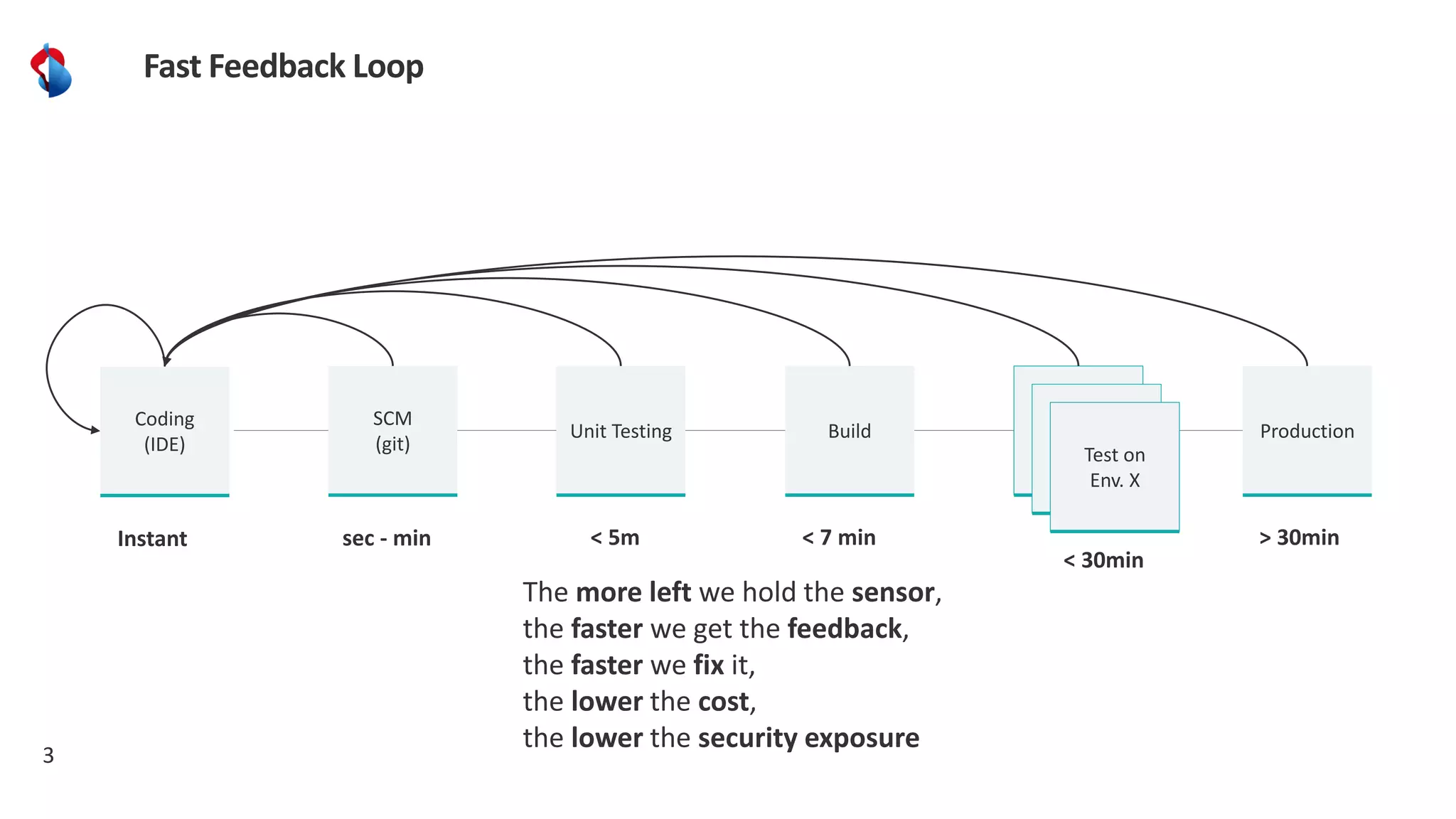
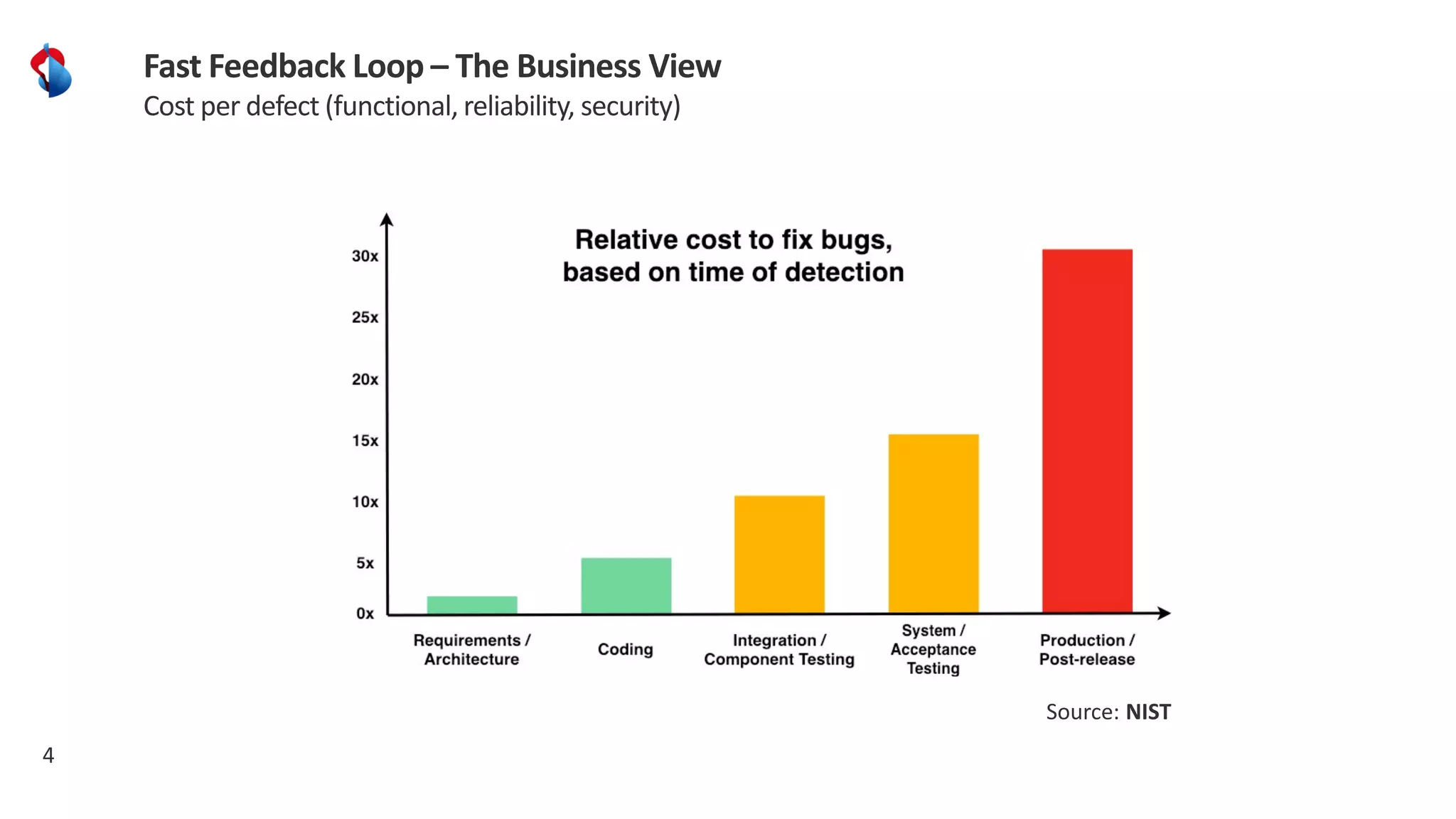
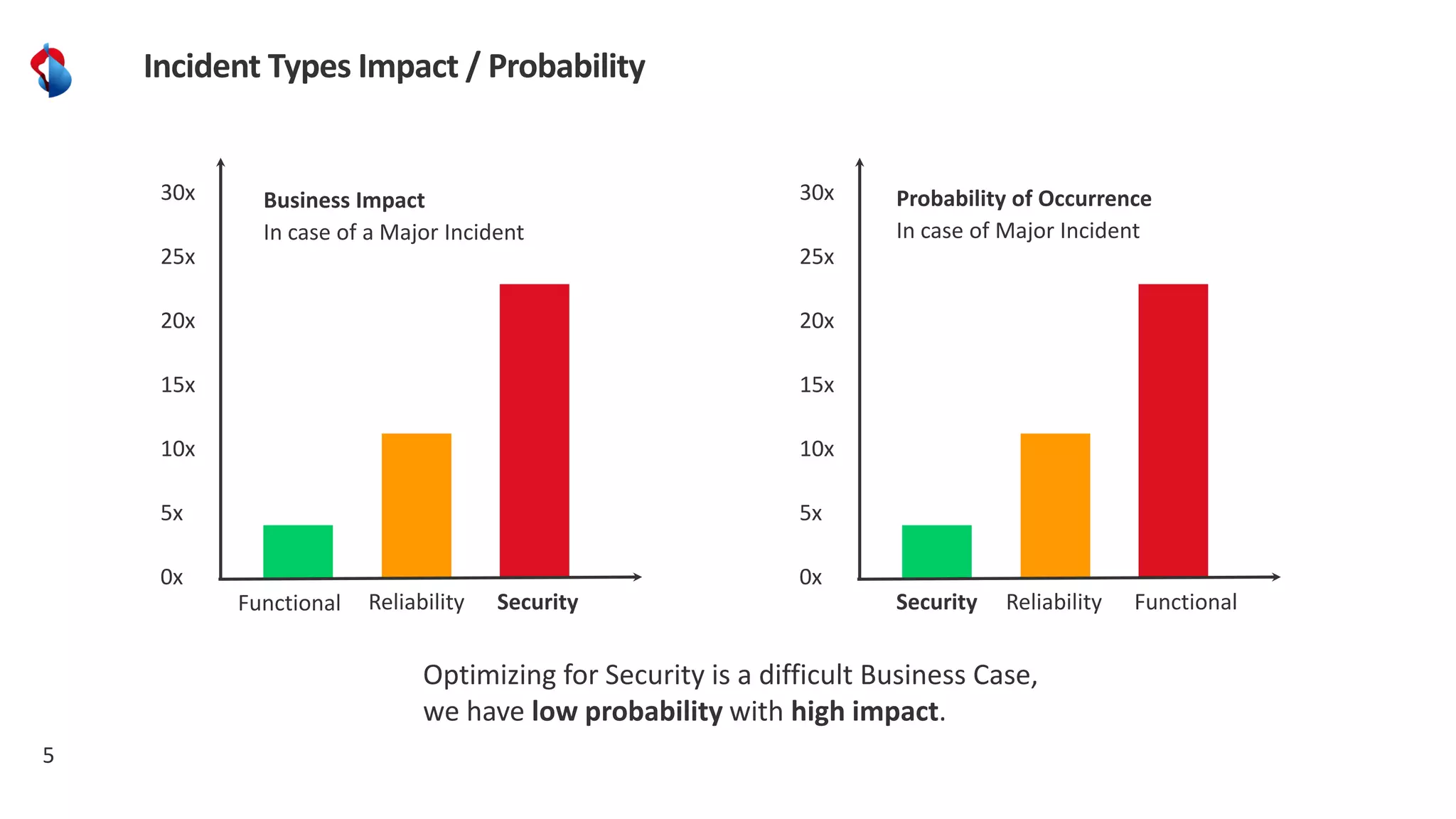
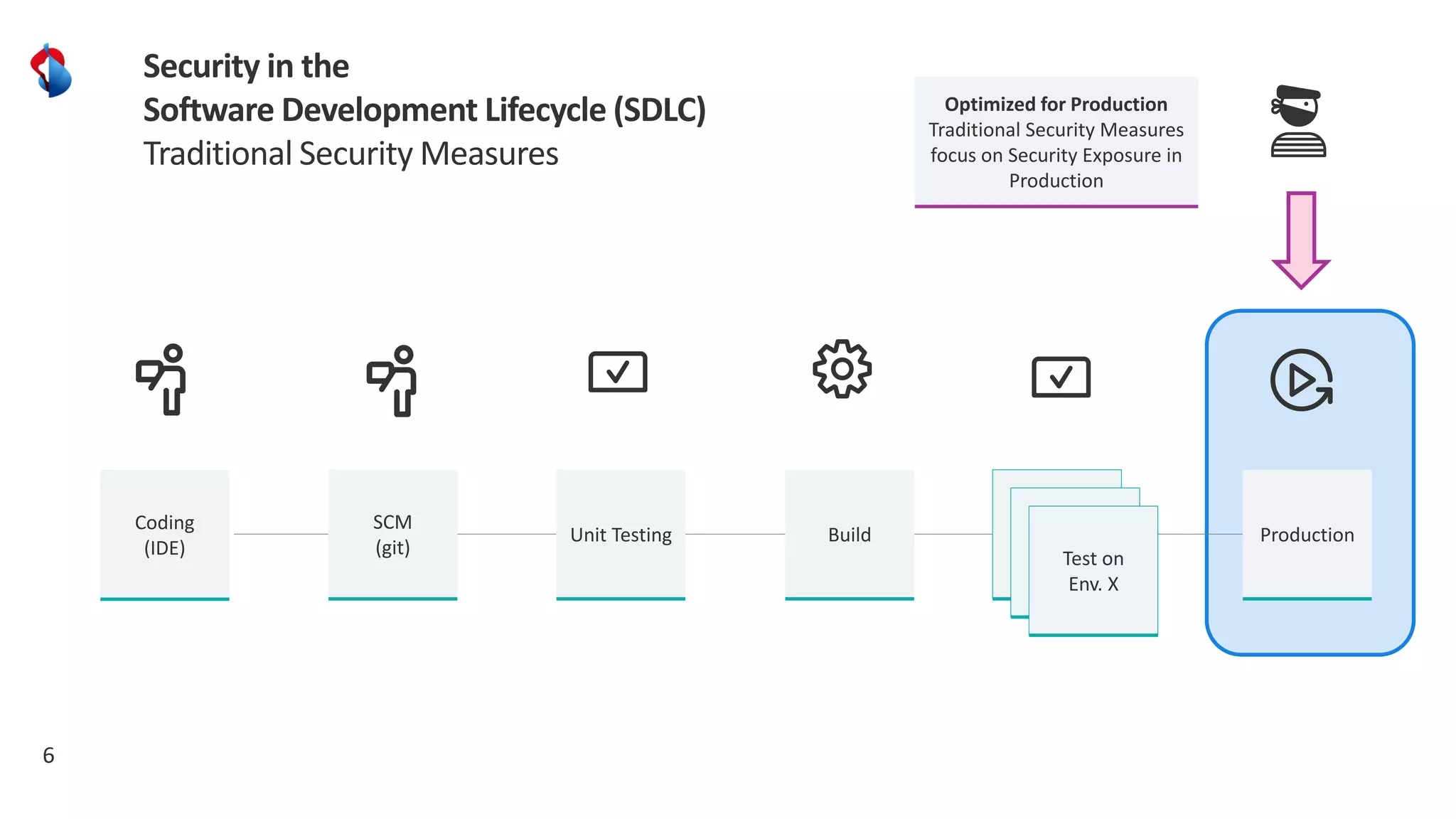
