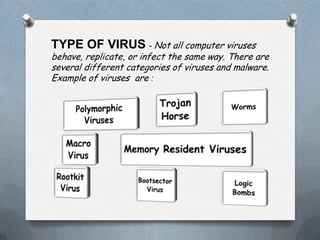
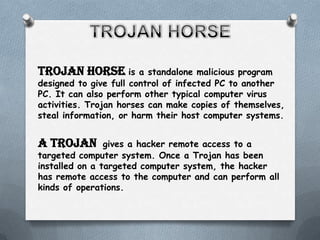
A Trojan horse is a malicious program that gives full control of an infected computer to another system. It can copy itself and harm the host computer. A salami attack involves committing many small crimes, like stealing small amounts from multiple bank accounts, that together result in a larger crime that is hard to detect. Computer viruses can copy themselves and infect systems without permission, affecting system performance and installing programs incorrectly. Anti-virus software is needed to protect against computer viruses.