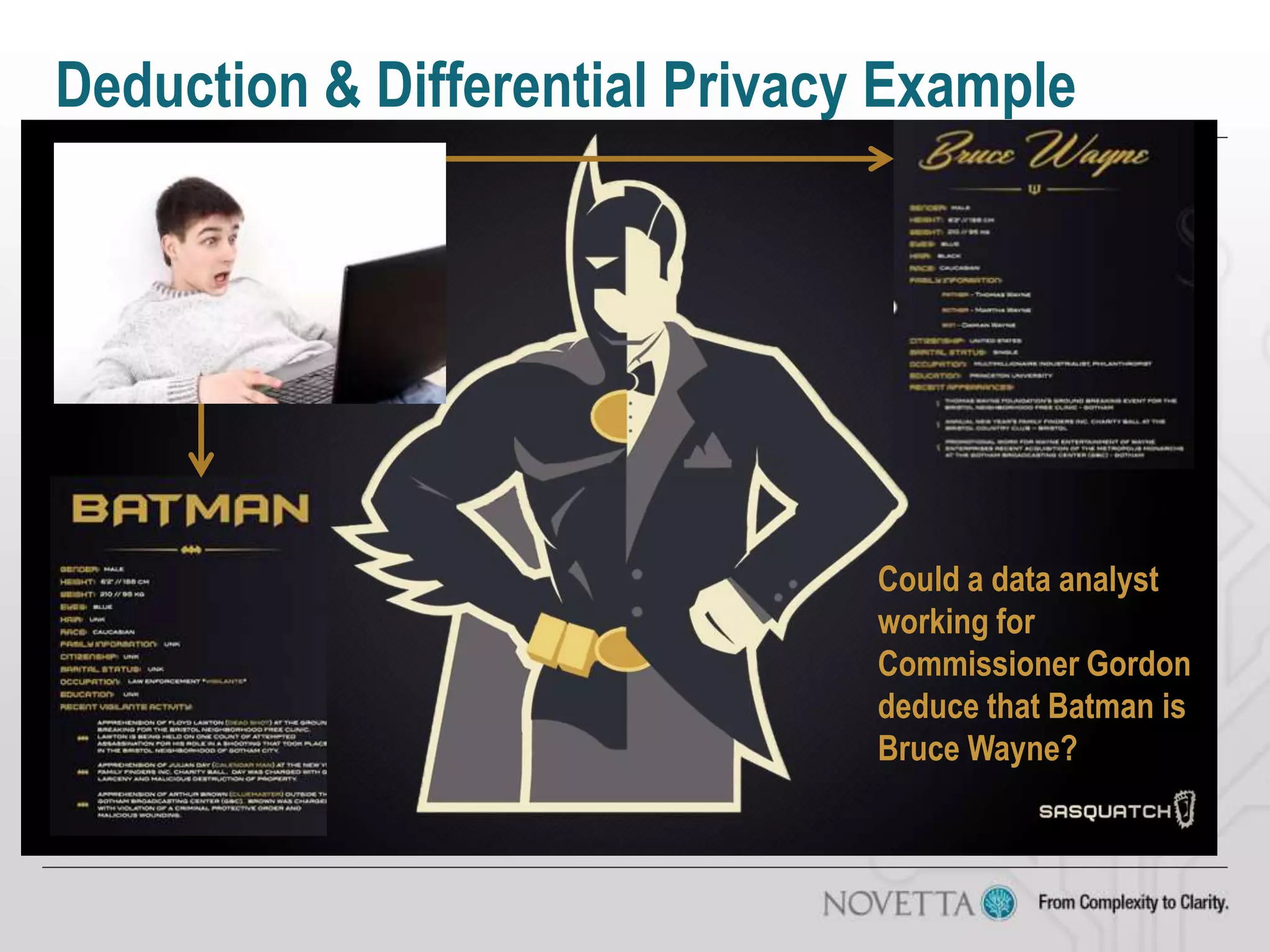
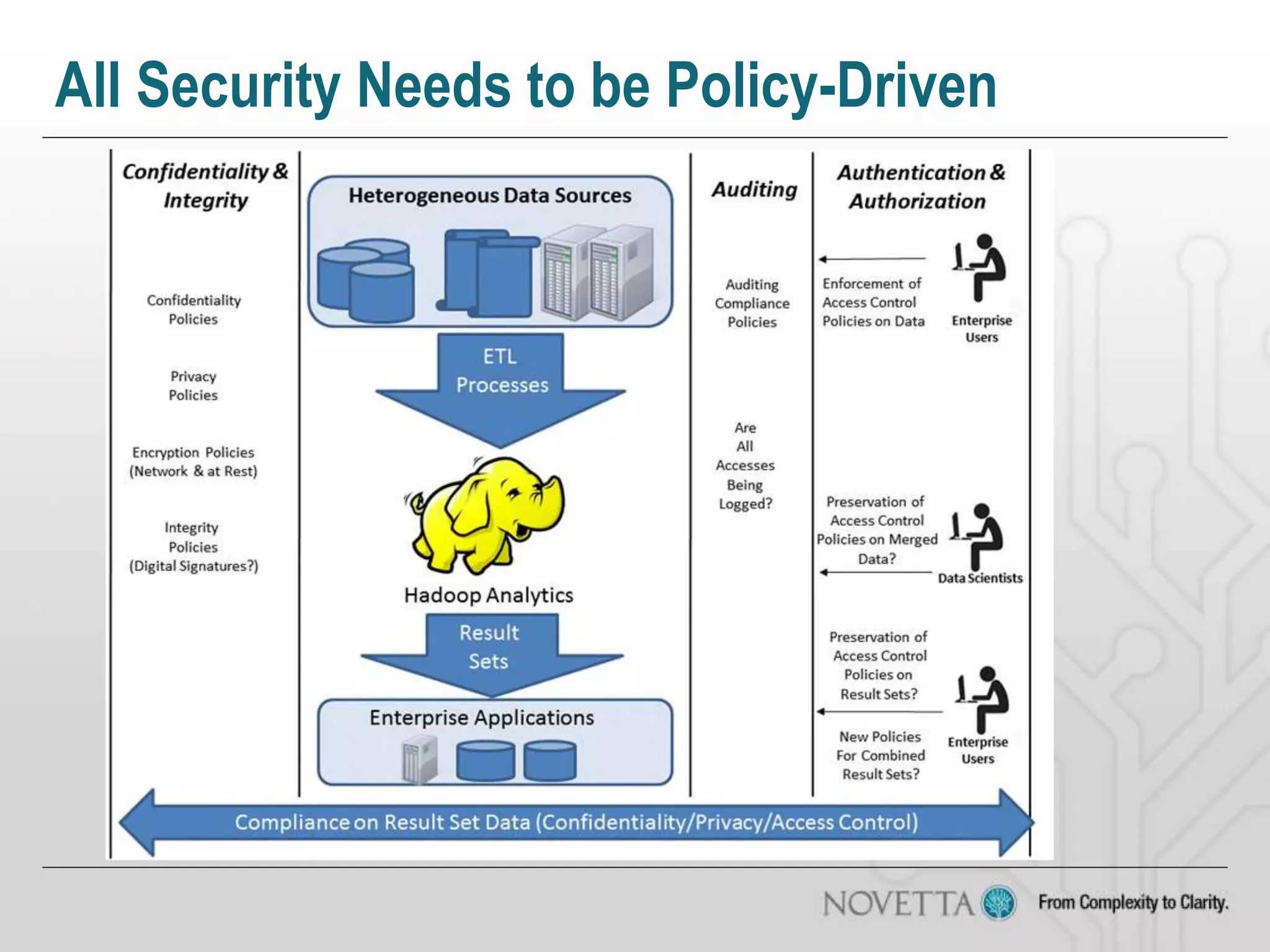
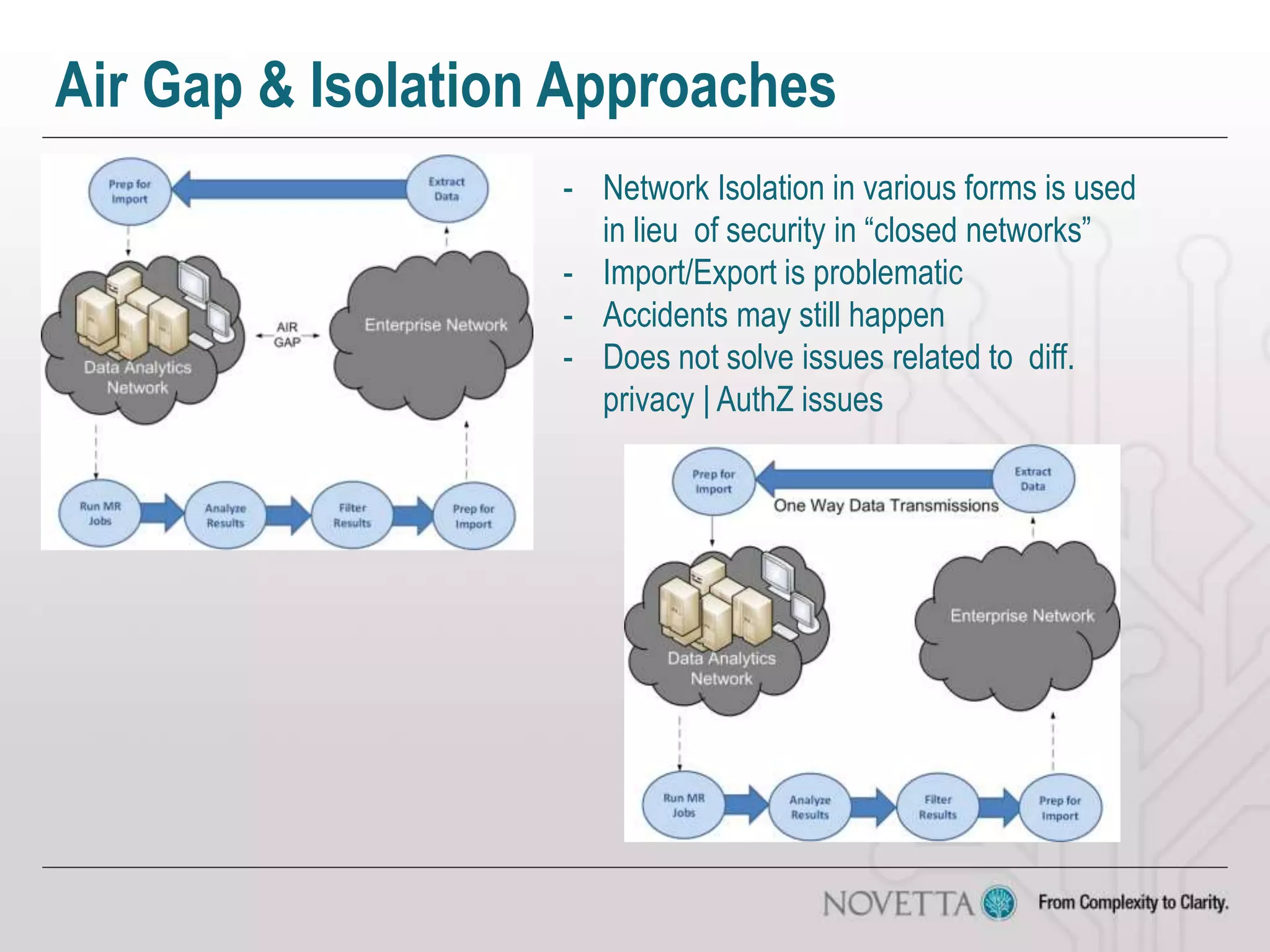