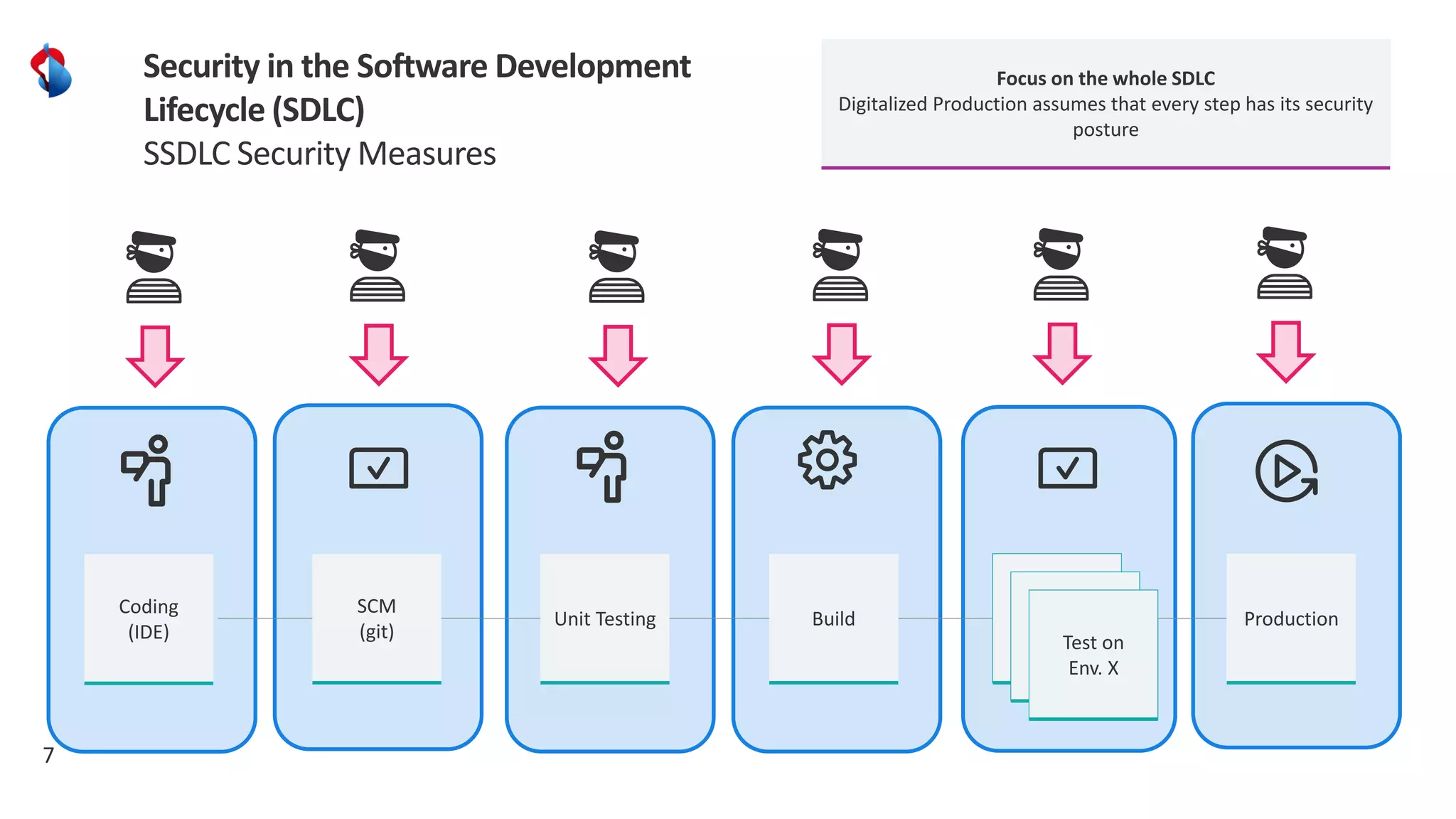
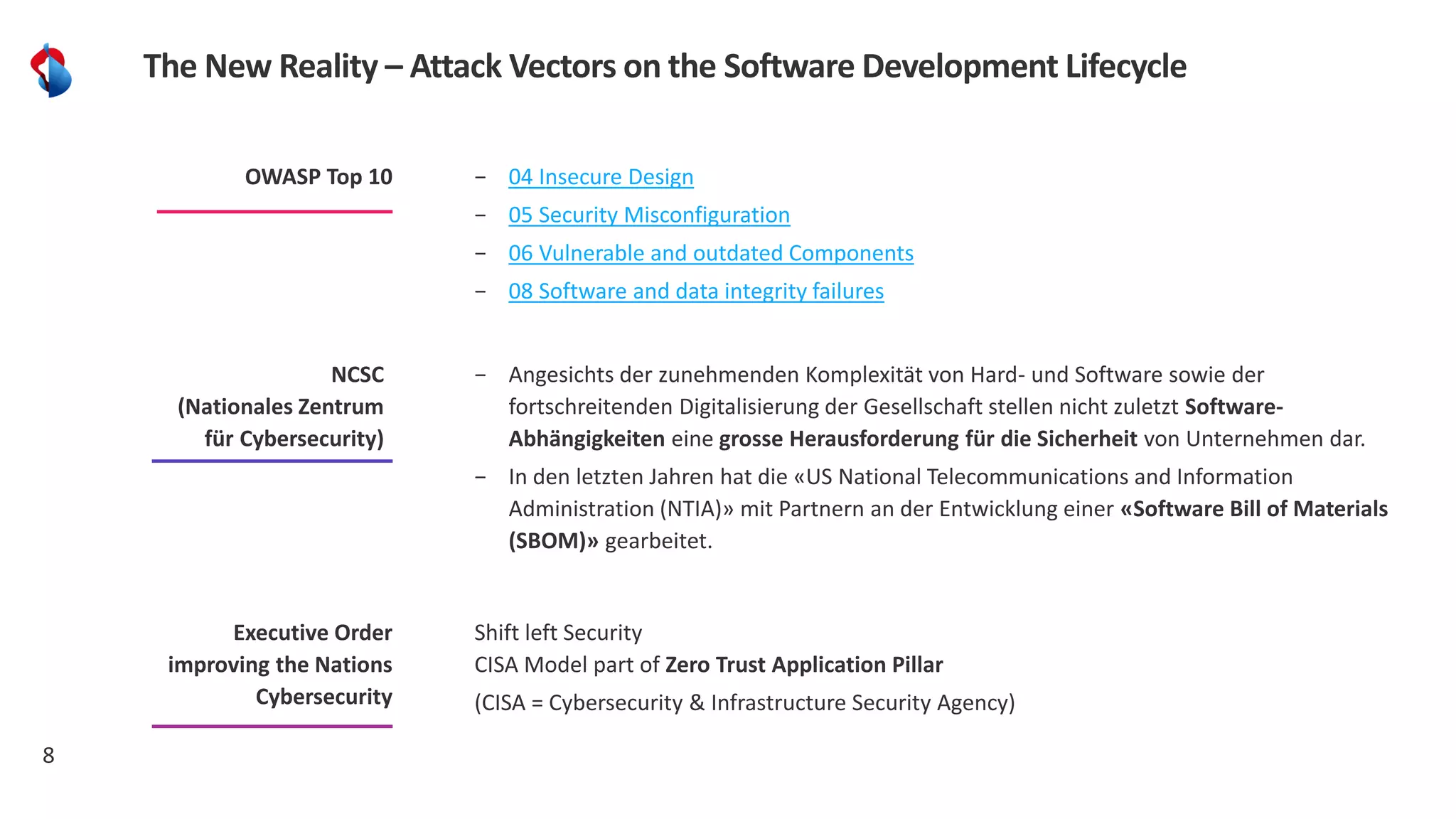
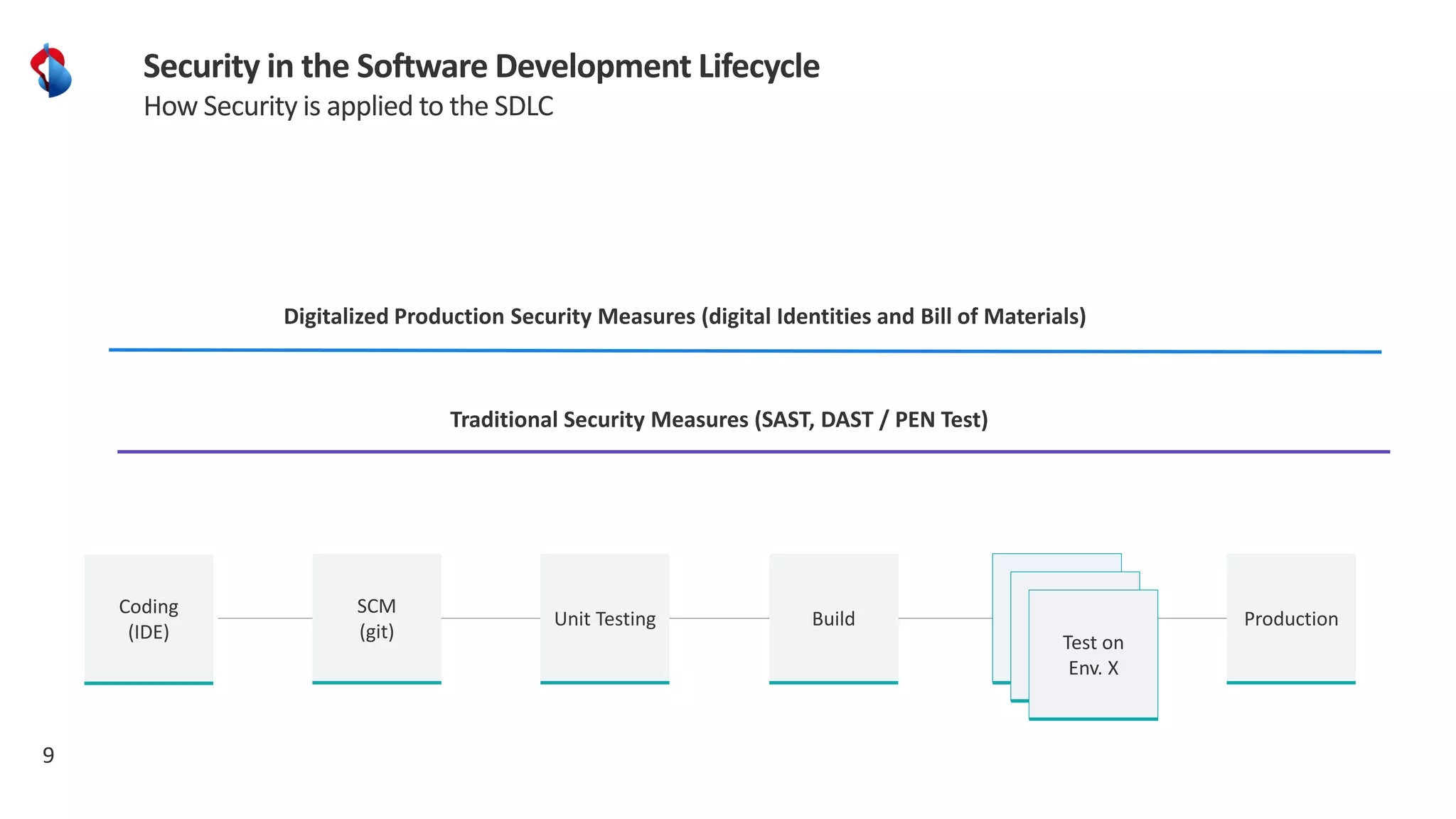
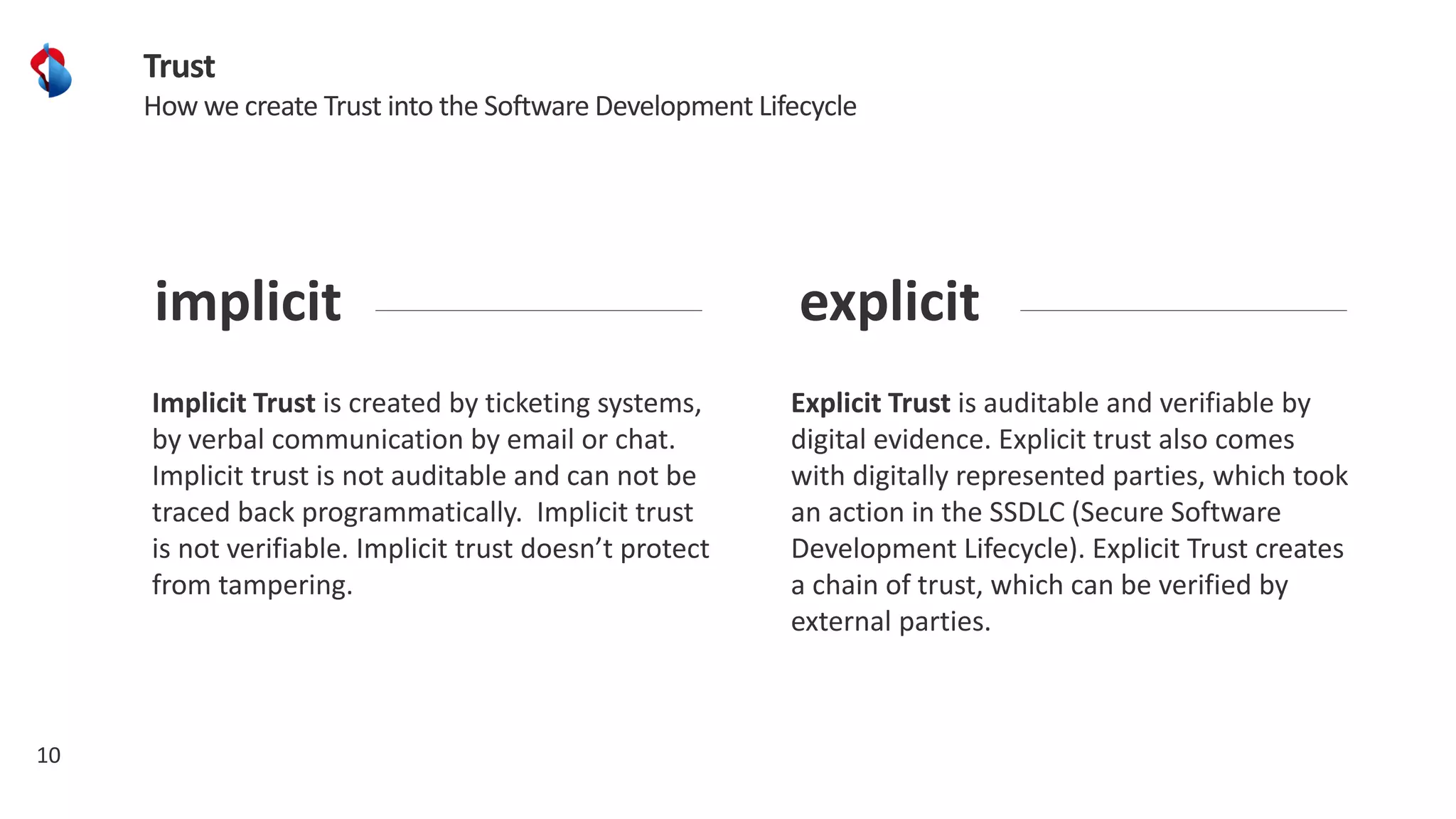
