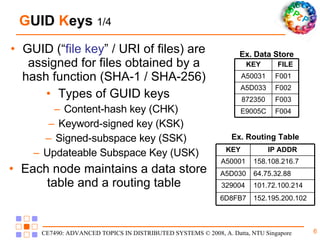
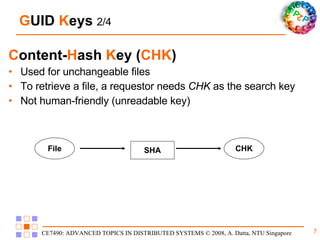
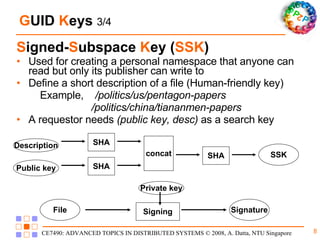
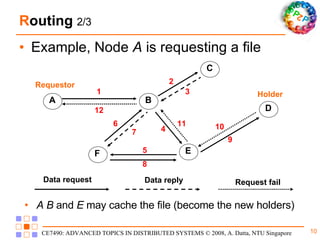
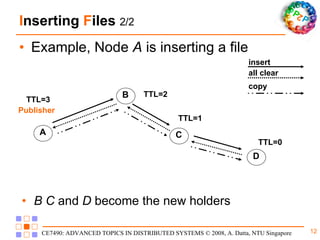
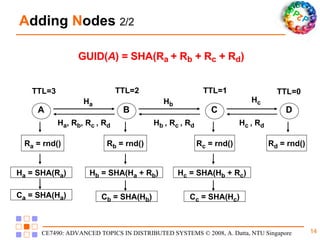
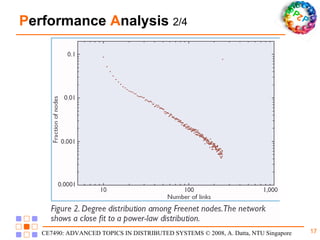
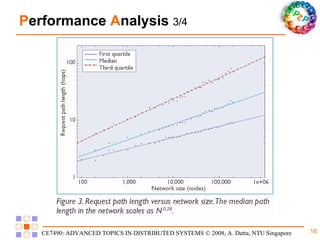
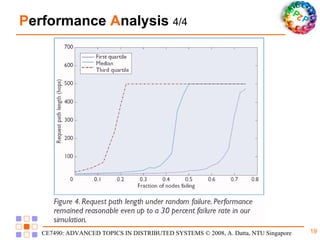
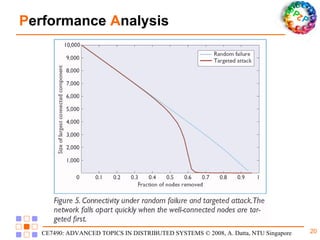
Freenet is a decentralized peer-to-peer platform designed for censorship-resistant storage and retrieval of information, prioritizing user anonymity and data privacy. The architecture of Freenet includes various types of GUID keys and routing mechanisms to facilitate the publication and access of files while managing node interactions. Although robust and scalable, Freenet faces challenges like the absence of file-lifetime guarantees and vulnerability to certain cyber attacks.