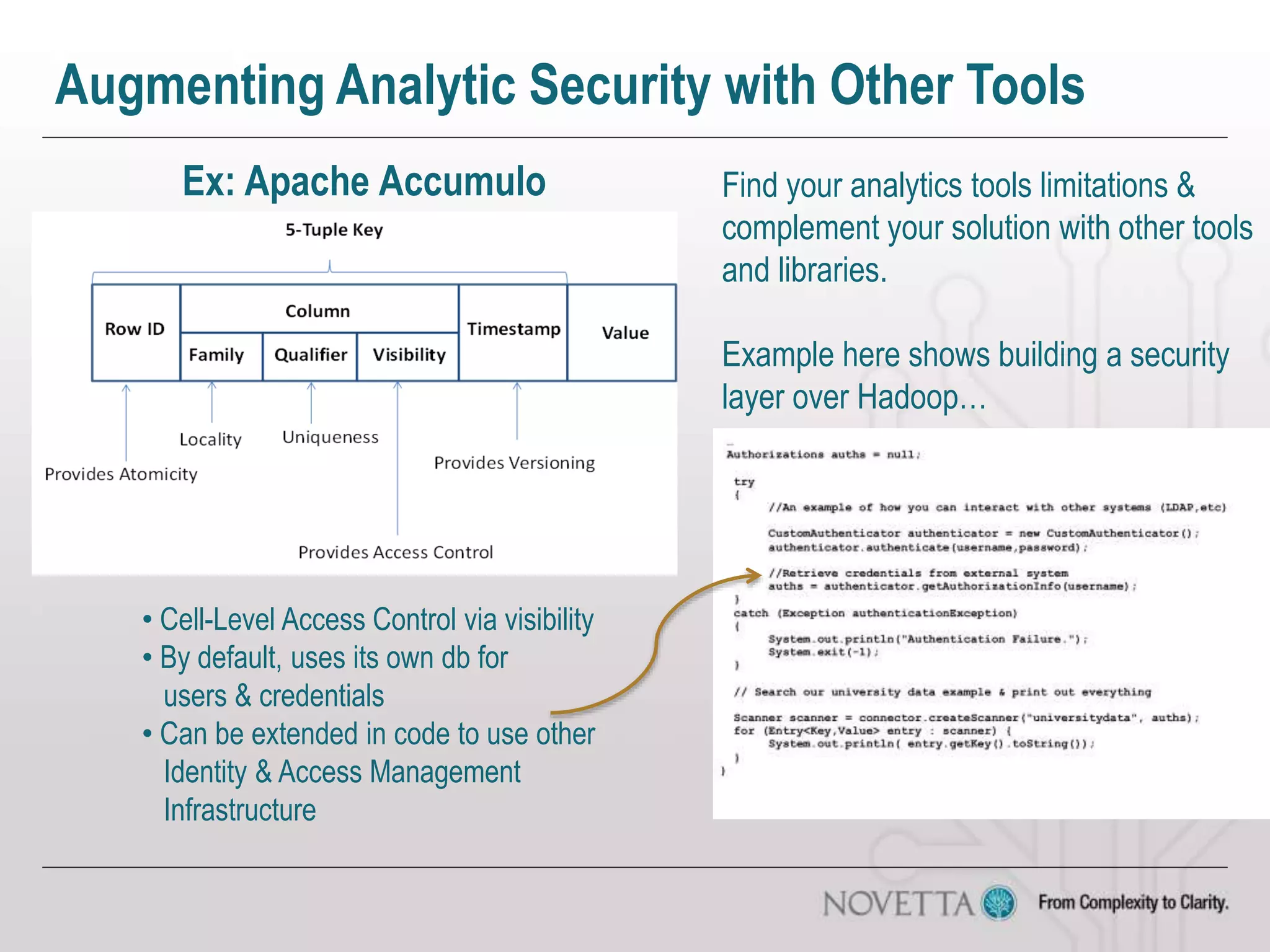
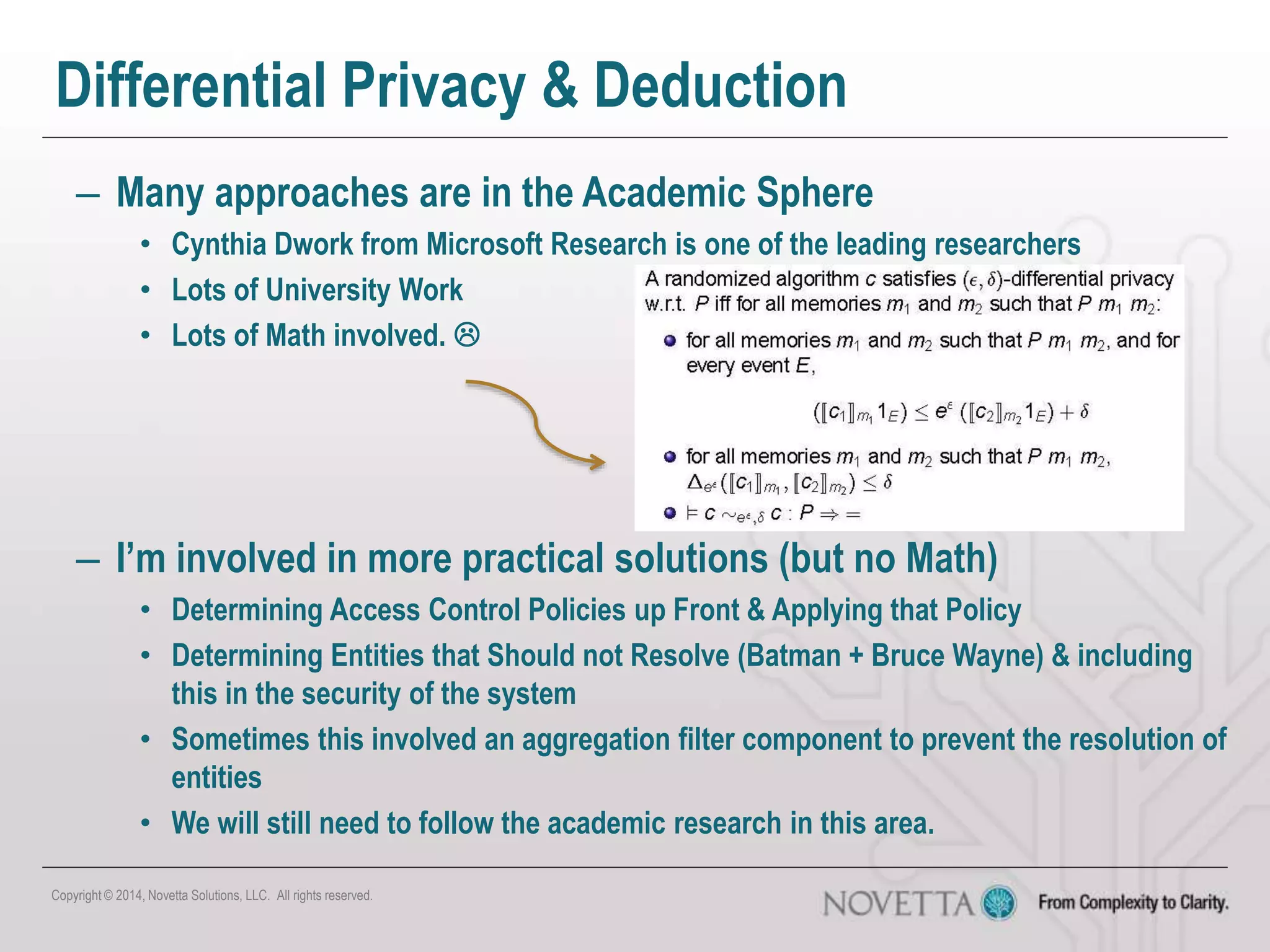
The document discusses the challenges of securing big data, emphasizing issues such as regulatory compliance, data mismanagement, and privacy concerns. It highlights the complexities of distributed security and the risks associated with combining different data sources, which can lead to unintended disclosures. The author provides insights on the need for policy-driven security approaches and the limitations of existing analytic tools.