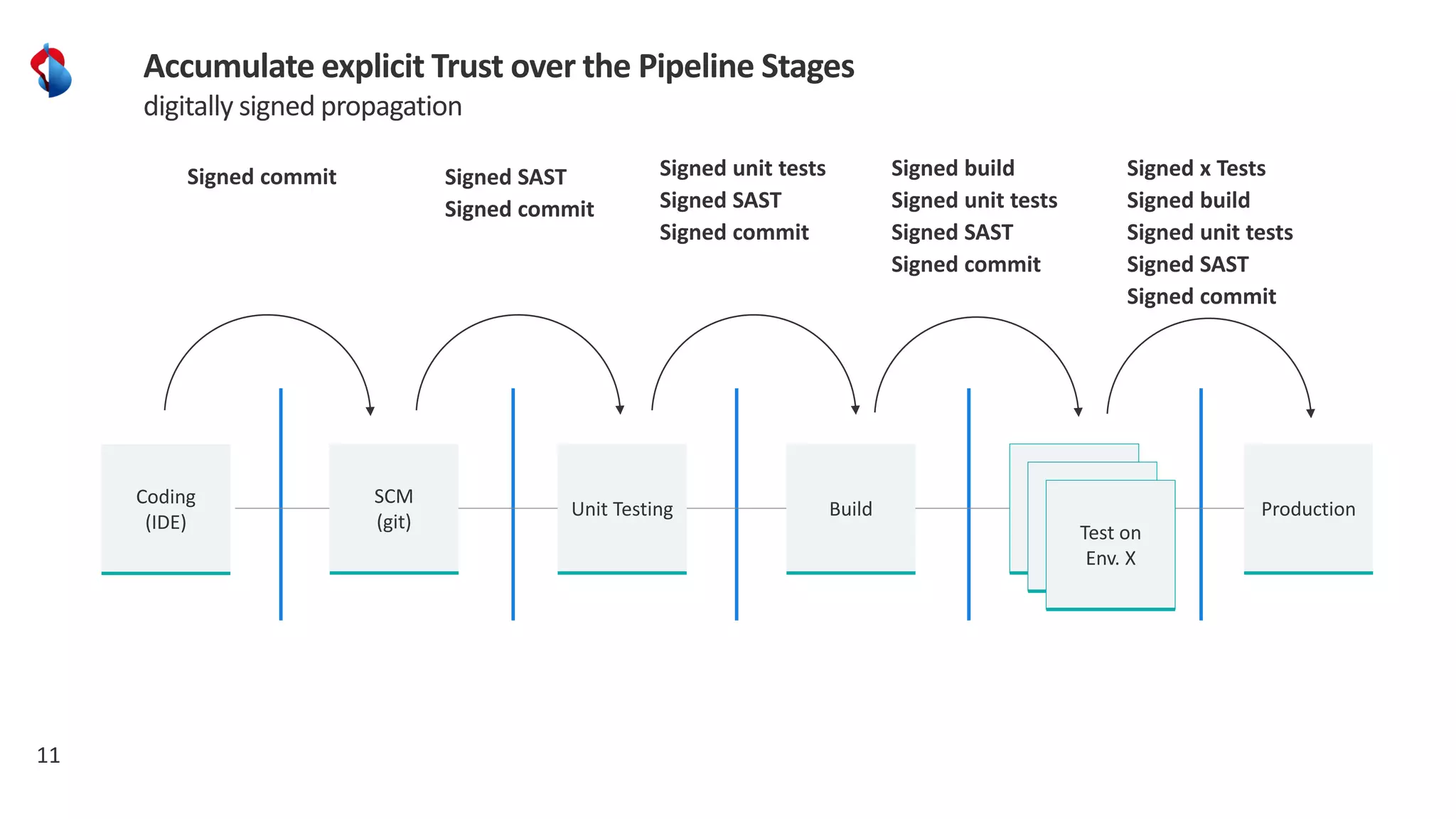
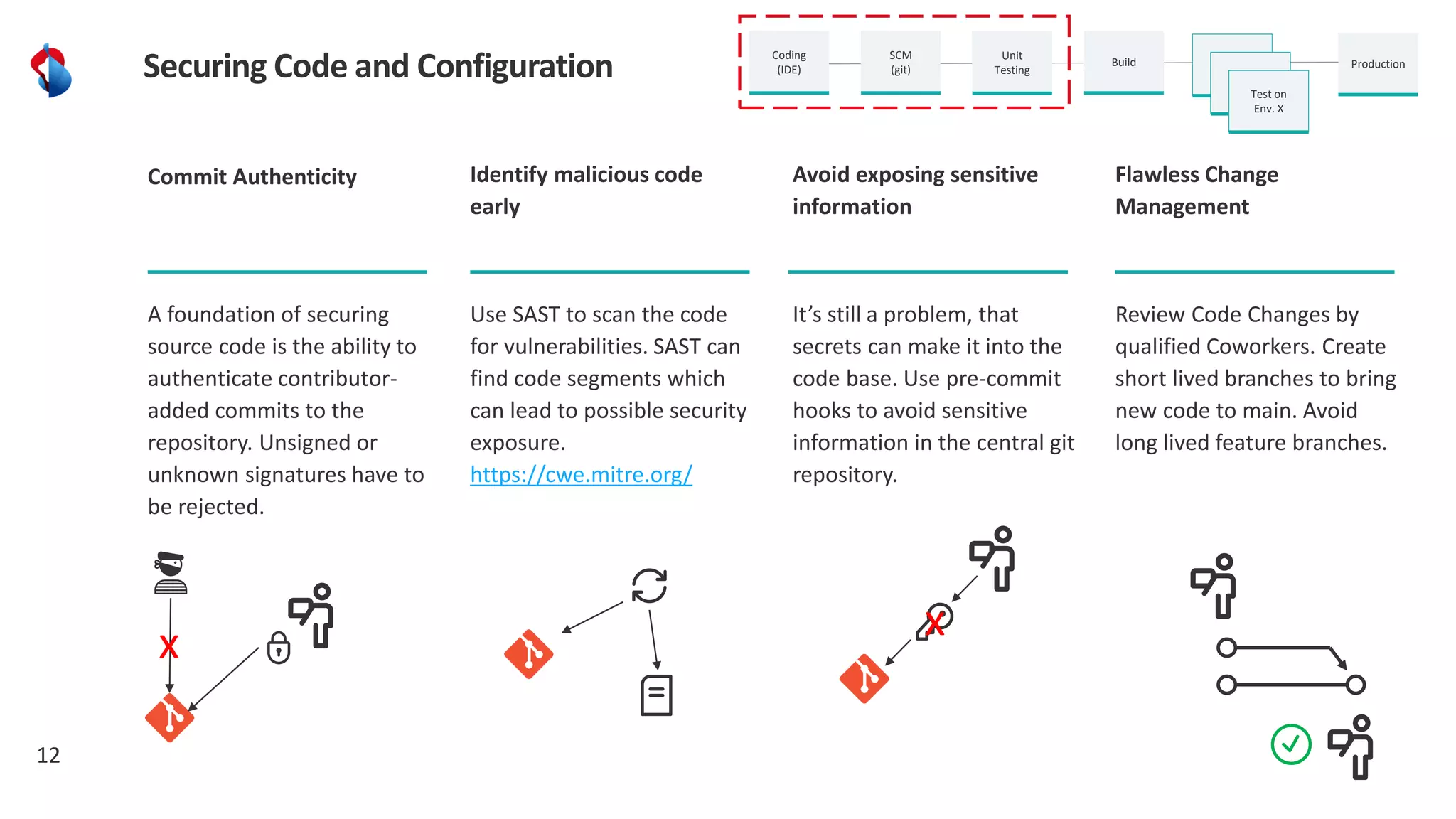
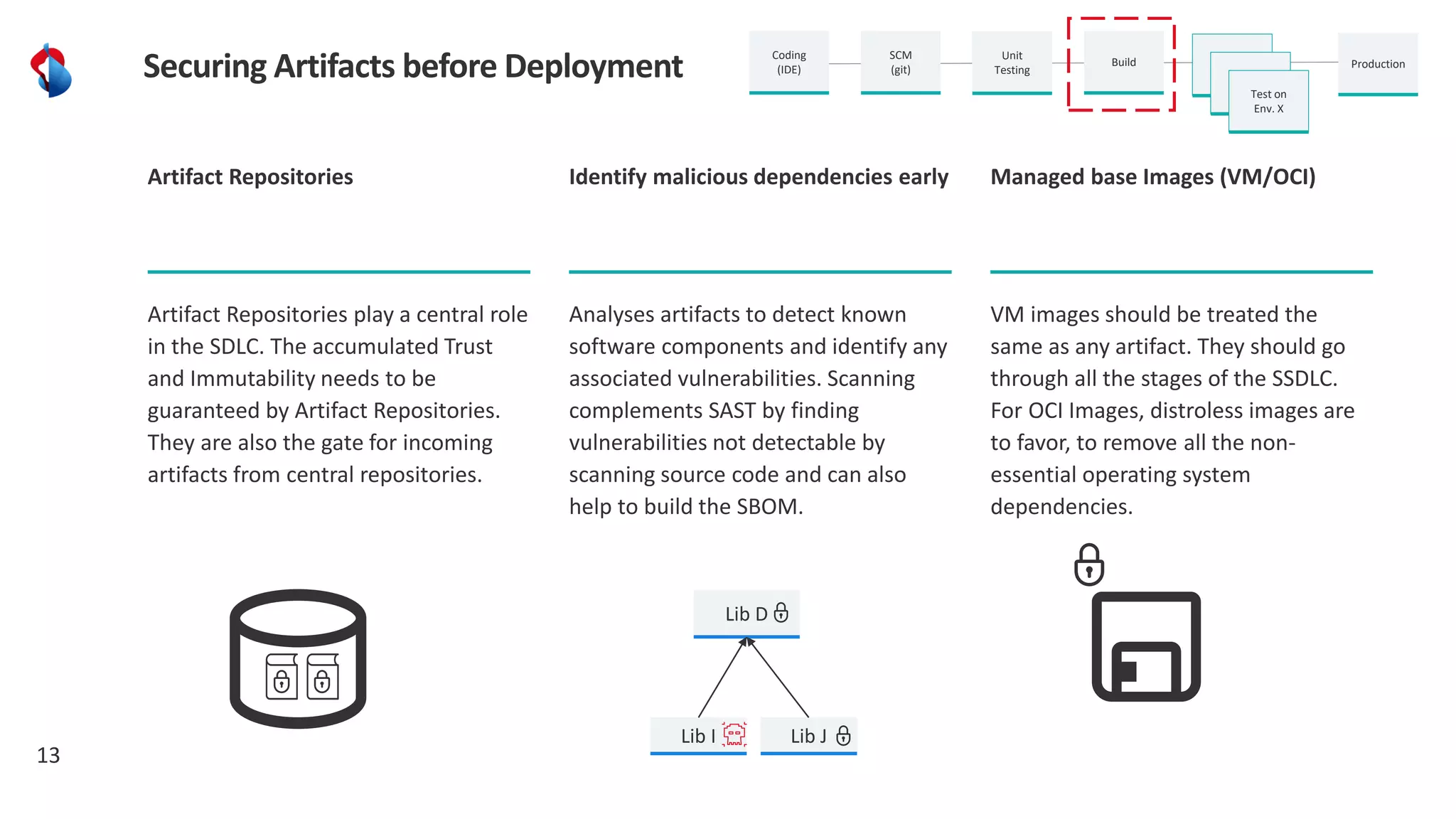
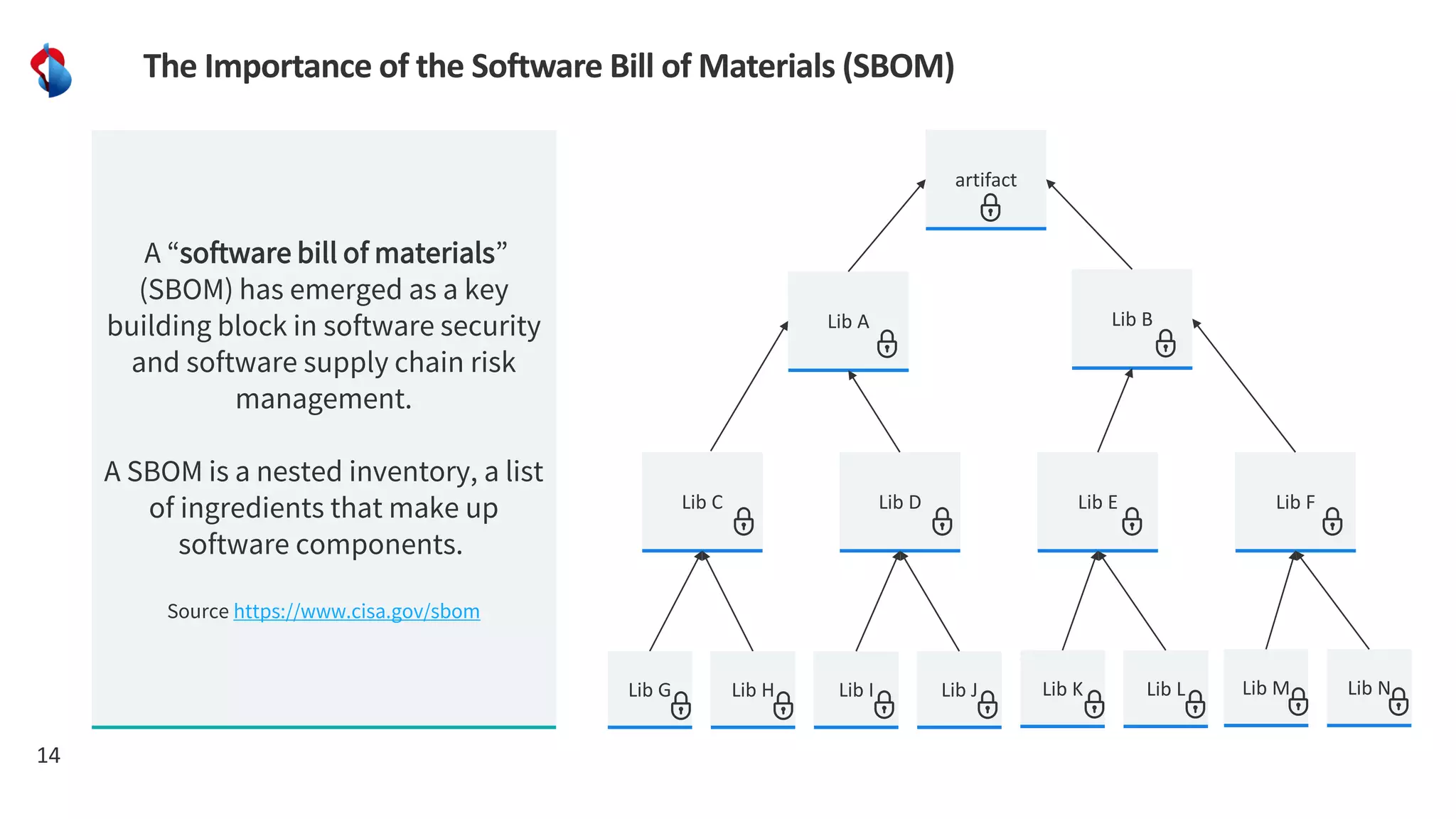
