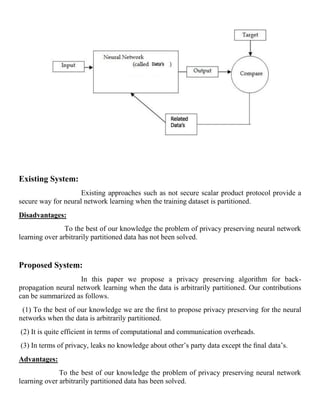
This document presents a privacy-preserving algorithm for back-propagation neural network learning with data arbitrarily partitioned between two parties, addressing privacy concerns when sharing training datasets. The proposed method ensures no knowledge is leaked about one party's data, besides the final learned outcomes, while achieving efficiency in computation and communication. This work marks a significant advancement in secure neural network training, especially with regards to data privacy.