The document details six dangerous types of cyberattacks: Cryptolocker, Spear Phishing, Timthumb Attacks, Manipulating Beef Toolkit, SEO Poisoning, and Phishing plus Social Attacks. Each attack employs different strategies to compromise systems and steal or manipulate information, often targeting small businesses due to inadequate security measures. The increasing sophistication of these cyberattacks poses significant threats to individuals and organizations by exploiting vulnerabilities and manipulating online behavior.










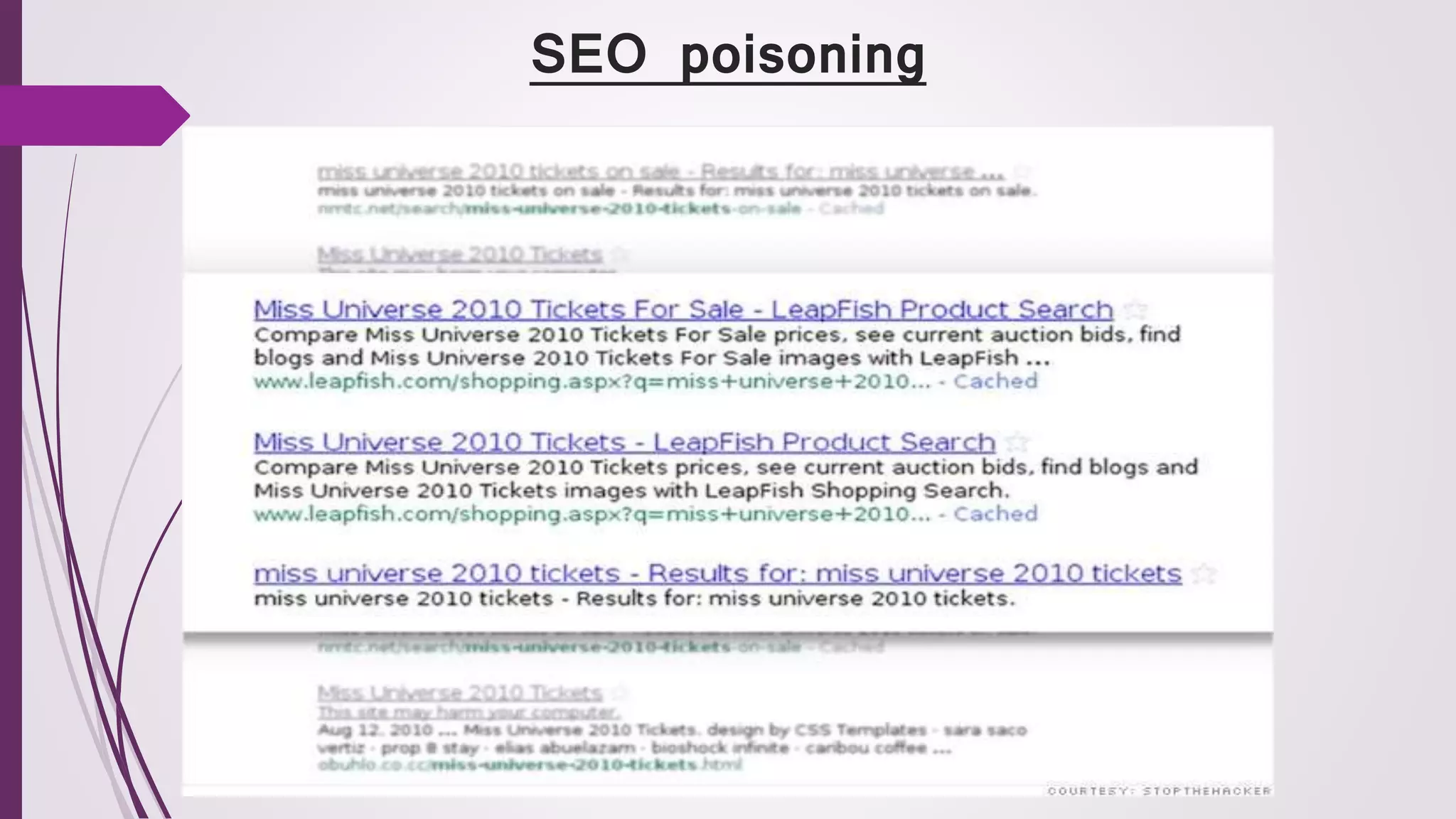
![ SEO begins with hackers isolating keywords that are generating buzz
on Google and other search engines. They then create malicious URLs
about this topic so that search engines will index it alongside other
results.
Suppose thousands of people are Googling "Miley Cyrus." In this attack,
cybercriminals would create dummy websites about her that are loaded
with malware.
If you're searching for Miley and unwittingly click on one of these links,
the malware could be used to hack into your computer or install
spyware.
There's another risk to small businesses. Because SEO poisoning floods
search results with bad links, it could push legitimate results down.