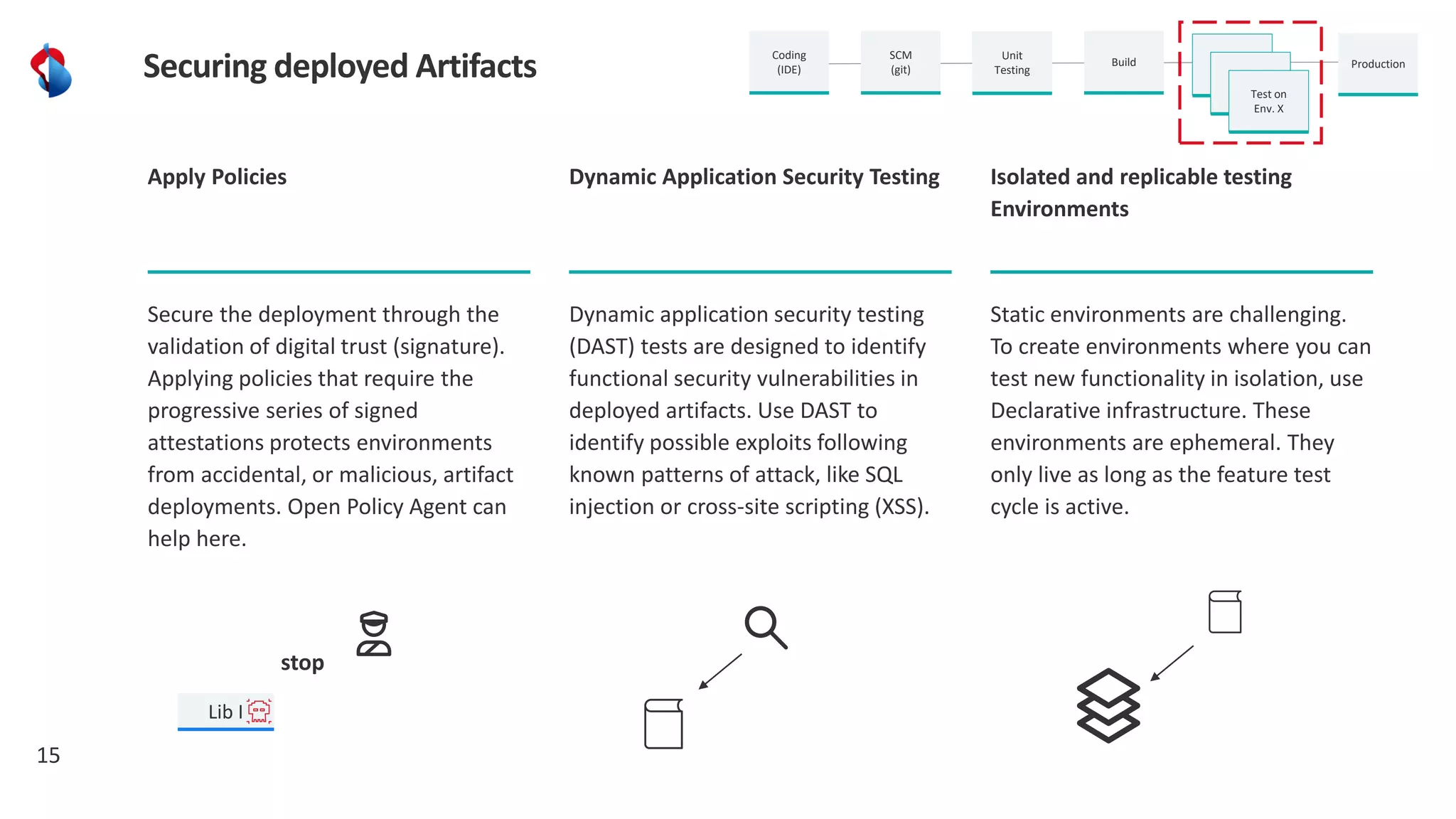
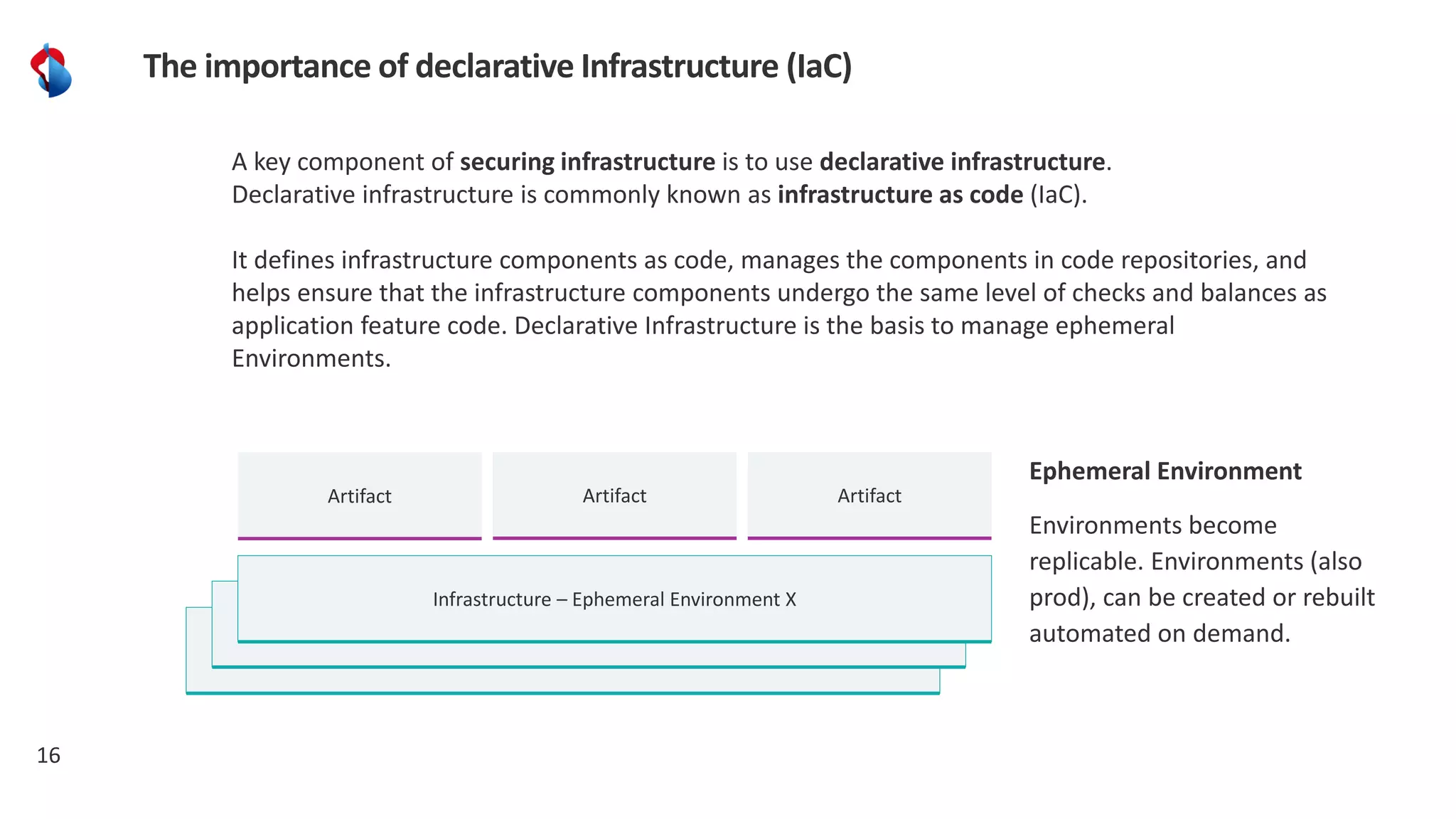
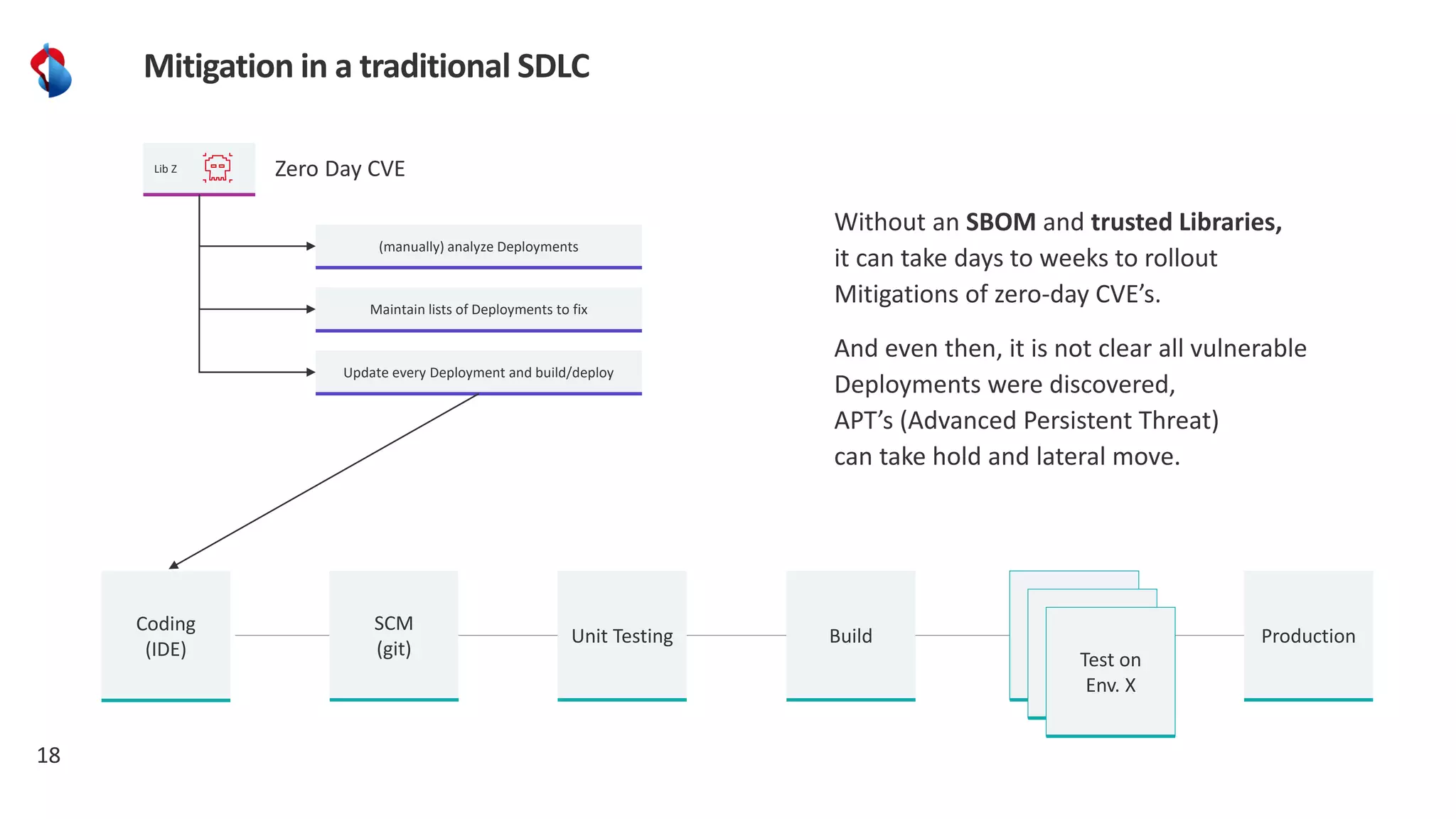
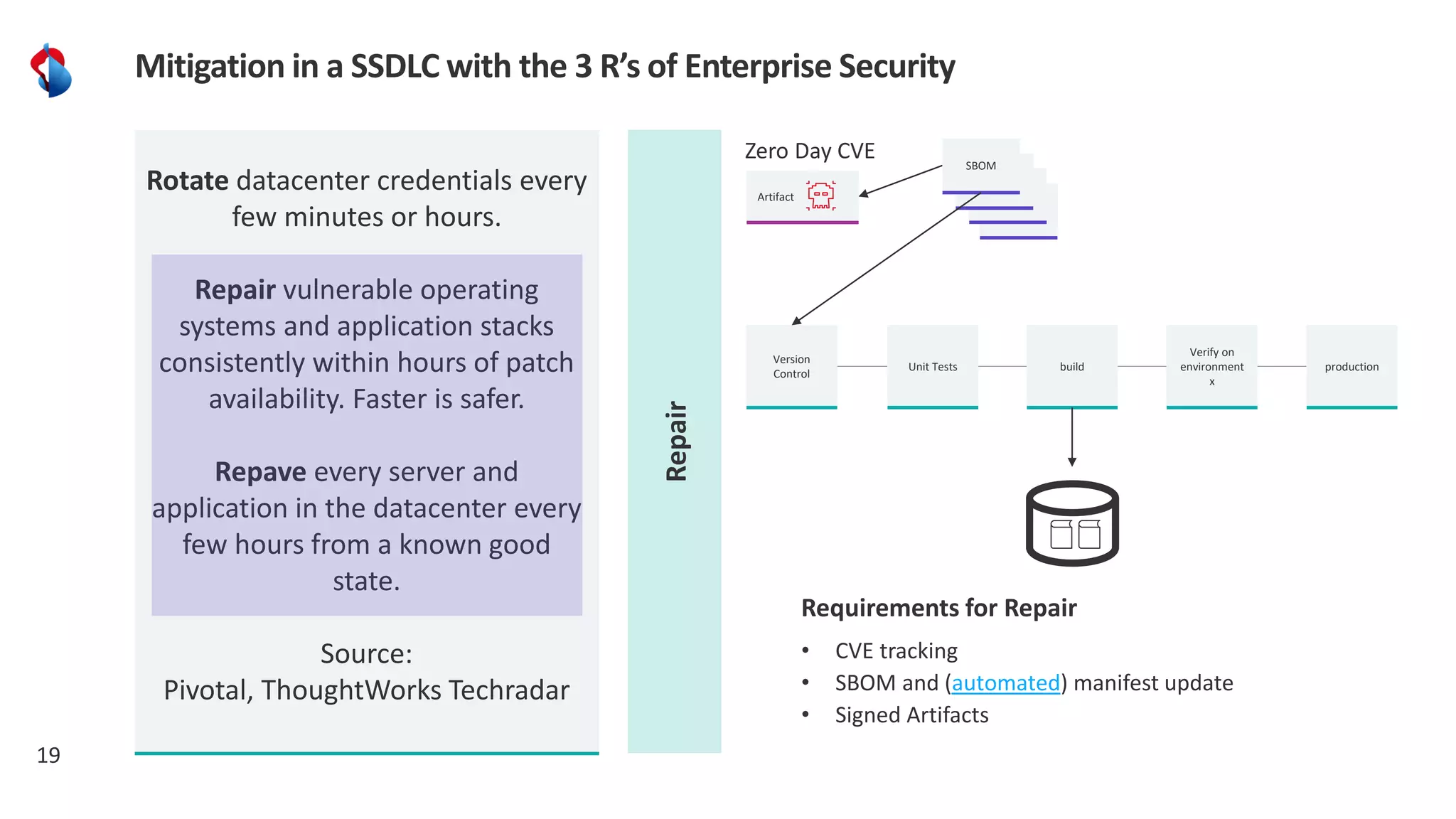
