This document presents a scheme for interactive communication between a base station and mobile stations to efficiently allocate resources. It models the problem and analyzes an approach where the base station broadcasts a threshold and mobile stations reply to indicate if their value is above or below it. Through multiple rounds of interaction, the base station can determine the mobile station with the maximum value with significantly less overhead than non-interactive schemes. Simulation results show the proposed approach of encoding the threshold or number of users at each round performs better than baselines. Extensions consider incorporating distortion and trading off communication costs versus time.



![Results
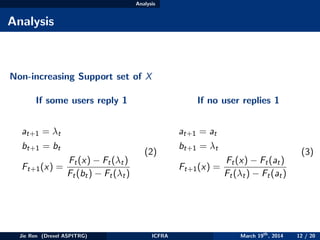
Some Extensions
Interaction with Distortion
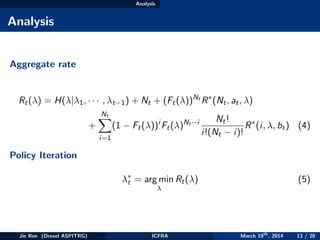
E[max{X1, . . . , XNt } − Xi ] ≤ D (8)
Bits Cost Vs. Time Cost
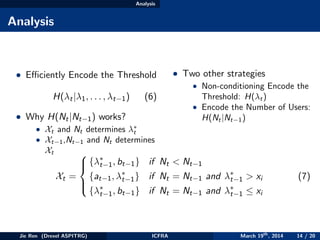
C = µR + (1 − µ)T (9)
Jie Ren (Drexel ASPITRG) ICFRA March 19th
, 2014 17 / 20](https://image.slidesharecdn.com/1d92aed3-2e97-44cb-911b-e6547b6ffbab-150309221930-conversion-gate01/85/presentation-17-320.jpg)