Suppose you sell Miley Cyrus T-shirts online and you're expecting an
uptick in business when "Miley Cyrus" is a hot search trend, But with so
many bad results that come up, people might not even get to [your] link.](https://image.slidesharecdn.com/cyberattacks-170226104302/75/Cyber-Attacks-14-2048.jpg)

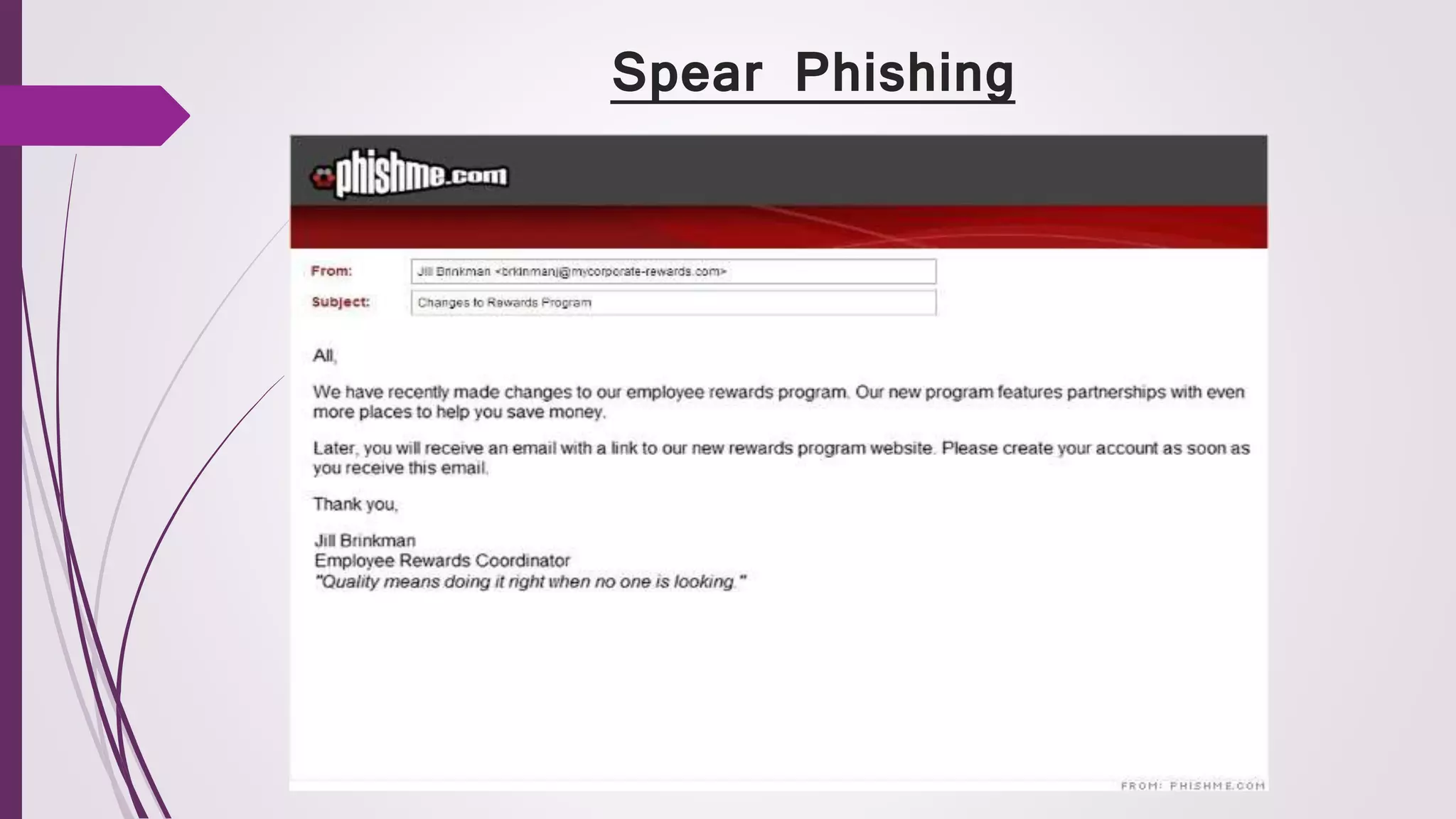
![ Hackers have upped the ante with this targeted attack, using
personal phone calls in addition to traditional emails.
It begins as a regular phishing email to people with financial
roles, such as an accountant or a CFO.
The scary part is that even if you think the email is suspicious
and don't click on it, you haven't escaped the attack.
The criminals pretend to be a vendor of the [targeted] company
and will convince you that you have a payment due on an old
invoice. The victim gets a follow-up email with an attachment
disguised as the invoice.
If you click on the attachment, it will install malware on your
computer. Then the hackers can get information such like the
login and password for bank accounts and steal funds.](https://image.slidesharecdn.com/cyberattacks-170226104302/75/Cyber-Attacks-16-2048.jpg)