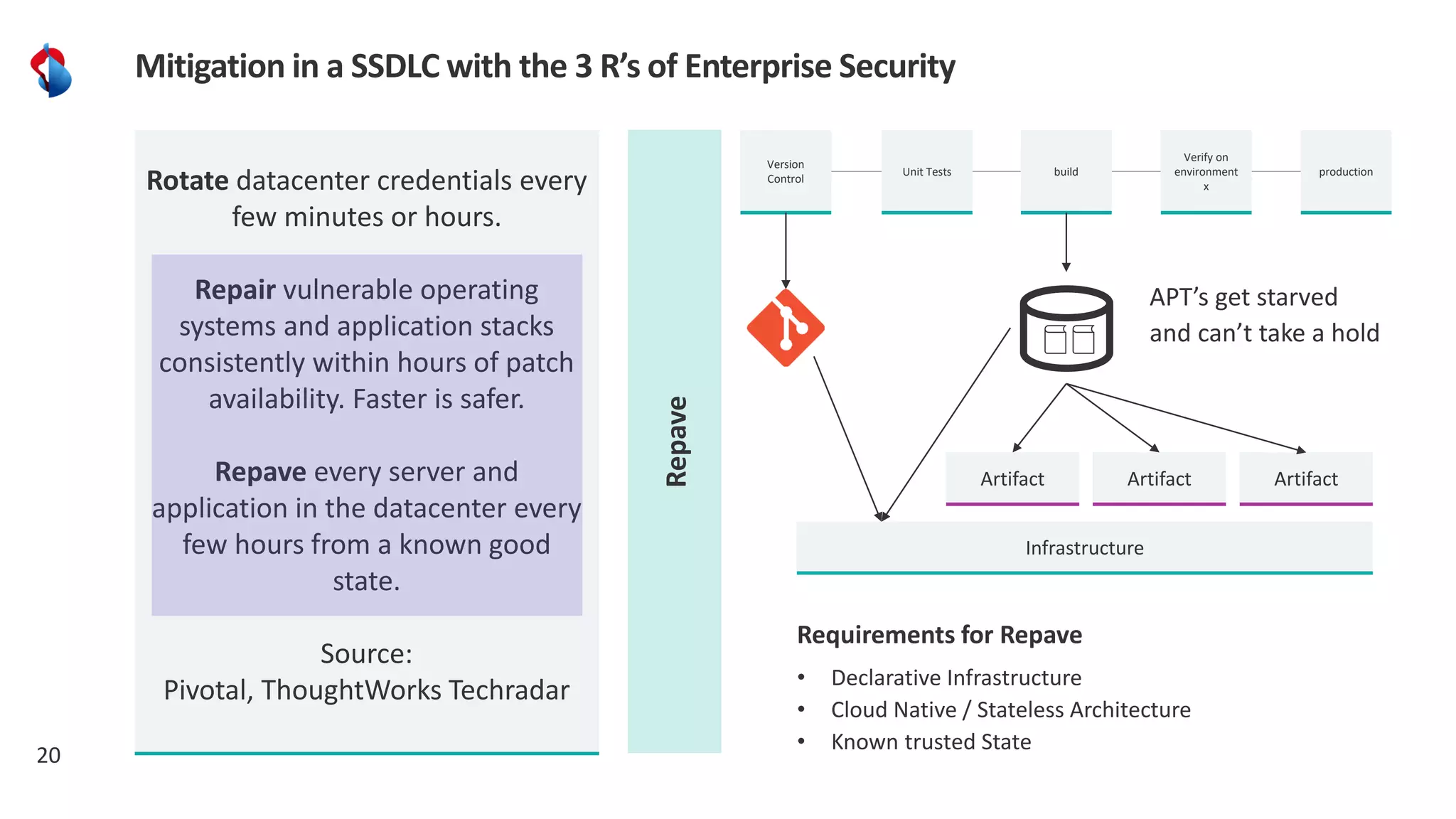
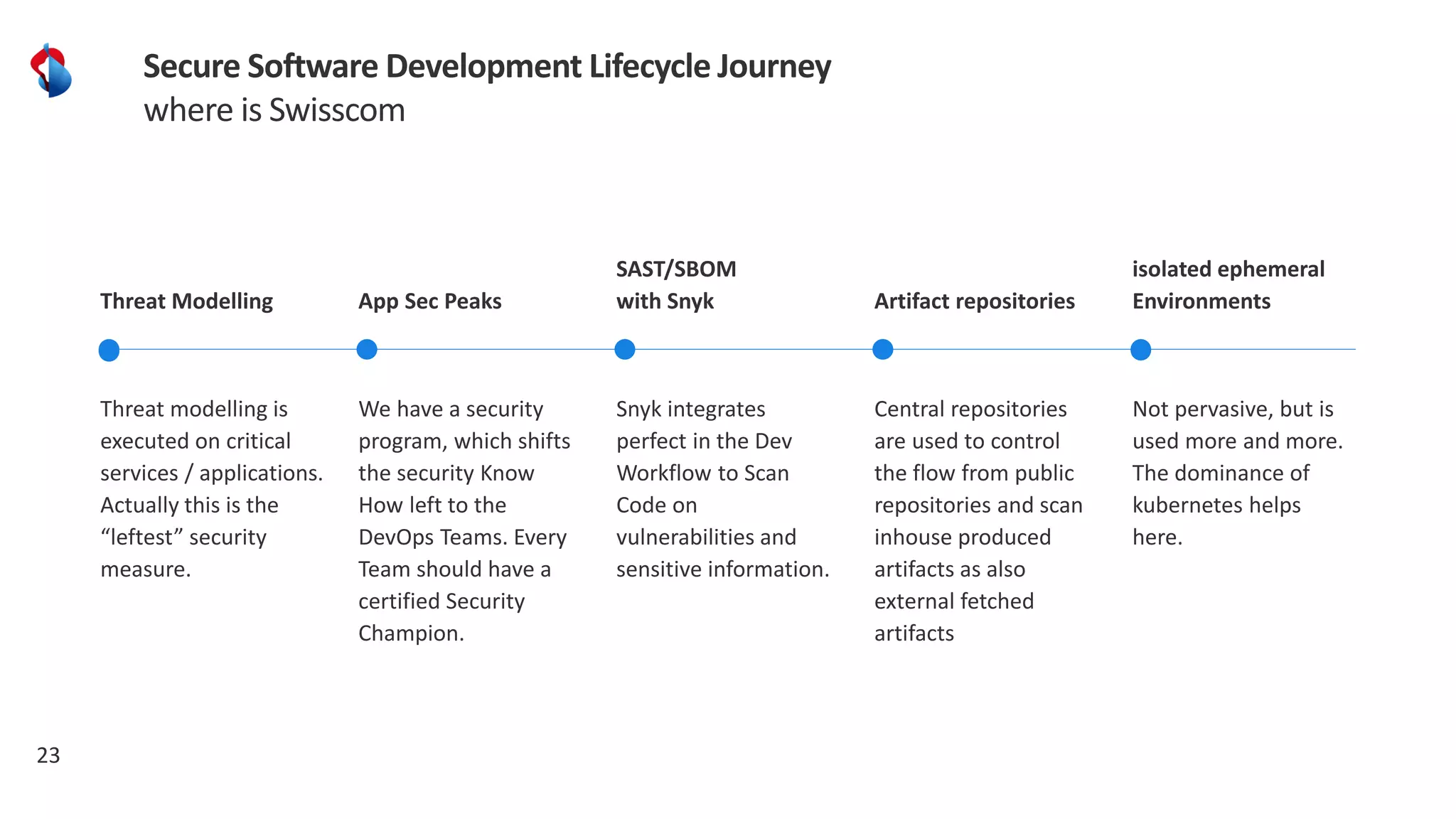
The document discusses the importance of integrating security into the software development lifecycle (SDLC) through a 'shift left' approach, emphasizing fast feedback loops and the necessity of explicit trust in development processes. Key strategies include implementing tools such as automated security testing and maintaining a software bill of materials (SBOM) to manage vulnerabilities. Furthermore, it highlights the need for auditable and verifiable security measures throughout the SDLC in order to establish a robust security posture against potential threats.